当前位置:网站首页>51 independent key basic experiment
51 independent key basic experiment
2022-07-05 03:07:00 【fifteen thousand four hundred and two】
Experimental principle :
Method of detecting keys :
Keyboard circuit diagram :
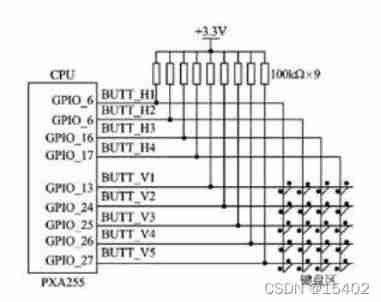
( One ) Row and column scanning ( The code is more complex )
First enter a column as 0, Others are 1( Determination of column coordinates ), Take turns to detect whether there is output in each row 0( Determination of row coordinates )
Then enter the next column in turn as 0, The rest are listed as 1, All keys can be detected after all columns are completed .
( Two ) Line reversal method
Place column line ( Output line ) All for 0, At this time, the line ( Input line ) If any output is 0 Then a key in this line is pressed .
Setting line ( Output line ) All for 0, At this time, the line ( Input line ) If any output is 0 Then a key in this column is pressed .
Experimental code :
#include "reg52.h"
typedef unsigned char u8;
typedef unsigned int u16;
void delay_10us(u16 ten_us); // The time delay function
u8 key_matrix_ranks_scan(void);
u8 key_matrix_filp_scan(void);
#define KEY_MATRIX_PORT P1
#define SMG_PORT P0
u8 gsmg_code[17]={0x3f,0x06,0x5b,0x4f,0x66,0x6d,0x7d,0x07,
0x7f,0x6f,0x77,0x7c,0x39,0x5e,0x79,0x71};
void main() // Press the key S1-S16 Corresponding LED Wait for it to light up 0-F
{
u8 key=0;
while(1)
{
key=key_matrix_filp_scan();
if(key!=0)
SMG_PORT=~gsmg_code[key-1]; // The above array is a common Yin code , Take the inverse to get the common Yang code
}
}
void delay_10us(u16 ten_us)
{
while(ten_us--);
}
u8 key_matrix_filp_scan(void) // Line reversal scanning
{
u8 key_value=0;
KEY_MATRIX_PORT=0x0f; // Column scan
if(KEY_MATRIX_PORT!=0x0f)
{
delay_10us(1000); // Desquamation
if(KEY_MATRIX_PORT!=0x0f)
{
switch(KEY_MATRIX_PORT)
{
case 0x07:key_value=1;break;
case 0x0b:key_value=2;break;
case 0x0d:key_value=3;break;
case 0x0e:key_value=4;break;
}
KEY_MATRIX_PORT=0xf0; // Line scan
switch(KEY_MATRIX_PORT)
{
case 0x70:key_value=key_value;break;
case 0xb0:key_value=key_value+4;break;
case 0xd0:key_value=key_value+8;break;
case 0xe0:key_value=key_value+12;break;
}
while(KEY_MATRIX_PORT!=0xf0);
}
}else
key_value=0; // There is no key press return 0
return key_value; // Return to key number
}
u8 key_matrix_ranks_scan(void) // Determinant scan
{
u8 key_value=0;
KEY_MATRIX_PORT=0xf7; // Low level of the first column
if(KEY_MATRIX_PORT!=0xf7)
{
delay_10us(1000);
switch(KEY_MATRIX_PORT)
{
case 0x77:key_value=1;break;
case 0xb7:key_value=5;break;
case 0xd7:key_value=9;break;
case 0xe7:key_value=13;break;
}
}
while(KEY_MATRIX_PORT!=0xf7); // Wait for the key to release
KEY_MATRIX_PORT=0xfb;
if(KEY_MATRIX_PORT!=0xfb)
{
delay_10us(1000);
switch(KEY_MATRIX_PORT)
{
case 0x7b:key_value=2;break;
case 0xbb:key_value=6;break;
case 0xdb:key_value=10;break;
case 0xeb:key_value=14;break;
}
}
while(KEY_MATRIX_PORT!=0xfb);
KEY_MATRIX_PORT=0xfd;
if(KEY_MATRIX_PORT!=0xfd)
{
delay_10us(1000);
switch(KEY_MATRIX_PORT)
{
case 0x7d:key_value=3;break;
case 0xbd:key_value=7;break;
case 0xdd:key_value=11;break;
case 0xed:key_value=15;break;
}
}
while(KEY_MATRIX_PORT!=0xfd);
KEY_MATRIX_PORT=0xfe;
if(KEY_MATRIX_PORT!=0xfe)
{
delay_10us(1000);
switch(KEY_MATRIX_PORT)
{
case 0x7e:key_value=4;break;
case 0xbe:key_value=8;break;
case 0xde:key_value=12;break;
case 0xee:key_value=16;break;
}
}
while(KEY_MATRIX_PORT!=0xfe);
return key_value;
}
experimental result :
In line with expectations , When the keyboard is pressed S1-S16 The corresponding nixie tube is on 0-F character .
