当前位置:网站首页>9. Introduction to convolutional neural network
9. Introduction to convolutional neural network
2022-07-08 00:55:00 【booze-J】
article
Convolutional neural networks
summary
Convolutional neural network is developed in recent years , It is widely used in image processing and NLP And other fields .
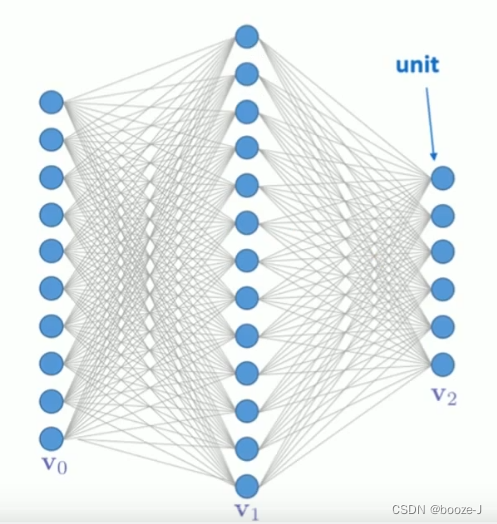
Tradition BP Problems in image processing :
- 1. Too many weights , Too much computation
Suppose you use 100X100 Train with pictures of , that 100X100 The size pictures are 10000 Pixels , Then the input of building the network needs 10000 Neurons , The number of hidden layer neurons in the network is similar to that of input layer neurons , In this case , There will be a lot of weights to be trained and updated . The amount of calculation is very large .
- 2. Too many weights , A large number of samples are needed for training
The more neurons , The more parameters , When you have more parameters , Just like solving equations, the more unknown parameters , The more data is needed to solve the unknown parameters .
Since there are these problems, what should we do ?
CNN adopt Local receptive field and Weight sharing The number of parameters needed to be trained in neural network is reduced .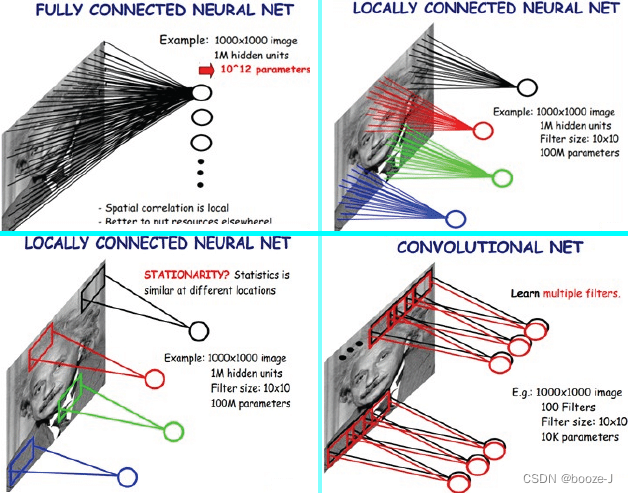
The first picture above shows a fully connected neural network , The second picture above and the first picture below are locally connected neural networks . Locally connected neural networks have fewer parameters than fully connected neural networks .
1. Convolution kernel
