当前位置:网站首页>Review of network attack and defense
Review of network attack and defense
2022-07-07 19:03:00 【Godams】
The introduction
1、 Cyberspace 4 Elements ( facilities 、 data 、 user 、 operation ) See Chapter one PPT 61 page
The following figure should be memorized 
2、 Basic concepts of Cyberspace Security ;
⽹ Network space security involves ⽹ Electromagnetic equipment in network space 、 electric ⼦ The information system 、 shipment ⾏ Data and systems should ⽤ Security problems in . It is necessary to prevent ⽌、 Protect “ Information and communication technology systems ” And the data it carries are damaged. We should also deal with the political security caused by these ICT systems 、 Economic security 、⽂ Chemical safety 、 Social security and national defense security .⽹ Main research on network space security ⽹ Security threats and protection in Cyberspace . Including infrastructure 、 Security and credibility of information system 、 And the confidentiality of relevant information 、 integrity 、 can ⽤ sex 、 Authenticity and controllability
3、 Network security attributes ;
Including infrastructure 、 Security and credibility of information system 、 And the confidentiality of relevant information 、 integrity 、 can ⽤ sex 、 Authenticity and controllability
4、 Basic concept of network attack 、 classification ( Focus on understanding active attacks 、 Passive attack );
PPT There are three parts in the concept :
- Cyber attack refers to any unauthorized act of entering or attempting to enter another person's computer network , It's the intruder intrusion The technical means and methods adopted for the purpose .
- Network attack refers to the use of security flaws in enemy network systems , by steal 、 modify 、 Falsify or destroy information , As well as reduce 、 Various measures and actions taken to destroy the efficiency of network use . Due to computer hardware and software 、 There are inevitable security vulnerabilities in network protocol, structure and network management , It makes network attacks impossible to prevent .
- Network attack refers to the use of security flaws or improper configuration of network information system hardware 、 Software or communication protocol , Damage the integrity of network information system 、 Usability 、 Confidentiality and non repudiation , Lead to the disclosure of sensitive information of the attacked information system 、 Unauthorized access 、 Attack behavior with consequences such as the decline of service quality .
classification :
- Take the initiative to attack : The attacker in order to achieve the purpose of the attack , Take the initiative to conduct unauthorized access to the system . It is usually a destructive attack , It will have a direct impact on the system . It can also be divided into the following 3 class :① interrupt It is an attack on the availability of the system . Such as destroying computer hardware 、 Network or file management system ② Tampering It is an attack on the integrity of the system . Such as modifying the data in the data file 、 Replace a program to perform different functions 、 Modify the message content transmitted in the network .③ forge It is an attack on the authenticity of the system . Such as inserting forged messages into the network or inserting forged records into files .
- Passive attack : Take advantage of the loopholes and security defects in the network to improve the hardware of the network system 、 Attacks on software and data in its system . Generally, the data is not tampered , Obtain the message content without user authorization by interception or eavesdropping , Or analyze the business data flow .
5、 Three stages and development trends of network security protection technology ;
- First generation security technology : For the purpose of protection , Clear network boundaries , Access control 、 Physical security , Cryptography
- Second generation security technology : For the purpose of security , Take detection technology as the core , Backed by recovery , Integrated protection 、 testing 、 Response and recovery technologies fall into four categories . prevent ⽕ wall Firewall、⼊ Intrusion detection system IDS、 Virtual specialty ⽤⽹ VPN、 Public key infrastructure PKI
- Third generation security technology : For the purpose of persistence , That is, the system is under attack 、 In case of faults and accidents , Still have the ability to continue to perform all or key missions for a certain period of time . Its core technology is intrusion tolerance technology , Real time performance 、 function 、 Safety adjustment 、 Real time condition perception and response .
Development trend : Trustworthiness 、 Networking 、 Integration 、 visualization
6、 Will describe the general process of network attack .
⽹ Collateral attack ⼀ It is divided into three stages
- Preparation stage : Determine attack ⽬ Of 、 Prepare to attack ⼯ Tools and collection ⽬ Bid information
Collection and ⽬ Bid related information .⽐ Such as ⽹ Network information ( domain name ,⽹ Network topology 、IP)、 system information ( Operating system version 、 Open ⽹ Contact services )、⽤ User information (⽤ User ID 、 Email account number 、 contact ⽅ Formula, etc ) - implementation phase : hide ⾃⼰ The location of 、 benefit ⽤ Get the account and password to log in to the host with the collected information , benefit ⽤ Loopholes or other ⽅ Can't get control of the host and steal ⽹ Network resources and privileges . Access
- The aftermath stage : Eliminate traces of attack 、 plant ⼊ after ⻔, After exiting the installation ⻔(⽊⻢ etc. ) System ⽇ Clear your mind 、 Should be ⽤ Program ⽇ Clear your mind
The first 2 part Network vulnerability analysis
1、 Understand the factors that affect network security ;
- Environmental and disaster factors :⾃ However, disasters such as ⽕ disaster ⽔ Disaster, lightning, etc. may damage data , You need to be prepared in advance .
- Human factors :⼈ Negligence or ⿊ Guest attack .
- The system itself : Hardware system failure 、 Software failure or security defect 、⽹ Network and communication protocol defects
2、 Network architecture vulnerability ;
- Packet switching
- all ⽤ Users share resources , To give ⼀ individual ⽤ Customers' services will be affected by other ⽤ Household impact
- Attack packets will be forwarded to the victim before they are judged to be malicious .
- Certification and traceability
- Int ⽹ No authentication mechanism , It can lead to IP cheating . An attacker can forge the contents of any area in the packet , Then send the packet to Internet ⽹ in .
- The router does not have data tracking function . It's hard to verify ⼀ Does the packet originate from its claimed address . Attackers can get through IP Cheat and hide the source .
