当前位置:网站首页>Mysql database storage engine
Mysql database storage engine
2022-07-06 04:17:00 【wake__ up】
Storage engine concept
■MySQL The data in is stored in files with various technologies ,
Each technology uses a different storage mechanism 、 Indexing techniques 、 Lock level
And ultimately provide different functions and capabilities , These different technologies and accessories
The function of the set is MySQL It's called storage engine in
■ The storage engine is MySQL . Where data is stored in the file system
Or storage format
MySQL Common storage engines
●MyISAM
Storage engine introduction
■MySQL Components in the database , Responsible for executing the actual data I/0 operation
■MySQL In the system ,
The storage engine is in the middle of the file system . On , The data is transferred to the storage engine before it is saved to the data file , Then according to each
Store in the storage format of the storage engine
MyISAM Characteristics
■MyISAM Unsupported transaction , Foreign key constraints are not supported either , Full text indexing only , Data files and index files are kept separately
■ Fast access , There is no requirement for transaction integrity
■MyISAM Suitable for inquiry 、 Insertion based applications
■MyISAM On disk . Stored in three files on the , The file name and table name are the same , But the extensions are :
●.frm Definition of file storage table structure
● The extension of the data file is .MYD (MYData)
Table level locking form , Lock the entire table when the data is updated
Databases block each other in the process of reading and writing
It will block the reading of user data in the process of data writing
It will also block the user's data writing in the process of data reading
Data is written or read separately , The process is fast and takes up less resources
■MyIAM Supported storage formats
● Static table
● Dynamic table
● Compression meter
(1) static state ( Fixed length ) surface
Static tables are the default storage format . Fields in static tables are immutable , So every record is a fixed length , The advantage of this storage method is that the storage is very fast , Easy to
cache , It's easy to recover in case of failure ; The disadvantage is that it usually takes up more space than a dynamic table .
(2) Dynamic table
Dynamic tables contain variable fields , Records are not fixed length , The advantage of this storage is that it takes up less space , But frequent updates 、 Deleting records will cause fragmentation , It needs to be carried out on a regular basis
0PTIMIZETABLE Sentence or myisamchk-r Command to improve performance , And it's relatively difficult to recover in case of failure .
(3) Compression meter
The compressed table consists of myisamchk Tool creation , Take up a very small space , Because each record is compressed individually , So there's only a very small cost of access .
MyISAM Examples of applicable production scenarios
■ Business doesn't need the support of business
■ Read or write data unilaterally
■MyISAM The storage engine reads and writes data frequently, which is not suitable for the scenario
■ Using read-write concurrency to access relatively low business
■ Business with relatively little data modification
■ Data service - Business that does not require very high consistency
■ The server hardware resources are relatively poor
InnoDB Feature introduction
■ Support transactions , Support 4 Transaction isolation levels
■MySQL from 5.5.5 Version start , The default storage engine is InnoDB
■ Read and write blocking is related to transaction isolation level
■ It can cache index and data very efficiently
■ Tables and primary keys are stored in clusters
■ Support partition 、 Table space , similar oracle database
■ Support for foreign key constraints ,5.5 Full text indexing is not supported before ,5.5 Full text index is supported after
■ The requirement for hardware resources is relatively high
■ Row level locking , But full table scan will still be table level locking , Such as
update table set a=1 where user like "%zhang%';
■InnoDB The number of rows in the table is not saved , Such as select count( * ) from table; when
InnoDB You need to scan the entire table to calculate how many rows there are , however MyISAM Simply read out the number of saved lines . It should be noted that , When count(*) The statement contains where When the conditions MyISAM You also need to scan the entire table .
■ For self growing fields ,InnoDB Must contain only the index of this field
But in MyISAM You can create a composite index with other fields in the table
■ When you empty the entire table ,InnoDB It's one - Line one Deletion of lines , Efficiency is very slow .
