当前位置:网站首页>File upload vulnerability - upload labs (1~2)
File upload vulnerability - upload labs (1~2)
2022-07-07 12:24:00 【hcjtn】
File upload vulnerability ——upload-labs(1~2)
The user uploaded a pointing script file , And through this script, you get the ability to execute server-side commands
In everyday life , We often upload various files , But if there is no restriction on the upload type or the restriction is not strict , An attacker may upload an executable file or web script ( Cause file upload vulnerability ), Cause the website to be controlled or even fall
Harm caused by file upload vulnerability :
- Make hackers hang black chains on your website
- Hang a malicious Trojan ( Automatically pop up advertisements , Brush Click ) Or mining
- Cause file data leakage
The premise of file upload vulnerability
- The website upload function can be used normally
- File types allow uploading such as :php asp In a word, the Trojan horse can enter the interior
- The upload path can be determined
- Files can be accessed , Can be executed or included
Therefore, we can start from the following three points to prevent loopholes
such as :
According to the second point, we can prohibit users from uploading php asp that will do ,
for instance , If users want to upload avatars , We can only let users upload jpg png gif jpeg The format of ( White list ) Filter at the front , Check the format of user's Avatar
We should try to check in advance , The workload of the back-end can be greatly reduced
Upload vulnerability basic process :
- Whether the pictures can be uploaded normally
- Whether the uploaded content of the picture is infected ( Content substitution )
- Whether the uploaded domain name is the target server ( If not , Judge whether the image server parses php、asp、aspx、jsp、cfm、shtml etc. )
- Whether the uploaded directory supports parsing php、asp、aspx、jsp、pht、phtml etc.
- Judge black and white list verification
With upload-labs-1 For example