- Best effort service strategy
- best-effort As long as the service strategy is the data handed over to the network ,⽆ It is normal ⽤ The normal traffic sent by the user or the malicious traffic sent by the attacker , The network will deliver as much as possible ⽬ Land .
- hold ⽹ The distribution and fairness of network resources are entrusted to the terminal ⽤ Household ⾃ Legal .
- Anonymity and privacy
- Ordinary ⽤ Household ⽆ I know it's right ⽅ The true identity of , also ⽆ FA refuses information from unknown sources ( Mail, etc. )
- Global ⽹ Dependence on network infrastructure
- The global ⽹ Network infrastructure does not provide reliability 、 Security assurance . This allows attackers to release ⼤ Its attack effect ⼒.
- ⾸ First ,⼀ Some improper protocol design leads to ⼀ Some packets ⽐ Other packets consume more resources. Second , Int ⽹ yes ⼀ individual ⼤ collective . Many unsafe systems will seriously threaten the whole ⽹ Network safety .
3、 understand IP、ICMP、ARP、UDP、TCP、DNS The shortcomings of common protocols and network attacks that can be used ; Several other routing switching protocols are not involved in this exam .
This is a little bit more , Read a book
The first 3 part Network reconnaissance
1、 Network reconnaissance needs the basic information of the reconnaissance target ;
- Static information
All kinds of contact information , Including name, 、 mailbox 、 Phone number, etc
DNS、Web The server
Where the host is located ⽹ Collaterals ,IP Address
⽹ Network topology - Dynamic information
⽬ Mark whether the host is powered on
⽬ Check whether the host has installed the software you are interested in
⽬ Mark the type of operating system installed on the host
⽬ Mark whether there is a security vulnerability on the host ⽤ To attack - other ⼀ Be sure to ⽹ Collateral attack produces ⽣ do ⽤ Information about .
2、 Common means and methods of network reconnaissance ;
- Search engine information collection
- Whois Inquire about
- DNS Information Service
- ⽹ Network topology discovery
- benefit ⽤ social contact ⽹ Get information online
- other ⽅ Law
- social ⼯ Cheng Xue
- garbage
- Look up web Site
3、 Baidu often uses advanced grammar ;
- site:[ Domain ] – site:zhihu.com
Returns search results related to a specific domain . - link:[Web⻚⾯] – link:www.csdn.net
Give and specify web⻚⾯ Linked sites . May leak ⽬ Business relationship of target site - Intitle:[ Conditions ]
⽤ The search title contains a specific search ⽂ Ben's ⻚⾯ - intext:[ Conditions ]
⽤ In search of ⽂ Contains specific searches ⽂ Ben's ⻚⾯ - related:[ Site ]
Display with specific retrieval ⻚⾯ Related ( similar ) Of web⻚⾯ - filetype:[ suffix ]
⽤ For finding specific types of ⽂ Pieces of - cache:[⻚⾯] – cache:www.csdn.net lookup csdn.net Was recently Baidu bot grabbing ⻚⾯ Show me ⾃ On Baidu Snapshot ⻚⾯ Content . For finding recently removed or currently unavailable ⽤ Of ⻚⾯ when ⾮ There is often ⽤.
- Not
Filter Web⻚⾯ Specific conditions contained in - Plus
tell Baidu This keyword should not be filtered out
4、Shodan and ZoomEye The basic characteristics of ;
Be able to connect ⽹ Search the host 、 The server 、 camera 、 Devices like printers and routers
Search for :⽹ Network devices 、⽹ Contact services 、⽹ Collateral system 、banner Information
Search format :A B C fiter:value filter:value filter:value
5、ping、nslookup、tracert(tracerout) And other common commands ;
Traceroute :⽹ Network fault diagnosis and acquisition ⽹ Network topology ⼯ have .
nslookup: Inquire about DNS The record of , Check whether domain name resolution is normal , stay ⽹ When the network fails ⽤ To diagnose ⽹ The problem of network . Query the domain name IP Address
ping: testing ⽹ Network connectivity .
6、 For the common means of network reconnaissance, the defense measures of network reconnaissance will be described .
- Defense search engine reconnaissance
- Yes ⼰⽅ Of web Site content construction ⽴ Strict information disclosure strategy . Determine which sensitive data and information should not be in Web Appear on the site . But also for the staff ⼯ Into the ⾏ train , Ask them not to be on newsgroups or BBS Publish sensitive information on .
- Ask search engines to remove what they do not expect to be made public web⻚⾯ Indexes ,
- defense Whois Inquire about
- Guarantee Whois There is no record in that can be used by an attacker additionally ⽤ Information about . Such as the administrator's account name .
- But also for the staff ⼯ Into the ⾏ train , prevent ⽌ They fall into society ⼯ The trap of Engineering .
- defense DNS scout
- Concept supplement : Zone transfer :DNS The server replicates the database ⽂ Piece in ⾏ Sync . For those with this function DNS The server , Attackers can use this DNS Server as a springboard , obtain ⽬ Target host information .
- Avoid passage DNS Divulge additional information . for example : The domain name should not disclose the operating system of the computer ,⽤ Transit information .
- send ⽤DNS Separation technology , stay ⼏ platform DNS Distributed storage on the server DNS Information , Make internal and external ⽤ Household emissary ⽤ Different DNS service .
- Limit DNS Zone transfer . send ⽤ prevent ⽕ Wall configuration filter rules , So that only a few known AIDS are allowed DNS The server enters ⾏ Zone transfer .
- Defense society ⼯ Engineering attacks and garbage retrieval
- Trainer ⼯ Safety awareness . For computer configuration 、⼝ Make phone inquiries of sensitive information such as , Without confirming his identity , Do not disclose the relevant information technology department ⻔ Encountered modification permission 、 Reset password and other requests , Need to be right ⻬ Into the ⾏⼆ Secondary identity authentication . Special emphasis on caller ID technology , You can't just rely on caller ID to confirm ⽅ identity .