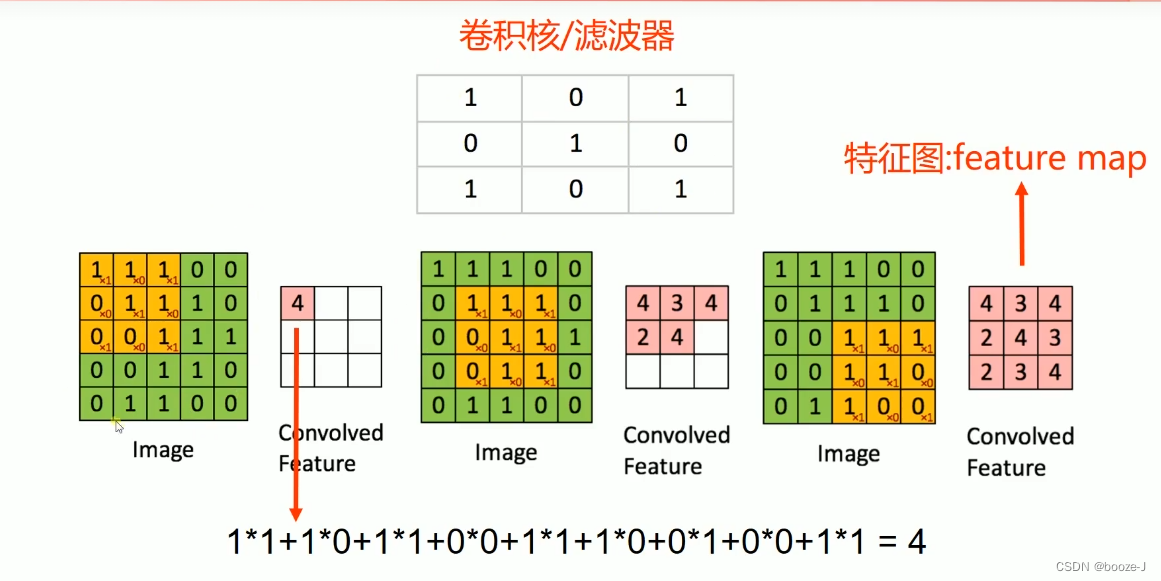

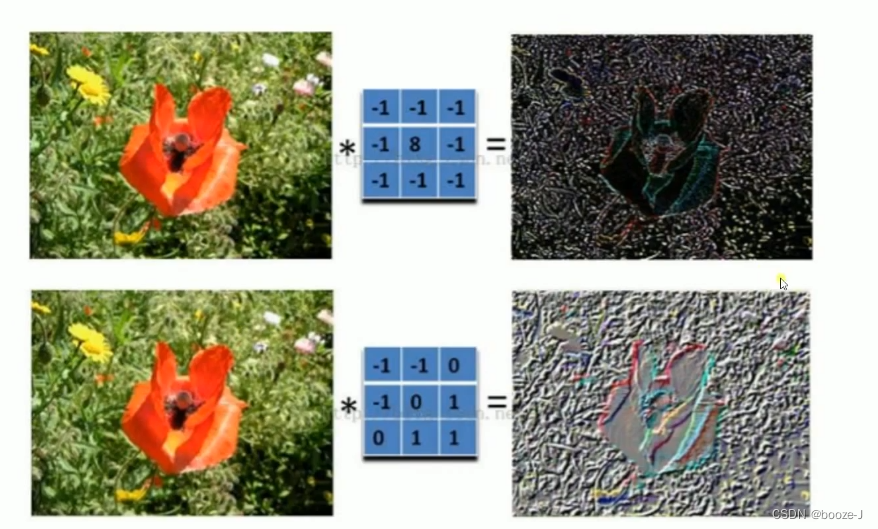 filter , The function of convolution kernel can be understood as extracting some different features of pictures , Different convolution kernels can extract different features .
filter , The function of convolution kernel can be understood as extracting some different features of pictures , Different convolution kernels can extract different features .
2. Pooling
Pooling Three common ways :
max-pooling
-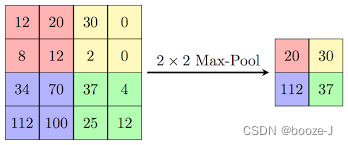
meaning-pooling
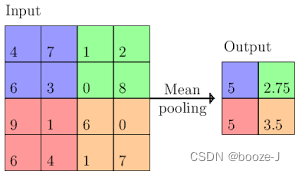
stochastic pooling
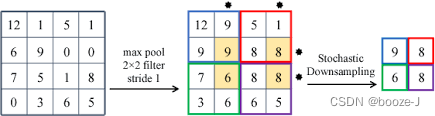
3. Convolution Padding
SAME PADDING
Supplement the outside of the plane 0, After convolution window sampling, a plane with the same size as the original is obtained 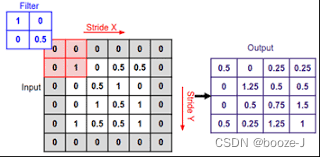
VALID PADDING
Not beyond the plane , After convolution window sampling, a plane smaller than the original plane is obtained 

4. Pooling Padding
SAME PADDING: May be added to the outside of the plane 0
VALID PADDING: Not beyond the plane
If there is one 28*28 The plane of the , use 2*2 In steps of 2 Window to it pooling operation :
Use SAME PADDING The way , obtain 14*14 The plane of the ;
Use VALID PADDING The way , obtain 14*14 The plane of the .If there is one 2*3 The plane of the , use 2*2 In steps of 2 Window to it pooling operation :
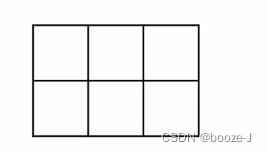
Use SAME PADDING The way , obtain 1*2 The plane of the ;
Use VALID PADDING The way , obtain 1*1 The plane of the .