MyISAM The table is rebuilt
InnoDB It is suitable for production scenario analysis
■ Business needs transaction support
■ Row level locking has a good adaptability to high concurrency , But make sure that the query is
Complete by indexing
■ Scenarios where business data is updated frequently
● Such as : Forum , Microblogging, etc
■ High requirements for business data consistency
Such as : banking business
■ The memory of hardware device is large , utilize InnoDB Better cache capacity to provide
High memory utilization , Reduce disk I0 The pressure of the
Enterprises choose storage engine based on
■ We need to consider the different core functions and application scenarios provided by each storage engine
■ Supported fields and data types
● All engines support common data types
● But not all bows | All of them support other field types , Like binary objects
■ Lock type : Different storage engines support different levels of locking
● Table locking : MyISAM Support
● Row lock : InnoDB Support
■ Index support
● Index | It can significantly improve performance when searching and recovering data in the database
● Different storage methods | Engine provides different indexes | Technology
● Some storage bows | Engine doesn't support indexing at all |
■ Transaction processing support
● Improve reliability during updating and inserting information into tables
● The storage engine can be selected according to whether the enterprise business needs to support transactions
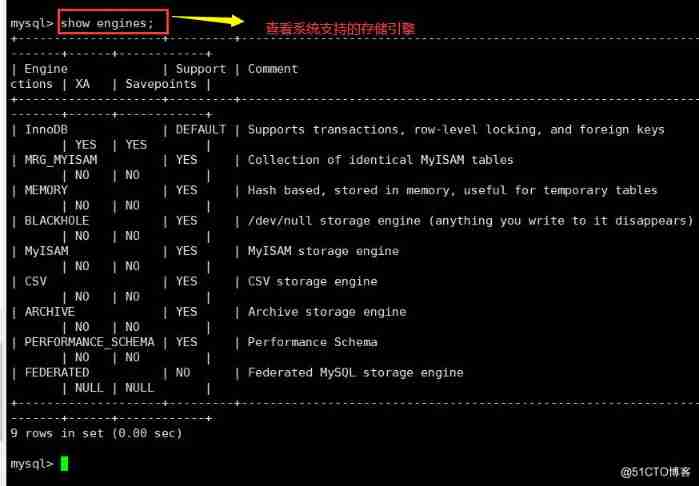
Check out the storage engines supported by the system
show engines;
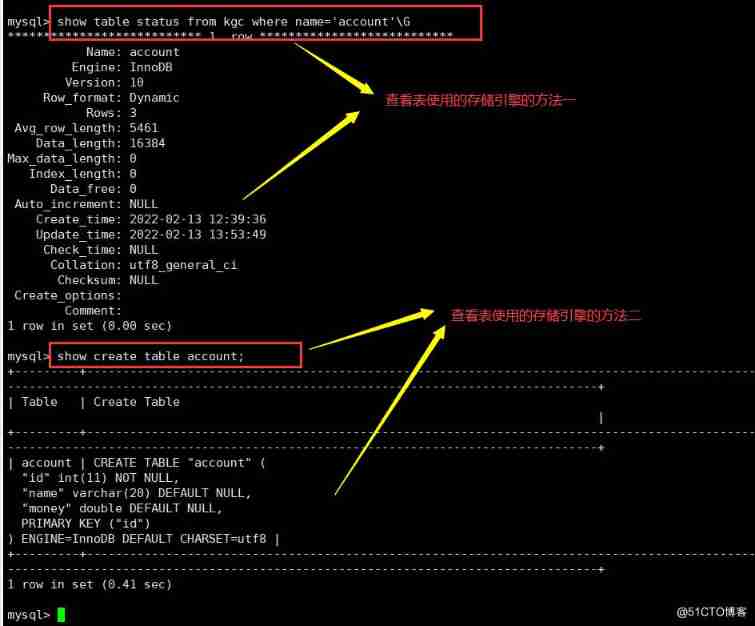
Look at the storage engine that the table uses
Method 1 -:
show table status from Library name where name=‘ Table name ’\G
Method 2 :
use Library name ;
show create table Table name ;
Modify the storage engine
1. adopt alter table modify
use Library name ;
alter table Table name engine=MyISAM;
2. By modifying the /etc/my.cnf The configuration file , Specify the default storage engine and restart the service
vim /etc/my. cnf
[mysqld]
default-storage-engine=INNODB
systemctl restart mysql. service
Be careful : This method only changes the configuration file and restarts mysql The newly created table is valid after service , has The existing table will not be changed .