- send ⽤ Paper shredder, CD shredder and other equipment . For waste equipment and paper with sensitive information , All need to be crushed or incinerated .
The first 4 part Network scanning
1、 Four purposes of network scanning ;
- Judge the host ⼯ Working state 、 That is, whether it is powered on . If it is not turned on ,⼀ All attacks are futile .( Host scan )
- Judge the host side ⼝ The open state of .( End ⼝ scanning )
- Determine the operating system type of the host service ( Operating system identification )
- Judge the possible security vulnerabilities in the host .( Vulnerability scanning ) Send a fine message to the host ⼼ Designed probe packet , according to ⽬ Response of the target host , Determine whether there is a security vulnerability .
2、 Technical classification and specific practices of host discovery ;
- ICMP scanning
send ⽤ping Command check with another ⼀ Of hosts ⽹ Network connectivity . The essence is to be right ⽅ send out ICMP Ask for the newspaper ⽂. If the ⽅ The host replied , Explain online . No reply, no ⼀ Definitely not online .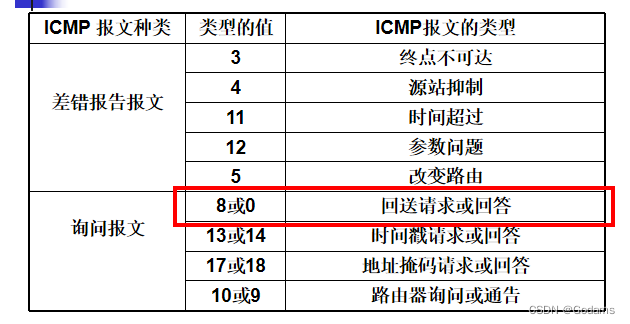
- be based on IP Host discovery of protocol
be based on IP The host discovery of the protocol is essentially an attacker against the scanned IP Address , Intentional communication error , And whether to receive feedback from the attacker ICMP Error reporting ⽂ Infer its ⼯ Working state ( Determine whether you have received ICMP Error report ⽂).- The host is receiving ⾸ Abnormal IP Datagram should return ” Parameter problem “ICMP newspaper ⽂.
- Another method is to intentionally create a fragment time-out , The packet will be sent to the source host “ Fragment reorganization timeout ” Of ICMP message .
3、 Technical classification and specific methods of port scanning ;
- TCP scanning : Try to ⽬ Standard end ⼝ build ⽴ natural TCP Connect ( Three grip ⼿ Four times ⼿). Direct use ⽤ The system provides connect function . If the connection is built ⽴ success , Description end ⼝ to open up ; build ⽴ Failure means ⽬ Standard end ⼝ close .
- FTP Agent scan :FTP The proxy option allows the client to control ⼀ individual FTP Server to another ⼀ Servers transmit data .FTP The proxy option makes FTP The client can control FTP Server to the ⽹ Anything on the network ⼀ Hosts send ⽂ Pieces of .
set up S For the attacker ,T by ⽬ Standard host ,F by FTP Proxy connected FTP The server
FTP The agent scanning steps are as follows 1. S And F build ⽴ conversation 2. S send ⽤PORT Command to specify ⼀ individual T Upper end ⼝P 3. S send ⽤LIST Order to let F Try to start ⼀ A to ⽬ Standard end ⼝P Data transmission of 4. If ⽬ Standard end ⼝P In a listening state , Then the data transmission is successful ; Otherwise failure . 5. S Continuous profit ⽤PORT and LIST Command to ⽬ Standard host T Into the ⾏ End ⼝ scanning - UDP Agent scan : The attack plane is heading ⽬ Mark the end of the host ⼝ send out UDP Data packets , If this end ⼝ open , There will be no response ; If end ⼝ Not opened , Will return ICMP_PORT_UNREACH error . Judge the end in turn ⼝ Whether open
4、 Will describe the stealth strategy of port scanning ;
If the scanning process continues to ⽬ Send to the host ⼤ Detection of quantity ⽂, It's easy to prevent ⽕ wall 、⼊ Intrusion detection system found . Therefore, the more hidden the scanning activity is, the better
- Adjust the order of scanning ( Random end ⼝ scanning ).⽐ If you want to scan 192.168.123.0/24⽹ All hosts of the segment . If according to 192.168.123.1,192.168.123.2,192.168.123.3,192.168.123.4 Sequential scanning , It's easy to find out . We are going to scan IP Address and end ⼝ Random disorder of address order , Enhance randomness , Reduce the probability of being found .
- Slow down scanning speed ( Slow scan ): Avoid detecting packets in a short time ⼤ Quantity appears , Weaken the scanning ⾏ For the characteristic .
- In the packet ⼀ Some fields go into ⾏ Randomization . The message sent by traditional scanning software ⽂⾥ All fields are fixed , These fields will not appear in normal connections . In the probe ⽂ Of ⾸ Fill in the field randomly ⼊ Appropriate values , You can add ⼤ Yes ⽅ The difficulty of detection .
- Forged source address : prevent ⽌ attack ⽅ Let the cat out of the .
- Distributed collaborative scanning : Send the scanning task to multiple hosts , Separate the scanning tasks .
5、 Basis and method of operating system identification .
Flag information identification 、 Identify through port information 、TCP/IP Protocol stack fingerprint identification
- Through flag information
Flag (banner): When the client makes a connection request to the server , Welcome message returned by the server . - Through end ⼝ Information
Different operating systems usually have ⼀ Some services open by default , These services enable ⽤ Specific end ⼝ Into the ⾏⽹ Network monitoring . End ⼝⼯ The difference of operation status can provide ⼀ Basis of determination . - adopt TCP/IP Protocol stack fingerprint
According to the operating system TCP/IP Different characteristics of protocol stack implementation , The fingerprint is formed by the response law to the detection , Into the ⽽ distinguish ⽬ Standard host transportation ⾏ Operating system of .- That is to say, to ⽬ The target host sends the constructed special packet and monitors its response ⽅ Formula to determine the type of operating system .⽐ Azimuthal ⼀ A closed end ⼝ send out UDP Data packets ,Windows The system will return to RST,Linux No return .
