当前位置:网站首页>Just a coincidence? The mysterious technology of apple ios16 is actually the same as that of Chinese enterprises five years ago!
Just a coincidence? The mysterious technology of apple ios16 is actually the same as that of Chinese enterprises five years ago!
2022-07-05 12:14:00 【Episodic technique】
lately , Apples again “ rectify ” Mobile phone manufacturers .
There are rumors that , new edition iOS 16 Will add a named 「 Automatic verification 」 New functions , Skip pages and App Human machine verification process in , The upgrade iOS 16 Beta users , Can enter the 「 Set up 」—「Apple ID」—「 Password and security 」, Find this function at the bottom of the page .
What does that mean ?
before , When you open an apple App when , The system must first prove that you are “ people ” instead of “ machine ”, You need an identification code to prove that you are you , If you pass, you can be trusted . Now? , Apple directly skipped the verification code for users , in other words , Apple proved that you are you through the algorithm first .
For this update , Many fruit fans call :“ It's really human ”.
Senseless verification will be a new trend in the future
that , How Apple bypasses “ Verification Code ” What about ?
The answer is that Apple uses a new 、 Open authentication mechanism —— Privacy proof token (Private Access Tokens , Abbreviation for PAT).
PAT It does not refer to a technology or a service , It's a protocol that authenticates users . It needs to Client、Mediator、Issuer and Origin Participate in , To complete the whole verification , Here's the picture :
This automatic verification is between apple and cloud service providers Cloudflare It's done in cooperation , The implementation process is as follows ( Take the scenario where users use a browser to visit a website as an example ):
The whole process consists of four parts , Browser (Client)、 Apple mobile phone system (Mediator)、 Cloud service provider Cloudflare(Issuer), Website (Origin), The website background needs to be deployed in Cloudflare On .
First , Users use a browser to access the web site , Because the background of the website is deployed in Cloudflare On ,Cloudflare Will require the browser to carry token.
Then , The browser will call the apple system service to detect , The system service will detect the legitimacy of the current device , Whether it is a trusted device , Called after passing the check Cloudflare( As Issuer role )API,Cloudflare Generate token To the browser .
Last , The browser carries token Visit website (Origin), ad locum , Cloud service provider Cloudflare Act as a gateway proxy , As Origin Role to verify token The effectiveness of the , Let's visit the website .
It looks complicated , But there are two key points in the whole process :
First, there is no verification process that requires manual intervention in the whole verification process ( Input characters or click on pictures, etc ), The whole verification process basically does not need the transformation of the client and server , By Apple devices and cloud service providers , The judgment of whether the device is trusted is completed by Apple system , Compared with the three parties SDK, Apple system has the ability to get more information , Make a more comprehensive judgment . in addition , This technology can significantly increase the cost of crawlers that use scripts to crawl data directly without browsers ;
The second is to prove 「 I am a human 」 The way is also from the answer 、 Privacy transfer , It becomes more reasonable to check whether the device is cracked , Use support PAT Device and website of the agreement , It will reduce the pop-up of verification code , The user experience will be better .
And this verification method , It also coincides with the original intention of the supreme image senseless verification .
The top image senseless verification focuses on senseless , Combined with device fingerprints 、 behavior characteristics 、 Access frequency 、 Many technologies such as geographical location , Effectively intercept malicious login 、 Bulk registration , Block machine operation , Intercept abnormal users , Compared with the traditional verification code , The user does not have to think or enter operations , It can be verified with a single slide . After intelligent identification, it is a normal user , No further sliding operation is required within a certain period of time , It not only provides security for enterprises, but also allows users to pass through without perception , Greatly improved the user experience .
Apple, as the first brother of mobile phone manufacturers, first proposed 「 Automatic verification 」 The function of , Have reason to believe , future , Senseless verification will be the general trend .
Can we say goodbye to human-computer verification ?
that , Is man-machine verification about to leave the stage ?
“ There is still a long way to go ”, Top image business security experts say .
