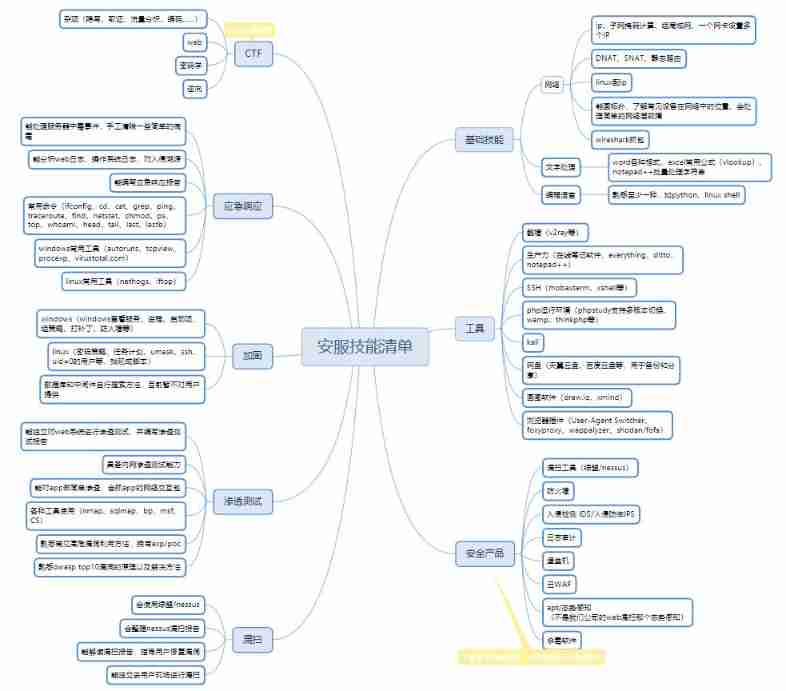
当前位置:网站首页>Network security - Security Service Engineer - detailed summary of skill manual (it is recommended to learn and collect)
Network security - Security Service Engineer - detailed summary of skill manual (it is recommended to learn and collect)
2022-07-06 03:47:00 【Advertising fever】
0x00 Skill outline
( One ) Basic network essential skills
( Two ) Use of common tools
( 3、 ... and ) Penetration testing skills
( Four ) Missed scanning skill ( The report , Repair , Independent support )
( 5、 ... and ) Emergency response
( 6、 ... and ) Safety reinforcement
( 7、 ... and ) Understanding of safety products
( 8、 ... and )CTF、 Target learning , Vulnerability mining, etc
0x01 Detailed explanation of skills and knowledge points
( One ) Basic network essential skills
1、ip、 Subnet mask calculation 、 Group lan 、 One network card sets up multiple IP
2、SNAT And DNAT:
This article is very good , But there are mistakes. Look at the comments :
https://blog.csdn.net/beanewself/article/details/78317626
SNAT: Modify the source address of the request message , For LAN access to the Internet
DNAT: Modify the destination address of the request message , For Internet access to local area network
#DNAT
iptables -t nat -A PREROUTING -d 172.18.0.107 -p tcp --dport=80 -j DNAT --to-destination 192.168.25.106:8000
#SNAT
iptables -t nat -A POSTROUTING -s 192.168.25.0/24 -j SNAT --to-source 172.18.0.10
3、 Static routing :
Static routing is mainly used in small networks , The number of network equipment of layer 3 switch or router is limited , The total number of network routes is limited , The workload of maintenance is controllable , At this point, we can consider using static routing ; Or network devices don't support some dynamic routing protocols, such as RIP,OSPF Only static routing can be used ;
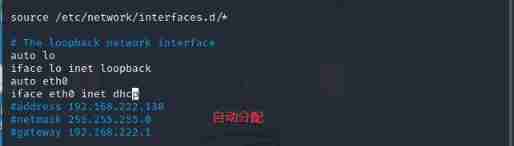
4、linux To configure IP:kali
vim /etc/network/interfaces
auto eth0
# Static settings ip
iface eth0 inet static / if dhcp Is automatically assigned , There is no need for , See clearly the network card and the spelling of words
# Set up ip Address
address 192.168.222.130
# Set subnet mask
netmask 255.255.255.0
# Set up the gateway
gateway 192.168.222.1
# restart
reboot
# Restart the service
systemctl restart networking
Temporary configuration IP, It doesn't work after restart
ifconfig eth0 192.168.222.130/24 # Configure temporary ip