边栏推荐
- Returns the lowest common ancestor of two nodes in a binary tree
- The latest blind box mall, which has been repaired very popular these days, has complete open source operation source code
- Watch the online press conference of tdengine community heroes and listen to TD hero talk about the legend of developers
- Design and practice of kubernetes cluster and application monitoring scheme
- Class inheritance in C #
- Avoid material "minefields"! Play with super high conversion rate
- Zabbix
- Simple use of devtools
- D3js notes
- Ask, does this ADB MySQL support sqlserver?
猜你喜欢
单项框 复选框
Sqoop command
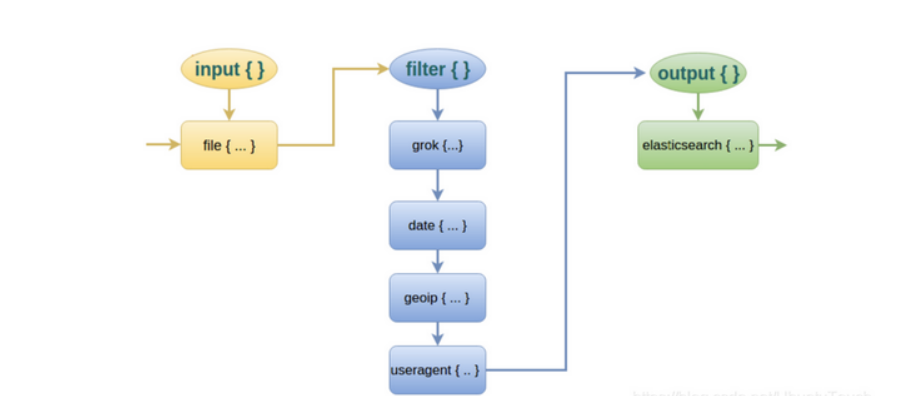
ELFK部署
2. Common request methods
Voice chip wt2003h4 B008 single chip to realize the quick design of intelligent doorbell scheme
Yyds dry goods inventory intelligent fan based on CC2530 design
![[200 opencv routines] 99 Modified alpha mean filter](/img/df/1b7beb6746f416198fc405249852f8.jpg)
[200 opencv routines] 99 Modified alpha mean filter
SQL injection exercise -- sqli Labs
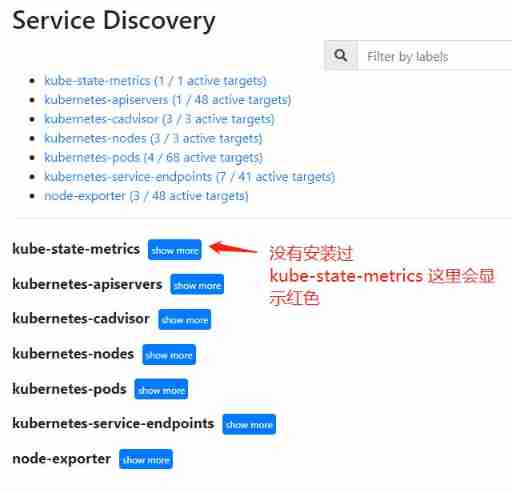
Design and practice of kubernetes cluster and application monitoring scheme
【LeetCode】404. Sum of left leaves (2 brushes of wrong questions)
随机推荐
Character painting, I use characters to draw a Bing Dwen Dwen
SQL performance optimization skills
Anchor free series network yolox source code line by line explanation Part 2 (a total of 10, ensure to explain line by line, after reading, you can change the network at will, not just as a participan
Use of kubesphere configuration set (configmap)
Avoid material "minefields"! Play with super high conversion rate
Elfk deployment
GFS分布式文件系统
The latest blind box mall, which has been repaired very popular these days, has complete open source operation source code
Azkaban安装部署
Design of KTV intelligent dimming system based on MCU
The database and recharge are gone
Cut! 39 year old Ali P9, saved 150million
Design and implementation of community hospital information system
問下,這個ADB mysql支持sqlserver嗎?
The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety
ELFK部署
This + closure + scope interview question
Accuracy problem and solution of BigDecimal
Logstash、Fluentd、Fluent Bit、Vector? How to choose the appropriate open source log collector
The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety