当前位置:网站首页>Network technology related topics
Network technology related topics
2022-07-06 14:13:00 【Chen Shenshen】
Large network enterprise network foundation
What is? ARP?ARP The role of ?
What is? ICMP?
Briefly describe the forwarding principle of the switch .
Briefly describe the working principle of the router .
sketch Trunk The role of .
common Cisco What are the simulators ?
sketch “ Analog switch module ” and “1 A fast Ethernet interface module ”.
Three layer exchange
1. What is layer 3 switching ?
2. Briefly describe the defects of single arm routing .
3. Briefly describe the forwarding principle of layer 3 switch .
4.Cisco Switch common MLS What are the architectures ?
5. Figure out what is “ Virtual interface ”?
6. What is the command to start the routing function ?
7. Configure an interface on the layer 3 switch as a routing interface ( in other words : Disable the switch ) What's your order ?
8. What is? DHCP?
9. sketch DHCP Authentication method of relay service .
10. sketch DHCP Precautions for relay configuration .
Spanning tree protocol (STP)
Briefly describe the problems of redundant links .
What is? STP?
sketch STP How it works .
What is? “ bridge ”?
Spanning tree algorithm (STA) Which three steps can be classified ?
How to select the root bridge ?
How to select the root port ?
How to select the specified port ?
Figure Bridge ID The composition of .
10. Figure port ID The composition of .
11. What is? BPDU?
12.BPDU What are the key fields ?
13. What do you mean “STP convergence ”?
14. Use a table to list five types of switch ports “STP Status and use ”.
15. Briefly describe three timing methods of spanning tree timer , And write the default time .
16. Spanning tree and VLAN What are the main relationships between ?
Hot backup routing protocol (HSRP)
What is? HSRP?
sketch HSRP Who are the group members of , And explain the functions of each group member .
sketch HSRP How it works .
Icon “ fictitious MAC Address structure ( Mark the bytes of each segment , common 6 byte )”.
HSRP The configured router has six states , Namely ?
sketch HSRP Two kinds of timers , And mark the time .
sketch HSRP And VRRP The difference between ( Write at least three points ).
sketch “ preempt ” The role of .
sketch “ Port tracking ” The role of .
IP Subnet partition
sketch “IP Address ” What are the two parts .
Briefly describe the principle of subnet division .
Application of subnet division —— The formula :
① Number of subnets :
② Host number :
③ Number of available hosts :
Briefly describe what is “ soft ” The rules .
Briefly describe what is “ hard ” The rules .
sketch IP Four principles that address planning mainly follows .
Access control list ( One )
Briefly describe what is TCP? What is? UDP?( And explain the differences )
 2.
2.
3. Icon “TCP Three handshakes ” And “TCP Four times ( Wave ) hand ”.
4. Use a table to list commonly used TCP Port and its description .
5. Use a table to list commonly used UDP Port and its description .
6. What is? ACL?
7. common ACL What are the three types ?( Explain and write the list number range )
8. Icon ACL The inspection conditions of ( in other words “ACL Five elements of ”).
9. sketch ACL Application direction of .
Access control list ( Two )
Brief description of standards ACL And expansion ACL The difference between .
Write to see ACL Orders for information .
Network address translation (NAT)
What is? NAT?
NAT What are the ways to implement ?
sketch NAT The advantages of .
sketch NAT The shortcomings of .
sketch PAT The advantages of .
Write to see NAT Commands for converting entries .
