当前位置:网站首页>2022 National Games RE1 baby_ tree
2022 National Games RE1 baby_ tree
2022-07-06 12:57:00 【Hofiy】
2022 National Games Re1 baby_tree
Preface
Open questions , It was found to be a large string of non code text .( Cute new panic )
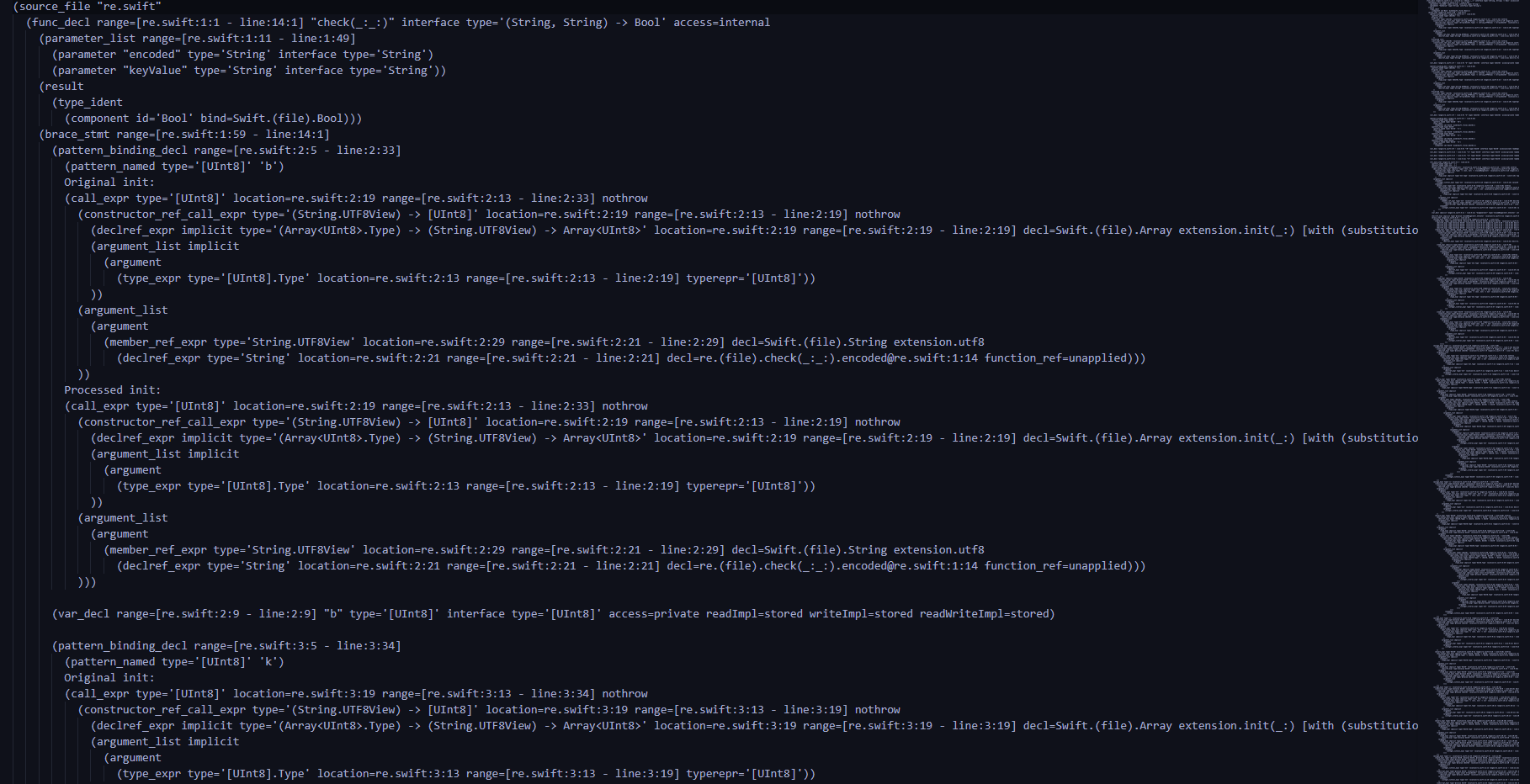
First step
Combined with file suffix and title baby_tree, It can be understood that this is ast Syntax tree . It can be found at the beginning of the file that this is caused by swift Written program , namely "re.swift".