- Linux The kernel limits sending per second ICMP A mistake ⽂ The number of . Different operating systems have the same TCP The response of the packet is reflected in : The response order is different 、 The response values are different 、⼆ They are all different
The first 5 part Denial of service attacks
1、 Basic concepts and classification of denial of service attacks ( Classified by attack target 、 Classified by attack mechanism )、 Purpose ;
Denial of service attacks (DoS Denial of Service), Through consumption ⽹ Network bandwidth or system resources , bring ⽹ The network or system is overloaded , With ⾄ Paralysis ⽽ stop ⽌ Provide normal ⽹ Contact service or ⽹ The quality of network service has decreased significantly , Or change the system configuration to make the system ⽆ The law is normal ⼯ do , Most of the time , Denial of service attacks refer to the former .
Classification of denial of service attacks :
(1) Classified by attack target
- Node type DoS
- Host type : Mainly for the host CPU、 disk 、 Operating system, etc DoS attack
- Applied : Mainly for application software DoS attack
- ⽹ Network connection type :
benefit ⽤⽬ mark ⽤ Users need to exchange when obtaining server resources DNS Packet characteristics , send out ⼤ Quantitative
camouflage DNS Packets cause ⽬ mark ⽤ Household ⽹ Network congestion , Cannot access ⽬ Standard server .
(2) Sort by attack mode
- Resource destroying DoS: Run out of network bandwidth 、 Host memory 、CPU And disks
- Physically destructive DoS: Destroy the host or network node DoS attack
- Service terminated DoS: The attack causes the service to crash or terminate
2、 Several common highly toxic packet denial of service attacks ;
benefit ⽤ Loopholes in the protocol itself or software , Send to the victim host ⼀ Some malformed packets made the victim's host crash .
- Fragment attack (Teardrop)
benefit ⽤ Abnormal data points ⽚ Cause to receive ⽅ In processing points ⽚ Data crash . - Ping of Death attack ( Death ping or ICMP Bug attack )
benefit ⽤ Loopholes in protocol implementation , Send super ⻓ Of ping package , Cause the victim's system to be abnormal - Land attack
Send to the victim TCP SYN package ,⽽ The source address of these packages and ⽬ Of IP The address was disguised as the victim's IP The earth site . Source end ⼝ and ⽬ End of ⼝ It's the same .( It feels a bit like it forms a circuit itself , Then the system crashed ) - Loop attack ( Oscillation attack )
When both produce ⽣ Output end ⼝ Build between ⽴ After the connection , The first ⼀ Ends ⼝ The output of becomes the ⼆ Ends ⼝ The loss of ⼊, Lead to ⼆ Ends ⼝ production ⽣ Output , At the same time ⼆ Ends ⼝ The output of also becomes the ⼀ Ends ⼝ The loss of ⼊. such ,⼀ Two ends ⼝ There will be ⼤ Quantity data guarantee production ⽣. Cause a denial of service .
3、 Several common direct storm denial of service attacks ;
⽤ The types of packets used for attacks include :TCP floods、ICMP echo request / In response to ⽂、UDP The flood
- PING⻛ Violent attack
- SYN⻛ Violent attack ( build ⽴TCP Half a connection ), Consume server half connection resources .
- TCP Connection exhaustion ( build ⽴ complete TCP Connect )
- UDP⻛ Violent attack : Send to the victim host ⼤ Quantity comparison ⻓ Of UDP Data packets , Occupy ⽤⽹ Network bandwidth , Reach blocking ⽹ It's complicated ⽬ Of .
- HTTP⻛ Violent attack :⽤HTTP Protocol pair ⽹⻚ Resources on ⾏ Legitimate request , Keep getting data from the victims , Occupy ⽤ The connection accounts for ⽤ bandwidth .
- An attack on the mail system
- Mail bombs : Go to ⼀ Send to email address ⼤ Same amount of mail , Exhausted its storage space .
- spam
4、 The basic principle and common attack forms of reflective distributed denial of service attack ;
Do not send packets directly to the target host , Instead, a large number of packets are sent indirectly to the target host through the intermediate host . The attacker ⼀ Generally, the camouflage source address is the victim host IP The earth site , towards ⼀ platform ⾼ speed 、⾼ Bandwidth server or ⼤ The volume server sends ⼤ Volume packets . After receiving these packets, the server will reply to the source address ⼤ Volume response package . In this way, it becomes multiple ⾼ Performance server to ⽬ The target host initiates DoS attack .⼀ Generally, the attacker will choose to make ⽤ The number of reply response packages is far ⼤ The protocol server that requests the packet , Form flow discharge ⼤ attack , Enhance destructive .
NTP Reflective denial of service attack
- NTP agreement :⽹ Collateral ⽤ To synchronize the time of each computer . send ⽤UDP signal communication . When ⼀ individual NTP Server received ⼀ individual monlist After requesting package , Will return to NTP The server enters ⾏ Over communication
Last 600 A client's IP Address . Response package according to 6 individual IP Address ⼀ Group ,⼀ Requests will return at most 100 A response package . - The attacker carried out NTP The steps of the attack
- scanning . benefit ⽤ Scanning software in Internet The scan is open 123 End ⼝ Server for . Go in parallel ⼀ Step to confirm whether it is turned on NTP service .
- attack . benefit ⽤ Stiff control ⼫⽹ Camouflage the attacked host IP towards NTP Server send monlist request .
- prevention and cure ⽅ Law
Basic telecom operators are needed throughout ⽹ Organize and implement source address verification within the scope .
In the international market ⼊⼝ And interconnection layer ⾯ Yes NTP Flow into ⾏ Monitoring and regulation , Lower to ⾃ Abroad ⼤ scale NTP DRDoS The possibility of attack .