First ,PAT Mainly rely on Apple system to detect the legitimacy of the device , At present, it is not clear what specific tests have been done , Judging from the public information, it will detect whether the device is trusted , Whether the equipment parameters have been changed . This completely silent detection can block some man-machine risks to a certain extent , Such as script crawler , Because you can't get token And will be block fall . But in the Internet , The risk performance of robots is diverse , There are other ways besides script , For example, page automation driver , Through group control, etc , The coverage of this technology to these risks is still unknown .
Besides , At present, there are few cloud service providers supporting this scheme , Website /App There is a certain cost if you support , Before the large-scale promotion and application of this scheme, man-machine verification will still be the mainstream .
meanwhile , From the perspective of mobile phone manufacturers , The focus of this scheme is how to improve the user experience , But with security in mind , Coverage and other issues , There are still many details to be improved .
One side , To achieve this function, we need to transform the enterprise website to support PAT agreement , Or the enterprise website is hosted on the cloud service provider , Currently known to support PAT There are only two foreign cloud service providers Cloudflare and Fastly.
Besides , This scheme can only be used on foreign websites and App when , The experience will be better . If it's domestic , In addition to the corporate website 、iOS Application needs to be transformed , Also consider how compatible Android、 Hongmeng 、 Wechat Xiaocheng 、 Alipay applet, etc. .
On the other hand , In terms of security , Many black products in China will use device farms or cloud mobile phones , This technology may not be effective for attackers using device farms or cloud phones , The devices of device farm and cloud mobile phone are basically normal devices , If open Automatic Verification Set up , This technology may make it easier for attackers to obtain benefits .
also , The professional level of domestic black products is very high , The confrontation is also very intense , I believe it won't take long , in the light of PAT The bypassing or cracking scheme will come out . For domestic manufacturers who need human-machine protection , In marketing , Online activities and other scenes not only need sufficient security protection , It also needs rapid emergency response and updating capabilities . If PAT This scheme has been cracked , I'm afraid I can only wait iOS The next version is updated .
But I have to say , Apple also offers... To other mobile phone manufacturers “ model ”.
From a user experience perspective ,PAT It is a good innovation . But for the vast number of Internet enterprises , Safety and experience need to be considered at the same time . While improving the user experience , Need to prepare sufficient safety emergency capacity . For example, the backstage should have the ability to make dynamic risk decisions , It can adjust online security policies in real time ; There should be a variety of verification codes as a reserve , And it can switch in real time . therefore , Enterprises are connecting PAT At the same time , Cannot rely on PAT,PAT It is a scheme to optimize user experience , But it can't replace the whole business security .
non-inductive + Risk confrontation + The whole link protection scheme of the strategy will be the focus
Sum up , It's not hard to see. , For enterprises , Their need is not just to improve the user experience , What is more important is the ability to resist and protect risks and how to solve risk problems .
The top image defense cloud is based on years of practical experience and technical products , Have a wealth of technical tools 、 Tens of thousands of security policies and hundreds of business scenario solutions , Have intelligence 、 perception 、 analysis 、 Strategy 、 protective 、 Ability to dispose of , Provide modular configuration and elastic expansion , Help enterprises quickly 、 Efficient 、 Build an independent and controllable business security system at low cost .
It mainly includes business awareness defense platform 、 Verification Code 、 Products such as equipment fingerprint and end reinforcement . Have equipment authenticity identification 、 Behavioral verification 、 Risk perception 、 High performance real-time computing 、 Six capabilities, including efficient strategy execution and attack recovery . It can integrate the risk situation of the whole network , Provide industry enterprises with network wide security attack and defense confrontation intelligence ; Based on the technology and practical experience polished in the actual attack and defense , Form general industry strategies and exclusive strategies customized for needs , And real-time iteration and linkage through the cloud ; Provide risk identification 、 Defensive disposal 、 Attack restore 、 Manual review 、 Correlation analysis 、 Data precipitation and other integrated closed-loop risk disposal ; Besides , It also has the function of realizing black sample data 、 Precipitation of risk behavior characteristics , And distribute various business security systems through the cloud , Further improve the overall risk prevention and control .