边栏推荐
- Internet Management (Information Collection)
- [err] 1055 - expression 1 of order by clause is not in group by clause MySQL
- Safe driving skills on ice and snow roads
- Poker game program - man machine confrontation
- Tencent map circle
- 力扣152题乘数最大子数组
- Strengthen basic learning records
- Hackmyvm Target Series (3) - vues
- 浅谈漏洞发现思路
- Canvas foundation 2 - arc - draw arc
猜你喜欢
强化学习基础记录
Yugu p1012 spelling +p1019 word Solitaire (string)
网络基础之路由详解
![[dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i](/img/d7/4671b5a74317a8f87ffd36be2b34e1.jpg)
[dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i
HackMyvm靶机系列(5)-warez

1. First knowledge of C language (1)
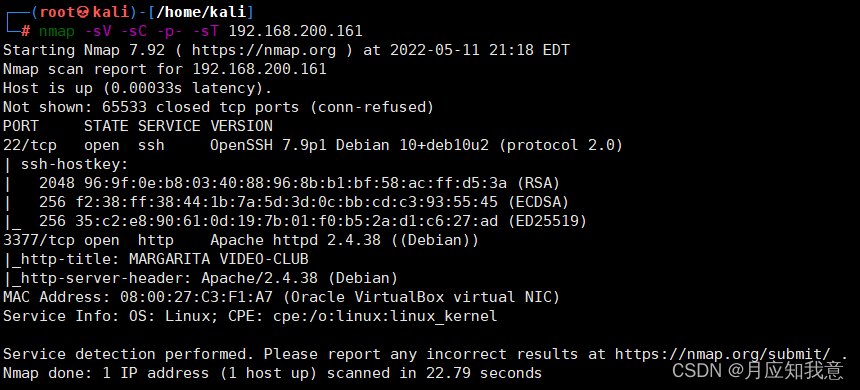
Hackmyvm target series (6) -videoclub
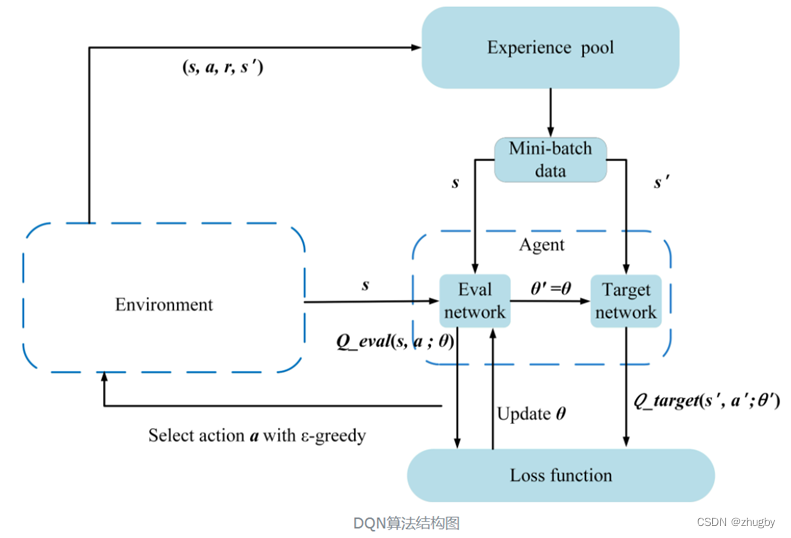
Intensive literature reading series (I): Courier routing and assignment for food delivery service using reinforcement learning