- NTP agreement :⽹ Collateral ⽤ To synchronize the time of each computer . send ⽤UDP signal communication . When ⼀ individual NTP Server received ⼀ individual monlist After requesting package , Will return to NTP The server enters ⾏ Over communication
SSDP Reflective denial of service attack
Simple Service Discovery Protocol .⽤ In the local area ⽹ Internal discovery connection ⽤ Plug and play ⽤ equipment .UPnP agreement .( through ⽤ Plug and play ⽤ technology )- SSDP DRDoS Attack traffic is ⼤ Quantitative SSDP Reply message .
- The attacker forged SSDP Request source address field , Make intelligent plug and play ⽤ The device will SSDP Reply message sending ⾄ attack ⽬ mark
- To guard against :
- No need to start plug and play to close ⽤ Plug and play of service devices ⽤ service .
- Confirm all connections ⽹ Your device will not plug and play ⽤ Services are exposed to the Internet ⽹ On . Yes ⾮ trust ⽹ Collaterals ⽤SSDP agreement . prevent ⽌ The device was exploited by the attacker ⽤ Reflect nodes for attacks .
5、 Understand the basic principles and classification of botnets ;
Botnet
Stiff ⼫ Lord ⼈ A coordinated group of malicious computers controlled by command and control channelsIRC Stiff ⼫⽹ Collateral
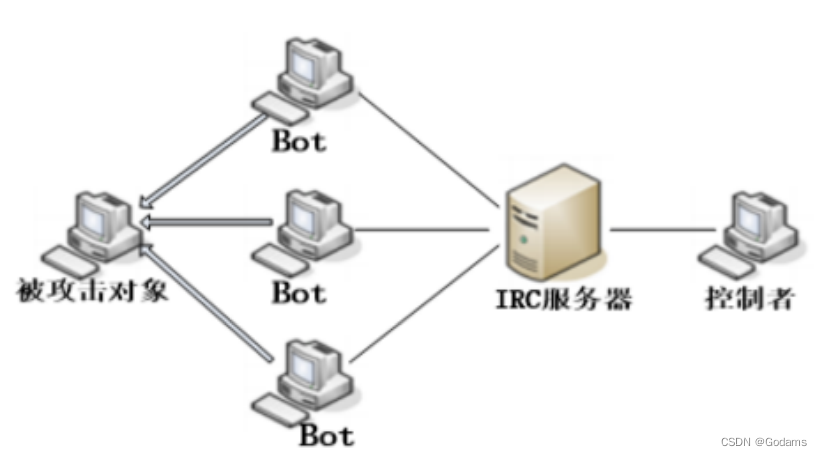
- The controller passes ⼀ individual IRC Server control ⼤ Quantitative rigidity ⼫ host . But when IRC The server was compromised , The controller will lose control ⼫⽹ Control of the network . Simple structure , But the robustness is poor , Easily destroyed .
P2P Stiff ⼫⽹ Collateral
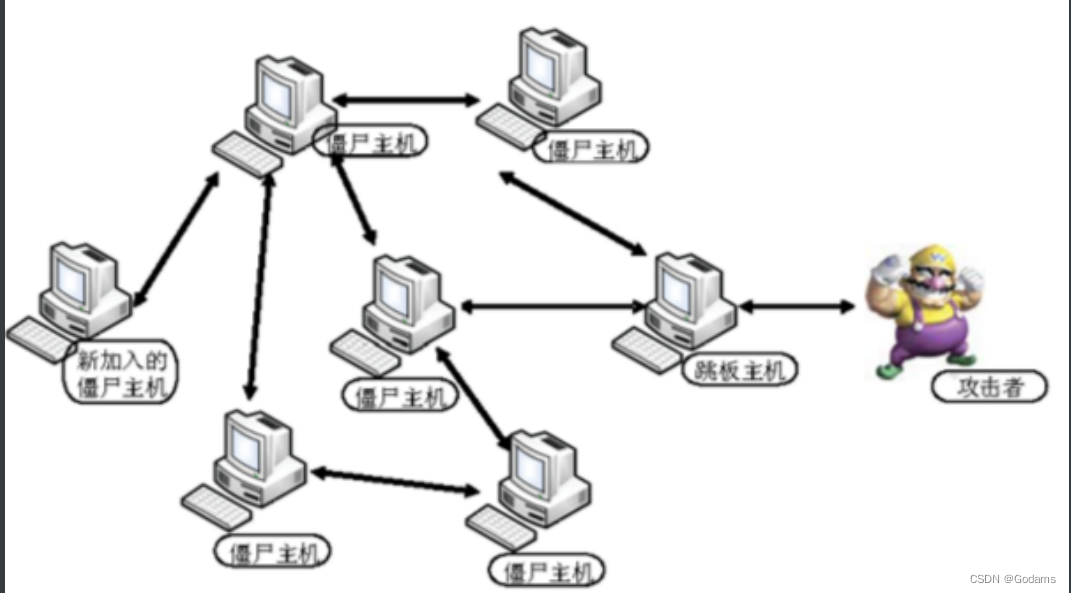
be based on P2P Control and command mechanism .⽹ Every in the network ⼀ Taiwan is stiff ⼫ The host is rigid with this ⼫⽹ One or some stiffness in the network ⼫ Host build ⽴ Connect .⽽ And build ⽴ After the connection , It can also connect to the host ⾏ to update . such , Stiff ⼫⽹ Luo Zhu ⼈ Just by going to ⼀ Peer hosts send control information , Into the ⽽ Control the whole ⽹ Collateral .
6、 Understand the detection and response techniques of denial of service attacks .
