当前位置:网站首页>Regulations for network security events of vocational group in 2022 Guizhou Vocational College skill competition
Regulations for network security events of vocational group in 2022 Guizhou Vocational College skill competition
2022-07-05 06:12:00 【Wangzai sec】
2022 Secondary vocational group of Guizhou Vocational College skills competition
Rules for network security events
One 、 Event name
Event name : Network security
The event belongs to : Information technology
Two 、 The purpose of the competition
To test the effectiveness of network security for secondary vocational schools , Promote the teaching reform of network information security specialty , Cultivate a large number of excellent skilled talents with world-class skills that meet the needs of the national network security strategy , Create... In society “ Skills change destiny 、 Ingenuity makes life ” The atmosphere of advocating skills , The Ministry of education of the people's Republic of China and many ministries and commissions jointly held this competition .
( One ) Test the effectiveness of teaching
The competition covers the latest requirements of enterprise posts in the network information security industry for students' vocational skills , The competition process is the specific implementation of the complete work task , The competition evaluation criteria meet the industry project acceptance and delivery standards . Pass the contest , It can well reflect the matching degree between the skills cultivated by students in secondary vocational schools and the job requirements of employers , So as to test the teaching effect of network information security specialty , Show the results of information security personnel training .
( Two ) Promote teaching reform
The competition content comes from the real projects and work tasks of the enterprise , Its contents and requirements directly reflect the requirements of network information security technology posts , Guide the school to connect majors with vocational posts 、 The course content is connected with professional standards 、 Connection between teaching process and working process 、 The connection between academic certificate and professional qualification certificate . Pass the contest , Guide secondary vocational schools to transform the complete work tasks of enterprises into teaching contents ; Turn the traditional teaching mode of emphasizing teaching and neglecting practice to “ Learning by doing 、 Teaching in China ” Project case teaching ; Take the professional qualification ability as the core ability of the specialty , So as to improve the pertinence and effectiveness of talent training .
( 3、 ... and ) Keep up with the world's high level
This event closely follows the development trend of network information security industry , Aim at the development level of international network security technology , The competition content is integrated into the latest technology of industry development . Lead the majority of secondary vocational schools to constantly cultivate national needs at a new and higher starting point 、 International level network information security skilled talents , Serving the national strategy , Building a strong network country .
( Four ) Create a social atmosphere advocating skills
Skilled talents are an important part of the talent team , A good social atmosphere is the environment and foundation for the growth of skilled talents , It is related to the long-term development of skilled talents . Promote through competition , Guide the whole society to respect 、 Attaches great importance to 、 Care about the cultivation and growth of skilled talents , Let respect labor 、 Respect technology 、 Respecting innovation has become a social consensus . Pass the contest , Commend a group of outstanding young skilled talents , Enhance their pride 、 The acquisition , Build... All over the country “ Skills change destiny 、 Ingenuity makes life ” The atmosphere of advocating skills , Encourage the majority of young people to become talents with skills 、 The road of serving the country with skills .
3、 ... and 、 Competition content
3.1 Standard specification
It mainly assesses the network system security strategy deployment of contestants 、 Information protection 、 Network security operation and maintenance management 、 Network security incident emergency response 、 Network security data forensics 、 Application security 、 Comprehensive practical ability such as code audit , Specific include :
project | |
1 | Work organization and management |
personal ( player ) Need to know and understand : • Health and safety related regulations 、 obligation 、 Regulations . • Where personal protective equipment must be used , Such as : Electrostatic protection 、 Electrostatic discharge . • The importance of integrity and security in handling user equipment and information . • waste recovery 、 The importance of safe disposal . • plan 、 Methods of scheduling and priority disposal . • In all work practices , Pay attention to accuracy 、 The importance of inspection and detail . • The importance of systematic work . • Of the work environment 6S management . | |
personal ( player ) Required ability : • Compliance with health and safety standards 、 Rules and regulations . • Maintain a safe working environment . • Identify and use appropriate personal electrostatic protective equipment . • Security 、 Choose properly 、 Use 、 clean 、 Maintain and store tools and equipment • Comply with relevant regulations , Planning the work area , Maintain daily cleanliness , Maximize productivity . • Work effectively , And regularly check the progress and results . • Adopt comprehensive and effective research methods , Ensure that knowledge is constantly updated . • Take the initiative to try new methods 、 New systems and willingness to accept change . | |
2 | Communication and interpersonal skills |
personal ( player ) Need to know and understand : • Listening is an important means of effective communication . • The role requirements of team members and the most effective way of communication . • The importance of building and maintaining creative working relationships with team members and managers . • Effective teamwork skills . • Techniques for eliminating misunderstandings and resolving conflicts . • The ability to manage tension and anger . • The importance of teamwork . | |
personal ( player ) Required ability : • Use good listening and questioning skills , Deepen the understanding of complex situations . • Continuous and effective oral and written communication with team members . • Recognize and adapt to the changing needs of team members . • Actively promote , Build a strong and effective team . • Share knowledge and expertise with team members , Form a mutually supportive learning culture . • Effectively manage negative emotions , Pass on to others the confidence to solve problems . • Communication skills with staff . | |
3 | Safety regulations |
personal ( player ) Need to know and understand : • Information technology risk management standards 、 policy 、 Requirements and processes . • Functions and usage of network defense and vulnerability assessment tools . • Specific functions of the operating system . • Concepts related to computer programming , Including computer language 、 Programming 、 test 、 debugging 、 Delete and file type . • Principles and methods of network security and privacy applied to software development . | |
personal ( player ) Required ability : • When designing the overall program test and recording the evaluation process , Network security and privacy principles should be applied to management requirements ( And confidentiality 、 integrity 、 Usability 、 Authentication 、 Non repudiation of digital signature ). • For management 、 Conduct independent and comprehensive assessment of operational and technical safety control , And evaluate the control improvement within or inherited from the information technology system , To determine the overall effectiveness of the control . • Development 、 Create and maintain new computer applications 、 Software or specialized applications . • Modify existing computer applications 、 Software or specialized applications . • Analyze new or existing computer applications 、 Security status of software or professional applications , Provide available analysis results . • Conduct software system research and develop new functions , Ensure that there is network security protection function . • Conduct comprehensive technical research , Evaluate the possible weak links in the network security system . • plan 、 Prepare and implement system testing . • According to technical specifications and requirements , Analyze 、 Evaluate and report the results . • Test and evaluate the security of information system , Covering the system development life cycle . | |
4 | operation 、 maintain 、 Supervise and manage |
personal ( player ) Need to know and understand : • query language , Such as SQL ( Structured query language ) . • Data backup and recovery , Data standardization strategy . • Network protocol , Such as TCP/IP、 Dynamic Host Configuration (DHCP)、 The domain name system (DNS) And directory services . • Firewall concept and function . • The concept of network security architecture , Including topology 、 agreement 、 Components and principles . • System 、 Network and operating system reinforcement technology . • Management information technology 、 User security policy ( for example : Account creation 、 Password rule 、 Access control ). • Information technology security principles and methods . • Authentication 、 Authorization and access control methods . • Network security 、 Loopholes and privacy principles . • Learning management system and its application in management learning . • The impact of network security law and other relevant regulations on its network planning . | |
personal ( player ) Required ability : • Management database or database management system . • Manage and implement processes and tools , Ensure that the organization can identify 、 The archive 、 Access to knowledge assets and information content . • Dealing with problems , install 、 To configure 、 Troubleshooting , And provide maintenance and training according to customer needs or consultation . • install 、 To configure 、 test 、 function 、 Maintain and manage networks and firewalls , Including hardware and software , Ensure that all information is shared 、 transmission , Support information security and information systems . • install 、 To configure 、 Debug and maintain the server ( Hardware and software ), Ensure the confidentiality of information 、 Integrity and availability . • Manage accounts 、 Set up firewall and install operating system patches . • Access control 、 Account and password creation and management . • Check the organization's existing computer systems and processes , Help the agency be safer 、 Faster and more efficient operations . • Assist in supervising information systems or networks , Possible problems in information security within the management organization or other aspects that need to be responsible , Including strategy 、 personnel 、 Infrastructure 、 demand 、 Policy implementation 、 Contingency plan 、 Safety awareness and other resources . | |
5 | Protection and defense |
personal ( player ) Need to know and understand : • File system implementation ( for example , New technology file system [NTFS]、 File allocation table [FAT]、 File extension [EXT]). • System files ( for example : Log files 、 Registry files 、 The configuration file ) Contains relevant information and where these system files are stored . • The concept of network security architecture , Including topology 、 agreement 、 Layering and principle . • Industry technical standards and analysis principles 、 Methods and tools . • Threat investigation 、 The report 、 Investigative tools and laws 、 statute . • Category of network security events 、 Response and handling methods . • Network defense and vulnerability assessment tools and their functions . • Countermeasures for known safety risks . • Authentication 、 Authorization and access methods . | |
personal ( player ) Required ability : • Use protective measures and information collected from different channels , To identify 、 Analyze and report what happened 、 Or possible network events , To protect information 、 Information systems and networks are free from threats . • test 、 The implementation of 、 Deploy 、 maintain 、 Check 、 Manage hardware infrastructure and software , Effectively manage the network and resources of computer network protection service providers as required . • Monitoring networks , Record unauthorized activities in a timely manner . • Respond effectively to crises or emergencies in your field , Reduce direct and potential threats in your area of expertise . • Use mitigation measures 、 Preparation measures , Respond and restore as required , Ensure the security of property and information to maximize the survival rate . • Investigate and analyze relevant network security emergency response activities . • Assess threats and vulnerabilities . • Assess the level of risk , Develop appropriate mitigation measures in business and non operational situations . | |
6 | analysis |
personal ( player ) Need to know and understand : • Background and methods of cyber threat actors . • Methods and techniques for detecting various available activities . • Network intelligence information collection capability and resource base . • Cyber threats and vulnerabilities . • Basic knowledge of network security ( for example , encryption 、 A firewall 、 authentication 、 Trap system 、 Peripheral protection ). • Vulnerability information dissemination source ( for example , alert 、 notice 、 Errata and bulletins ). • Structure of development tools 、 Methods and Strategies ( for example , Sniffing 、 Recording keyboard ) And technology ( for example , Get back door access 、 Collect confidential data 、 Analyze the vulnerability of other systems in the network ). • forecast 、 Internal strategies to simulate threats and responses . • Internal and external collaborative network operations and tools . • System forgery and judicial use cases . | |
personal ( player ) Required ability : • Identify and evaluate cyber security criminal activities . • Issue the investigation results , To help initiate or support law enforcement and counterintelligence investigations or activities . • Analyze the information collected , Find system weaknesses and potentially exploitable Links . • Analyze different channels from the intelligence community 、 Threat information from different disciplines and institutions . • According to the background , Synchronize and place intelligence information , Find out the possible meaning . • Applications come from one or more different countries 、 region 、 The latest knowledge in the field of organization and Technology . • Applied language 、 Information collection with cultural and technical expertise 、 Analysis and other network security activities . • distinguish 、 Preserve and use the legacy of the system development process and use it for analysis . | |
7 | Collection and operation |
personal ( player ) Need to know and understand : •• Collection strategy 、 Technology and tool application . • The ability of network information and intelligence collection and the utilization of resource base . • Transformation between information needs and collection needs 、 track 、 Prioritization . • Network operation plan 、 Strategies and related resources . • Network operation strategy 、 Resources and tools . • The concept of network operation 、 Network operation terminology 、 Principles of network operation 、 function 、 Boundaries and effects . | |
personal ( player ) Required ability : •• Use appropriate strategies , Establish priorities through the process of collection management , To perform information collection . • Perform in-depth joint targeting , Implement the network security process . • Collect information as needed , Execute detailed plans and orders . • Support the collection of evidence about cyber threats , Mitigate or protect against possible or real-time cyber threats . | |
8 | survey |
personal ( player ) Need to know and understand : • Threat investigation 、 The report 、 Investigative tools and laws 、 statute . • Concepts and methods of malware analysis . • collect 、 pack 、 The process of transmitting and storing electronic evidence , And maintain the chain of custody . • Judicial process , Including factual statements and evidence . • Types and collections of persistent data . • Types and identification methods of digital forensics data . • The specific operational impact of network security vulnerabilities . | |
personal ( player ) Required ability : •• collect 、 Handle 、 preservation 、 Analyze and provide computer related evidence , To reduce network vulnerability , Support crime 、 cheat 、 Anti espionage or law enforcement investigations . | |
3.2 Competition score, weight and schedule
Module name | Competition time ( Hours ) | A weight | |
A | Infrastructure setting and security reinforcement | 3.0 | 20% |
B | Network security event response 、 Digital forensics investigation and application security | 40% | |
C | CTF Flag capture - attack | 3.0 | 20% |
D | CTF Flag capture - defense | 20% | |
A total of | 6 | 100% | |
Four 、 The way of competition
This event is a team event , Form teams based on institutions , Do not form teams across schools . Each team consists of 2 It's made up of two players , The number of teams from the same school should not exceed 1 the , Each team is limited to 2 A tutor .
5、 ... and 、 Competition process
( One ) Competition flow chart
( Two ) Competition schedule
The competition is limited to 1 Within days , The number of competitions is 1 site , The competition time is 3 Hours , Time is 9:00-16:00, The specific arrangement is as follows :
date | Time | matter | Participants | place |
Before the game 2 Japan | 20:00 front | The referee 、 arbitration 、 Supervise the check-in | Personnel | Accommodation Hotel |
Before the game 1 Japan | 09:00-12:00 | The team reports for duty , Arrange accommodation , Collect information | Personnel 、 Teams | Accommodation Hotel |
09:00-12:00 | Referee working meeting | Referee 、 Referee 、 Supervision team | Conference Room | |
13:00-14:30 | The team leader will | Each team leader 、 Referee | Conference Room | |
15:00-16:00 | Visit the stadium | Each team leader | Competition venues | |
16:00 | Check the enclosed stadium | Referee 、 Supervision team | Competition venues | |
16:00 | Back to the hotel | Team leader 、 supervise | Competition venues | |
competition same day | 07:30 | The referee is in position | The referee 、 supervise | Competition venues |
07:30-08:00 | Players draw lots , One time encryption | Contestant 、 The referee 、 supervise | Competition venues | |
08:00-08:30 | Players draw lots , Secondary encryption and admission | Contestant 、 The referee 、 supervise | Competition venues | |
08:30-08:40 | The contestants are in position , Read out the discipline of the examination room | Contestant 、 The referee 、 supervise | Competition venues | |
08:40-09:00 | Equipment inspection 、 modular A、 modular B The competition questions are distributed | Contestant 、 The referee 、 supervise | Competition venues | |
09:00-12:00 | modular A、B competition | Contestant 、 The referee 、 supervise | Competition venues | |
12:00-13:00 | lunch | Contestant 、 The referee 、 supervise | lounge | |
13:00-16:00 | modular C、D competition | Contestant 、 The referee 、 supervise | Competition venues | |
16:00 | The competition is officially over | Contestant 、 The referee 、 supervise | Competition venues | |
16:00-18:00 | Grade evaluation 、 verification 、 Decrypt 、 confirm | Referee 、 Scoring referee 、 supervise | Competition venues | |
18:00-19:00 | Results announced , Score submission | Referee 、 supervise | Competition venues |
6、 ... and 、 Competition volume
See the attachment for the sample questions of the competition paper .