# Modify the storage engine
1. adopt alter table modify
use Library name ;
alter table Table name engine=MyISAM;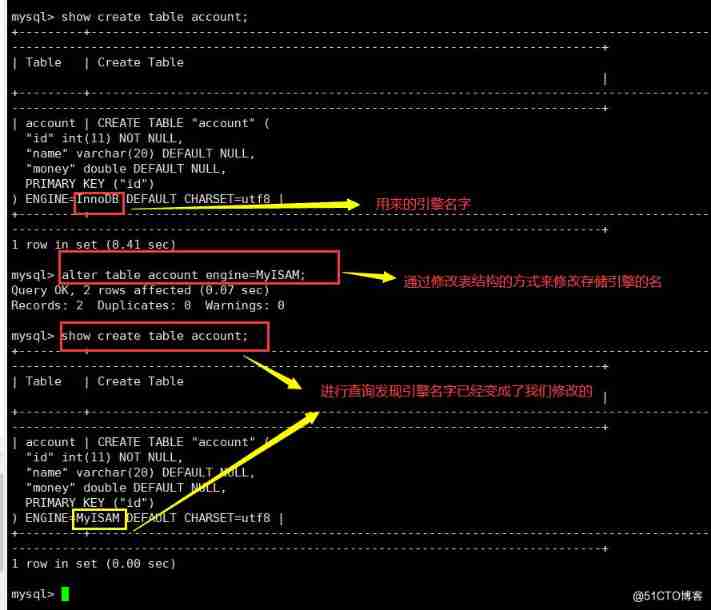
2. By modifying the /etc/my.cnf The configuration file , Specify the default storage engine and restart the service
vim /etc/my. cnf
[mysqld]
default-storage-engine=INNODB
systemctl restart mysql. service
Be careful : This method only changes the configuration file and restarts mysql The newly created table is valid after service , The existing table will not be changed .
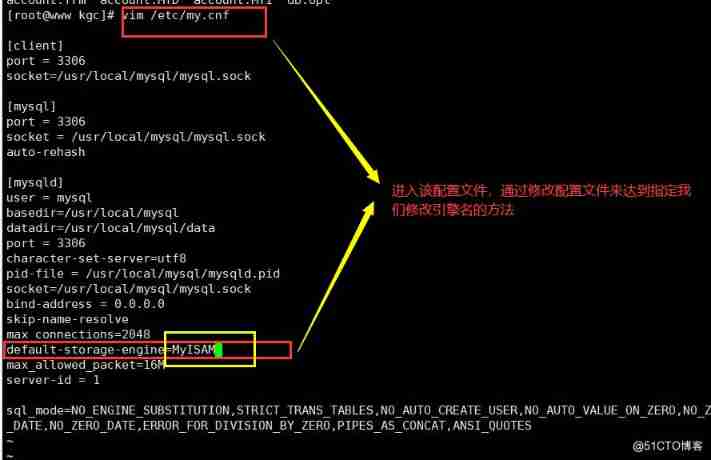
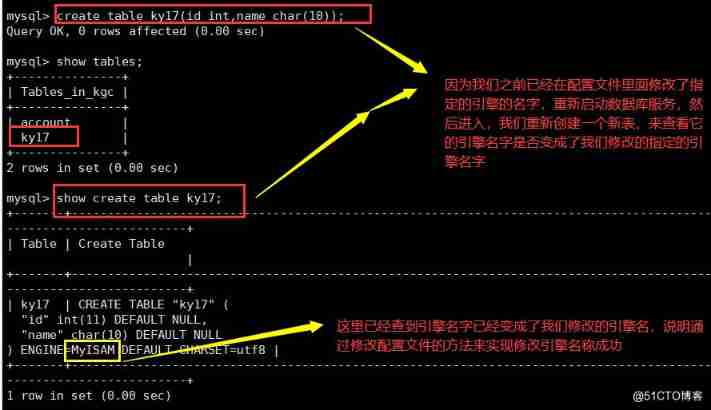
3. adopt create table Specify the storage engine when creating the table
use Library name ;
create table Table name ( Field 1 data type ,…)
engine=MyISAM;
//InnoDB The relationship between row lock and index
InnoDB Row locking is achieved by locking index entries , If there is no index ,InnoDB The record will be locked by a hidden cluster index .
1)
delete from t1 where id=1;
If id Field is primary key ,innodb Yes Cluster index is used for primary key , Will directly lock the whole line of records .