route add default gw 192.168.222.1 # Configure the default route

5、 Understand the location of common devices in the network 、 Can draw topology , Handle simple network layer failures
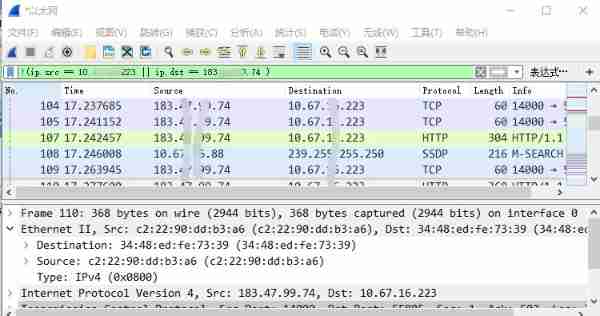
6、wireshark Use of packet capturing :
Command summary :
(1) MAC Address filtering
eth.addr==20:dc:e6:f3:78:cc
eth.src==20:dc:e6:f3:78:cc
eth.dst==20:dc:e6:f3:78:cc
(2)P Address filtering
ip.addr==192.168.1.1 // according to IP Address screening , Include source ip Or purpose IP
ip.src==192.168.1.1 // According to the source IP Address screening
ip.dst==192.168.1.1 // According to the purpose IP Address screening
(3) Port filtering
tcp.port==80 // according to TCP Port filter packets , Including source port or destination port
tcp.dstport==80 // According to the purpose TCP Port filter packets .
tcp.srcport==80 // According to the source TCP Port filter packets .
udp.port==4010 // according to UDP Port filter packets , Including source port or destination port
udp.srcport==4010 // According to the source UDP Port filter packets .
udp.dstport==4010 // According to the purpose UDP Port filter packets .
(4) Protocol filtering
Common agreements :
udp
tcp
arp
icmp
smtp
pop
dns
ip
ssl
http
ftp
telnet
ssh
rdp
rip
ospf
(5) Packet filtering
http.request.method==GET
http.request.method==POST
// select http The agreement adopts get/post Way of packet . Be careful GET Be sure to write in capital , Otherwise, it cannot be screened .
(6) Logical operations
|| // Logic or
&& // Logic and
! // Logic is not
7、 Word processing ability
Including but not limited to
1.word Various formats :
2.excel Common formula (vlookup):
Use of official documents :https://support.microsoft.com/zh-cn/office/vlookup-%E5%87%BD%E6%95%B0-0bbc8083-26fe-4963-8ab8-93a18ad188a1
VLOOKUP(lookup_value, table_array, col_index_num, [range_lookup]).
The expression is VLOOKUP( Find value , Find the range , Number of lookup columns , Exact match or approximate match )
for example :VLOOKUP(H3,$A$3:$F$19,5,FALSE)
Commonly recommended use FALSE As an accurate search , Others may have unexpected results
3.notepad++ Batch processing string : Various functions usually need to use regularization and so on , Attached is an introductory regular help I wrote before
https://blog.csdn.net/qq_53577336/article/details/121951156?spm=1001.2014.3001.5501
8、 Familiar with at least one programming language :
Usually it is Python,JAVA,GO etc.
