当前位置:网站首页>Reptiles have a good time. Are you full? These three bottom lines must not be touched!
Reptiles have a good time. Are you full? These three bottom lines must not be touched!
2022-07-06 18:46:00 【Big data V】
Reading guide : Legal compliance 、 Carefully apply crawler technology .
author : Guo Bin Jim Yuzhiwen
source : big data DT(ID:hzdashuju)

Data crawling technology has always been one of the efficient ways for data companies to obtain data , But strictly speaking, crawling behavior itself is not completely legal and compliant , According to China's current laws and regulations and judicial precedents , Crawler technology may violate the legal requirements of the following dimensions ( List only the relatively important legal dimensions ).
01 Anti Unfair Competition Law Dimension
Without the authorization of the crawled party , Crawling data may violate Robots agreement .Robots Protocol is a mechanism produced by the technical community to solve the communication of intention between the crawling party and the crawling party through computer program .2012 year 11 month 1 Japan , Twelve enterprises jointly launched 《 Self regulation Convention on Internet search engine services 》, The Convention requires all signatories to abide by Robots agreement .
In judicial practice , Even if the crawler does not belong to the above 12 Within companies ,Robots The agreement has also been recognized as a recognized business ethics in the search field of the Internet industry : Beijing first intermediate people's court in the unfair competition case of an Internet security company , Will be recognized in the industry Robots The agreement is recognized as a recognized business ethics in the search field of the Internet industry .
The Court pointed out in its judgment that :
When the defendant launched the search engine , Its website also published Robots Content and setting method of the agreement , It shows that the entire Internet industry, including the defendant, is interested in Robots Agreements are recognized and observed . It should be recognized as a general rule in the industry , Should be recognized as the search engine industry recognized 、 Business ethics that should be observed .
therefore , Crawler violates Robots The behavior of the agreement may be considered as a violation 《 Anti Unfair Competition Law 》 The first 2 strip , That is, violating the principle of good faith and business ethics .
Although the information disclosed on the network is difficult to constitute trade secrets , But because some information on the network can be made by taking technical measures Only specific users can contact , Therefore, the information on the network may still have the confidentiality and confidentiality required by trade secrets , The possibility of constituting trade secrets .
If the crawler controller deliberately evades the protection measures set by the website operator in the process of capturing information , Contact 、 Save and even disclose information that ordinary users cannot access , And such information constitutes a trade secret , Then such behaviors of the crawler controller may infringe the trade secrets of others , In turn, it may violate 《 Anti Unfair Competition Law 》 The first 9 strip .
meanwhile , Because the crawler will hinder the network system of the crawled party , So such behavior may violate 《 Anti Unfair Competition Law 》 The first 12 strip .

02 Copyright dimension
Whether it's an article on the Internet 、 picture 、 User reviews , Or the website's own database , It is possible to constitute works protected by copyright law with originality . The capture and use of such information may constitute an infringement of copyright , Especially the right of reproduction and the right of network information dissemination . Because the behavior of grabbing data is essentially the replication of data , Therefore, such acts may infringe the copyright owner's reproduction right .
At the same time, in terms of data extraction and use behavior , If the crawler controller grabs the information , Publicly disseminate the captured information on their own websites , Then it may further infringe the right of information network dissemination .
for example , Ma and others sued a network technology company for copyright infringement dispute .
The facts of the case
The defendant, a network technology company, used the computer crawler technology similar to the search engine to collect French entries and search for translation and interpretation , Using the copyright enjoyed by the plaintiff in large quantities without paying the corresponding remuneration 《 Contemporary French Chinese Dictionary of science and Technology 》 The content in , Mr. Ma sued the network technology company for copyright infringement .
Verdict
According to the law , In addition to reasonable use , The use of others' works shall be subject to the consent of the copyright owner , And pay corresponding remuneration . The defendant claimed that he collected vocabulary entries and Chinese definitions through crawler technology , This technology is a means for the defendant to collect and form his Online Dictionary Thesaurus , Instead of using 《 French assistant 》 when , Directly point to other target websites through search links , The defendant should have a high duty of examination and attention to the legality of the vocabulary and Chinese interpretation it collects and uses .
therefore , The content of the French translation software made by the defendant , Some plagiarized the plaintiff 《 Contemporary French Chinese Dictionary of science and Technology 》 The interpretation of , Infringed the copyright of the plaintiff and others , Should undertake to stop infringement according to law 、 Apologize 、 Civil liability for damages .
