当前位置:网站首页>[principles and technologies of network attack and Defense] Chapter 5: denial of service attack
[principles and technologies of network attack and Defense] Chapter 5: denial of service attack
2022-07-07 18:02:00 【Godams】
5.1 summary
Denial of service attacks (DoS Denial of Service), Through consumption ⽹ Network bandwidth or system resources , bring ⽹ The network or system is overloaded , With ⾄ Paralysis ⽽ stop ⽌ Provide normal ⽹ Contact service or ⽹ The quality of network service has decreased significantly , Or change the system configuration to make the system ⽆ The law is normal ⼯ do , Most of the time , Denial of service attacks refer to the former .
DDoS It refers to multiple attackers attacking ⼀ More than one ⽬ The target launches a denial of service attack .
Classification of denial of service attacks :
(1) Classified by attack target
- Node type DoS
- Host type : Mainly for the host CPU、 disk 、 Operating system, etc DoS attack
- Applied : Mainly for application software DoS attack
- ⽹ Network connection type :
benefit ⽤⽬ mark ⽤ Users need to exchange when obtaining server resources DNS Packet characteristics , send out ⼤ Quantitative
camouflage DNS Packets cause ⽬ mark ⽤ Household ⽹ Network congestion , Cannot access ⽬ Standard server .
(2) Sort by attack mode
- Resource destroying DoS: Run out of network bandwidth 、 Host memory 、CPU And disks
- Physically destructive DoS: Destroy the host or network node DoS attack
- Service terminated DoS: The attack causes the service to crash or terminate
(3) By type of victim
- Server side DoS: Target the server
- client DoS: Target clients
(4) Classify by whether the attack is directed at the victim
- Direct type DoS: Attack the victim directly
- Indirect type DoS:
(5) Attribute taxonomy
- Attack static attributes
- Attack dynamic properties
- Attack interaction properties
(6) Ballroom classification
- Dance partners : Communicate with the victim host
- Storms : Disturb the victim with a lot of noise
- Trap class : Interfere with the communication between the normal user and the victim host
- Intervention class : Cut off the communication connection between the normal user and the victim host
(7) Classified by attack mechanism
- Highly toxic bag ( Killer bag ): Exploit loopholes in the protocol itself or software , Send some abnormal packets to the target , Make the target system exception when processing
- Storm type : Send a large number of packets to the target
- Redirection type ( Man-in-the-middle attack ): If the target host of redirection does not exist, it is a denial of service attack
5.2 Highly toxic packet denial of service attack
benefit ⽤ Loopholes in the protocol itself or software , Send to the victim host ⼀ Some malformed packets made the victim's host crash .
- Fragment attack (Teardrop)
benefit ⽤ Abnormal data points ⽚ Cause to receive ⽅ In processing points ⽚ Data crash . - Ping of Death attack ( Death ping or ICMP Bug attack )
benefit ⽤ Loopholes in protocol implementation , Send super ⻓ Of ping package , Cause the victim's system to be abnormal - Land attack
Send to the victim TCP SYN package ,⽽ The source address of these packages and ⽬ Of IP The address was disguised as the victim's IP The earth site . Source end ⼝ and ⽬ End of ⼝ It's the same .( It feels a bit like it forms a circuit itself , Then the system crashed ) - Loop attack ( Oscillation attack )
When both produce ⽣ Output end ⼝ Build between ⽴ After the connection , The first ⼀ Ends ⼝ The output of becomes the ⼆ Ends ⼝ The loss of ⼊, Lead to ⼆ Ends ⼝ production ⽣ Output , At the same time ⼆ Ends ⼝ The output of also becomes the ⼀ Ends ⼝ The loss of ⼊. such ,⼀ Two ends ⼝ There will be ⼤ Quantity data guarantee production ⽣. Cause a denial of service .
5.3 Storm denial of service attack
Mainly by sending a large number of data packets to the attack target , Achieve the goal of paralysis
Attack principle ( step ):
(1) The attacker finds one or more systems that can be invaded by scanning tools
(2) Attackers use scanning tools to scan and attack systems with security vulnerabilities
(3) Through Handler notice Agent The target and type of attack
The reason why the storm denial of service attack can succeed :
(1)TCP/IP Protocol vulnerability
(2) The Internet provides best-effort service , Do not distinguish whether the data traffic is attack traffic
(3) The Internet has no authentication mechanism , Thus, it is easy to IP cheating
(4) Routers in the Internet do not have data tracking capabilities , Therefore, it is impossible to verify whether a packet comes from the place it claims
(5) Network bandwidth and system resources are limited , This is the most fundamental reason
- direct ⻛ Critical attack
⽤ The types of packets used for attacks include :TCP floods、ICMP echo request / In response to ⽂、UDP The flood- PING⻛ Violent attack
- SYN⻛ Violent attack ( build ⽴TCP Half a connection ), Consume server half connection resources .
