当前位置:网站首页>Zephyr study notes 2, scheduling
Zephyr study notes 2, scheduling
2022-07-04 07:17:00 【mayiQX】
Chapter two : Scheduler (Scheduling).
The kernel priority based scheduler allows application threads to share CPU.
The thread changes from running state to pending or waiting state , For example, through k_sem_take() perhaps k_sleep().
The thread transitions to the ready state , For example, using k_sem_give() perhaps k_thread_start().
Return the thread context after processing the interrupt , When the running thread calls k_yield() when .
When a thread actively starts an operation that converts itself to a suspended or waiting state , It will sleep .
Collaborative
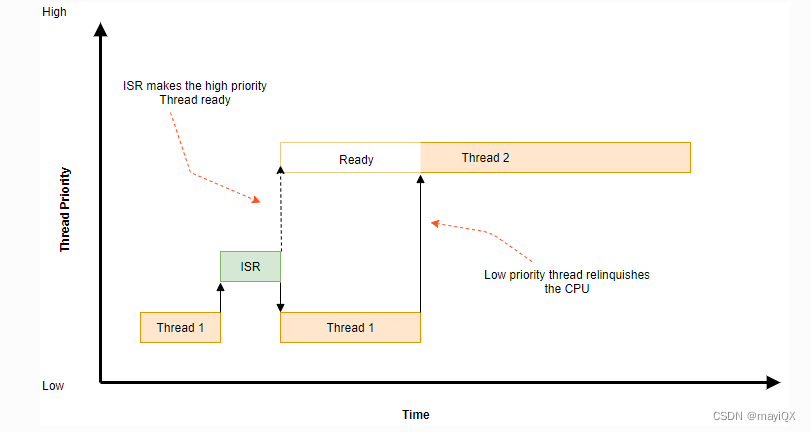
Preemptive
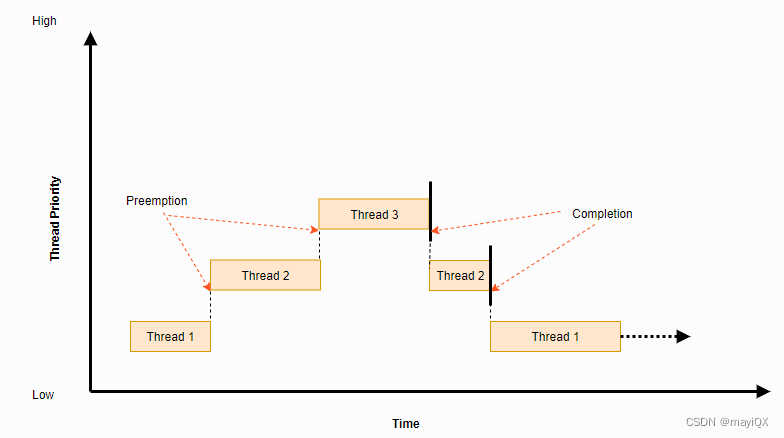
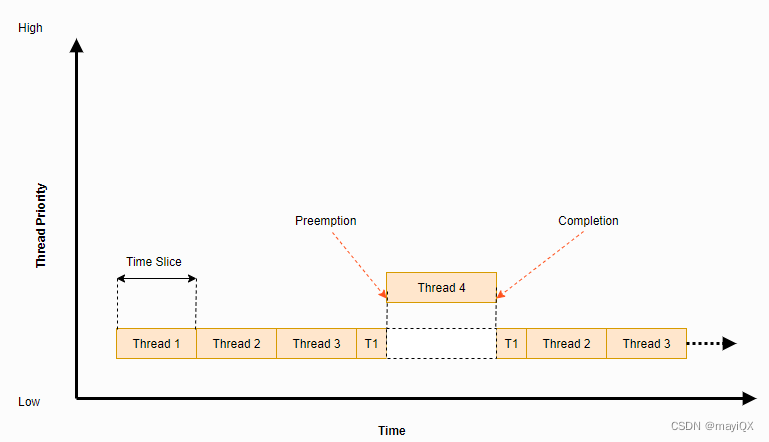
Scheduler Locking
The preemptive thread that does not want to be preempted when performing critical operations can be called k_sched_lock(). Once the critical operation is completed , Preemptable threads must call k_sched_unlock() To restore its normal preemptive state .
Thread Sleeping
k_sleep()
k_wakeup()
Threads can call k_busy_wait() To perform busy waiting , This wait delays its processing for a specified period of time , Instead of CPU Give up to another ready thread .
CPU Idling
static k_sem my_sem;
void my_isr(void *unused)
{
k_sem_give(&my_sem);
}
void main(void)
{
k_sem_init(&my_sem, 0, 1);
/* wait for semaphore from ISR, then do related work */
for (;;) {
/* wait for ISR to trigger work to perform */
if (k_sem_take(&my_sem, K_NO_WAIT) == 0) {
/* ... do processing */
}
/* put CPU to sleep to save power */
k_cpu_idle();
}
}边栏推荐
- MySQL 45 lecture learning notes (VII) line lock
- Electronic Association C language level 1 35, bank interest
- Node connection MySQL access denied for user 'root' @ 'localhost' (using password: yes
- Pangu open source: multi support and promotion, the wave of chip industry
- Redis - detailed explanation of cache avalanche, cache penetration and cache breakdown
- What is industrial computer encryption and how to do it
- 【网络数据传输】基于FPGA的百兆网/兆网千UDP数据包收发系统开发,PC到FPGA
- [GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
- [FPGA tutorial case 7] design and implementation of counter based on Verilog
- Finishing (III) - Exercise 2
猜你喜欢
![[network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA](/img/71/1d6179921ae84b1ba61ed094e592ff.png)
[network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA
响应式移动Web测试题
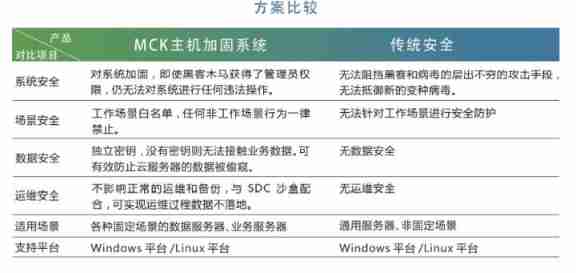
The important role of host reinforcement concept in medical industry
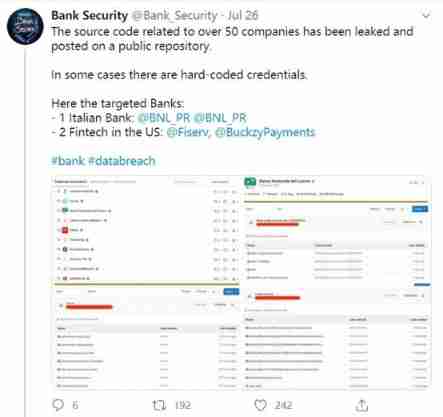
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
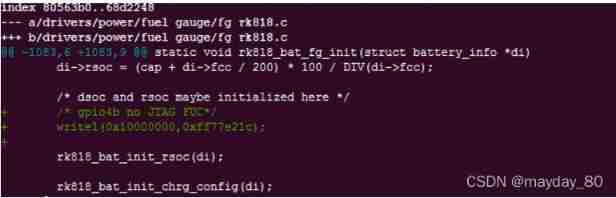
Set JTAG fuc invalid to normal IO port
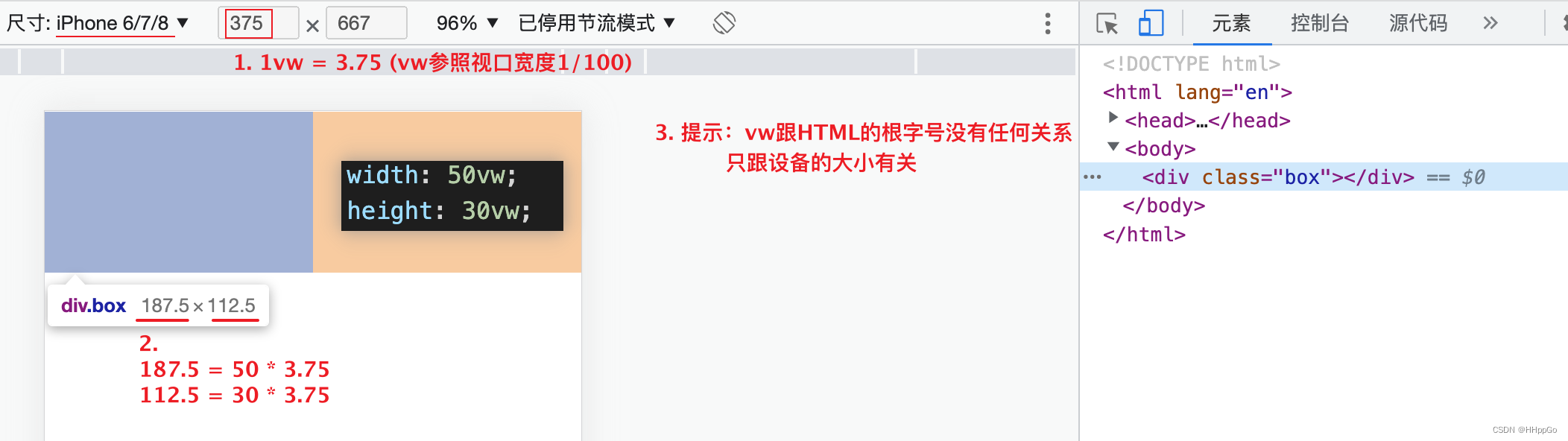
移动适配:vw/vh
Campus network problems
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
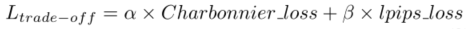
Adaptive spatiotemporal fusion of multi-target networks for compressed video perception enhancement
【Kubernetes系列】Kubernetes 上安装 KubeSphere
随机推荐
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
Enter the year, month, and determine the number of days
Research on an endogenous data security interaction protocol oriented to dual platform and dual chain architecture
【森城市】GIS数据漫谈(一)
Transition technology from IPv4 to IPv6
云Redis 有什么用? 云redis怎么用?
About how idea sets up shortcut key sets
电子协会 C语言 1级 35 、银行利息
Zabbix agent主动模式的实现
What is the use of cloud redis? How to use cloud redis?
MySQL relearn 2- Alibaba cloud server CentOS installation mysql8.0
Valentine's Day is coming! Without 50W bride price, my girlfriend was forcibly dragged away...
Deep profile data leakage prevention scheme
[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
【FreeRTOS】FreeRTOS學習筆記(7)— 手寫FreeRTOS雙向鏈錶/源碼分析
There is no Chinese prompt below when inputting text in win10 Microsoft Pinyin input method
Rhcsa day 3
A real penetration test
[Flink] temporal semantics and watermark
大厂技术专家:架构设计中常用的思维模型