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-4N6R297m-1643720447610)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20220201192714673.png)]](/img/41/635fe5f1f75e9f4f22b656390d236e.jpg)
To upload pictures , Found upload successful
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-ao2WoYr8-1643720447611)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20220201192751583.png)]](/img/4b/623159ee8c415a0f3c39d248dcad05.jpg)
Upload shell Find out :![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-i1BhKt45-1643720447611)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20220201192946481.png)]](/img/ac/63f5c99d397dbadd70ca29709cdf5a.jpg)
Found a white list , So from the front we know , It is very likely that there is a filter at the front end , Let's check :
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-1SIsmpDw-1643720447612)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20220201194030034.png)]](/img/88/799e58efef6f99b516d762dff7981c.jpg)
Find out checkFile() It has the effect of checking and filtering , We delete it and submit Find out :
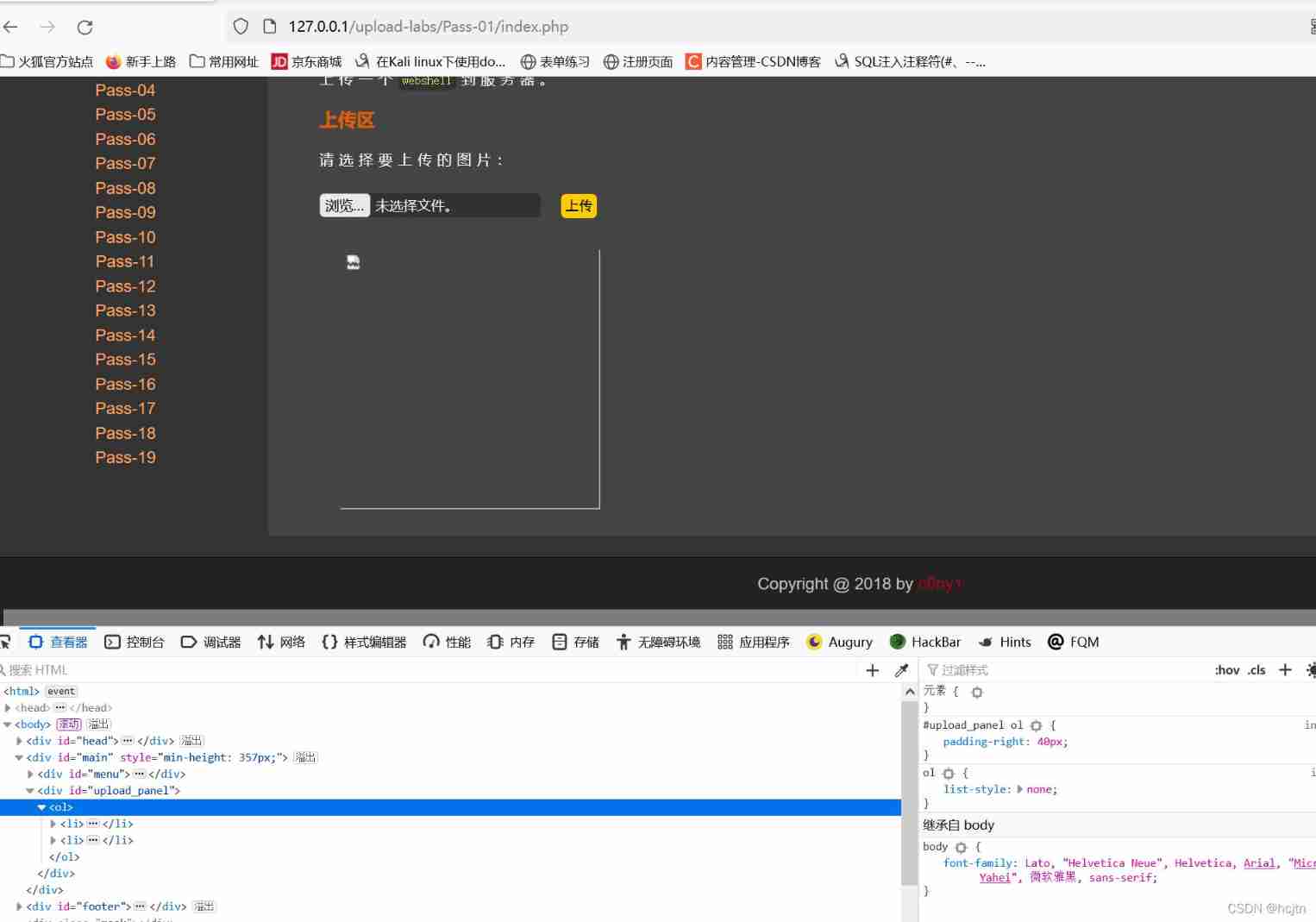
Then use Chinese ant sword Link Find success
Find success
At the same time, we find that just filtering at the front end is not enough , We can easily delete , So apart from the front end , The backend must also be verified
upload-labs-2(MIME verification )
Let's take a look at its source code first :
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR . $_FILES['upload_file']['name'];
$is_upload = true;
}
} else {
$msg = ' Incorrect file type , Please upload again !';
}
} else {
$msg = $UPLOAD_ADDR.' Folder does not exist , Please create... By hand !';
}
}
Find out :
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR . $_FILES['upload_file']['name'];
$is_upload = true;
}
} else {
$msg = ' Incorrect file type , Please upload again !';
At this time, we will have questions : How does the browser get the type of file we upload
This is about MIME type ( Multipurpose Internet mail extension type )