03 《 The criminal law 》 And 《 Network security law 》 dimension
From a technical point of view , Crawlers may cause the target website to be overloaded , And then cause the website to be inaccessible or even paralyzed , Crawling party may violate 《 Network security law 》 About China Network operation security Provisions on . But if you are also involved in intrusion , May violate 《 The criminal law 》 The first 285、286 The provisions of article .
For example, in a case , Wang used the method of remote login , Invade the computer information system of the target company through an attack instruction , The email address of the company's employees in the system 、 The address book is exported , Then change the corresponding password , So you can enter the employee's mailbox at will , Finally, he was sentenced to the crime of illegally obtaining computer information system data .
From the perspective of crawling content , If the content crawled is personal information , Then it may violate 《 Network security law 》 Requirements on the compliance of collecting personal information , May even violate 《 The criminal law 》 The crime of infringing on citizens' personal information .

Summary
Sum up , Data crawling is not only easy to attract the attention of regulators , It is also vulnerable to lawsuits from competitors , It is suggested that enterprises should pay attention to the following points when crawling data .
Try to avoid crawling the platform data of enterprises that form a direct competitive relationship , Avoid competitors' basis 《 Anti Unfair Competition Law 》 The risk of litigation .
Try to crawl clear and public data , comply with Robots Agreements and other explicit and public agreements on websites , Avoid crawling the data prohibited by the platform .
according to 《 Data security management measures ( Solicitation draft )》 The first 16 The requirements of article , Data crawling and collection traffic shall not exceed one third of the average daily traffic of the website , Avoid causing the target website to crash 、 Unable to operate normally .
For the target website, technical measures have been clearly taken to prevent crawler access , The company should not invade 、 Destroy its protective measures .
For example, the target website clearly issued a notice to stop data crawling , Then the data crawling behavior should be suspended , Take measures in time .
This article is excerpted from 《 Data compliance : introduction 、 Actual combat and advanced 》(ISBN:978-7-111-70536-9), Issued under the authority of the publisher .

Extended reading 《 Data compliance : introduction 、 Actual combat and advanced 》
Click on the picture above to learn and buy
Please contact wechat for reprint :DoctorData
Recommended language : Systematic summary of years of front-line management experience ! Follow the protagonist to grow , Quickly grasp the practical treatment scheme in multiple scenes ! A Practical Workbook for enterprise data compliance governance ! The secret to the growth of data compliance professionals !
About author : Meng Jie , He is now a partner of Beijing universal law firm , The main field of practice is network security 、 Personal information and privacy protection . He has served as legal director and data protection officer in many well-known enterprises , ren IAPP Chairman of knowledge community in China , By chambers 、The Legal 500、LEGALBAND And other well-known legal rating agencies “TMT Field leader ”“ Leader in data protection ”“Fintech Head lawyer in the field ” etc. , He was rated as one thousand foreign-related expert lawyers by Beijing Lawyers Association .
Xue Ying , He has been the director of data compliance and intellectual property in Internet Group for a long time . In a foreign company 、 The world's top 500 companies have been engaged in data privacy compliance for many years , Have rich front-line experience in Internet scenes . hold CIPP/E、CIPP/U authentication , election ALB China intellectual property legal affairs 15 Strong and led the team to win 《 commercial law 》 year “ Data compliance ” Excellent team and other awards .
Zhulingfeng , Currently, he is a privacy and data compliance expert of well-known Internet companies , He used to be the vice chairman of Xiaomi security and privacy committee . He has been engaged in data privacy compliance research and practical work for many years , Deeply participate in the formulation of domestic information security related standards and important legal discussions , In global privacy law research 、 Privacy protection design 、 Application and management of privacy security technology and App、 The Internet of things 、 Rich practical experience in artificial intelligence and other fields .

Focus on
Dry goods go straight to
The booming intelligent Internet of things in recent years (AIoT), What is the future ?