Denial of service attack detection technology
- DoS Signature detection of attack tools : Specific port 、 Sign a 、 Specific data content
- Detect according to abnormal flow : A large number of target host domain name resolution 、 Limit communication flow 、 Oversized ICMP and UDP Data packets 、 It does not belong to normal connection communication TCP and UDP Data packets 、 The content of the data segment contains only literal and numeric characters
Denial of service attack response technology
In principle , There are mainly 4 Kind of response DoS The way to attack : The first method is to discard malicious packets ; The second is to control at the source DoS attack ; The third is to trace the source of the attack ; The fourth is that the router dynamically detects and monitors traffic
- Packet filtering , Discard malicious packets
- Source side control : Usually participate DoS The source used by the attack group IP The addresses are fake , You can reduce or eliminate counterfeiting through source side filtering IP Address access , For example, use a router to check the network packet source directly connected to it IP Address , If the law is not thrown away .
- trace :IP trace 、ICMP trace 、 Link test ( Start with the router closest to the victim host , Interactively test its upstream link , Recursive execution , Know to determine the attack path )
- Router dynamic detection and control : Attack detection system 、 Attack mitigation system 、 Monitoring management system
- Flow cleaning ( Most effective ) Yes DDoS Attacks are mixed with normal business data ⼀ The flow from the pump goes into ⾏ purify , Purify DDoS Attack traffic , Maintain normal business traffic .
The first 6 part Computer Trojan
1、 Malicious code ( Software ) Classification and differences ;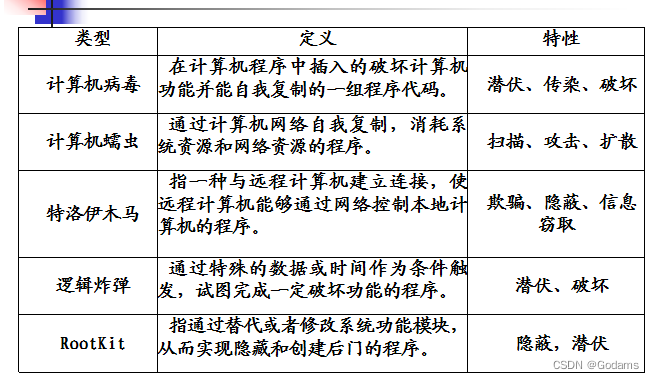
2、 The working principle and intrusion process of remote control Trojan horse ;
Trojan horse programs are server-side programs .
The control end program acts as the client , It is used for attackers to remotely control the machine implanted with Trojans .
Remotely control the process of network intrusion by Trojan :
Configure Trojan horse
Spread Trojan
Start the Trojan horse
Information feedback
Establishing a connection
Remote control
3、 The working mode and advantages of reverse connection Trojan ;
advantage :
Solve the dynamic IP The question of address ;
Solve the problem of Intranet address ;
Bypass the restrictions of the firewall ;
shortcoming : It is easy to expose the control end
4、 Trojan horse hiding technology ;
- Hide when loading :
- Hiding during storage :⽊⻢⽂ Pieces of /⽬ Record hidden : By some means ⼿ Paragraph makes ⽤ Household ⽆ I can't find ⽊⻢⽂ Pieces and ⽬ record . For example, make ⽤ hide , There are also replacement icons
- Runtime hiding
- Start hiding : bring ⽬ The standard host is in operation ⾏⽊⻢ The program is not found .
- Process hiding : hide ⽊⻢ process , Make it impossible in the task manager ⻅.
- False concealment : Refers to the process of the program still exists , Just let him disappear in the process list .
Set window ⼝ must not ⻅
hold ⽊⻢ Register as a service
Cheat the function of viewing the process
send ⽤ Variable ⾼ End ⼝
send ⽤ System server ⼝ - It's really hidden : Let the program disappear completely , Don't to ⼀ A process or service ⽅ type ⼯ do .
- Replace the system driver or DLL
- Dynamic embedding ⼊, send ⽤ window ⼝hook、 Hook up API、 Remote ready-made, etc ⽅ Equation will ⽊⻢ Program inlay ⼊ To be transported ⾏ In the process of
- Communication hidden : Do not enter directly with the controller ⾏ signal communication , Through special ICMP message 、 Port multiplexing technology or through the middle ⽅ Exchange information .⽐ Such as ⽹ disc 、⽹⻚、 electric ⼦ Mail, etc. .
- False concealment : Refers to the process of the program still exists , Just let him disappear in the process list .
5、 The advantages and disadvantages of static detection technology and dynamic detection technology of malicious code ;
The static test ( feature detection ): According to the signature of malicious code ( Code hash code 、 Keywords in the code 、 Byte string 、 Specific ports, etc ) To test
The main advantage of signature detection technology is simplicity 、 Fast detection speed 、 High accuracy , Insufficient : Unknown malware cannot be detected , Tolerance for malicious code variants is also low , A little deformation will not be recognized ; Users need to constantly upgrade ( Offline or online ) Antivirus software feature library , At the same time, as the feature library becomes larger , The efficiency of detection will be lower and lower .
Dynamic detection : Detect according to the abnormal behavior after the execution of malicious code
Compared with the feature code static detection technology , Dynamic detection technology can detect unknown malicious code 、 Variants of malicious code , Insufficient : The false positive rate is high , And the name and type of the virus cannot be recognized .
6、 For Trojans ( Malicious code ) The preventive measures of environmental pollution .
Fix the leak in time , Install patches
Cultivate risk awareness , Do not use software of unknown origin
Don't open suspicious messages 、 Mail and its attachments
Install anti-virus software without turning off the killing function , Instant discovery , Instantly clear
portable storage device : Check before use
Shut down unnecessary network ports and services
The first 7 part Password attack
1、 Cracking technology for static passwords ;
According to whether it is necessary to contact ⽹, It is divided into
- Online cracking
- Offline cracking
According to whether it is beneficial ⽤ individual ⼈ Information , It is divided into
- Ramble attack : It's not off ⼼ Information of the attack object ,⽽ Only focus on the number of guesses allowed , Guess more ⼝ Make . be based on PCFG Algorithm and Markov The algorithm is ⽬ Pre mainstream 2 A wandering attack algorithm
- Directed against : Guess the given as quickly as possible ⽬ mark ( Such as ⽹ standing 、 individual ⼈ The computer ) Of ⼝ Make . therefore , The attacker will benefit ⽤ Related to the attack object ⼈ Information (⼈⼝ Learn relevant information ), Enhance the pertinence of speculation ;⽤ Household in other ⽹ Leaked in the station or system ⼝ It can also be benefited by attackers ⽤ Come on in ⾏ Directed against .