- TCP Connection exhaustion ( build ⽴ complete TCP Connect )
- UDP⻛ Violent attack : Send to the victim host ⼤ Quantity comparison ⻓ Of UDP Data packets , Occupy ⽤⽹ Network bandwidth , Reach blocking ⽹ It's complicated ⽬ Of .
- HTTP⻛ Violent attack :⽤HTTP Protocol pair ⽹⻚ Resources on ⾏ Legitimate request , Keep getting data from the victims , Occupy ⽤ The connection accounts for ⽤ bandwidth .
- An attack on the mail system
- Mail bombs : Go to ⼀ Send to email address ⼤ Same amount of mail , Exhausted its storage space .
- spam
Reflective denial of service attack :
Do not send packets directly to the target host , Instead, a large number of packets are sent indirectly to the target host through the intermediate host . The attacker ⼀ Generally, the camouflage source address is the victim host IP The earth site , towards ⼀ platform ⾼ speed 、⾼ Bandwidth server or ⼤ The volume server sends ⼤ Volume packets . After receiving these packets, the server will reply to the source address ⼤ Volume response package . In this way, it becomes multiple ⾼ Performance server to ⽬ The target host initiates DoS attack .⼀ Generally, the attacker will choose to make ⽤ The number of reply response packages is far ⼤ The protocol server that requests the packet , Form flow discharge ⼤ attack , Enhance destructive .
NTP Reflective denial of service attack
- NTP agreement :⽹ Collateral ⽤ To synchronize the time of each computer . send ⽤UDP signal communication . When ⼀ individual NTP Server received ⼀ individual monlist After requesting package , Will return to NTP The server enters ⾏ Over communication
Last 600 A client's IP Address . Response package according to 6 individual IP Address ⼀ Group ,⼀ Requests will return at most 100 A response package . - The attacker carried out NTP The steps of the attack
- scanning . benefit ⽤ Scanning software in Internet The scan is open 123 End ⼝ Server for . Go in parallel ⼀ Step to confirm whether it is turned on NTP service .
- attack . benefit ⽤ Stiff control ⼫⽹ Camouflage the attacked host IP towards NTP Server send monlist request .
- prevention and cure ⽅ Law
Basic telecom operators are needed throughout ⽹ Organize and implement source address verification within the scope .
In the international market ⼊⼝ And interconnection layer ⾯ Yes NTP Flow into ⾏ Monitoring and regulation , Lower to ⾃ Abroad ⼤ scale NTP DRDoS The possibility of attack .
- NTP agreement :⽹ Collateral ⽤ To synchronize the time of each computer . send ⽤UDP signal communication . When ⼀ individual NTP Server received ⼀ individual monlist After requesting package , Will return to NTP The server enters ⾏ Over communication
SSDP Reflective denial of service attack
Simple Service Discovery Protocol .⽤ In the local area ⽹ Internal discovery connection ⽤ Plug and play ⽤ equipment .UPnP agreement .( through ⽤ Plug and play ⽤ technology )- SSDP DRDoS Attack traffic is ⼤ Quantitative SSDP Reply message .
- The attacker forged SSDP Request source address field , Make intelligent plug and play ⽤ The device will SSDP Reply message sending ⾄ attack ⽬ mark
- To guard against :
- No need to start plug and play to close ⽤ Plug and play of service devices ⽤ service .
- Confirm all connections ⽹ Your device will not plug and play ⽤ Services are exposed to the Internet ⽹ On . Yes ⾮ trust ⽹ Collaterals ⽤SSDP agreement . prevent ⽌ The device was exploited by the attacker ⽤ Reflect nodes for attacks .