7、 ... and 、 Competition rules
( One ) Application qualification
Contestants must be 2022 Annual full-time secondary vocational school students ; Five year full-time vocational college grades 1 to 3 ( Including grade three ) Registered students can participate in the competition . Contestants are not limited to gender , Must be no older than 21 One year old , The cut-off time for age calculation is in 2022 year 11 month 1 The date shall prevail .
( Two ) The competition is decided by drawing lots , Contestants are not allowed to leave the competition station during the competition .
( 3、 ... and ) Hardware equipment required for the competition 、 The system software and auxiliary tools shall be arranged by the organizing committee , Contestants are not allowed to bring their own hardware equipment 、 Software 、 Mobile storage 、 Auxiliary tool 、 Mobile communication, etc. enter the competition site .
( Four ) The contestants decide their own working procedures and time arrangement .
( 5、 ... and ) Contestants before the competition 20 Minutes to enter the competition station and receive the competition task , Relevant work can only be carried out after the competition officially starts .
( 6、 ... and ) During the competition , Players must strictly abide by the operating procedures , Ensure personal and equipment safety , And accept the supervision and warning of the referee . In case of equipment failure or damage due to player factors , Can't continue the competition , The referee has the right to decide to terminate the team's competition ; If the equipment fails due to non personal factors of the contestants , The chief referee shall make a ruling according to the specific situation .
( 7、 ... and ) The competition is over ( Or finish ahead of schedule ) after , Contestants stand up , No further operation is allowed after confirmation , Leave in order .
( 8、 ... and ) The final result of the competition is checked and confirmed to be correct by the referee 、 After the supervisor signs for confirmation , At the designated place , It shall be announced to all teams in advance in paper form at the designated point , After all teams have no objection, they will announce it at the closing ceremony .
( Nine ) The final results of each team in this event shall be entered into the competition management system by the information officer of the organizer . After the information clerk of the undertaking unit reviews the score data , Export and print the scores entered in the game management system , After being checked and verified by the event referee, sign . The information officer of the organizer shall upload the electronic version of the event performance information confirmed by the referee to the game management system , At the same time, the paper printed transcript signed by the chief referee shall be submitted to the competition Executive Committee .
( Ten ) After the competition, the expert working group will judge the score according to the referee , Analyze the contestants' knowledge points during the competition 、 Mastery of Technology , And report the analysis report to the competition Executive Committee Office , The office of the Executive Committee shall announce in due time according to the actual situation .
( 11、 ... and ) The original materials and final results scored by the referee in each competition link of the event shall be bagged and sealed for filing after being signed by the personnel of the supervision team and the referee , And sealed by the competition undertaking institution , Appoint a special person to keep it properly .
8、 ... and 、 Competition environment
1. Competition venues . The allocation of competition venues must meet the requirements of epidemic prevention , Set up a competition area at the competition site 、 The referee District 、 service area 、 Technical support area . Ensure good daylighting on site 、 Lighting and good ventilation ; Provide stable water 、 Electricity and power supply emergency equipment , Provide sufficient dry powder fire extinguishing equipment . At the same time, all instructor lounges are provided 1 between .
2. Competition equipment . The competition equipment shall be provided and guaranteed by the Executive Committee and the host school , The competition area prepares the software and hardware platforms required for the competition according to the number of teams , Provide standard equipment for the competition team .
3. Competition station . The station spacing and site space must meet the epidemic prevention requirements , Each working area of the competition site is equipped with single-phase equipment 220V/3A Above AC power supply . Each competition station shall be marked with number and isolated with isolation tape , Make sure the teams don't interfere with each other , Each competition station is equipped with 2 A work chair ( Stool ).
4. The technical support area is the workplace of technical support personnel , Provide network environment deployment and network security protection for contestants .
5. The service area provides medical and other service guarantee , And isolate... With isolation tape .
6. Competition station isolation and anti-interference . Isolation lines are marked between stations .
Nine 、 The technical specification
The competition combines the talent training needs of enterprise professional posts , The information network security project involved is under design 、 During the establishment process , There are mainly the following 8 National professional standards , Contestants are required to follow the following specifications in the implementation of competition projects :
Serial number | Standard No | Chinese standard name |
1 | GA/T 1389-2017 | 《 Information security technology network security level protection grading guide 》 |
2 | GB 17859-1999 | 《 Classification criteria for security protection level of computer information system 》 |
3 | GB/T 20271-2006 | 《 Information security technology - general security technical requirements for information systems 》 |
4 | GB/T 20270-2006 | 《 Information security technology network basic security technical requirements 》 |
5 | GB/T 20272-2006 | 《 Information security technology operating system security technical requirements 》 |
6 | GB/T 20273-2006 | 《 Information security technology database management system security technical requirements 》 |
7 | GA/T 671-2006 | 《 Information security technology terminal computer system security level technical requirements 》 |
8 | GB/T 20269-2006 | 《 Information security technology information system security management requirements 》 |
Ten 、 Technology platform
( One ) Competition equipment
Serial number | Equipment name | Number | Equipment requirements |
1 | Network security competition platform | 1 | 1. Be able to complete the infrastructure setting 、 Safety reinforcement 、 Security incident response 、 Network security data forensics 、 Application security 、CTF Flag grabbing attack 、 CTF Knowledge of flag grabbing defense 、 The skill content competition environment realizes , Can effectively support 300 Human scale , Have a centralized answer environment based on the same scene of the competition content of this procedure . 2. Standard configuration 2 Gigabit Ethernet port ,Intel processor , Greater than or equal to 16G Memory ,SSD +SATA Hard disk . Scalable to multiple virtualization platforms , Support cluster management , Incremental backup is adopted for synchronization , Virtualization management adopts standards libvirt Interface ; Support multi-user concurrent online competition , According to different actual combat tasks, the target virtualization template is issued for automatic scheduling , There is no need to manually configure the address in the whole process ,VLAN And IP It can be set according to the competition requirements ; Provide individual soldiers to pass through the pass 、 Group scuffle and other actual combat modes , There is no need for manual switching between phases , The system automatically processes ; Provide more than 20 Different levels 70 A new attack and defense scene ; modular B、C Automatic evaluation of the whole process , Support the uploading of image elements during the competition , The ranking decision strategy is greater than or equal to 12 Kind of ; Custom animation situation display , Detailed analysis of results ; Support monitoring abnormal virtual machines , Simultaneous detection FTP、HTTP、ICMP、SMTP、SSH、TCP and UDP agreement , The service port supports service ports within the valid range ; Support full encryption , Supports the import of encrypted files , The encryption method is asymmetric encryption , The device can randomly generate passwords . |
2 | PC machine | 2 | CPU Main frequency >=2.8GHZ,>= Four cores, four threads ; Memory >=8G; Hard disk >=500G; Support hardware virtualization . |
( Two ) Software technology platform :
The application system environment of the competition is mainly Windows and Linux System oriented , The following versions are involved :
1. The physical machine installs the operating system : Microsoft Windows 7(64 position ) Chinese trial version or Microsoft Windows 10(64 position ) Chinese trial version .
2. Virtual machine installation operating system :
Windows System ( Trial version ):Windows XP、Windows 7、Windows 10、Windows Server2003 And above ( Determine according to the reality of the proposition ).