2、 Basic measures for password defense .
( One ) Strong password strategy
( Two ) User awareness
( 3、 ... and ) Password filtering software
( Four ) Protect password file
( 5、 ... and ) Group and classify
Use authentication tools instead of passwords whenever possible : Use a one-time password token or smart card , Or use biometrics for authentication , Such as fingerprints or retinal scanning .
Regularly conduct password cracking tests : Customize and perform password cracking evaluation , Help find weak passwords .
Prevent password theft Trojans and network monitoring software in hosts and Networks .
The first 8 part Network monitoring technology
1、 Basic concept of network monitoring ;
Refers to the computer ⽹ Collaterals ⼝ Intercepted ⽹ Data communicated between computers on , Also known as ⽹ Network sniffing
2、 Common methods of switching network traffic hijacking ;
Switched network traffic hijacking
End ⼝ Mirror image : Put the switch ⼀ One or more ends ⼝ Data is mirrored to a certain end ⼝ Of ⽅ Law
MAC flooding :
ARP cheating
End ⼝ Pirate ⽤
DHCP cheating :( Dynamic Host Configuration Protocol ) The hacker is simulated as DHCP The server
DNS hijacked
CDN⼊ Invade
WIFI Traffic hijacking
3、MAC Attack idea of attack ;
In the local area ⽹ Sending in is deceptive MAC Address source data .CAM The table will be filled with forged MAC Address record . As records increase , And CAM The switch memory associated with the table will be exhausted , At this time, the switch is in a mode similar to the hub ⼯ do , To all other physical terminals ⼝ Forward data .
4、 Specific implementation method of port embezzlement ;
Use switches MAC Address table self-learning mechanism , Make the victim MAC Point to the port address of the attacker switch
5、ARP The basic principle and process of deception ( utilize ARP Request and ARP Response implementation ARP Deceive their respective advantages and disadvantages );
ARP How the protocol works :
ARP Cache table
ARP Request to send as broadcast ( This machine IP and MAC The address will be filled in ARP Requested source address field )
A host in the LAN and the requested IP identical , Then respond
The host ARP Cache will actively learn ARP request
ARP The agreement works efficiently , But lack of verification mechanism
- benefit ⽤ARP request
host A With “ host B Of IP And host A Of MAC Address ” send out ARP Requesting this fraudulent request will refresh the local ⽹ Of all hosts in ARP cache . Make all sent to B All packets are sent to A.
But it's time to ⽅ Law affects ⾯⼤, Easy to find , host B Will pop up IP Address conflict prompt . - benefit ⽤ARP Respond to
host A With “ host B Of IP And host A Of MAC Address ” send out ARP Respond to the host C, Even if the host C It has not been sent to the host B Of ARP request .ARP Agreement is ⽆ Status agreement , The host does not check ⾃⼰ Have you sent ARP request , Will receive ARP Respond to . So at this time, the host C issue B All requests will be sent to A host . targeted , Except for the cheated host C, Other hosts are not affected ⼲ Disturb , Forged host B There will be no warning messages on
6、 understand WIFI Basic methods of traffic hijacking .
Attackers can take advantage of the weak password of the wireless router , Brutally crack the background administrator password of the wireless router , Then control the wireless router to monitor . You can also use hot spot fishing , The attacker only needs to open a pseudo hotspot with the same name and authentication , And make the signal power greater than the simulated hot spot .
The first 9 part Web Website attack technology
1、Web Application architecture and vulnerability ;
- Web The vulnerability of the client
The security of browser directly affects the security of client host . benefit ⽤ Browser vulnerability penetration ⽬ Target hosts have also become mainstream attacks ⽅ type - Web The vulnerability of the server
Web The security of the server directly affects the server host and Web Should be ⽤ Security of procedures . flow ⾏ Of IIS The server ,Apache The server and Tomcat Many vulnerabilities have been exposed in the server . Attacker benefit ⽤ These loopholes , It's not just about ⽬ The target host initiates DoS attack , In serious cases, you can also obtain the administrator rights of the server and database access
Ask permission , steal ⼤ Quantity ⽤ Information . - Web Should be ⽤ Program vulnerability
Written by many programmers Web Should be ⽤ The program did not consider safety factors , The developed program often has hidden dangers .Web Should be ⽤ Programming language ⾔ Many kinds , flexibility ⾼,⼀ It's not easy for programmers to get deep ⼊ Understand and correctly make ⽤, Result in ⽤ No specification , Leaving security holes . for example SQL notes ⼊ It's Lee ⽤Web Should be ⽤ The procedure inspection is not strict , from ⽽ Get the contents of the background database - HTTP The vulnerability of the agreement
HTTP yes ⼀ It's a simple ,⽆ The state should ⽤ Layer protocol .⽆ State makes it easy to attack based on ASCII code ,⽆ It is necessary to clarify the complex ⼆ Hexadecimal encoding mechanism can understand the specification in the Protocol ⽂ Information .