Based on the top image defense cloud , Dingxiang also recently launched the fifth generation verification code . Combined with secure and trusted links 、 Rapid risk confrontation 、 Rich verification methods , It can effectively intercept the library collision and number scanning 、 Machine risk behaviors such as batch registration .
The product integrates cloud awareness , Upgraded the insensibility strategy , Combined with more risk identification dimensions , Have stronger offensive and defensive confrontation and user experience , covering iOS、 Android 、PC browser 、 Small program etc. . It is applied to all kinds of enterprises that want to do key machine flow prevention and control in the human-machine verification link . This product has the richest verification methods in the industry , By verifying the magic cube, we can achieve rapid attack and defense confrontation (10s Complete the configuration inside ,60s Effective ), Effectively intercept machine operation and other risk behaviors .
The specific term , It has the following advantages :
One 、 Intelligent senseless , Ultimate user experience
Top image intelligent risk control brain according to the suspicious degree of users , Multi level differentiation of user levels , Provide the ultimate experience for safe users , Security users pass without perception , High risk users need secondary verification . Compared with the previous generation of senseless mode , Strengthen the ability of equipment risk identification , Enhanced human-machine recognition model 、 Behavioral characteristics and other models , Provide a better experience for trusted security users .
Two 、 Cloud empowerment , Immediate awareness iteration
The top image defense cloud protects the Internet through online full link risk prevention and control products 、 Financial and other industries to monitor cheating 、 Analysis of black production characteristics 、 Business risk identification forms Risk Intelligence , Through the same industry 、 Cross industry risk intelligence information sharing , Connect the upstream and downstream prevention and control links , Link industries “ Information Island ", Thus, the new generation of verification code is endowed with the ability of self upgrading and iteration according to risk dynamics . More importantly, it empowers enterprise business personnel through cloud intelligence , Get risk dynamics at the first time , Provide prevention and control ideas , Help enterprises improve their risk prevention and control capabilities , From risk perception to risk control product upgrading 、 Closed loop process for improving risk control capability .
3、 ... and 、 Multidimensional judgment , Fast attack and defense confrontation
With the diversification of black production means , Multidimensional information is more powerful in risk judgment , A man-machine model of real-time flow computing and scene strategy combined with machine learning training 、 Correlation analysis of historical data , In the face of risk changes, it can achieve comprehensive 、 instant 、 Rapid risk analysis against .
At the user experience level , Combination of intelligent risk control identification and verification , Multi level differentiation of user requests through the risk control engine , It can realize the safe user to pass without perception , Enhance user experience , So far, it has been widely used in various Internet and financial institutions .