Linux System :Ubuntu、Debian、CentOS( The specific version is determined according to the actual situation of the proposition ).
3. Other major applications are ( The actual competition environment may not be limited to the following software ):
VMware workstation 12 pro And above version free version
Putty 0.67 And above
Python 3 And above
Chrome browser 62.0 And above
RealVNC client 4.6 And above
JDK(Java Development Kit)7.0 And above
11、 ... and 、 Grade evaluation
( One ) The referee's scoring method
The on-site referee team supervises the on-site computer test score , The scoring referee is responsible for the contestants' submission of work scores , The referee is responsible for the whole process of the competition .
Supervisors shall be stationed at the competition site 、 Referee 、 Technical support team, etc , A clear division of responsibilities . The on-site referee is responsible for the communication with the contestants and the sending and receiving of test papers and other materials , Be responsible for equipment problem confirmation and on-site execution ; The technical support engineer is responsible for the emergency response of all station equipment , Be responsible for the equipment emergency treatment after being confirmed by the referee .
( Two ) How to produce results
1. Scoring stage :
Competition stage | Stage name | Mission phase | Scoring method |
modular A The weight 20% | Infrastructure settings 、 Safety reinforcement | Mission 1…N | The referee scored objectively |
modular B The weight 40% | Security incident response 、 Network security data forensics 、 Application security | Mission 1…N | Computer test score |
modular C The weight 20% | CTF Flag grabbing attack 、 | System attack and defense drill | Computer test score |
modular D The weight 20% | CTF Flag grabbing defense | System attack and defense drill | The referee scored objectively |
2. modular A、 modular B Scoring rules
modular A And modules B The total score is 600 branch , It is divided into N A mission , The specific score of each question is indicated in the competition question ; modular A Infrastructure settings 、 The score of the safety reinforcement part shall be objectively scored by the scoring referee ; modular B Security incident response 、 Network security data forensics 、 Application security and other parts are automatically scored and ranked by the system , Publicly display .
3. modular C、 modular D Scoring rules
modular C The total score is 200 branch , Get the attack according to the player “FLAG” Is worth the corresponding score . The system automatically scores and ranks , Publicly display .
modular D The total score is 200 branch , According to the contestant's answer , Objective scoring by the scoring referee .
In the process of answering questions, contestants shall not answer questions in violation of the requirements of the competition questions , No score shall be obtained in the form of violation , Do not attack the referee server in violation of regulations 、 gateway 、 System server and other non target targets , If the player is detected to have illegal attacks , If you continue to attack after one warning , The team was ordered to terminate the competition , Qingli comes out .
Twelve 、 Stadium plan
In order to ensure the smooth progress of the event , Avoid uncontrollable but possible emergencies during the competition , The event plan is designed by the reliability of the event 、 The emergency treatment plan for faults consists of two parts .
- Event reliability design
1. Power system reliability design
The power supply load matches the power requirements , Prevent overloading of electronic equipment during operation, resulting in fire hazards or power interruption ; Provide three power grounding guarantees , Eliminate the possibility that static electricity may cause equipment restart during operation 、 A short circuit 、 Leakage and other security threats ; Wiring strong and weak current separation , Prevent interference ; The power supply of each area shall be independent , Mutual noninterference .
2. Reliability design of weak current system
The weak current system must be in good operating condition , The system shall have long-term and stable working ability , There should be quick solutions in case of emergencies , Ensure the reliable operation of the system . The weak current system shall be isolated from the power system , Prevent interference from causing failure .
3. Reliability design of network equipment
Network equipment must operate stably , Meet bandwidth requirements , Reserved port backup , Communication cable 、 Equipment reserve backup , With rapid fault recovery mechanism , Provide necessary redundant backup design .
4. Design attack and defense platform reliability
The platform must support cluster function , Support load sharing under large-scale traffic , At the same time, it can provide backup for competition data 、 Fallback mechanism . Redundant backup mechanism , Recover the fault problem in the shortest time . The platform shall provide access control mechanism , Have anti attack means , Ensure the stable operation of the platform .
5.PC Reliability design
PC The deployment of must ensure good running state , There should be quick solutions in case of emergencies , Ensure the reliable operation of the system . The system specifications must meet the requirements , Ensure good performance and stable operation .
- Emergency treatment plan for faults
1. Contestant PC fault
Like contestants PC In trouble , First judge whether it is a hardware fault or a software fault . Software failure or stuck phenomenon is right PC To restart , because PC Equipped with restore card , The system can be restored to its original state , The recovery time is about 30 second ; Replace the standby unit after the hardware fault is approved by the on-site referee , The recovery time is about 1 minute . keyboard 、 If the mouse fails, replace it in time , The recovery time is about 1-3 minute . It will not affect students' performance .
2. The cable connection of the competition station is faulty
If the competition station encounters network connection problems , The on-site referee judged that the cable physical connection problem , Non player setting operation leads to , The spare cable shall be replaced in time , The recovery time is about 30 second ; Physical failure of more than two network cables in the competition station , The competition station shall be changed with the permission of the on-site referee , The recovery time is about 3-5 minute .
3. Competition station power failure
In case of power failure of the competition station , Change the standby station with the permission of the referee . Recovery time 3-5 minute .
4. Network equipment switch failure
Replace the standby switch , The recovery time is about 5-10 minute ; If the jumper cable fails, replace the spare cable in time ( Optical fiber and network cable ), The recovery time is about 3-5 minute .
5. Attack and defense platform cluster failure
The main equipment of the server cluster fails , Enable standby cluster devices , Mutual data backup , The cluster recovery time is about 5-10 minute . Server cluster slave device failure , Replace spare equipment , The recovery time is about 5-10 minute . Results are saved in real time , It will not affect students' performance .
6.WEB Application Firewall failure
In case of encounter WAF Equipment failure , Impact access , Cancel the protection policy or cancel WAF Device to connect , The recovery time is about 1-3 minute .
7. Server area power supply problem
If there is a power supply problem in the server area ,UPS The power supply can support about 20-30 minute .
13、 ... and 、 What we need to know about the competition
( One ) Instructions for teams
1. The participating team should participate in the closing ceremony and other events organized by the event organizer .
2. During the event , The team leader and other members of the team shall not contact the referee without permission , Anyone who finds fraud , Disqualification , The result is invalid .
3. All participants must complete the evaluation of the event in accordance with the requirements of the event rules .
4. For teams that hinder the fairness and normal progress of the competition , Depending on the circumstances , Give warning according to relevant management measures 、 Cancel the competition result 、 Circulate a notice of criticism, etc .
( Two ) Instructions for team leaders
1. The competition leader is determined by the College 1 people , The team leader of the competition should be the middle-level or above management personnel of the participating institutions or the personnel of the education administrative department , Be familiar with the competition process , Have the ability of management, organization and coordination .
2. The team leader should attend the pre match team leader meeting on time , You must not be absent without cause .
3. The team leader is responsible for organizing the participating teams of the school to participate in various events .
4. The team leader should actively do a good job in the service of the participating team of our school , Coordinate the participating teams and event organizations 、 Host the docking of colleges and universities , Do a good job in the epidemic prevention work of the team according to the epidemic prevention requirements .
5. The team believes that there is equipment that does not meet the competition regulations 、 Tools 、 Software , An unfair judgment 、 Reward , And violations of staff , The team leader must submit written appeal materials to the competition arbitration group . Each team leader shall take the lead in obeying and enforcing the final arbitration result of the appeal , And ask the instructor 、 Players obey and execute .