The learning of programming language needs to accumulate over time , It can't be done quickly in a short time , Need more hands , It's better to watch it a hundred times than to master it , Xiaobian is also lazy , I hope the masters can persevere , Here is an article I wrote before python Introductory learning points :
https://blog.csdn.net/qq_53577336/article/details/121873412?spm=1001.2014.3001.5501
( Two ) Use of common necessary tools
1. Science and the Internet :
v2ray etc. , I won't elaborate here , A useful master kicked me / dog's head
2. Online productivity :
As a security service , People who eat need to take it with them at any time , Maybe the customer needs it in the middle of the night , Also have to from ah , After all, Party A's father didn't call for nothing
Online notebook ,
everything Universal search :https://www.voidtools.com/zh-cn/downloads/
notepad++( Support viewing in multiple languages ):https://www.aliyundrive.com/s/HMKr35RTN3x
ditto( Multifunctional pasting board ):https://pc.qq.com/detail/11/detail_24411.html
3.SSH Use (xshell(xftp Transmission tools ),mobaxterm etc. ):
xshell Download address :「Xshell-7.exe」https://www.aliyundrive.com/s/pPCfivHPdZT
xshell Use :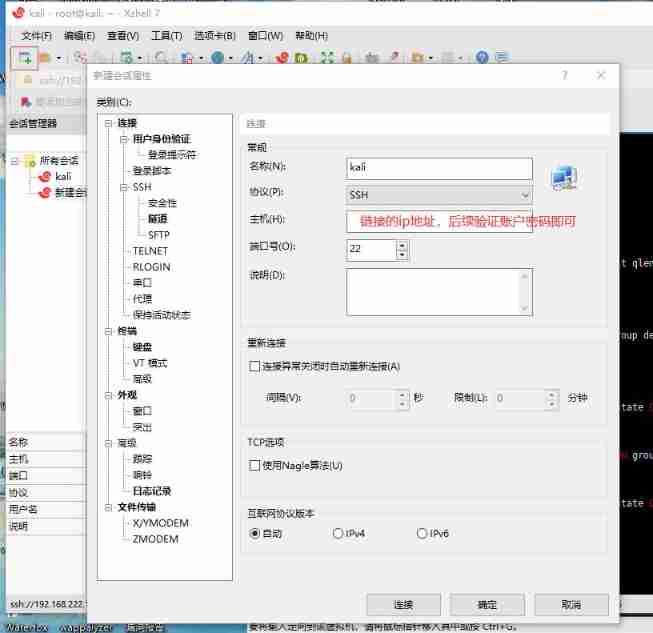
4.php Use of the operating environment :
phpstudy Support multi version switching 、wamp、thinkphp etc. )
Small leather panel download :https://www.xp.cn/
wamp Baidu itself can
5.kali
Penetration test weapon , Integrated many testing tools
6. Network disk
( Sky wing cloud disk 、 Baidu cloud disk, etc , For backup and sharing )
7. Drawing software
recommend Xmind Download address :https://www.aliyundrive.com/s/FVgE6vBHrDL
8. Use of browser plug-ins
Chrome User agent switch plug-in :User-Agent Switcher
You can install Firefox agent on Google browser :FoxyProxy
Fingerprint identification plug-in :wappalyzer
fofa、shodan etc.
