当前位置:网站首页>Lintcode logo queries the two nearest saplings
Lintcode logo queries the two nearest saplings
2022-07-06 14:23:00 【Lan Zhou Qianfan】
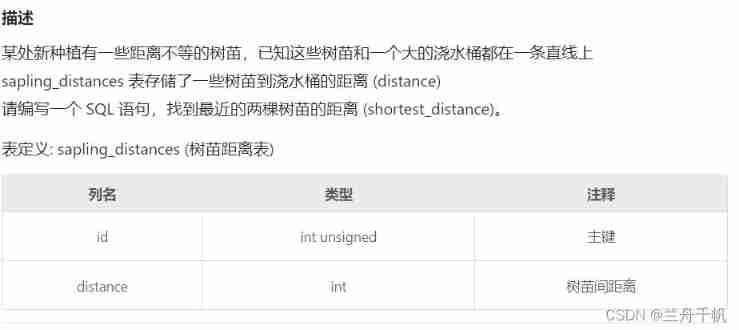
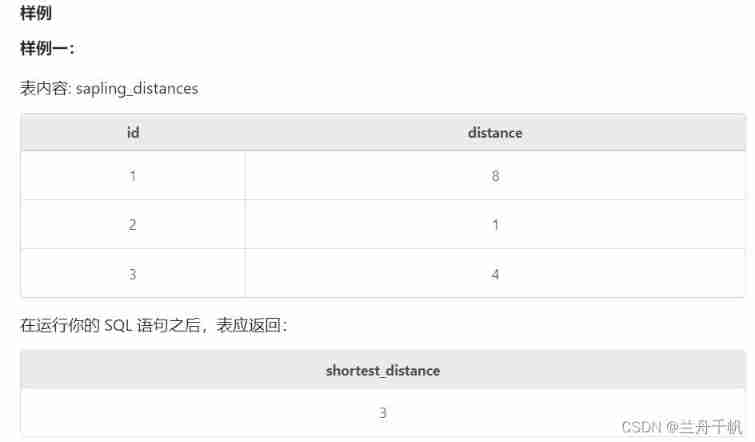
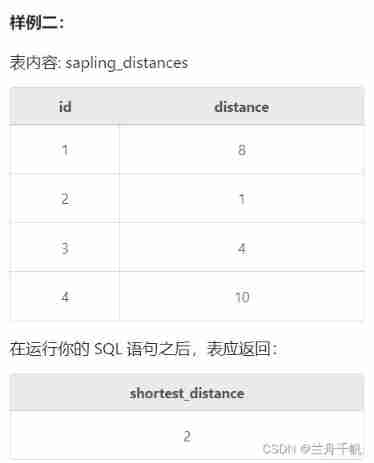
The requirement of the question is the distance between the nearest two trees in the query table . And rename the result (shortest_distance)
Answer 1 :( Adopt aggregate function and self connection )
SELECT MIN(ABS(a.distance - b.distance)) AS shortest_distance
FROM sapling_distances AS a
INNER JOIN sapling_distances b
ON a.id != b.id;
This is a very simple solution , Fields are not complicated .
Attention is paid to small details . Distance , The preconditions for finding the absolute value and the added minimum value are adopted . Then there is self join query . The condition of self connection query is the combination of both id inequality . If they are the same, then the query distance is meaningless . If id The same is comparing itself . What is the analogy between oneself and oneself ?
!= You can also use <> Instead of . It means the same thing
Explanation 2 :( Adopt nested query thinking )
SELECT MIN(distance_diff) AS shortest_distance FROM (
SELECT abs(b.distance - a.distance) AS distance_diff FROM sapling_distances a, sapling_distances b
WHERE a.id <> b.id
) cc
HAVING shortest_distance is not null;
It adopts the thinking of nested query , It's also very easy to understand . The outer layer minimizes the required result , The inner layer calculates the absolute value of the query distance . The processing of the table in memory is to name the table twice , Make it a different watch , Then attach conditions . The last thing to note is cc This is the name of the sub query table , If not , Will report a mistake , This is the grammatical requirement .
Answer 3 :( Another mode of thinking , It's nothing special )
select min(a.distance - b.distance) shortest_distance
from sapling_distances a
join sapling_distances b on a.distance > b.distance
having shortest_distance is not null;
One limitation a.distance>b.distance This replaces abs() Aggregate functions , In this way, you can also get normal results .