After searching relevant information, I learned ,
Swift compiler has an interesting mode: -dump-ast which outputs the abstract syntax tree of a swift source code. AST is used to represent the source code in form of a tree containing syntactic information.
From this, we can know the test site of this question , analysis swift Of ast grammar , Judge the encryption process , obtain flag, To analyze .(tips: It should also be able to deploy locally swift Environmental comparative analysis )
The second step
1. Find the ciphertext
Because of the AST share 635 That's ok , Reading efficiency is too low , So I plan to find the ciphertext first , Find a breakthrough . In the file 528 OK, let's start , Found the ciphertext , And found traces of comparison .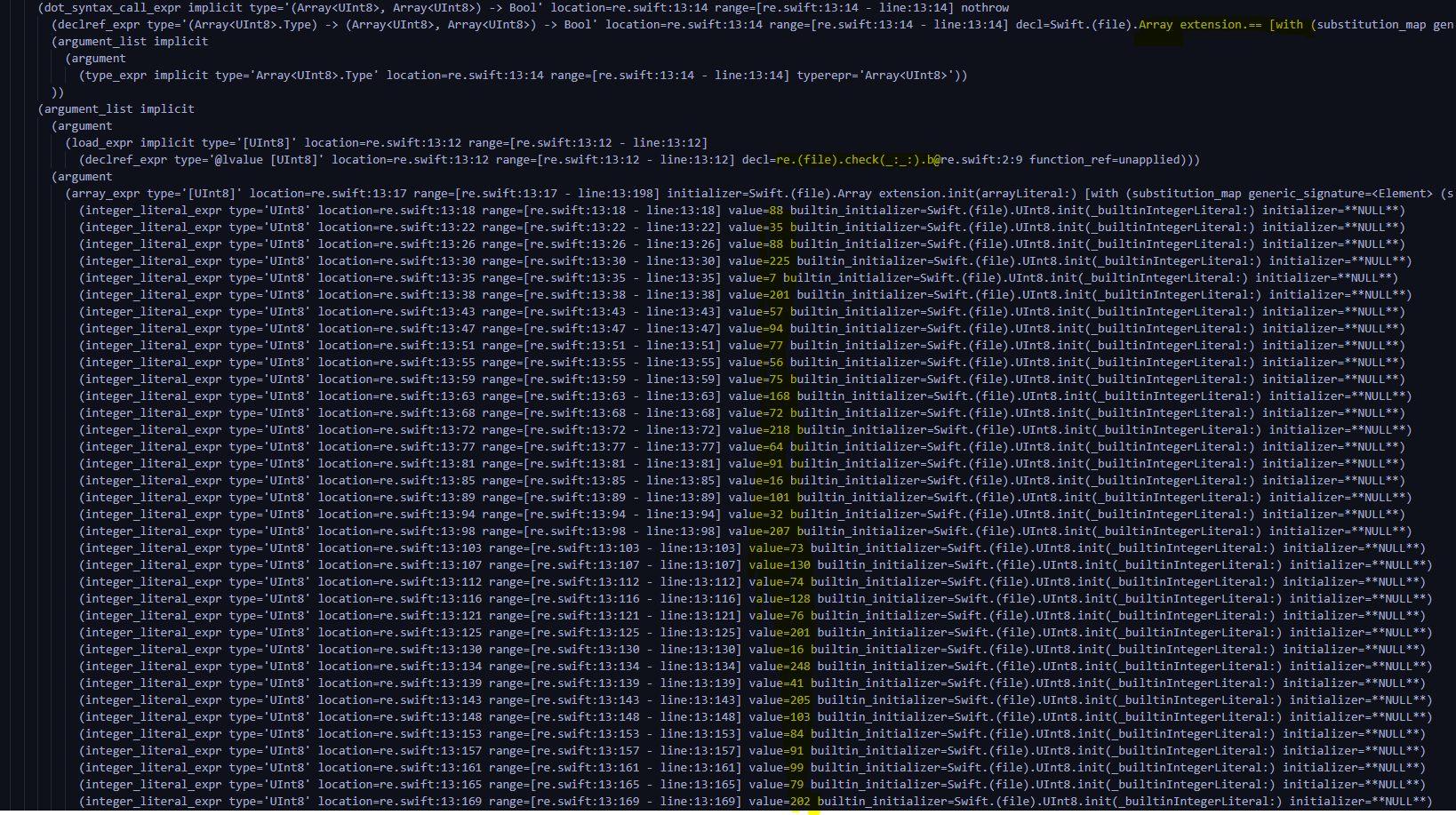
Here is a point to understand that ast How logic works , And apply it to the subsequent analysis .