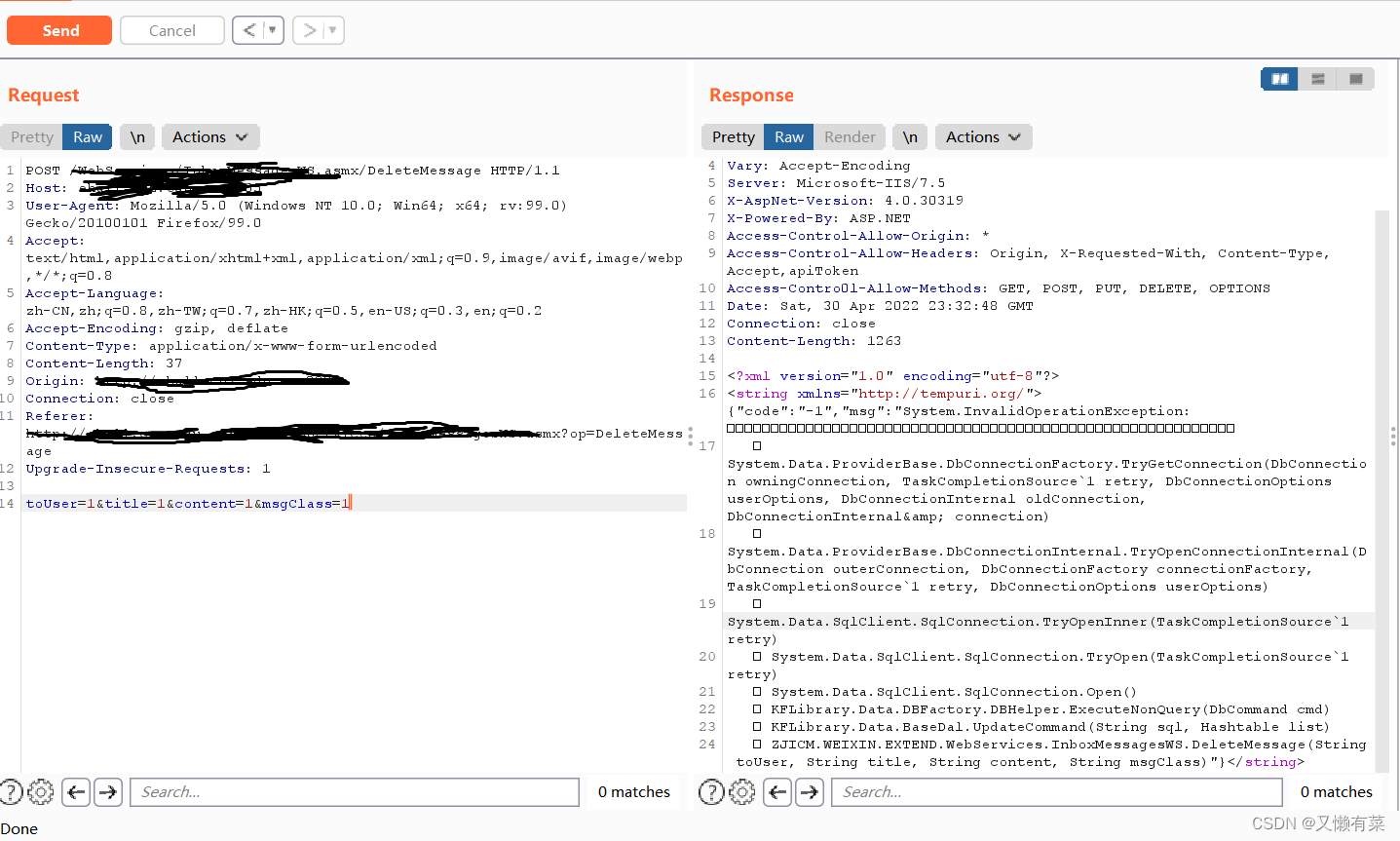
记一次api接口SQL注入实战

强化學習基礎記錄
随机推荐
Low income from doing we media? 90% of people make mistakes in these three points
记一次edu,SQL注入实战
Experiment 7 use of common classes
网络层—简单的arp断网
HackMyvm靶机系列(4)-vulny
Nuxtjs quick start (nuxt2)
Brief introduction to XHR - basic use of XHR
Yugu p1012 spelling +p1019 word Solitaire (string)
Wei Shen of Peking University revealed the current situation: his class is not very good, and there are only 5 or 6 middle-term students left after leaving class
强化学习基础记录
XSS之冷门事件
【MySQL数据库的学习】
附加简化版示例数据库到SqlServer数据库实例中
Hackmyvm target series (4) -vulny
记一次,修改密码逻辑漏洞实战
实验六 继承和多态
SQL injection
7-11 机工士姆斯塔迪奥(PTA程序设计)
Detailed explanation of network foundation routing
The United States has repeatedly revealed that the yield of interest rate hiked treasury bonds continued to rise