( 3、 ... and )、 Penetration testing skills
1. Can be independent to web Perform penetration test on the system , And prepare penetration test report
Generally, security service penetration tests are mostly authorized , Use automated testing
Then write a report , Loophole recurrence and so on
2. Have the common sense of Intranet penetration , Lateral movement involving post infiltration , Knowledge points of authority promotion and Authority maintenance , You can refer to the previous articles to learn
Intranet penetration information collection :http://www.kxsy.work/2021/09/19/nei-wang-shen-tou-zui-shi-yong-de-xin-xi-shou-ji/
Intranet penetration horizontal movement :http://www.kxsy.work/2021/10/04/nei-wang-shen-tou-zui-shi-yong-de-heng-xiang-yi-dong-zong-jie/
Intranet penetration tunnel and agent technology solutions :http://www.kxsy.work/2021/10/09/nei-wang-shen-tou-bi-xu-zhang-wo-de-dai-li-yu-sui-dao-ji-zhu-jie-da/
3. Be able to app Simple penetration , Be able to carry on app Interactive packet capture
Let's talk about , commonly app The direction of infiltration theme is app to turn to web, This is the part related to information collection ,app For interactive packet capturing, you usually need to download an simulator, such as lightning simulator , Forward the traffic agent to the local machine in the simulator IP This machine bur The agent can capture packets
4. Use of various penetration tools :(nmap、sqlmap、bp、msf、CS)
nmap Common usage parameters :
-sS:syn Half open scan , Strong concealment
-sY: Full open scan , More accurate
-sT: Will record a lot of logs , Use with caution
-sP: Only when the host survives will it be scanned ping scanning
-sA: Advanced scanning , Filter through firewall rules
-sV: Version probe scan
-Pn: banned ping Scanning method
-A: Full scan
-p: Specified port scan /-p- Full port scanning
sqlmap Common use and bypass waf Ideas and methods :
Inject into Liulian :–dump -C “columns_name” -T “table_name” -D “db_name” ( --dbs/ --current-db/ --tables/–columns)
Customize ua head :–random-agent=“ua head ”
Setting agent :–proxy=
Delay injection parameters :–delay 1 ( One second delay )
cookie Inject :–cookie “ To get the cookie”
Level scan :–level 5 /–risk 3
Automatic interaction :–batch
Specify the plug-in call : --tamper
Thread injection :–threads Number of threads
Scanning record storage :…/…/././sqlmap/output
BurpSuite Basic use :
I summarized an article about BurpSuite Common use of , And some linkage penetration , For reading
BurpSuite Use :https://blog.csdn.net/qq_53577336/article/details/122393296
BurpSuite Advanced linkage :https://blog.csdn.net/qq_53577336/article/details/122674520
msf Basic use :
There is not much explanation here ,msf Is a big attack framework , You need to learn more about getting started
Search module :search ms17-010
Call a module :use modular
Check the configuration :show options
Configure relevant parameters, such as attacks IP:set rhosts IP
Start the attack :exploit
obtain shell:shell
CS Basic use of :
Reference resources :https://blog.csdn.net/qq_53577336/article/details/119768707
( Four )、 Missed scanning skill ( The report , Repair , Independent support )
As a security service , This should be the most work done , Missed scanning report , Loophole recurrence , Vulnerability repair suggestions, etc
1. Be able to use professional leak scanning tools
The missing scan in the line agrees with the measurement standard : Green League missed scanning arsa、 And others awvs,xray,nesus etc.
2. Be able to sort out missed reports , Check for false positives , Summary of test result report , There will be companies here Template Report
3. Able to organize templates , Guide the customer of the service to fix the vulnerability , Give suggestions, etc
4. It can independently support the whole missing scanning workflow , Some time ago, due to big brother , Later, if you are proficient, you need to have an independent missed scan output report and know the repair suggestions
( 5、 ... and )、 Emergency response
1. Can simply deal with some emergency time , And it can remove viruses and so on
2. Be able to analyze web journal , Operating system logs , Traceable attack information
Emergency response process and handling :http://www.kxsy.work/2021/10/13/zui-shi-yong-de-ying-ji-xiang-ying-bi-ji-si-lu-xiao-jie/
3. Writing skills , Prepare emergency response report
4.Linux Common practical commands :
ifconfig,cd,cat,ls,grep Screening ,find lookup ,ping,traceroute( Packet monitoring ),netstat( Internet Information ),chmod,ps process ,top Task manager ,whoami,head/tail View the contents of the specified line of the file ,last/lastb Login success or failure ,history History commands …
5.windows Commonly used tools :
autoruns( Boot item management tool )
tcpview( Port thread probe )
procexp( Daemon delete monitoring )
virustotal.com( file url virus detection )
6.linux Commonly used tools :
nethogs( Traffic monitoring )
iftop( Flow detection )
( 6、 ... and )、 Safety reinforcement
1.windows(windows View service 、 process 、 Start item 、 Group Policy 、 patch up 、 Firewall, etc )
2.linux( Password policy 、 Task plan 、umask、ssh、uid=0 Users, etc , Find a ready-made script )
3. Database and middleware reinforcement
Refer to previous articles for reinforcement :https://blog.csdn.net/qq_53577336/category_11479034.html
( 7、 ... and )、 Understanding of safety products
Security industry , Safety products are an essential part , As a security server, you should know all kinds of security devices at the network level , for example waf, Fortress machine , Leakage and , Honeypot , Situational awareness , Firewall commercial products and so on , As the safety service personnel of their own manufacturers , You should be familiar with the equipment , It has been better to serve customers .