MIME(Multipurpose Internet Mail Extensions) Multipurpose Internet mail extension type . Is to set some kind of Extension Of file Use one kind Applications To open the way type , When the extension file is accessed , browser Will automatically use the specified application to open . Mostly used to specify some client-side customized file names , And some ways to open media files .
It's an Internet standard , Extended e-mail standards , To enable it to support :
Not ASCII Character text ; Non text attachments ( Binary system 、 voice 、 Image, etc ); By many parts (multiple parts) The body of the message ; Include non ASCII Character header information (Header information).
Common types :
| Upload files | multipart/from-data |
|---|---|
| Hypertext markup language text . | text/html |
| xml file .xml | text/xml |
| XHTML file .xhtml | application/xhtml+xml |
| jpg Image format | image/jpeg |
| RTF Text .rtf | application/rtf |
| PDF file .pdf | application/pdf |
| Microsoft Word file .word | application/msword |
MIME usage :
Client usage :
- Tell the server , The type of file I uploaded
- Tell the server , The types of documents I can accept
Server use :
- Tell the client , The data type I respond to
So when doing this problem, we should think of a reform Put it content-type Get rid of
So we use burp suite Carry out bag grabbing and package changing
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-Aei1DeVo-1643720447613)(C:\Users\hcj\AppData\Roaming\Typora\typora-user-images\image-20220201205405896.png)]](/img/fc/07348ecd9deae59118cbebde977062.jpg)
Find will content-type Change it
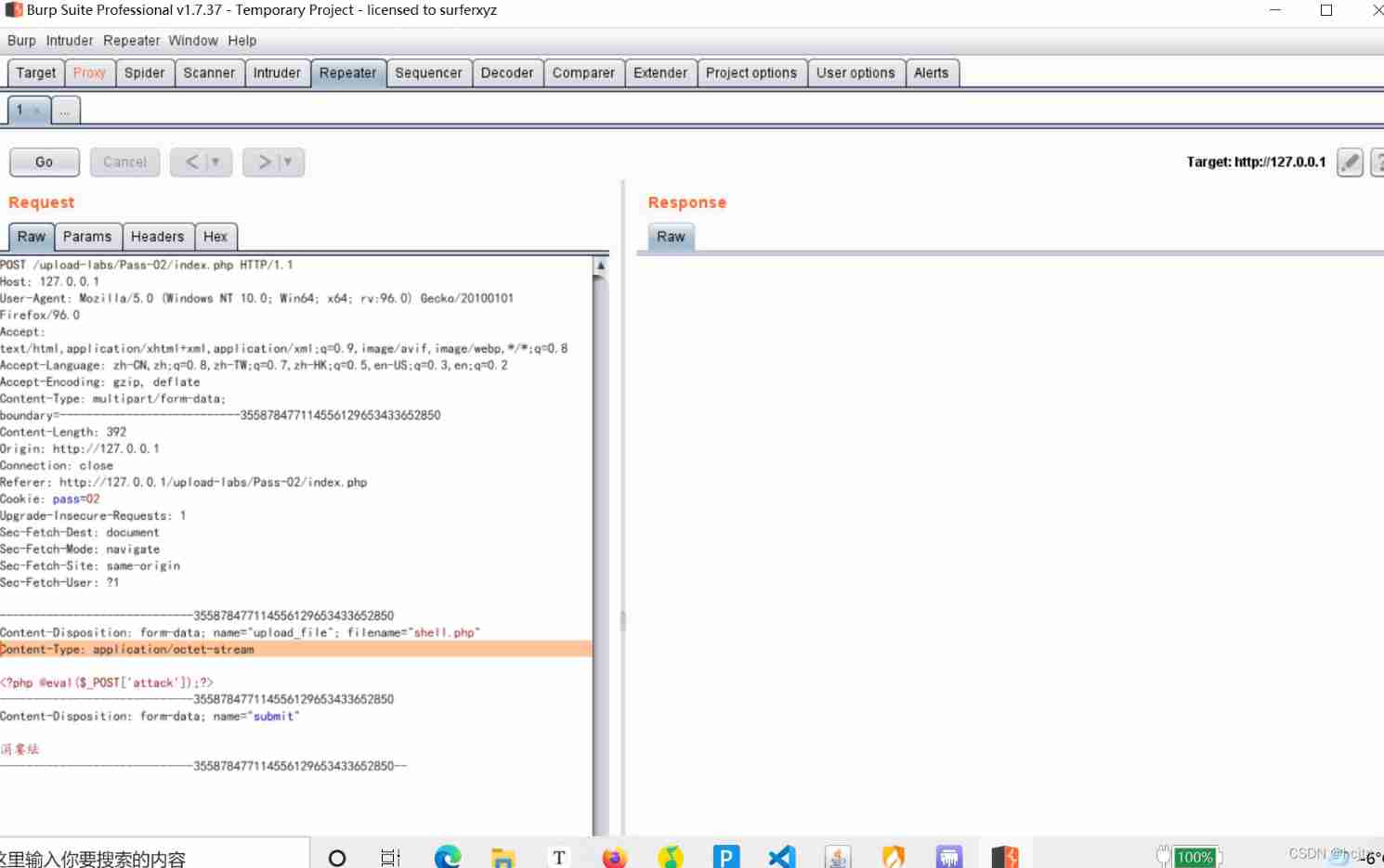
Change it to image/jpeg;
Click Send ,
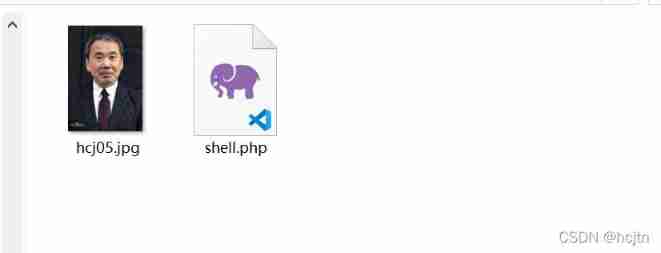
Find success
边栏推荐
- 5V串口接3.3V单片机串口怎么搞?
- <No. 9> 1805. Number of different integers in the string (simple)
- 问题:先后键入字符串和字符,结果发生冲突
- Superscalar processor design yaoyongbin Chapter 8 instruction emission excerpt
- 112. Network security penetration test - [privilege promotion article 10] - [Windows 2003 lpk.ddl hijacking rights lifting & MSF local rights lifting]
- (待会删)yyds,付费搞来的学术资源,请低调使用!