2)
delete from t1 where name=‘aaa’ ;
If name Fields are normal indexes , Will lock the two rows of the index first , Then the record corresponding to the primary key will be locked .
3)
delete from t1 where age=23;
If age Field has no index , Will use all trace filtering , At this time, all records on the form will be locked .
// Deadlock
Deadlocks are transactions waiting for each other's resources , Finally formed a loop .
Case study :
create table t1 (id int primary key, name char(3),age int) ;
insert into t1 values(1, ‘aaa’,22) ;
insert into t1 values(2, ‘bbb’ ,23) ;
insert into t1 values (3, ’ aaa’,24) ;
insert into t1 values(4, ‘bbb’ ,25) ;
insert into t1 values(5, ‘ccc’,26) ;
insert into t1 values(6, ‘zzz’,27) ;
session 1
session 2
begin;
begin;
delete from t1 where id=5;
select * from t1 where id=1 for update;
delete from t1 where id=1; # A deadlock occurs
update t1 set name=‘qqqq’ where id=5; # A deadlock occurs
#forupdate An exclusive lock can be placed on a row in the database . When the operation of a transaction is not completed , Other transactions can read but cannot write or update .
// How to avoid deadlock as much as possible ?
1) Access tables and rows in a fixed order .
2) Big business, small business . Big business tends to deadlock , If business permits , Break up big business into small ones .
3) At the same time - In a business , Try to lock all the resources you need at once , Reduce deadlock probability .
4) Reduce isolation level . If business permits , Lowering the isolation level is also a good choice , Let's take the isolation level from RR Adjusted for RC, A lot can be avoided because gap A deadlock caused by a lock .
5) Add a reasonable index to the table . If you do not use indexes, you will add locks to each row of records in the table , The probability of deadlock is greatly increased .
边栏推荐
- MySQL master-slave replication
- HotSpot VM
- The global and Chinese market of negative pressure wound therapy unit (npwtu) 2022-2028: Research Report on technology, participants, trends, market size and share
- In depth MySQL transactions, stored procedures and triggers
- 2/11 matrix fast power +dp+ bisection
- SharedPreferences 源码分析
- 软考 系统架构设计师 简明教程 | 总目录
- TCP/IP协议里面的网关地址和ip地址有什么区别?
- Solution to the problem that the root account of MySQL database cannot be logged in remotely
- /usr/bin/gzip: 1: ELF: not found/usr/bin/gzip: 3: : not found/usr/bin/gzip: 4: Syntax error:
猜你喜欢
DM8 archive log file manual switching
10个 Istio 流量管理 最常用的例子,你知道几个?

One question per day (Mathematics)
Lombok原理和同时使⽤@Data和@Builder 的坑
Data processing methods - smote series and adasyn
Mysql数据库慢sql抓取与分析
Solution to the problem that the root account of MySQL database cannot be logged in remotely

10個 Istio 流量管理 最常用的例子,你知道幾個?

Introduction to hashtable
1291_Xshell日志中增加时间戳的功能
随机推荐
[FPGA tutorial case 12] design and implementation of complex multiplier based on vivado core
[tomato assistant installation]
牛顿插值法
Viewing and verifying backup sets using dmrman
脚本生命周期
lora网关以太网传输
2/13 review Backpack + monotonic queue variant
[PSO] Based on PSO particle swarm optimization, matlab simulation of the calculation of the lowest transportation cost of goods at material points, including transportation costs, agent conversion cos
绑定在游戏对象上的脚本的执行顺序
/usr/bin/gzip: 1: ELF: not found/usr/bin/gzip: 3: : not found/usr/bin/gzip: 4: Syntax error:
Understanding of processes, threads, coroutines, synchronization, asynchrony, blocking, non blocking, concurrency, parallelism, and serialization
Solution to the problem that the root account of MySQL database cannot be logged in remotely
Lora gateway Ethernet transmission
C. The third problem
Global and Chinese markets for patent hole oval devices 2022-2028: Research Report on technology, participants, trends, market size and share
《2022年中国银行业RPA供应商实力矩阵分析》研究报告正式启动
【HBZ分享】ArrayList的增删慢查询快的原因
10个 Istio 流量管理 最常用的例子,你知道几个?
About some basic DP -- those things about coins (the basic introduction of DP)
729. My schedule I (set or dynamic open point segment tree)