( 3、 ... and ) Instructions for instructors
1. Instructors should reasonably formulate training programs according to professional teaching plans and competition rules , Carefully guide the players' training , Cultivate the players' comprehensive professional ability and good professional quality , Overcome utilitarian thinking , Avoid learning for the game 、 Learn by race .
2. The instructor should check the notice and content of the competition on the special website of the competition in time , Carefully study and master the rules of this competition 、 Technical specifications and field requirements , Guide the players to make all technical preparations and competition preparations before the competition .
3. The instructor should handle the insurance of the contestants according to the requirements of the competition rules , Do a good job of team epidemic prevention according to the requirements of epidemic prevention , And actively do a good job in the safety education of players .
4. Guide teachers to participate in events observation and other activities , Do not enter the field in violation of the competition regulations , Interfere with the normal progress of the competition .
( Four ) Instructions for contestants
1. All contestants shall do a good job in individual and team epidemic prevention according to the epidemic prevention requirements , Carry forward good moral fashion , Follow the command , Obey the referee , Don't cheat . If a fraud is found , Disqualification , Invalid ranking .
2. Contestants should truthfully fill in their personal information according to relevant requirements , Otherwise, you will be disqualified from the competition .
3. Contestants should arrive at the venue at the specified time , With the uniformly printed entry certificate 、 Checking and recording of valid identity documents , Enter as required , Don't be late and leave early . Do not carry any electronic equipment or other information 、 Supplies enter the stadium .
4. Participants should carefully study and understand the relevant documents of this competition , Consciously abide by the competition discipline , Obey the command , Follow the arrangements , Civilized competition .
5. Contestants should enhance their role awareness , Scientific and reasonable time allocation .
6. Contestants should sit in the designated position according to relevant requirements .
7. Contestants must start the competition after confirming that the competition contents and on-site equipment are correct . During the competition , It is really due to computer software or hardware failure , That makes the operation impossible to continue , Confirmed by the project referee , Enable the standby computer .
8. All contestants must operate the competition equipment according to the specifications . Once there is a serious safety accident , With the approval of the chief referee, they will be disqualified immediately .
9. Contestants should read the naming requirements of competition documents in the competition questions in detail , No place names of competitors shall be marked in the submitted competition documents 、 School name 、 full name 、 Entry number and other information , Otherwise, the competition results will be cancelled .
10. The race is over , All contestants should stand up , End operation , Put the data and tools on the operating platform in order , The staff can leave the stadium after counting . Don't take any information away when you leave the field .
11. During the competition , Without the approval of the Executive Committee , Contestants are not allowed to accept interviews related to the contents of the competition conducted by other units and individuals . Contestants shall not publish the relevant information of the competition without permission .
( 5、 ... and ) Instructions for staff
1. Establish a service concept , All for the sake of the players , In a highly responsible spirit 、 Serious attitude and rigorous and meticulous style , Under the leadership of the event organization department , Do a good job of post work according to their respective responsibilities and requirements .
2. All staff must wear certificates , Be devoted to one's duty , decide a case according to law , keep a secret .
3. Be polite , Maintain a good image , Familiar with the event guide .
4. Consciously abide by the discipline and rules of the event , Obey the allocation and division of labor , Ensure the smooth progress of the competition .
5. advance 30 Minutes to the field , Strictly abide by the work post , Don't be late , Don't leave early , Do not leave the post without reason , In special circumstances, it is necessary to ask for leave from the leader of the working group .
6. Be familiar with the competition rules , Work in strict accordance with working procedures and relevant regulations , In case of an emergency , According to the emergency plan , Organize and command personnel evacuation , Ensure personnel safety .
7. If a staff member commits fraud in the competition , Immediate disqualification , And deal with it seriously .
8. Keep communication open , Obey the unified leadership , Strictly abide by competition discipline , Strengthen cooperation and cooperation , Improve work efficiency .
fourteen 、 Appeal and arbitration
All participating teams shall be responsible for the instruments that do not comply with the regulations of the competition and events 、 equipment 、 work clothes 、 material 、 thing 、 Computer hardware and software 、 Competition tools 、 Articles , Competition referee 、 Field management , And the non-standard behavior of staff , You can appeal to the competition arbitration group . The main body of the appeal is the team leader . The team leader of the participating team can ( The players have completed all the competition contents in the field )2 Submit a written appeal to the arbitration panel within hours , Beyond the time limit, it is not handled .
Written appeal response to the phenomenon of appeal Events 、 Time of occurrence 、 People involved 、 The basis of appeal shall be fully 、 A realistic narrative , And signed by the team leader . Non written complaints are inadmissible .
After receiving the appeal report, the competition arbitration working group will 2 Organize reconsideration within hours , And promptly inform the appellant of the reconsideration result in writing . The complainant still disagrees with the result of the reconsideration , Can be saved by province ( City ) The team leader appealed to the regional Arbitration Committee . The arbitration result of the division arbitration committee shall be the final result .
The arbitration result shall be signed and received by the complainant , Can't collect , If the complainant leaves at the agreed time and place , It is deemed to have waived the appeal on its own .
The complainant may waive the appeal at any time , Do not take drastic actions to disturb the order of the stadium for any reason .
15、 ... and 、 Competition observation
This event will provide an open viewing area , Use the large screen to display the process of Cyberspace Security competition in real time .
The competition environment is designed according to the competition needs and professional characteristics , On the premise that the competition will not be disturbed, some venues will be opened safely . The observation personnel shall wear the observation certificate and follow the designated route under the guidance of the staff 、 Watch the game on site in the designated area .
sixteen 、 Live broadcast of the competition
The competition questions shall be kept confidential before the competition 、 Equipment installation and debugging 、 Live video recording of key links such as software installation . The competition is broadcast live , The opening and closing ceremony of the competition 、 The whole process of the competition was videotaped .
This event will be made after the competition, and the excellent contestants will be interviewed 、 Interview with excellent instructors 、 Judges, experts and business people interview video materials .
seventeen 、 Resource transformation
According to relevant requirements , The competition resource transformation plan shall be published at the same time as the requirements and procedures ; The organizer will 30 Submit the resource transformation implementation plan to the competition Executive Committee Office within days , Complete the supplement and improvement of new resources in three months , Complete the transformation of all resources within half a year .
( One ) The main resources obtained during the competition
1. Competition sample questions 、 Question bank ;
2. The scoring standard of competition questions ;
3. Assessment environment description ;
4. Audio and video recording of the competition process ;
5. Judges 、 The referee 、 Expert comments and technical analysis report ;
6. Good players 、 Instructor interview .
( Two ) Basic scheme and presentation form of resource transformation
The results of resource transformation are in accordance with industry standards 、 Conform to the curriculum standards 、 Highlight skill characteristics 、 Show competitive advantage , Form to meet the teaching needs of vocational education 、 Reflect the advanced teaching mode 、 Shared vocational education teaching resources reflecting the advanced level of vocational education . The results of resource transformation include basic resources and expanded resources , Fully reflect the characteristics of skill assessment in this competition : The results of resource transformation should include basic resources and expanded resources .
1. Basic resources
Basic resources are displayed according to style 、 Skill summary 、 Three teaching resource settings .
(1) Style display . After the game, the time of real-time production 15 About minutes of event publicity film , And how long 10 The winning team in about minutes ( player ) Show your style . For professional media to broadcast .
(2) Skill summary . Including skills Introduction 、 Key points of skill operation 、 Evaluation index, etc .
(3) Teaching resources . Teaching resources fully cover the contents of the competition . Including teaching programs 、 Training To guide the 、 Homework / Mission 、 experiment / Practical training / Internship resources, etc , Its presentation form is mainly presentation 、 picture 、 Operation process demonstration video 、 Animation and related micro courses 、 Micro resources, etc .