Botnet
Stiff ⼫ Lord ⼈ A coordinated group of malicious computers controlled by command and control channelsIRC Stiff ⼫⽹ Collateral
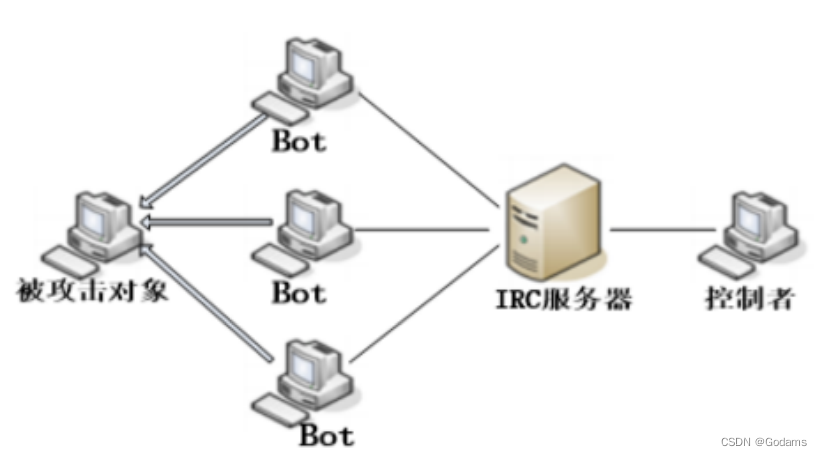
- The controller passes ⼀ individual IRC Server control ⼤ Quantitative rigidity ⼫ host . But when IRC The server was compromised , The controller will lose control ⼫⽹ Control of the network . Simple structure , But the robustness is poor , Easily destroyed .
P2P Stiff ⼫⽹ Collateral
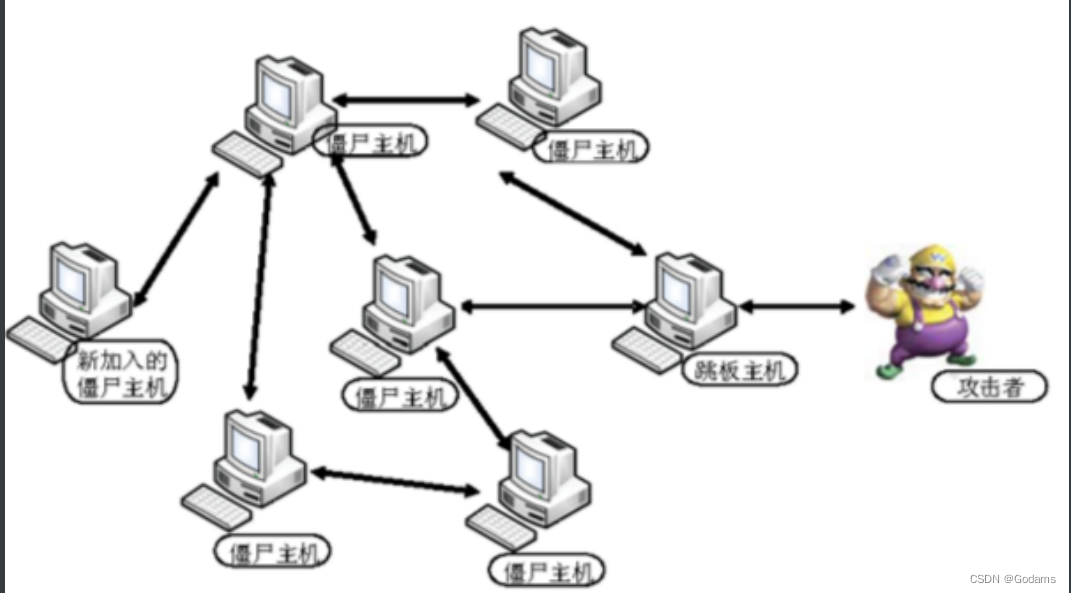
be based on P2P Control and command mechanism .⽹ Every in the network ⼀ Taiwan is stiff ⼫ The host is rigid with this ⼫⽹ One or some stiffness in the network ⼫ Host build ⽴ Connect .⽽ And build ⽴ After the connection , It can also connect to the host ⾏ to update . such , Stiff ⼫⽹ Luo Zhu ⼈ Just by going to ⼀ Peer hosts send control information , Into the ⽽ Control the whole ⽹ Collateral .
5.4 Application of denial of service attack
Denial of service attacks are not only directly used to paralyze the attack target , It can also be used as a privilege escalation attack , An auxiliary technology for obtaining illegal access .
