当前位置:网站首页>Sorting, dichotomy
Sorting, dichotomy
2022-07-07 12:35:00 【Xiaobai shelter】
One 、 matters needing attention
1 name :
Mandatory rules : Numbers , Underline , Case letters , Dollar symbol , The number can't start , You can't use keywords and reserved words
Non mandatory rules : Look at the text and know the meaning , Hump nomenclature
Variable name and method name , Initial lowercase user, userService
Class names are capitalized User , UserService
2 notes
3 communicate
Two 、 Sort
Sort This means that the saved elements are sorted and stored according to certain rules
such as achievement Sort in descending order , Top three in the class Just take the first three data
2.1 Bubble sort
1 Compare adjacent elements . If the first one is bigger than the second one , Just swap them .
2 Do the same for each pair of adjacent elements , From the beginning of the first couple to the end of the last couple . At this point , The last element should be the largest number .
3 Repeat the above steps for all elements , Except for the last one . 4 Keep repeating the above steps for fewer and fewer elements each time , Until there's no pair of numbers to compare .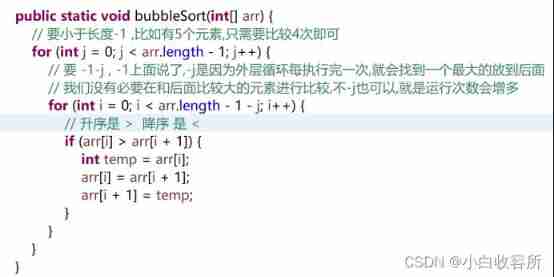
2.2 Selection sort
1 Put the smallest one on the left and take out the first one every time , The assumption is the smallest , Then compare with the following one by one , If there is one smaller than the first , Just exchange subscripts after a round of comparison , The subscript of the smallest element has been obtained , Then put it in the front for transposition
2 Repeat this step , Until after the current element When there are no other elements End 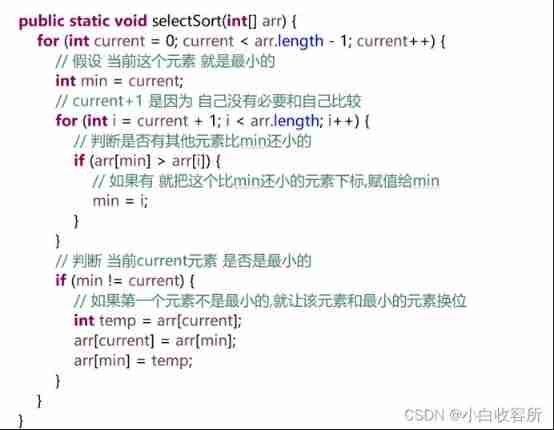
3. Look for the element 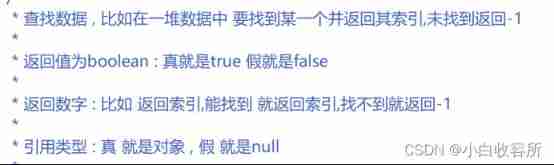
3.1 In order to find 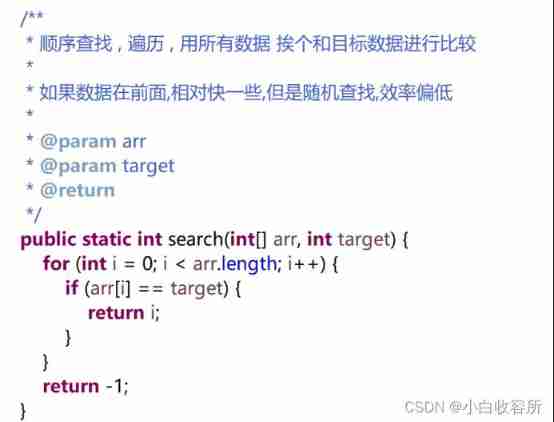
3.2 Two points search
/**
* Two points search , Also known as half query
*
* 1 The data must be orderly
*
* 2 Generally used for fixed data , Because of order , So adding and deleting is a little more troublesome , Also consider the element shift problem
*
* 3 Both ascending and descending are OK , Just change the algorithm judgment
*
* 4 Random query performance is good
*
* Algorithm implementation
*
* 1 Determine the beginning and end of the intermediate data
* 2 With target data and Compare intermediate data
* 3 If the target data is equal to the intermediate data , Return the index of intermediate data
* 4 If the target data is larger than the intermediate data , Then continue to search in the second half , start = middle +1, End unchanged , Then generate intermediate data
* 5 If the target data is smaller than the intermediate data , Take the first half , Initial invariance , end = middle -1, Then generate intermediate data
* 6 Repeat the above steps , If you start Greater than end Description not found , return -1
*
* @param arr
* @param target
* @return
*/
public static int binarySearch(int[] arr, int target) {
// 1 Determine the beginning and end of the intermediate data