2. Expand resources
Expanding resources means reflecting the characteristics of skills 、 It can be applied to all teaching and training links 、 Relatively mature and diversified auxiliary resources supporting skill teaching and learning process .
( 3、 ... and ) Technical standards of resources
Resource transformation results are in text documents 、 Presentation 、 Video file 、Flash file 、 graphics / Image materials and web resources .
( Four ) Submission method and copyright of resources
The copyright of the transformation results of competition resources is shared by the Executive Committee of skill competition and the Executive Committee of competition .
( 5、 ... and ) Use and management of resources
The use and management of resource transformation achievements shall be uniformly used and managed by the competition Executive Committee , Together with the event organizer 、 Competition experts , Contact the publishing house to edit and publish high-quality resources such as competition training materials .
The attachment :
2022 Guizhou Vocational College skills competition ( Secondary vocational group )
Network security competition questions ( Sample questions )
( Total score 1000 branch )
The title explains
One 、 Introduction to the competition
“ Network security ” The competition is divided into A. Infrastructure setting and security reinforcement ;B. Network security event response 、 Digital forensics investigation and application security ;C.CTF Flag capture - attack ;D. CTF Flag capture - Defense and other four modules . The competition schedule and score weight are shown in table 1.
surface 1 Competition schedule and score weight
Module number | Module name | Competition time ( Hours ) | total |
A | Infrastructure setting and security reinforcement | 3.0 | 20% |
B | Network security event response 、 Digital forensics investigation and application security | 40% | |
C | CTF Flag capture - attack | 3.0 | 20% |
D | CTF Flag capture - defense | 20% | |
A total of | 6 | 100% | |
Two 、 Competition considerations
1. It is forbidden to carry and use mobile storage devices during the competition 、 Calculator 、 Communication tools and references .
2. According to the competition environment provided by the competition , Check the listed hardware devices 、 Software inventory 、 Whether the material list is complete , Whether the computer equipment can be used normally .
3. Before doing anything , Please read all the tasks in each section . There may be some correlation between tasks .
4. In the process of operation, it is necessary to save relevant results in time according to the answer requirements . After the competition , Keep all equipment running , The judgment is based on the final submitted results .
5. After the competition , Competition equipment 、 Please keep the software and questions in your seat , All items used in the competition are prohibited ( Including test papers, etc ) Get off the court .
6. It is forbidden to fill in marks irrelevant to the competition on the submission , In case of violation of regulations , Can be regarded as 0 branch .
Competition content
modular A Infrastructure setting and security reinforcement
( This module consists of 200 branch )
One 、 Project and task description
Suppose you are a network security engineer in an enterprise , For enterprise server system , Ensure the normal operation of all services according to the task requirements , And through the comprehensive use of login and password policies 、 Database security policy 、 Traffic integrity protection strategy 、 Event monitoring strategy 、 Firewall strategy and other security strategies to improve the network security defense ability of the server system . This module requires screenshots of specific tasks and corresponding text descriptions , And word Document writing , With PDF Format preservation , And take the match number as the file name .
Two 、 Server environment description
IDS: Intrusion detection system server (Snort), The operating system is Linux
LOG: Log server (Splunk), The operating system is Linux
Web:IIS The server , The operating system is Windows
Data: database server (Mysql), The operating system is Linux
3、 ... and 、 Specific tasks
Task a Login security
1. Password policy (IDS,LOG,Web,Data)
a. The minimum password length shall not be less than 12 Characters ;
2. Login strategy (IDS,LOG,Web,Data)
a. When the user logs in to the system , Should have “For authorized users only” Prompt information ;
3. User permission assignment (WEB)
a. Prohibit guest account login and access ;
Task 2 Database hardening (Data)
1. Run safely as a normal account mysqld, prohibit mysql Run with administrator account privileges ;
2. Delete the default database (test);
Task three Web Safety reinforcement (Web)
1. Delete default site ;
2. Restrict directory execution permissions , Set the execution permission to none for the picture or upload directory ;
Task 4 Flow integrity protection (Web,Data)
1.HTTP Redirect HTTPS, Use only HTTPS Agreement to visit the website (Web);
2. Prevent passwords from being stolen , Log in with a certificate only SSH(Data).
Task five Event monitoring
1. Web The server turns on the audit policy :
Login Events success / Failure ;
Privilege use success ;
Policy changes success / Failure ;
Process tracking success / Failure ;
Task six Service reinforcement ssh\vsftpd
1. modify ssh The service port is 2222;
2.ssh prohibit ROOT User remote login ;
Task seven Firewall policy
All servers turn on the firewall , In order to prevent blackmail virus attack, the firewall is reinforced :
1.Windows System Disabled 445 port ;
2.Linux System Disabled 23 port ;
modular B Cyber security incidents 、 Digital forensics investigation and application security
( This module consists of 400 branch )
One 、 Project and task description :
Suppose you are a member of a network security technical support team , The server system of an enterprise was attacked by hackers , Your team came to help the enterprise investigate and track the source of this cyber attack , Analyze the attack methods of hackers , Discover system vulnerabilities , Submit network security incident response report , Fix system vulnerabilities , Delete the back door created by the hacker in the system , And help the system return to normal operation .
Two 、 Server environment description
operating system :Windows/Linux
3、 ... and 、 Specific tasks
Task a Data analysis
1. Use Wireshark View and analyze xxx Under the desktop capture.pcapng Package file , find telnet User name and password of the server , And use the password as Flag Value submission .
2. Use Wireshark View and analyze xxx Under the desktop capture.pcapng Package file ,ftp The server has finished transferring files , Take the first instruction after logging in to the server as Flag Value submission .
3. Use Wireshark View and analyze xxx Under the desktop capture.pcapng Package file ,web The server address is 192.168.181.250, The scripting language used is php, Use the server php The version number of is used as Flag Value submission .
4. Use Wireshark View and analyze xxx Under the desktop capture.pcapng Package file , There are a lot of these data ICMP message , One of the devices is a router ,IP The address is 192.168.181.25, Send the unsolicited message from the router ping Number of requests as Flag Value submission .
Task 2 Digital forensics
1. Hackers successfully entered windows2008 And created multiple users , Use the user name created by the hacker as flag Value submission { name 1- name 2-……}.
2. Find hacker login ip, take ip Address for submission .
3. Hackers have brutally cracked the database many times , Take the number of attacks as flag Value submission .
4. Find the time when the hacker successfully cracked the database , Change the time as flag Value submission .
Task three Memory forensics
1. Get the user from memory admin And crack the password , With flag{admin,password} Form submission ( The password for 6 position );
2. Get the current system ip Address and host name , With flag{ Host name ,ip} Form submission ;
3. There is a on the desk flag file , Please get flag Contents of the file ;
4. The malicious process registered the service in the system , Please name the service with flag{ service name } Form submission ;
Task 4 Vulnerability scanning and exploitation
1. Via local PC Medium penetration test platform Kali2.0 For the server scenario Windows2020 Conduct system service and version scanning penetration test , And display the operation in the result 3389 The service version information string corresponding to the port is used as Flag Value submission ;
2. stay msfconsole of use search The command to search MS12020 RDP Access to the attack module is denied , The vulnerability disclosure time in the echo result is taken as Flag value ( Such as :2012-10-16) Submit ;
3. stay msfconsole In the use of MS12020 RDP Access denied to vulnerability assisted scanning module , Call the command of this module as Flag Value submission ;
4. In the 3 Check the options you need to set based on the questions , And take the option name that must be set in the echo as Flag Value submission ;
5. Use set Command set target IP( In the 4 Based on the question ), And detect whether the vulnerability exists , Run this module to take the fourth word in the first line of the echo result as Flag Value submission ;
Task five Windows Operating system penetration test
1. Find the task server network adapter information , Will be preferred DNS Server address as Flag Value submission ;
2. Find it on the desktop 111 The suffix in the folder is .docx The file of , Use document content as Flag Value submission ;
3. Find it on the desktop 222 Picture files in folders , Use the English words in the picture as Flag Value submission ;
Task six Emergency response
1. Hackers break into local servers through the network , stay Web There is a Trojan link on the home page of the server , Please find this link and delete it , The third word displayed in the title bar of the first row of the home page after deleting the link , As flag Submit .