- Niuke website
- 数据库系统原理与应用教程(011)—— 关系数据库
- Completion report of communication software development and Application
- 2022 8th "certification Cup" China University risk management and control ability challenge
猜你喜欢
![[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]](/img/65/bf1d0f82878a49041e8c2b3a84bc15.png)
[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]
【数据聚类】基于多元宇宙优化DBSCAN实现数据聚类分析附matlab代码

即刻报名|飞桨黑客马拉松第三期盛夏登场,等你挑战

Xiaohongshu microservice framework and governance and other cloud native business architecture evolution cases
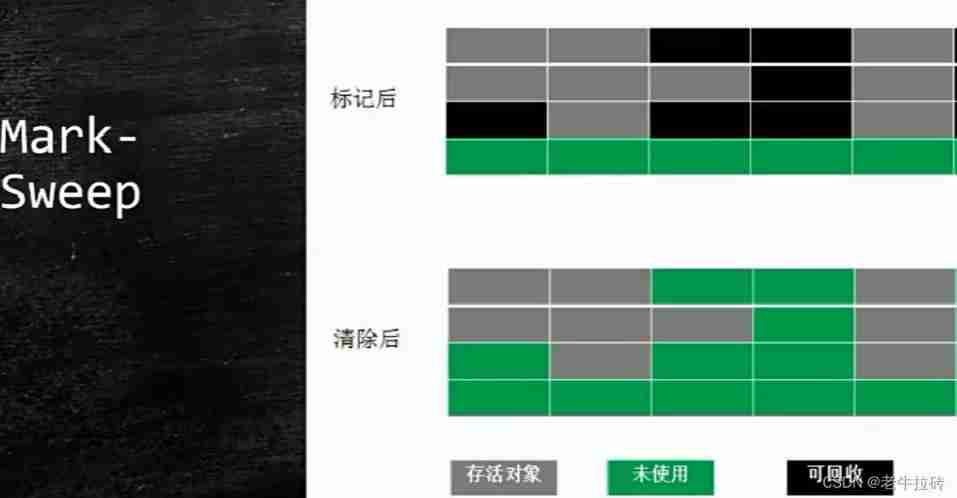
Sort out the garbage collection of JVM, and don't involve high-quality things such as performance tuning for the time being
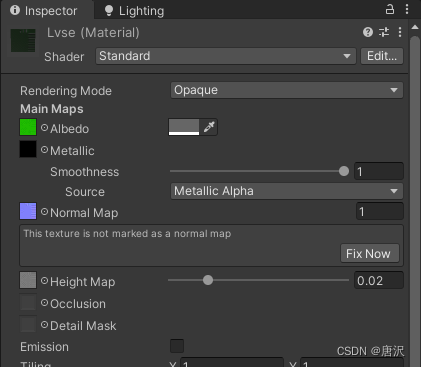
Unity map auto match material tool map auto add to shader tool shader match map tool map made by substance painter auto match shader tool

UP Meta—Web3.0世界创新型元宇宙金融协议
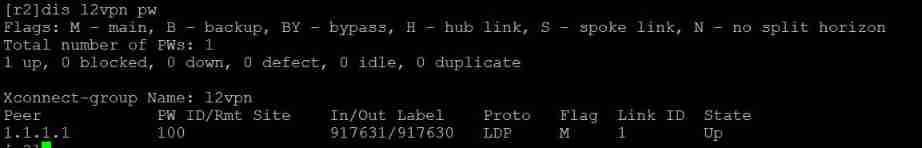
H3C HCl MPLS layer 2 dedicated line experiment

小红书微服务框架及治理等云原生业务架构演进案例

Baidu digital person Du Xiaoxiao responded to netizens' shouts online to meet the Shanghai college entrance examination English composition
随机推荐
数据库系统原理与应用教程(008)—— 数据库相关概念练习题
Problem: the string and characters are typed successively, and the results conflict
@Bean与@Component用在同一个类上,会怎么样?
What are the technical differences in source code anti disclosure
[data clustering] realize data clustering analysis based on multiverse optimization DBSCAN with matlab code
Fleet tutorial 15 introduction to GridView Basics (tutorial includes source code)
Tutorial on the principle and application of database system (008) -- exercises on database related concepts
关于 Web Content-Security-Policy Directive 通过 meta 元素指定的一些测试用例
Detailed explanation of debezium architecture of debezium synchronization
Learning and using vscode
Explore cloud database of cloud services together
SQL blind injection (WEB penetration)
Fleet tutorial 19 introduction to verticaldivider separator component Foundation (tutorial includes source code)
[filter tracking] strapdown inertial navigation pure inertial navigation solution matlab implementation
Tutorial on the principle and application of database system (011) -- relational database
Simple network configuration for equipment management
源代码防泄密中的技术区别再哪里
什么是局域网域名?如何解析?
Fleet tutorial 14 basic introduction to listtile (tutorial includes source code)
Apache installation problem: configure: error: APR not found Please read the documentation