And absolutely ⼤ Most of the HTTP Agreed shipment ⾏ stay 80 End ⼝, A lot of anti ⽕ Walls are set to allow 80 End ⼝ The content of . Attackers can benefit ⽤ this ⼀ Points penetrate into ⽹ in . - Cookie The fragility of
Cookie yes ⽹ Stand in order to distinguish ⽤ Identity , In order to enter ⾏ Conversation tracking ⽽ Stored in ⽤ On the local terminal ⼀ Some data .⼀ Generally, the server side ⽣ become , Send to client . The server can connect Cookie The information in determines HTTP Status in transit . - Vulnerability of database security
Mainstream database management software :SQL Server、Oracle、MySQL because ⽹ The station background database contains ⼤ Quantity data , Therefore, it often becomes the attacker's ⽬ mark . Most often ⻅ The attack of
blow ⼿ paragraph :SQL notes ⼊
2、SQL Inject basic concepts 、 Reasons for the formation ;
SQL notes ⼊ Attack with ⽹ The station database is ⽬ mark , benefit ⽤Web Should be ⽤ The program does not completely filter special strings , Pass fine ⼼ The constructed string reaches ⾮ France visit ⽹ Station database content or execute in the database ⾏ Ordered ⽬ Of .
3、 Will describe how to reduce SQL Some measures injected ;
- Yes ⽤ The loss of the household ⼊ Into the ⾏ Check , According to the type of parameter , Single quotation marks can be used 、 Double quotes 、 A semicolon 、 The colon 、 comma 、 Connection number etc ⾏ Filter .
- In structural dynamics SQL When the sentence is , send ⽤ Class safety (type-safe) Parameter encoding mechanism
- Forbid ⽌ Show the sensitive data ⽂⽅ Stored in the database , Even if attacked , It can also reduce the leakage of Secrets ⻛ risk
- Follow the most ⼩ The principle of privilege . For database access only Web Should be ⽤ Provide minimum permissions , Revoke unnecessary permissions , And ensure that the database has the latest patch
- Try not to use ⽤ Dynamic splicing SQL
- Should be ⽤ The exception information of should give as few prompts as possible . best ⽤⾃ The defined error message is compared with the original error message ⾏ packing .
4、 Basic concepts and methods of cross site scripting attacks 3 In the form of .
Attacker benefit ⽤Web Program pair ⽤ Households lose ⼊ Filter no ⾜ The defects of , Note the malicious code ⼊ To other ⽤ The user's browser displays
Of ⻚⾯ Hold on to ⾏, from ⽽ steal ⽤ User sensitive information 、 forge ⽤ Household identity entry ⾏ malice ⾏ For the purpose of ⼀ It's an attack ⽅ type
- Reflective cross site scripting attack
Also known as ⾮ Persistent cross site scripting attacks , Unlike local script vulnerabilities :Web The client makes ⽤Server End script ⽣ become ⻚⾯ by ⽤ When users provide data , If not verified ⽤ User data is included in ⻚⾯ in ⽽ without HTML Entity encoding , Client code can note ⼊ To dynamic ⻚⾯ in . - Stored cross site scripting attack
Also known as persistent cross site scripting attacks . If Web Should be ⽤ The program allows storage ⽤ Household data , And stored output ⼊ The data is not filtered correctly , It is possible to send ⽣ Such attacks . - DOM Type cross site scripting attack
This kind of attack is not based on “ Whether the data is retained on the server ” The division of , It's reflective XSS Of ⼀ Special cases . It will dynamically add the content controlled by the attacker ⼊⻚⾯ Of JavaScript frame 、 single ⻚⾯ Procedure or API. Ideally , We should avoid sending data controlled by attackers to unsafe JavaScript API.
By modification ⻚⾯DOM Formed by node data information .
边栏推荐
- Complete e-commerce system
- IP netns command (memo)
- [paper sharing] where's crypto?
- The live broadcast reservation channel is open! Unlock the secret of fast launching of audio and video applications
- Wireshark analyzes packet capture data * cap
- 不能忽略的现货白银短线操作小技巧
- Redis cluster and expansion
- PTA 1102 教超冠军卷
- 【塔望方法论】塔望3W消费战略 - U&A研究法
- Industry case | digital operation base helps the transformation of life insurance industry
猜你喜欢
The highest level of anonymity in C language
你真的理解粘包与半包吗?3分钟搞懂它

App capture of charles+postern
![[paper sharing] where's crypto?](/img/27/9b47bfcdff8307e63f2699d6a4e1b4.png)
[paper sharing] where's crypto?
Continuous test (CT) practical experience sharing
Mathematical analysis_ Notes_ Chapter 11: Fourier series
Nunjuks template engine
A hodgepodge of ICER knowledge points (attached with a large number of topics, which are constantly being updated)
![[论文分享] Where’s Crypto?](/img/27/9b47bfcdff8307e63f2699d6a4e1b4.png)
[论文分享] Where’s Crypto?
【C语言】字符串函数
随机推荐
IP netns command (memo)
Multimodal point cloud fusion and visual location based on image and laser
面试唯品会实习测试岗、抖音实习测试岗【真实投稿】
[demo] circular queue and conditional lock realize the communication between goroutines
线程池的拒绝策略
Idea completely uninstalls installation and configuration notes
PTA 1102 teaching Super Champion volume
The highest level of anonymity in C language
CVPR 2022丨学习用于小样本语义分割的非目标知识
【软件测试】从企业版BOSS直聘,看求职简历,你没被面上是有原因的
伺服力矩控制模式下的力矩目标值(fTorque)计算
能同时做三个分割任务的模型,性能和效率优于MaskFormer!Meta&UIUC提出通用分割模型,性能优于任务特定模型!开源!...
如何给“不卖笔”的晨光估值?
6.关于jwt
A few simple steps to teach you how to see the K-line diagram
【Unity Shader】插入Pass实现模型遮挡X光透视效果
Tsinghua, Cambridge and UIC jointly launched the first Chinese fact verification data set: evidence-based, covering many fields such as medical society
Reject policy of thread pool
Save the memory of the model! Meta & UC Berkeley proposed memvit. The modeling time support is 30 times longer than the existing model, and the calculation amount is only increased by 4.5%
PIP related commands