2. Hackers break into the database server of the local server , And added division admin A super user with administrator privileges other than , Please find this user and delete the user , Use this user name and password as flag Submit .
modular C CTF Flag capture - attack
( This module consists of 200 branch )
One 、 Project and task description
Suppose you are a network security penetration test engineer in an enterprise , Be responsible for the security protection of some servers in the enterprise , In order to better find various problems and vulnerabilities that may exist in the enterprise network . You try to use all kinds of attacks , Attack a specific target , In order to understand the latest attack methods and technologies , Understand the mentality of network hackers , To improve your defense strategy .
Please according to 《 Field parameter table 》 Information provided , Log in to the attacker using Google browser on the client .
Two 、 Operating system environment description
Client operating system :Windows 10
Attacker operating system :Kali Linux 2019 edition
Target server operating system :Linux/Windows
3、 ... and 、 Vulnerability description
1. The vulnerability in the server may be a conventional vulnerability or a system vulnerability ;
2. The website on the target server may have a vulnerability of command injection , Ask contestants to find vulnerabilities related to command injection , Exploit this vulnerability to obtain certain permissions ;
3. There may be a file upload vulnerability on the website on the target server , Ask the contestants to find the loopholes related to file upload , Exploit this vulnerability to obtain certain permissions ;
4. There may be a File Inclusion Vulnerability in the website on the target server , Ask the contestant to find the relevant vulnerabilities contained in the file , Combine with other vulnerabilities to obtain certain permissions and raise rights ;
5. The services provided by the operating system may contain vulnerabilities in remote code execution , Ask the user to find the service for remote code execution , And use this vulnerability to obtain system permissions ;
6. The service provided by the operating system may contain a buffer overflow vulnerability , Services that require users to find buffer overflow vulnerabilities , And use this vulnerability to obtain system permissions ;
7. There may be some system backdoors in the operating system , Players can find this back door , And use the reserved back door to directly obtain the system permission .
Four 、 matters needing attention
1. Cannot attack the referee server , If the attack continues after one warning, the team will be ordered to leave the field ;
2.Flag The value is the unique identification of each target server , Each target server has only 1 individual ;
3. After entering the target, the competitor shall not close the target 、 Change Password 、 Restart or shut down the target 、 Delete or modify flag、 Create unnecessary files and other operations ;
4. After logging into the automatic scoring system , Submit to the target server Flag value , At the same time, you need to specify the target server IP Address ;
5. There are target planes with different basic scores according to the difficulty in the field , For each target server , The first three get Flag The value team will add points to the basic points , The total score of each team in this stage is included in the stage score , The specific scoring rules refer to the scoring standard of the field ;
6. There is no supplementary time for this link .
modular D CTF Flag capture - defense
( This module consists of 200 branch )
One 、 Project and task description
Suppose you are a network security engineer of a security enterprise , Responsible for penetration test and security protection of several servers , These servers may have various problems and vulnerabilities . You need to perform penetration testing and security protection on these servers as soon as possible . Each team has its own fortress server , Other teams cannot visit . Contestants scan 、 Penetration test and other means to detect the security defects in your fortress server , Carry out targeted reinforcement , So as to improve the security and defense performance of the system .
Please according to 《 Field parameter table 》 Information provided , Use Google browser on the client to log in to the fortress server that needs to be reinforced .
Two 、 Operating system environment description
Client operating system :Windows 10
Attacker operating system :Kali Linux 2019 edition
Fortress server operating system :Linux/Windows
3、 ... and 、 Vulnerability description
1. The vulnerability in the fortress server may be a conventional vulnerability or a system vulnerability ;
2. The website on the fortress server may have a vulnerability of command injection , Ask contestants to find vulnerabilities related to command injection , Exploit this vulnerability to obtain certain permissions ;
3. There may be a file upload vulnerability on the website on the fortress server , Ask the contestants to find the loopholes related to file upload , Exploit this vulnerability to obtain certain permissions ;
4. There may be a File Inclusion Vulnerability in the website on the fortress server , Ask the contestant to find the relevant vulnerabilities contained in the file , Combine with other vulnerabilities to obtain certain permissions and raise rights ;
5. The services provided by the operating system may contain vulnerabilities in remote code execution , Ask the user to find the service for remote code execution , And use this vulnerability to obtain system permissions ;
6. The service provided by the operating system may contain a buffer overflow vulnerability , Services that require users to find buffer overflow vulnerabilities , And use this vulnerability to obtain system permissions ;
7. There may be some system backdoors in the operating system , Players can find this back door , And use the reserved back door to directly obtain the system permission .
Four 、 matters needing attention
1. Each player needs to take screenshots of reinforcement points and key processes , And make its own system defense implementation report , The final score shall be subject to the system defense implementation report .
2. When strengthening the system, it is necessary to ensure the availability of services provided by the fortress server ;
3. Cannot attack the referee server , If the attack continues after one warning, the team will be ordered to leave the field ;
4. There is no supplementary time for this link .
边栏推荐
- RGB LED infinite mirror controlled by Arduino
- A reason that is easy to be ignored when the printer is offline
- 【Rust 笔记】15-字符串与文本(下)
- LaMDA 不可能觉醒吗?
- MatrixDB v4.5.0 重磅发布,全新推出 MARS2 存储引擎!