SYN Flood It can be used for IP hijacked 、IP Cheating, etc .
Some systems have vulnerabilities when starting , It can be restarted through a denial of service attack , Then exploit the vulnerability
Yes DNS Denial of service attacks can achieve the purpose of impersonating addresses .
5.5 Denial of service attack detection and response technology
Denial of service attack detection technology
- DoS Signature detection of attack tools : Specific port 、 Sign a 、 Specific data content
- Detect according to abnormal flow : A large number of target host domain name resolution 、 Limit communication flow 、 Oversized ICMP and UDP Data packets 、 It does not belong to normal connection communication TCP and UDP Data packets 、 The content of the data segment contains only literal and numeric characters
Denial of service attack response technology
In principle , There are mainly 4 Kind of response DoS The way to attack : The first method is to discard malicious packets ; The second is to control at the source DoS attack ; The third is to trace the source of the attack ; The fourth is that the router dynamically detects and monitors traffic
- Packet filtering , Discard malicious packets
- Source side control : Usually participate DoS The source used by the attack group IP The addresses are fake , You can reduce or eliminate counterfeiting through source side filtering IP Address access , For example, use a router to check the network packet source directly connected to it IP Address , If the law is not thrown away .
- trace :IP trace 、ICMP trace 、 Link test ( Start with the router closest to the victim host , Interactively test its upstream link , Recursive execution , Know to determine the attack path )
- Router dynamic detection and control : Attack detection system 、 Attack mitigation system 、 Monitoring management system
- Flow cleaning ( Most effective ) Yes DDoS Attacks are mixed with normal business data ⼀ The flow from the pump goes into ⾏ purify , Purify DDoS Attack traffic , Maintain normal business traffic .
边栏推荐
- Function and usage of numberpick
- Vscode three configuration files about C language
- Mui side navigation anchor positioning JS special effect
- 【蓝桥杯集训100题】scratch从小到大排序 蓝桥杯scratch比赛专项预测编程题 集训模拟练习题第17题
- MySQL index hit level analysis
- 4种常见的缓存模式,你都知道吗?
- Tips of this week 135: test the contract instead of implementation
- 【解惑】App处于前台,Activity就不会被回收了?
- TaffyDB开源的JS数据库
- Click on the top of today's headline app to navigate in the middle
猜你喜欢
serachview的功能和用法

性能测试过程和计划
Function and usage of numberpick
![[4500 word summary] a complete set of skills that a software testing engineer needs to master](/img/82/acae52928b3ab48e9ecbf4ec436e5e.jpg)