边栏推荐
- SENT协议译码的深入探讨
- What is digital existence? Digital transformation starts with digital existence
- Mmclassification training custom data
- Swift - add navigation bar
- Reading notes of growth hacker
- Principle of redis cluster mode
- [untitled]
- MySQL trigger
- MySQL transaction
- Check the debug port information in rancher and do idea remote JVM debug
猜你喜欢
![[pytorch modifies the pre training model: there is little difference between the measured loading pre training model and the random initialization of the model]](/img/ad/b96e9319212cf2724e0a640109665d.png)
[pytorch modifies the pre training model: there is little difference between the measured loading pre training model and the random initialization of the model]
Linux安装部署LAMP(Apache+MySQL+PHP)

July Huaqing learning-1
![[cloud native | kubernetes] actual battle of ingress case (13)](/img/1a/9404f6dcedd15827fa45f8f6f4c093.png)
[cloud native | kubernetes] actual battle of ingress case (13)
![[yolov3 loss function]](/img/79/87bcc408758403cf3993acc015381a.png)
[yolov3 loss function]
![[pytorch pre training model modification, addition and deletion of specific layers]](/img/cb/aa0b1116ec9b98e3ee5725aa58f4fe.png)
[pytorch pre training model modification, addition and deletion of specific layers]
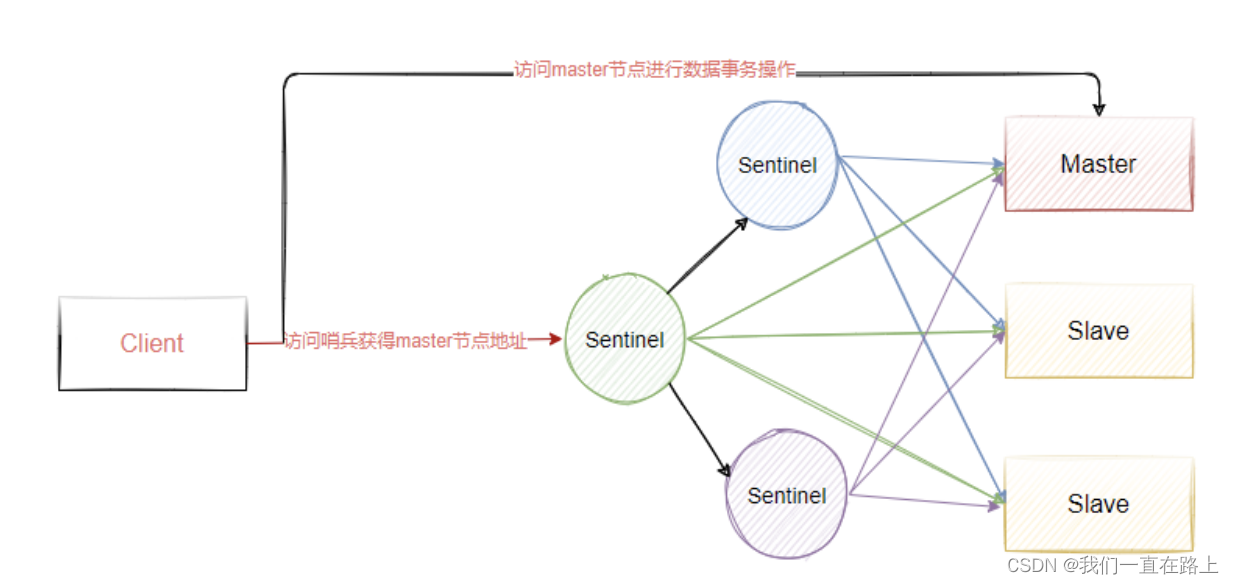
Sentinel sentinel mechanism of master automatic election in redis master-slave
Simple production of wechat applet cloud development authorization login
HiEngine:可媲美本地的云原生内存数据库引擎
嵌入式软件架构设计-消息交互
随机推荐
[loss functions of L1, L2 and smooth L1]
Principle of persistence mechanism of redis
Is investment and finance suitable for girls? What financial products can girls buy?
A guide to threaded and asynchronous UI development in the "quick start fluent Development Series tutorials"
Multi table operation - Auto Association query
The most comprehensive new database in the whole network, multidimensional table platform inventory note, flowus, airtable, seatable, Vig table Vika, flying Book Multidimensional table, heipayun, Zhix
1. Laravel creation project of PHP
一款新型的智能家居WiFi选择方案——SimpleWiFi在无线智能家居中的应用
Splunk configuration 163 mailbox alarm
Want to ask, how to choose a securities firm? Is it safe to open an account online?
MySQL constraints
7月华清学习-1
mmclassification 训练自定义数据
Recyclerview paging slide
IPv6与IPv4的区别 网信办等三部推进IPv6规模部署
Hash tag usage in redis cluster
Redis master-slave mode
[yolov5.yaml parsing]
无线WIFI学习型8路发射遥控模块
[mainstream nivida graphics card deep learning / reinforcement learning /ai computing power summary]