Solution 4 :( Superfluous solution , Simple problems complicate )
select min(s2.distance-s1.distance) shortest_distance from
(select distance,@rownum1:=@rownum1+1 r1
from sapling_distances,(select @rownum1:=0) ra
order by distance) s1,
(select distance,@rownum2:=@rownum2+1 r2
from sapling_distances,(select @rownum2:=0) rb
order by distance) s2
where s1.r1 = s2.r2-1 having shortest_distance is not null;
Don't explain , Because I won't . Solution from netizens . I really hate this solution . Simple problems complicate , Don't do it . ok ! I haven't used this method yet , When you learn it, you can add .
边栏推荐
- [experiment index of educator database]
- Realize applet payment function with applet cloud development (including source code)
- SQL injection
- Network technology related topics
- Library management system
- [err] 1055 - expression 1 of order by clause is not in group by clause MySQL
- HackMyvm靶机系列(2)-warrior
- 【Numpy和Pytorch的数据处理】
- Hackmyvm Target Series (3) - vues
- msf生成payload大全
猜你喜欢
HackMyvm靶机系列(4)-vulny
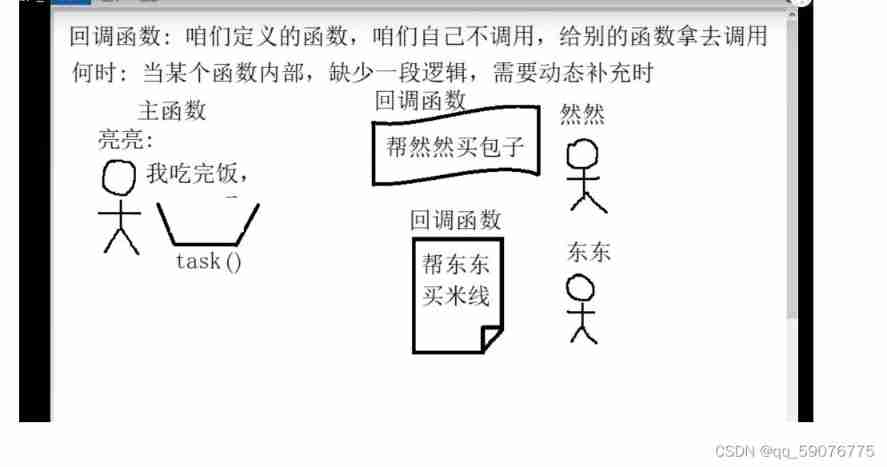
Callback function ----------- callback
Realize applet payment function with applet cloud development (including source code)