Here are some manufacturers' safety products in various fields :
https://www.freebuf.com/news/307349.html
( 8、 ... and )、CTF hobby , Target learning , Vulnerability mining
CTF It can be used as a way to learn about vulnerabilities ,
Recommend a few ctf platform :
https://ctf.bugku.com
https://www.ctfhub.com
https://adworld.xctf.org.cn/
Target learning , Have a preliminary understanding of the penetration test process steps
https://www.vulnhub.com/
Vulnerability mining :
Mend the sky :https://www.butian.net/
Loophole box :https://www.vulbox.com
CNVD:https://www.cnvd.org.cn/
EDUsrc:https://src.sjtu.edu.cn/
The network security industry is an industry that needs continuous learning , But don't be too lazy, Masters , I'm almost rolled up / Purring
边栏推荐
- User experience index system
- SWC introduction
- Blue Bridge Cup - Castle formula
- Exchange bottles (graph theory + thinking)
- 遥感图像超分辨率论文推荐
- Python implementation of maddpg - (1) openai maddpg environment configuration
- P7735-[noi2021] heavy and heavy edges [tree chain dissection, line segment tree]
- Pytorch基础——(1)张量(tensor)的初始化
- [analysis of variance] single factor analysis and multi factor analysis
- Canvas cut blocks game code
猜你喜欢
![[Massey] Massey font format and typesetting requirements](/img/27/6b641551d6d8699683972f40f3b8e5.jpg)
[Massey] Massey font format and typesetting requirements

JS music online playback plug-in vsplayaudio js
Brush questions in summer -day3
Error 1045 (28000): access denied for user 'root' @ 'localhost' (using password: no/yes
1、工程新建
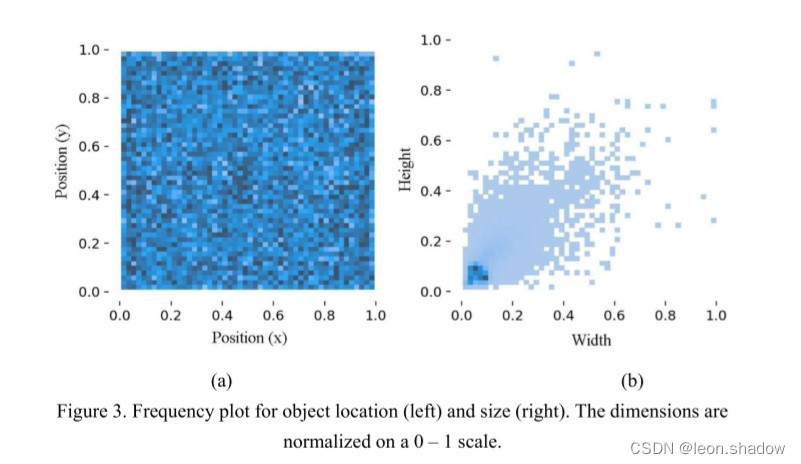
Remote Sensing Image Super-resolution and Object Detection: Benchmark and State of the Art
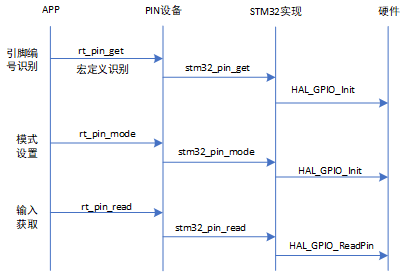
2.2 STM32 GPIO操作
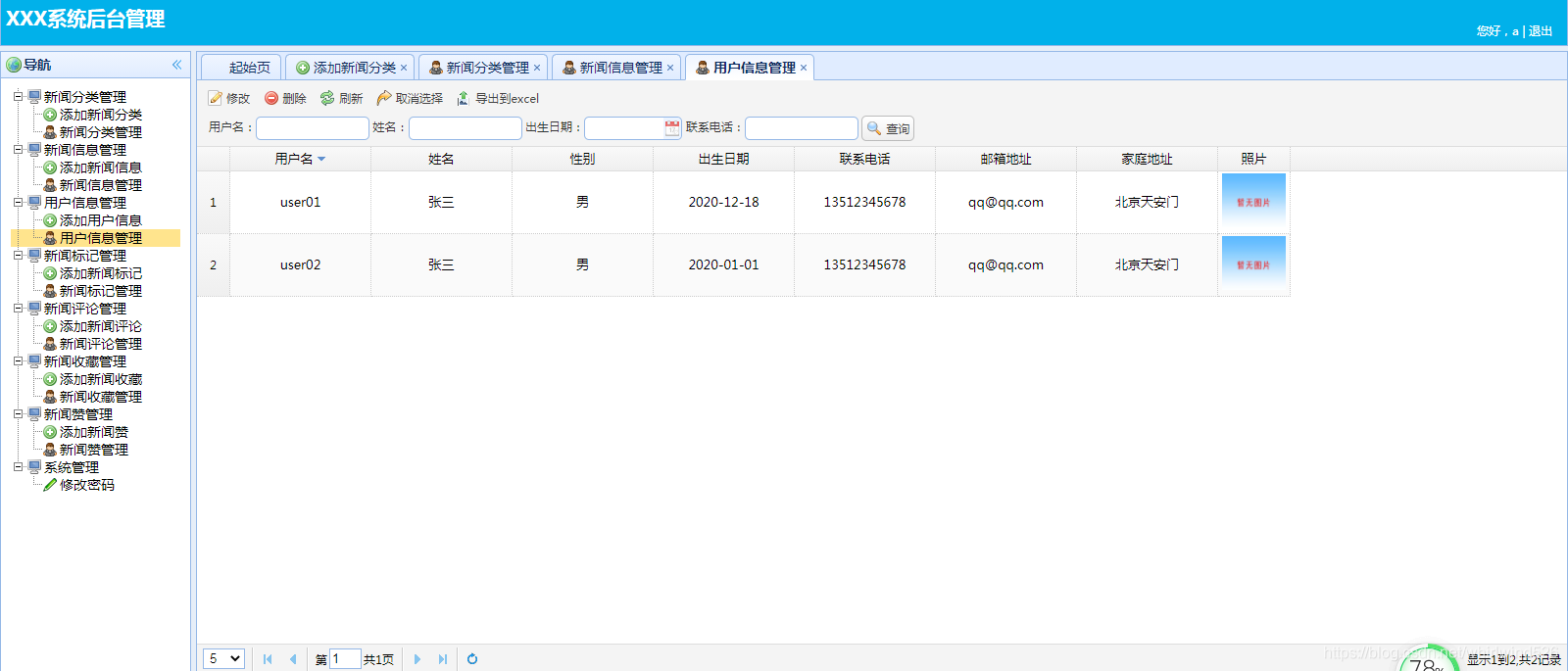
KS008基于SSM的新闻发布系统