AI Landing Manufacturing : Intelligent robots should have this 4 Kind of ability
More exciting
Enter the following dialog box in the official account dialog box key word
See more quality content !
read | book | dried food | Make it clear | God operation | handy
big data | Cloud computing | database | Python | Reptiles | visualization
AI | Artificial intelligence | machine learning | Deep learning | NLP
5G | Zhongtai | User portrait | mathematics | Algorithm | Number twin
According to statistics ,99% The big coffee is concerned about the official account
边栏推荐
- How does crmeb mall system help marketing?
- UFIDA OA vulnerability learning - ncfindweb directory traversal vulnerability
- STM32+ENC28J60+UIP协议栈实现WEB服务器示例
- C#/VB.NET 给PDF文档添加文本/图像水印
- 小程序在产业互联网中的作用
- 人体骨骼点检测:自顶向下(部分理论)
- AFNetworking框架_上传文件或图像server
- ORACLE进阶(四)表连接讲解
- Cobra 快速入门 - 专为命令行程序而生
- 同宇新材冲刺深交所:年营收9.47亿 张驰与苏世国为实控人
猜你喜欢
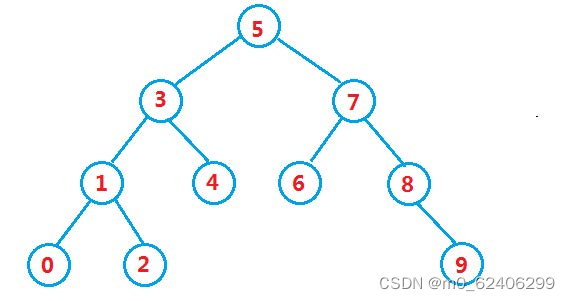
二叉搜索树
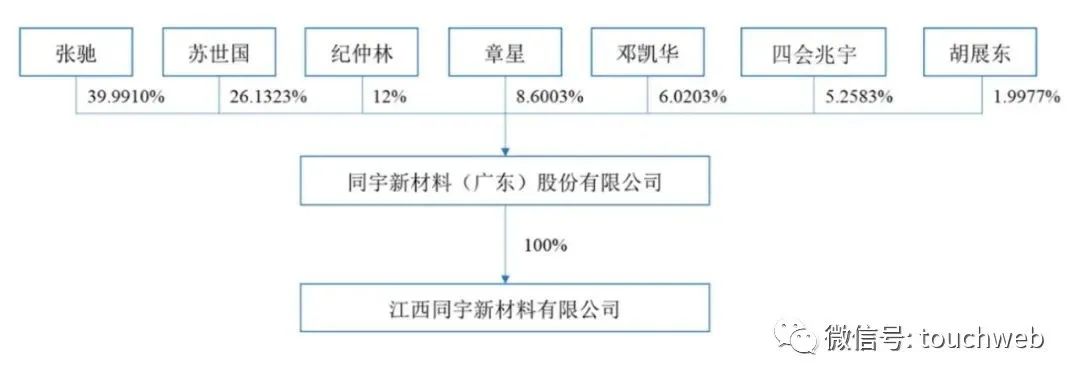
同宇新材冲刺深交所:年营收9.47亿 张驰与苏世国为实控人
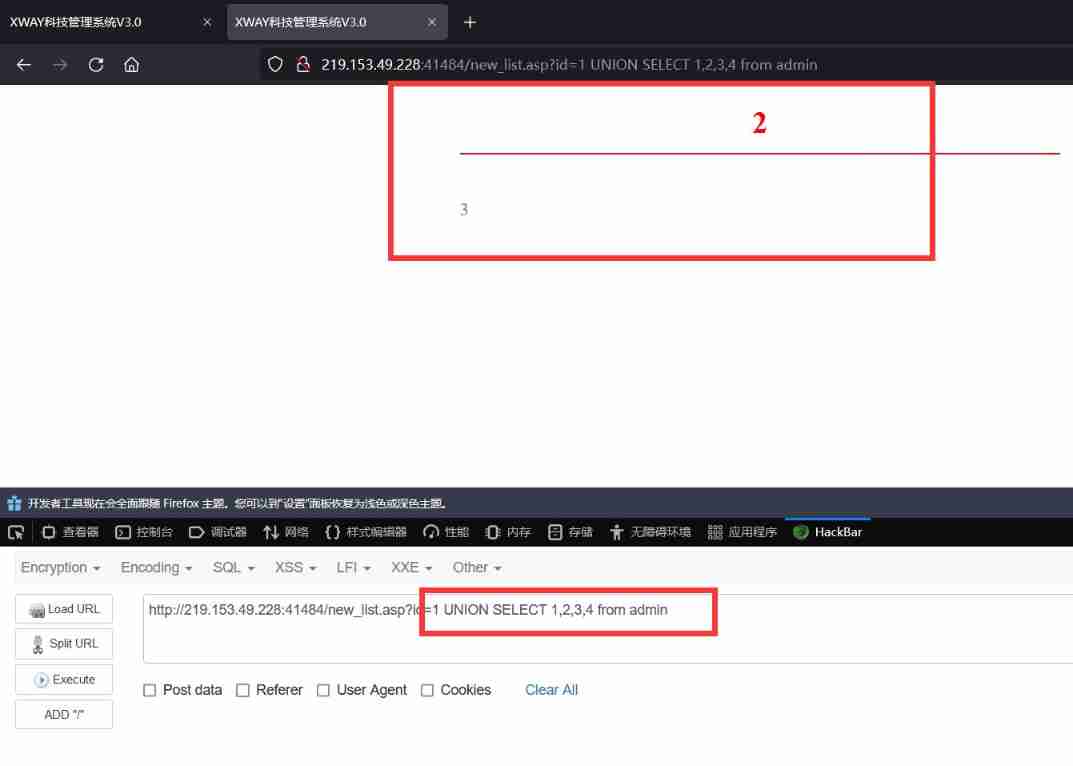
SQL injection - access injection, access offset injection
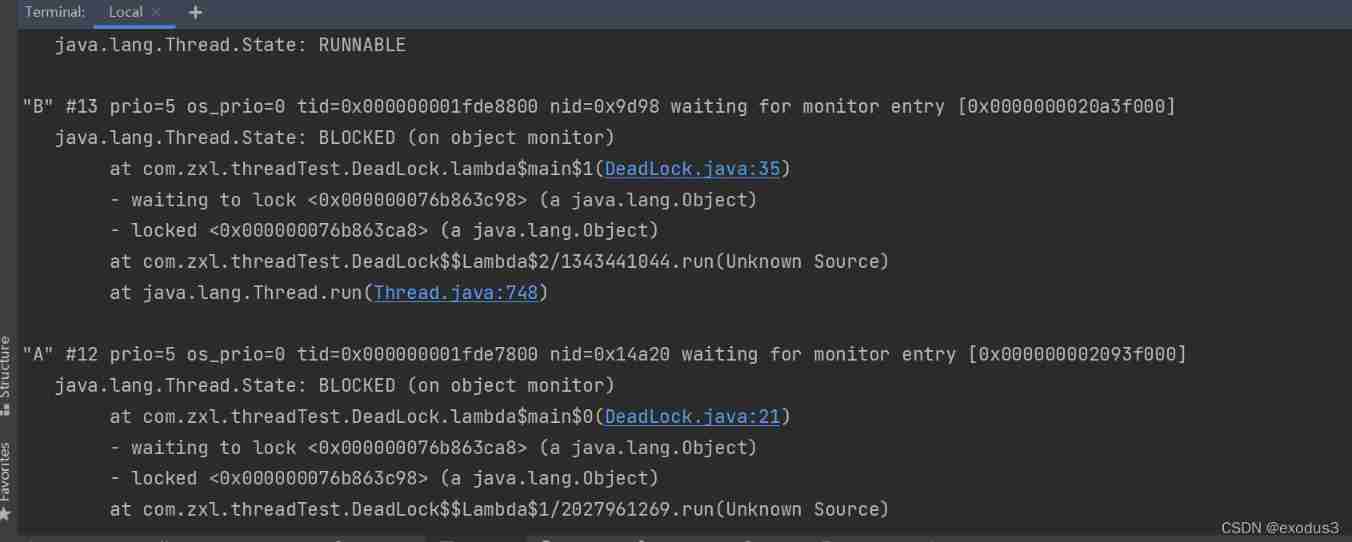
Shangsilicon Valley JUC high concurrency programming learning notes (3) multi thread lock

人体骨骼点检测:自顶向下(部分理论)