![New version of postman flows [introductory teaching chapter 01 send request]](/img/0f/a41a39093a1170cc3f62075fd76182.jpg)
New version of postman flows [introductory teaching chapter 01 send request]
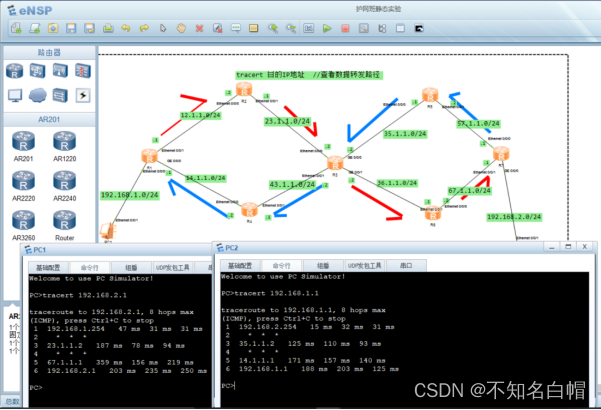
网络基础之路由详解

Uibutton status exploration and customization

JVM memory model concept
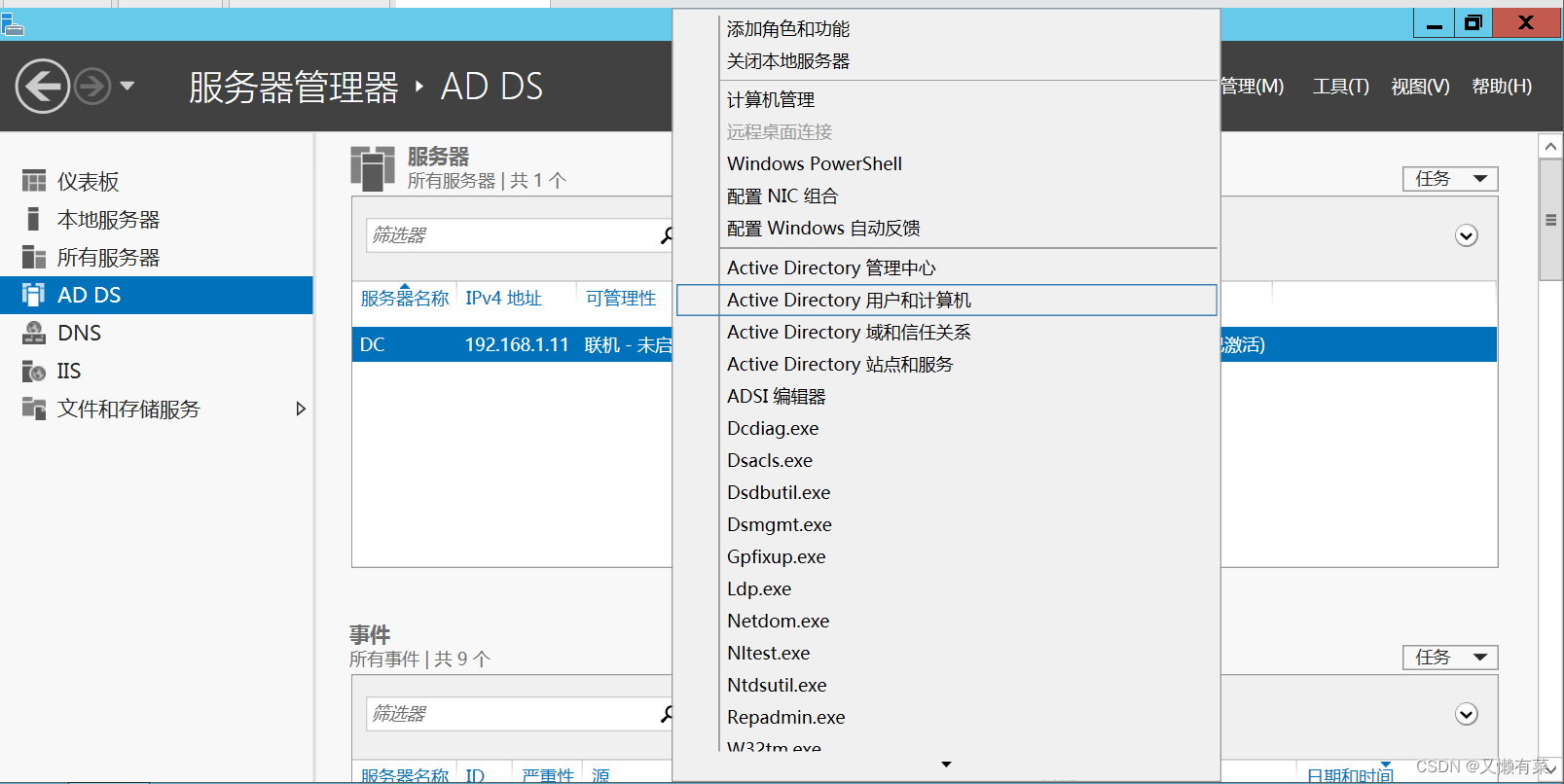
搭建域环境(win)

7-7 7003 combination lock (PTA program design)
HackMyvm靶机系列(2)-warrior
随机推荐
强化學習基礎記錄
攻防世界MISC练习区(SimpleRAR、base64stego、功夫再高也怕菜刀)
New version of postman flows [introductory teaching chapter 01 send request]
captcha-killer验证码识别插件
HackMyvm靶机系列(4)-vulny
Intranet information collection of Intranet penetration (5)
Circular queue (C language)
《统计学》第八版贾俊平第十一章一元线性回归知识点总结及课后习题答案
HackMyvm靶機系列(3)-visions
《统计学》第八版贾俊平第十四章指数知识点总结及课后习题答案
Xray and Burp linked Mining
Network technology related topics
xray与burp联动 挖掘
Web vulnerability - File Inclusion Vulnerability of file operation
Attach the simplified sample database to the SQLSERVER database instance
Hackmyvm target series (1) -webmaster
Hackmyvm target series (4) -vulny
[insert, modify and delete data in the headsong educator data table]
7-15 h0161. Find the greatest common divisor and the least common multiple (PTA program design)
JDBC看这篇就够了