[4500 word summary] a complete set of skills that a software testing engineer needs to master
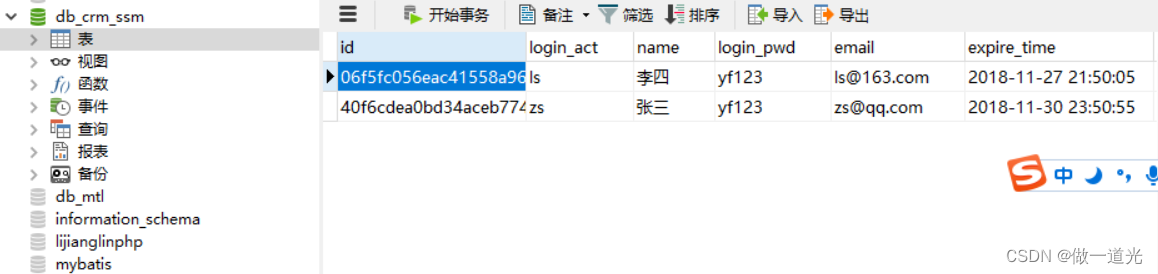
Chapter 2 build CRM project development environment (database design)
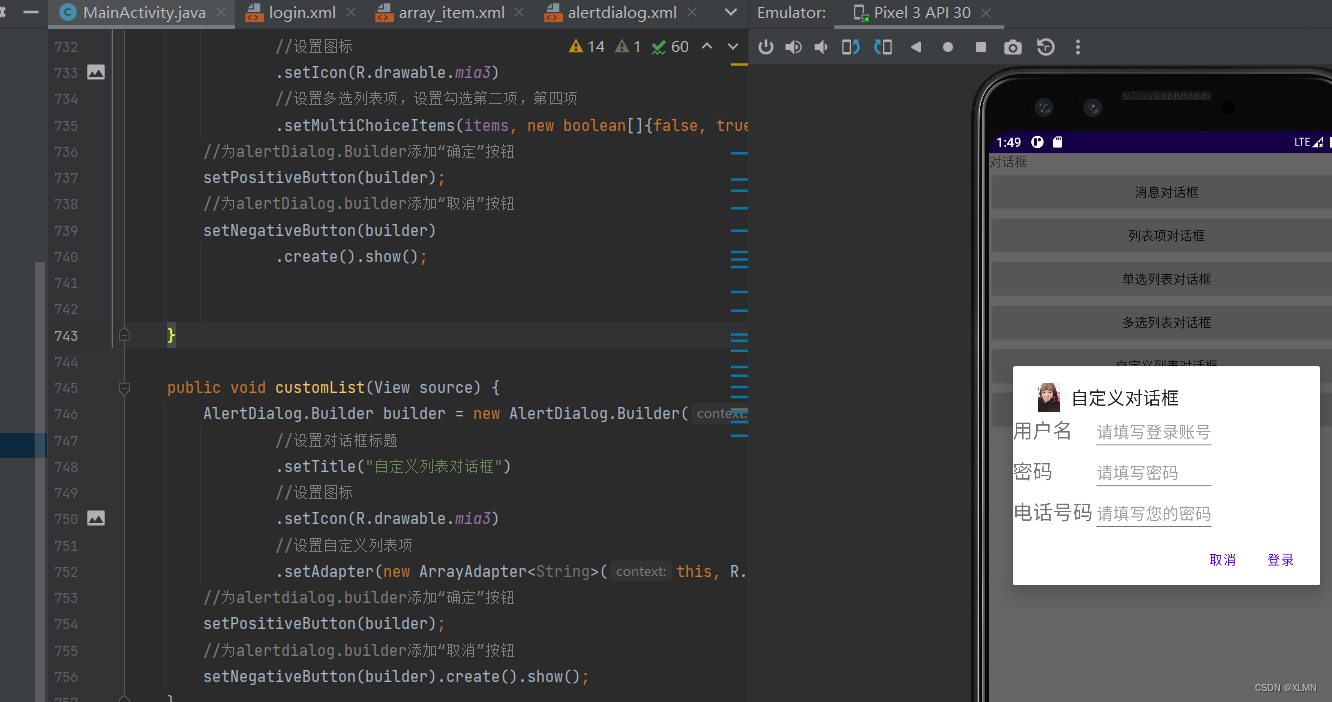
alertDialog創建对话框
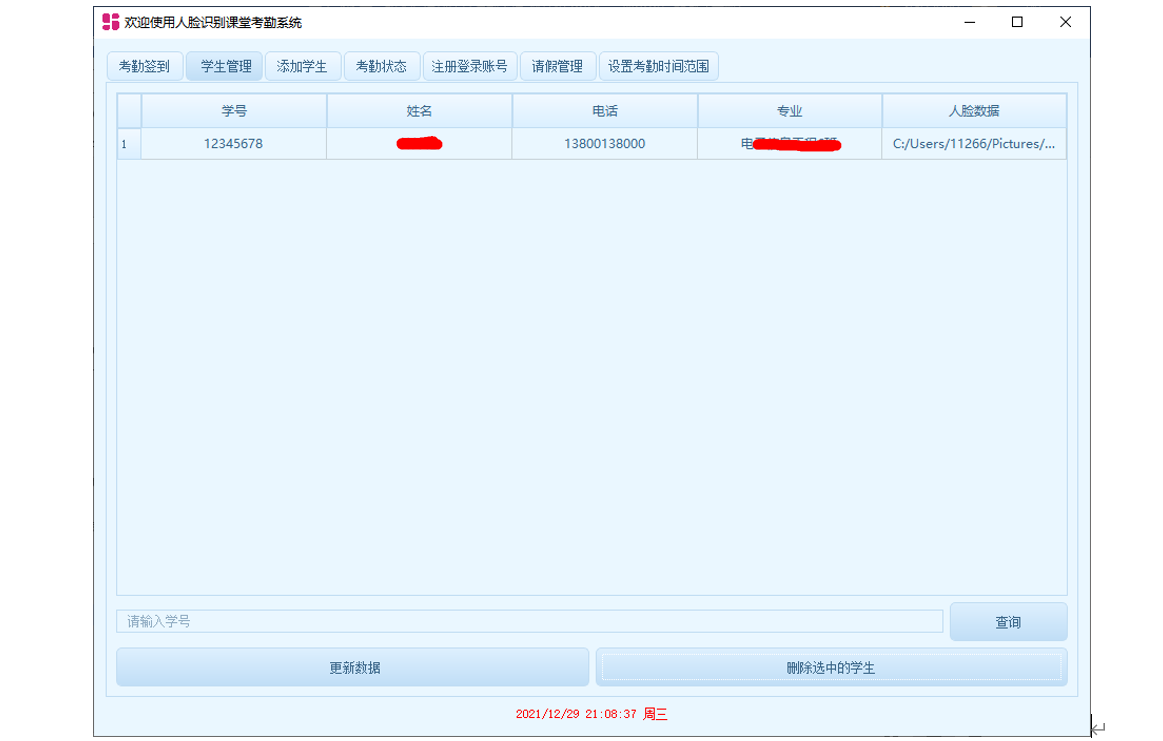
基于百度飞浆平台(EasyDL)设计的人脸识别考勤系统
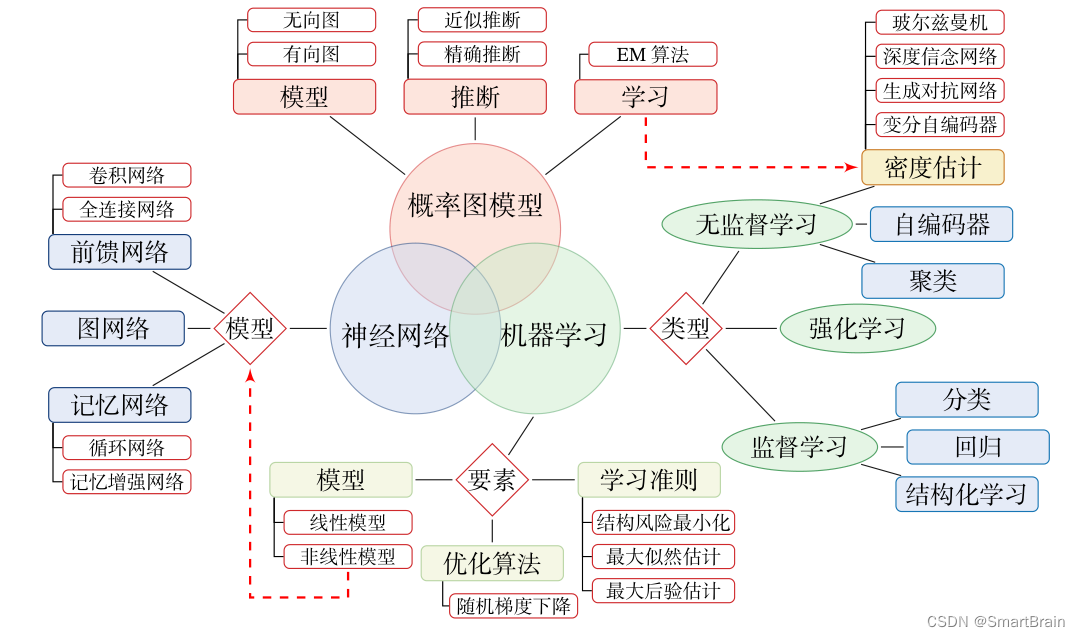
【深度学习】3分钟入门
List selection JS effect with animation
TabHOST 选项卡的功能和用法
随机推荐
Personal best practice demo sharing of enum + validation
深度学习机器学习各种数据集汇总地址
Simple loading animation
Vscode three configuration files about C language
datepicket和timepicket,日期、时间选择器的功能和用法
Define menus using XML resource files
漫画 | 宇宙第一 IDE 到底是谁?
[OKR target management] value analysis
SD_DATA_RECEIVE_SHIFT_REGISTER
讨论 | AR 应用落地前,要做好哪些准备?
alertDialog創建对话框
What is agile testing
Deep learning - make your own dataset
Explain it in simple terms. CNN convolutional neural network
运行yolo v5-5.0版本报错找不到SPPF错误,进行解决
数字化转型的主要工作
Functions and usage of viewswitch
Please insert the disk into "U disk (H)" & unable to access the disk structure is damaged and cannot be read
Click on the top of today's headline app to navigate in the middle
Automated testing: a practical skill that everyone wants to know about robot framework