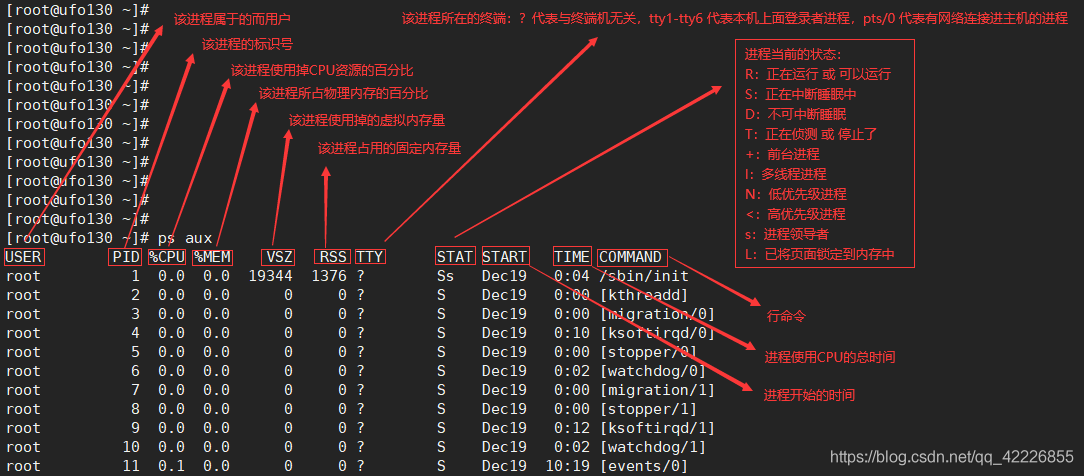
10、 Process management
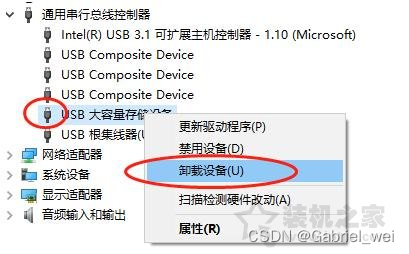
There is a sound prompt when inserting a USB flash disk under win10 system, but the drive letter is not displayed
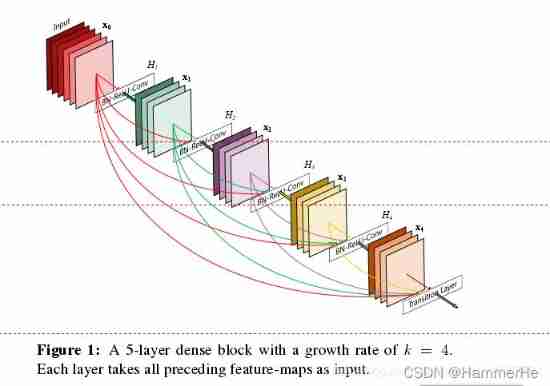
Medical image segmentation
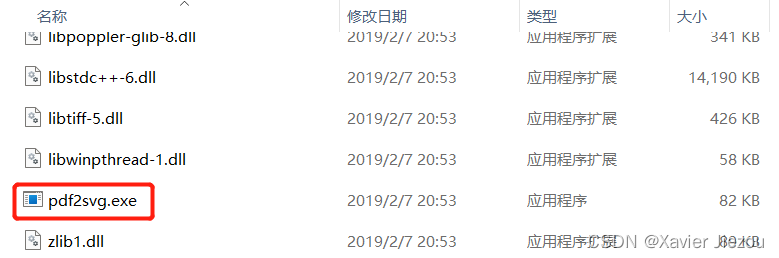
Easy to use PDF to SVG program
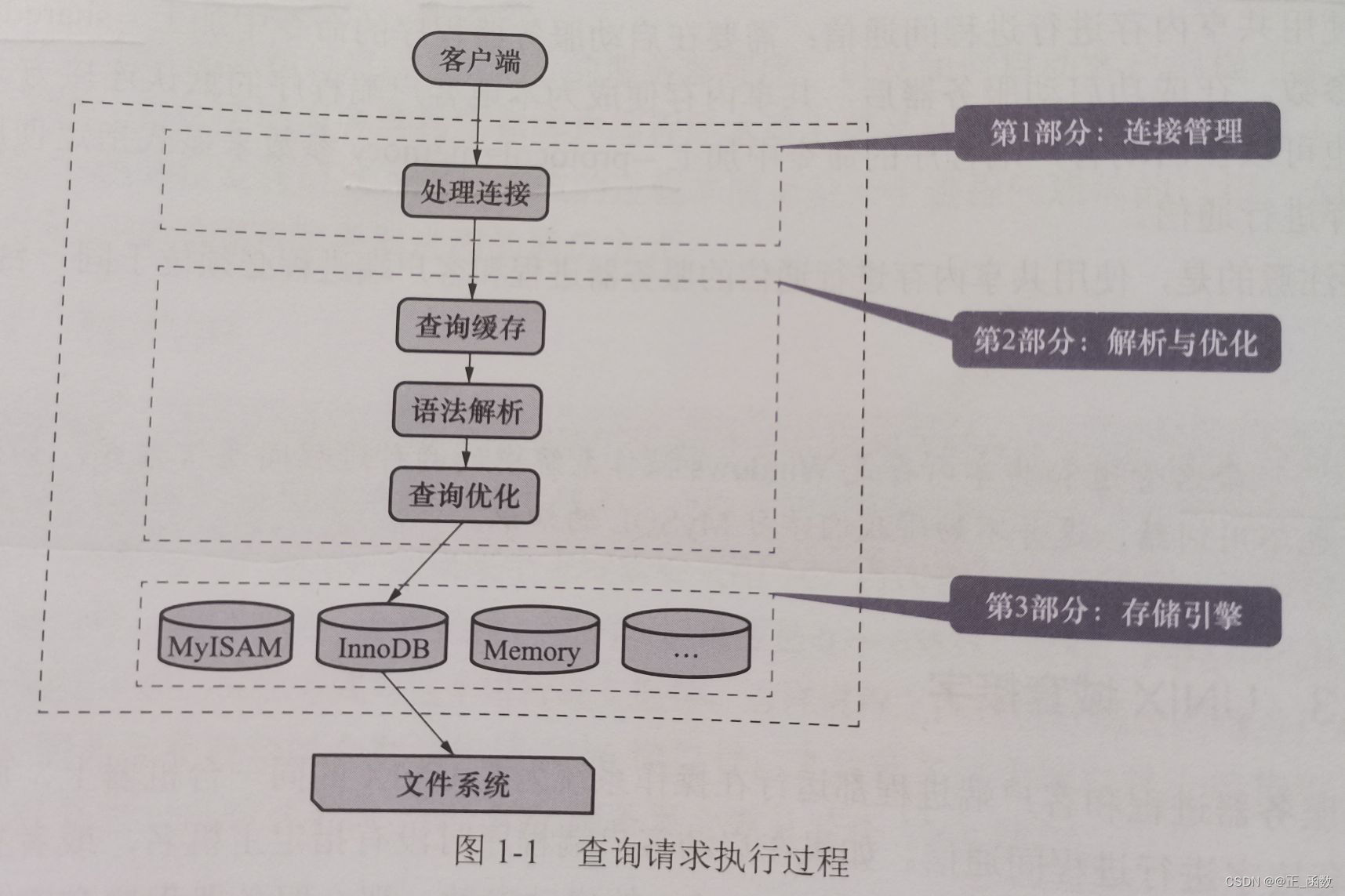
MySQL查询请求的执行过程——底层原理
随机推荐
Describe the process of key exchange
celery最佳实践
关于npm install 报错问题 error 1
C#/VB.NET 给PDF文档添加文本/图像水印
DOM Brief
Atcoder a mountaineer
RedisSystemException:WRONGTYPE Operation against a key holding the wrong kind of value
Execution process of MySQL query request - underlying principle
Use cpolar to build a business website (1)
[the 300th weekly match of leetcode]
Specify flume introduction, installation and configuration
Shangsilicon Valley JUC high concurrency programming learning notes (3) multi thread lock
Why does wechat use SQLite to save chat records?
Oracle advanced (IV) table connection explanation
Nuc11 cheetah Canyon setting U disk startup
[sword finger offer] 60 Points of N dice
SQL injection - access injection, access offset injection
Huawei 0 foundation - image sorting
Brief description of SQL optimization problems
epoll()无论涉及wait队列分析