- Brief introduction to tcp/ip protocol stack
- Introduction et expérience de wazuh open source host Security Solution
- Leetcode-3: Longest substring without repeated characters
- 全排列的代码 (递归写法)
- MIT-6874-Deep Learning in the Life Sciences Week 7
猜你喜欢
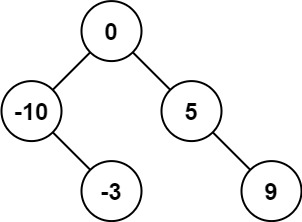
LeetCode 0108.将有序数组转换为二叉搜索树 - 数组中值为根,中值左右分别为左右子树
中职网络安全技能竞赛——广西区赛中间件渗透测试教程文章
Error ora-28547 or ora-03135 when Navicat connects to Oracle Database
Data visualization chart summary (I)
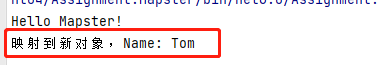
4. 对象映射 - Mapping.Mapster
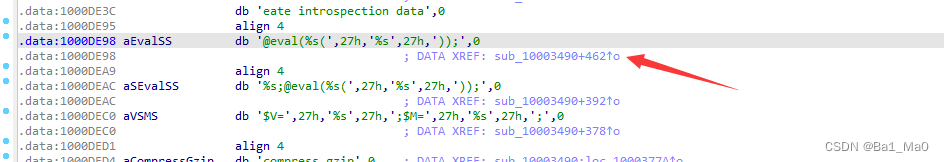
Analysis of backdoor vulnerability in remote code execution penetration test / / phpstudy of national game title of national secondary vocational network security B module
![[practical skills] technical management of managers with non-technical background](/img/4d/1081c71df6ee2087359111baf7498a.png)
[practical skills] technical management of managers with non-technical background
leetcode-6110:网格图中递增路径的数目
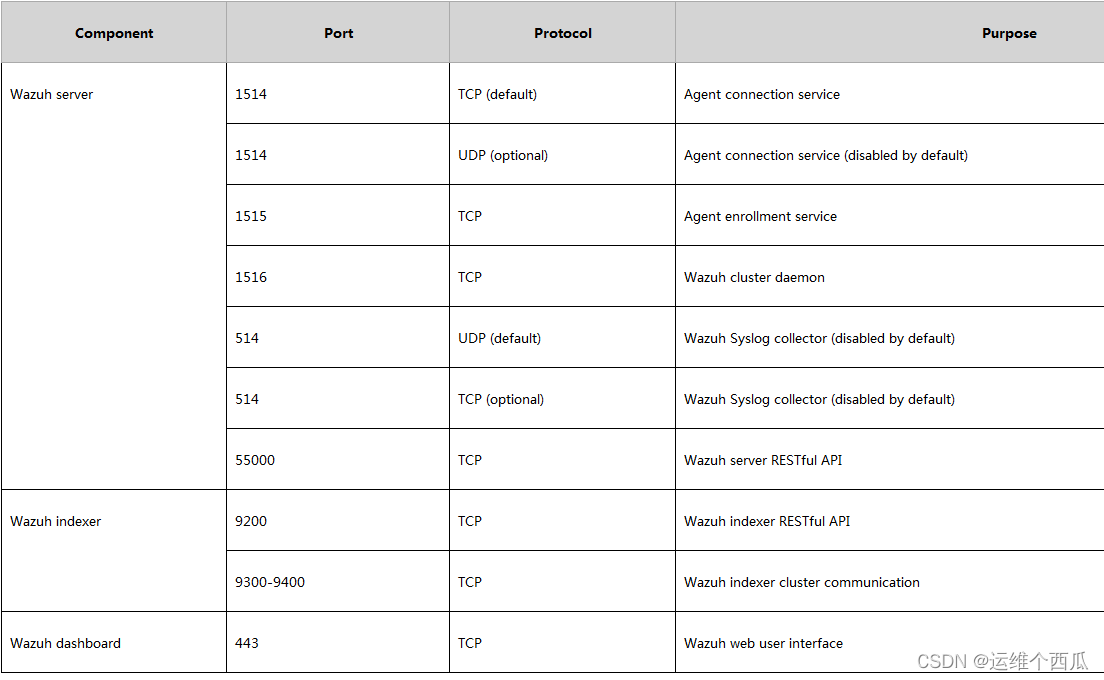
Wazuh開源主機安全解决方案的簡介與使用體驗
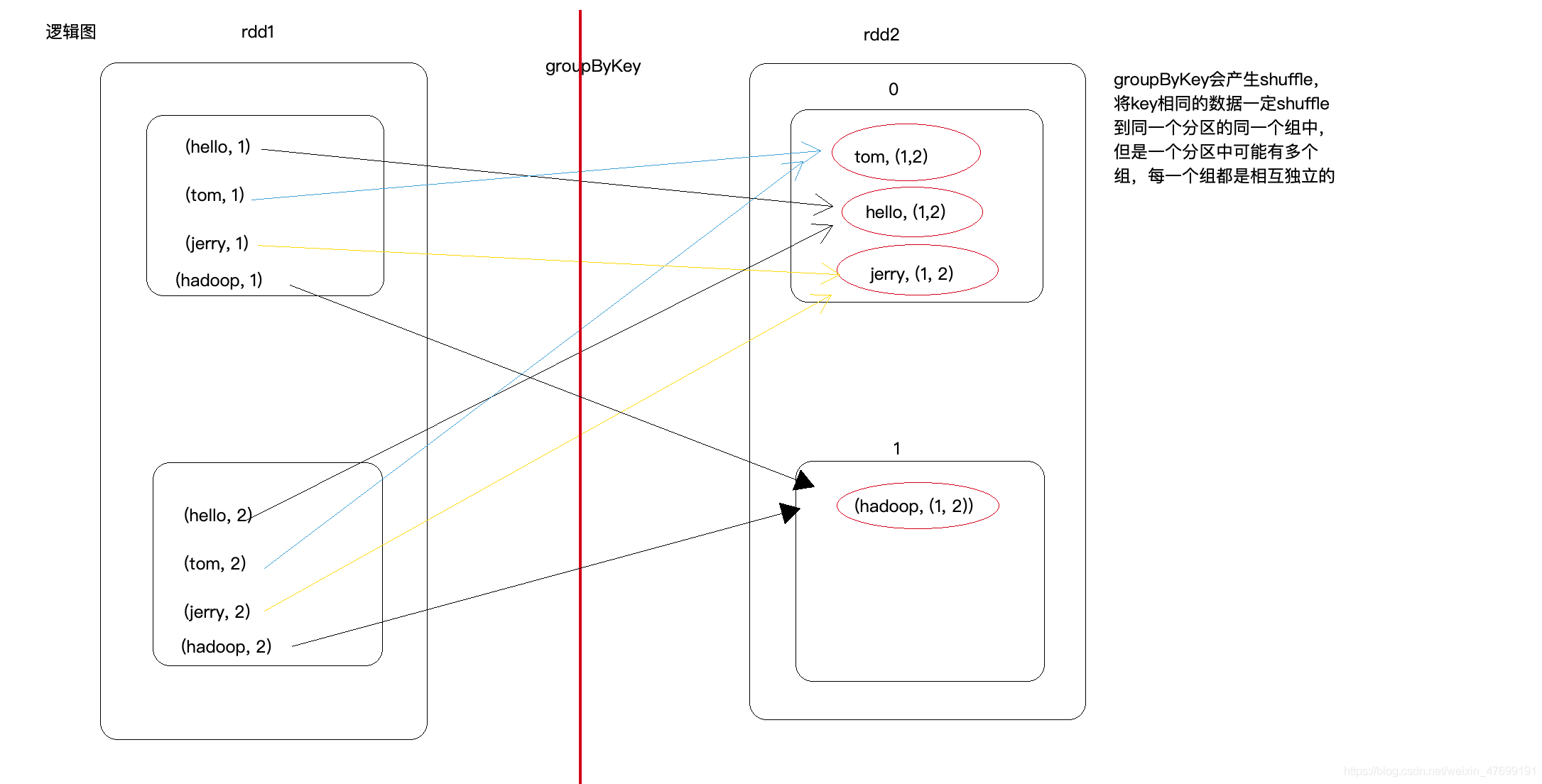
Groupbykey() and reducebykey() and combinebykey() in spark
随机推荐
The difference between CPU core and logical processor
Appium自动化测试基础 — Appium测试环境搭建总结
One question per day 1765 The highest point in the map
Daily question 1984 Minimum difference in student scores
对for(var i = 0;i < 5;i++) {setTimeout(() => console.log(i),1000)}的深入分析
Leetcode-6109: number of people who know secrets
Daily question 1688 Number of matches in the competition
剑指 Offer II 058:日程表
SPI details
QT判断界面当前点击的按钮和当前鼠标坐标
Implement a fixed capacity stack
中职网络安全技能竞赛——广西区赛中间件渗透测试教程文章
1040 Longest Symmetric String
[rust notes] 17 concurrent (Part 1)
【Rust 笔记】16-输入与输出(上)
927. 三等分 模拟
leetcode-6108:解密消息
【Rust 笔记】13-迭代器(下)
Real time clock (RTC)
LeetCode 0107.二叉树的层序遍历II - 另一种方法