5.LeNET-5 Introduce
LeNET-5 It is one of the earliest convolutional neural networks , Once widely used in Bank of America . The recognition accuracy of handwritten digits is 99% above .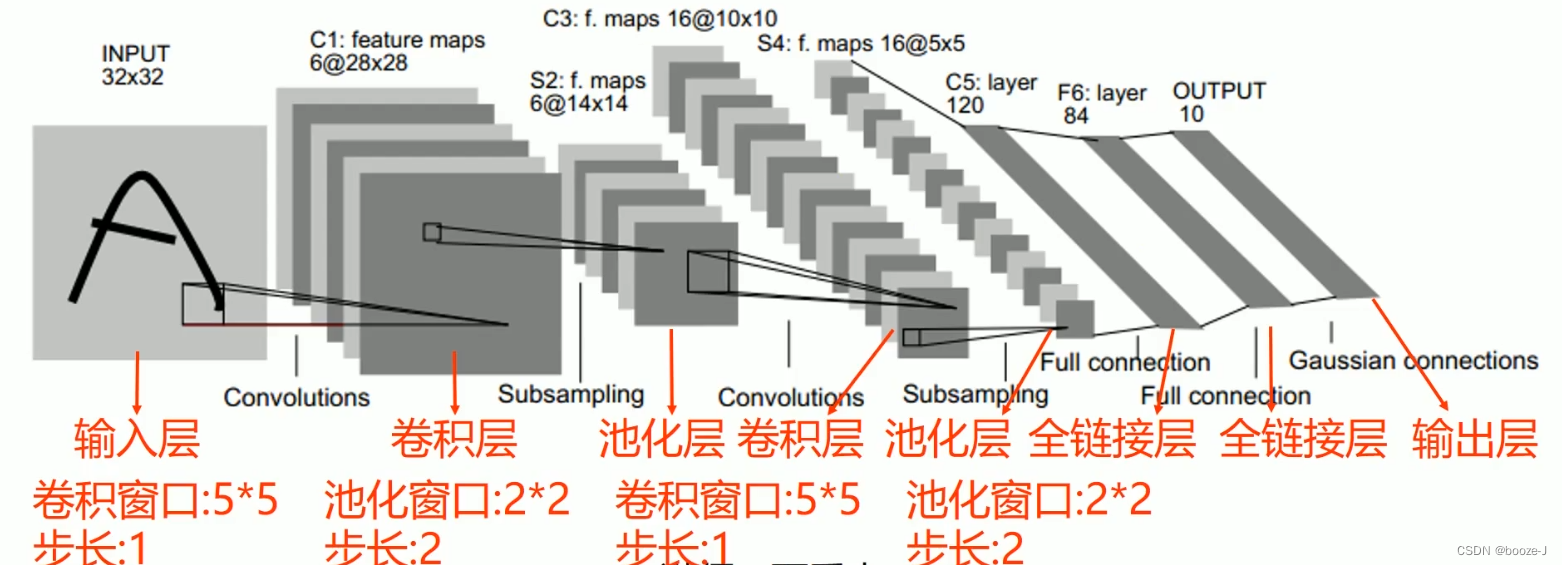
边栏推荐
- Deep dive kotlin synergy (XXII): flow treatment
- Introduction to paddle - using lenet to realize image classification method II in MNIST
- STL--String类的常用功能复写
- Cancel the down arrow of the default style of select and set the default word of select
- 英雄联盟胜负预测--简易肯德基上校
- Four stages of sand table deduction in attack and defense drill
- 基于微信小程序开发的我最在行的小游戏
- 从服务器到云托管,到底经历了什么?
- Su embedded training - day4
- 新库上线 | 中国记者信息数据
猜你喜欢
深潜Kotlin协程(二十二):Flow的处理
New library launched | cnopendata China Time-honored enterprise directory
【obs】官方是配置USE_GPU_PRIORITY 效果为TRUE的
基于微信小程序开发的我最在行的小游戏
New library online | cnopendata China Star Hotel data
Redis, do you understand the list

图像数据预处理
After going to ByteDance, I learned that there are so many test engineers with an annual salary of 40W?

Tapdata 的 2.0 版 ,开源的 Live Data Platform 现已发布
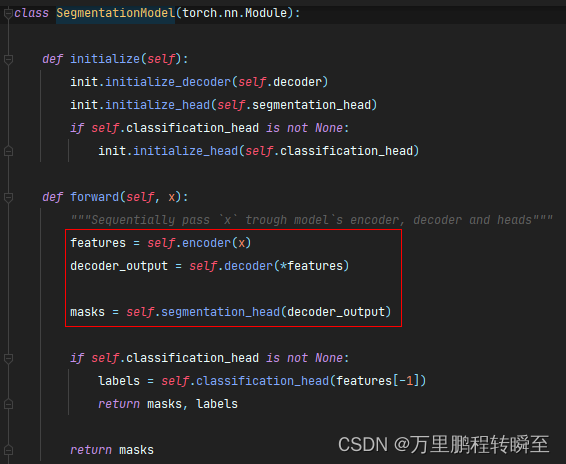
语义分割模型库segmentation_models_pytorch的详细使用介绍
随机推荐
Malware detection method based on convolutional neural network
Cve-2022-28346: Django SQL injection vulnerability
ReentrantLock 公平锁源码 第0篇
STL--String类的常用功能复写
Binder core API
接口测试要测试什么?
DNS series (I): why does the updated DNS record not take effect?
深潜Kotlin协程(二十二):Flow的处理
How does the markdown editor of CSDN input mathematical formulas--- Latex syntax summary
英雄联盟胜负预测--简易肯德基上校
Operating system principle --- summary of interview knowledge points
Semantic segmentation model base segmentation_ models_ Detailed introduction to pytorch
Cause analysis and solution of too laggy page of [test interview questions]
NVIDIA Jetson test installation yolox process record
Qt不同类之间建立信号槽,并传递参数
服务器防御DDOS的方法,杭州高防IP段103.219.39.x
QT adds resource files, adds icons for qaction, establishes signal slot functions, and implements
jemter分布式
C# 泛型及性能比较
[reprint] solve the problem that CONDA installs pytorch too slowly