int startIndex = 0;
int endIndex = arr.length-1;
int m = (startIndex+endIndex) /2;
// Cycle comparison
while (startIndex <= endIndex) {
// 3 If the target data is equal to the intermediate data , Return the index of intermediate data
if (target == arr[m]) {
return m;
}
// If the target data is larger than the intermediate data , Then continue to search in the second half , start = middle +1, End unchanged , Then generate intermediate data
if (target > arr[m]) {
startIndex=m+1;
}else{
// If the target data is smaller than the intermediate data , Take the first half , Initial invariance , end = middle -1, Then generate intermediate data
endIndex = m-1;
}
// Generate intermediate data
m = (startIndex+endIndex) /2;
}
// Can be implemented here , Indicates that there is no
return -1;
}
边栏推荐
- wallys/Qualcomm IPQ8072A networking SBC supports dual 10GbE, WiFi 6
- NGUI-UILabel
- @What happens if bean and @component are used on the same class?
- H3C HCl MPLS layer 2 dedicated line experiment
- Financial data acquisition (III) when a crawler encounters a web page that needs to scroll with the mouse wheel to refresh the data (nanny level tutorial)
- 【二叉树】删点成林
- (to be deleted later) yyds, paid academic resources, please keep a low profile!
- 利用栈来实现二进制转化为十进制
- Cenos openssh upgrade to version 8.4
- "Series after reading" my God! It's so simple to understand throttling and anti shake~
猜你喜欢
SQL Lab (41~45) (continuous update later)

Customize the web service configuration file
leetcode刷题:二叉树25(二叉搜索树的最近公共祖先)
Experiment with a web server that configures its own content
In the small skin panel, use CMD to enter the MySQL command, including the MySQL error unknown variable 'secure_ file_ Priv 'solution (super detailed)
Financial data acquisition (III) when a crawler encounters a web page that needs to scroll with the mouse wheel to refresh the data (nanny level tutorial)
2022A特种设备相关管理(锅炉压力容器压力管道)模拟考试题库模拟考试平台操作
数据库系统原理与应用教程(011)—— 关系数据库
30. Feed shot named entity recognition with self describing networks reading notes
SQL Lab (32~35) contains the principle understanding and precautions of wide byte injection (continuously updated later)
随机推荐
VSCode的学习使用
Experiment with a web server that configures its own content
【PyTorch实战】用RNN写诗
The left-hand side of an assignment expression may not be an optional property access. ts(2779)
通讯协议设计与实现
Learning and using vscode
ES底层原理之倒排索引
Using stack to convert binary to decimal
平安证券手机行开户安全吗?
[statistical learning methods] learning notes - Chapter 5: Decision Tree
利用棧來實現二進制轉化為十進制
File upload vulnerability - upload labs (1~2)
College entrance examination composition, high-frequency mention of science and Technology
Upgrade from a tool to a solution, and the new site with praise points to new value
30. Feed shot named entity recognition with self describing networks reading notes
leetcode刷题:二叉树21(验证二叉搜索树)
leetcode刷题:二叉树24(二叉树的最近公共祖先)
Is it safe to open an account in Ping An Securities mobile bank?
【深度学习】图像多标签分类任务,百度PaddleClas
消息队列消息丢失和消息重复发送的处理策略