![[risc-v] external interrupt](/img/9d/eb1c27e14045d9f1f690f4a7f5c596.jpg)
[risc-v] external interrupt
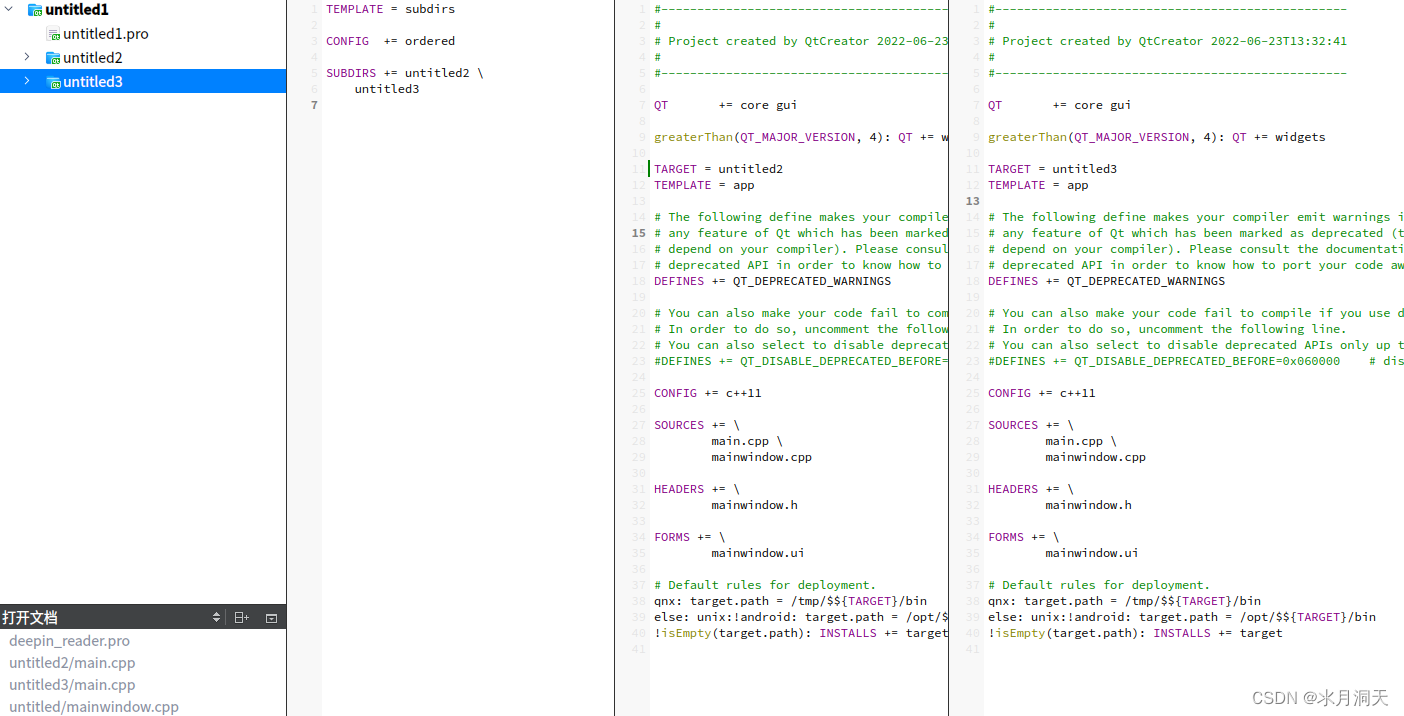
多项目编程极简用例
随机推荐
Facebook等大厂超十亿用户数据遭泄露,早该关注DID了
Cubemx transplantation punctual atom LCD display routine
[rust notes] 18 macro
Prime Protocol宣布在Moonbeam上的跨链互连应用程序
阿里测试师用UI自动化测试实现元素定位
Quartz misfire missed and compensated execution
SWC introduction
Prime protocol announces cross chain interconnection applications on moonbeam
施努卡:视觉定位系统 视觉定位系统的工作原理
Take you to wechat applet development in 3 minutes
Basic concepts of LTE user experience
KS003基于JSP和Servlet实现的商城系统
[risc-v] external interrupt
[optimization model] Monte Carlo method of optimization calculation
2.1 rtthread pin设备详解
Do you know cookies, sessions, tokens?
C#(三十)之C#comboBox ListView treeView
Introduction to data types in MySQL
[practical exercise] face location model based on skin color
Cubemx 移植正点原子LCD显示例程