Through analysis , It was found that decl In the call Swift.(file).Array extension.==, It is similar to declaring operators first , And then in type Declare the operation result of this operator at typerepr='ArrayUInt8>, Finally, load the operand , The question is b And the encrypted array 88,35,88,225,7,201,57,94,77,56,75,168,72,218,64,91,16,101,32,207,73,130,74,128,76,201,16,248,41,205,103,84,91,99,79,202,22,131,63,255,20,16
2. line-by-line analysis
Start from scratch based on the logic just , Can save a lot of time .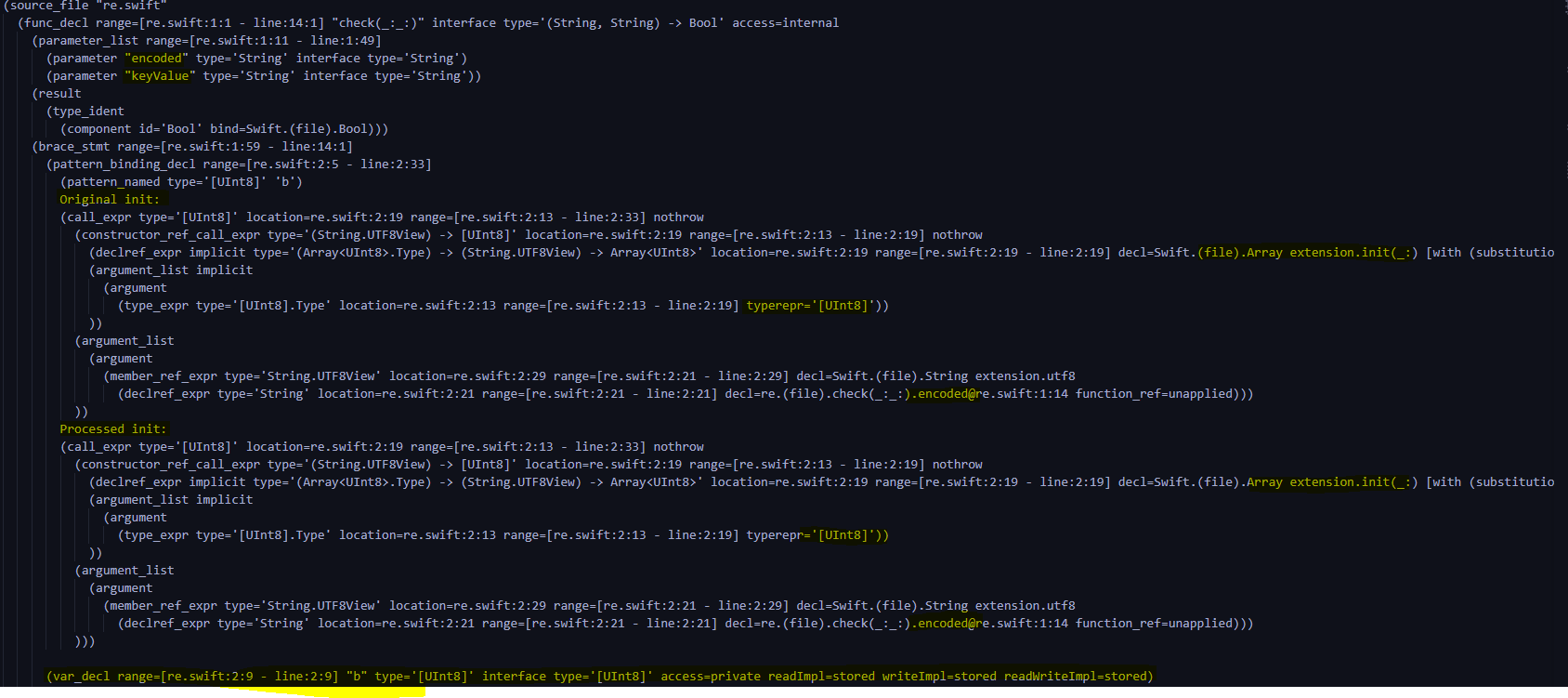
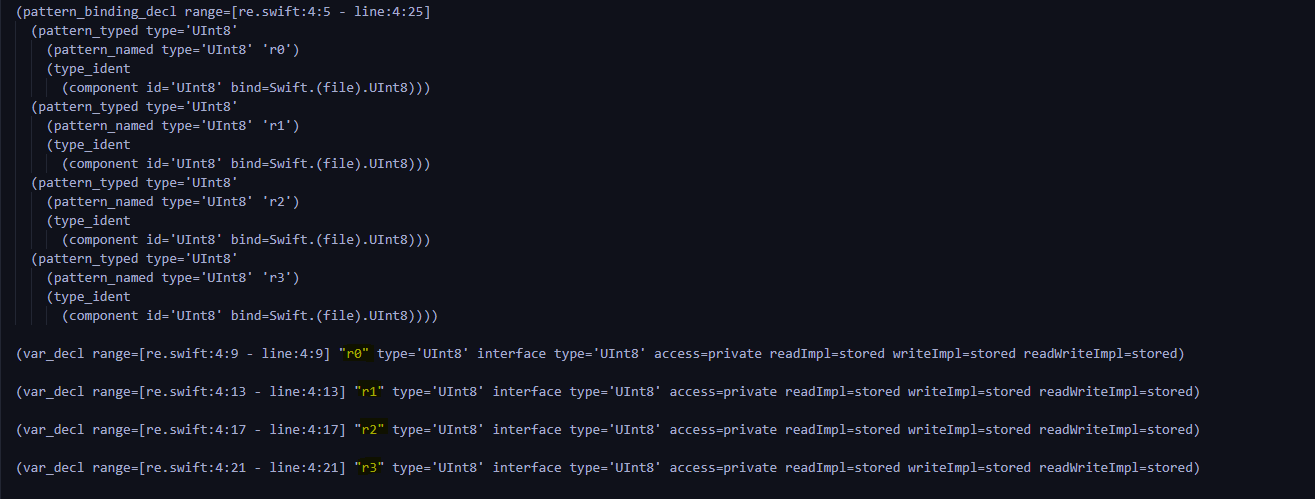
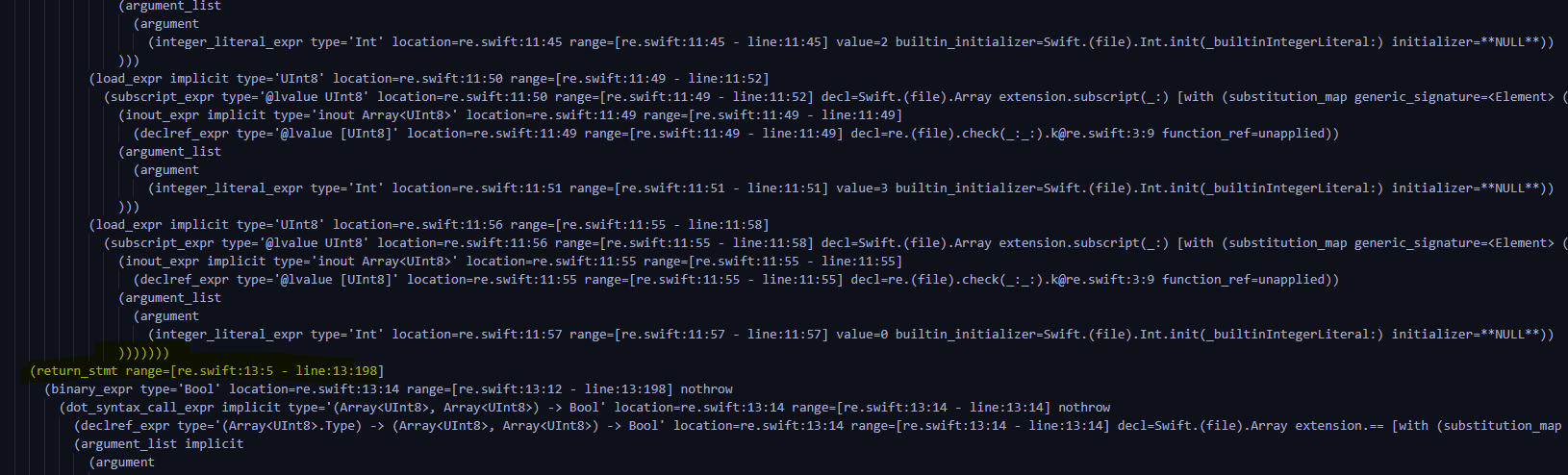
You can see ,check Function has 2 individual string Parameters encoded and keyvalue, Then convert them into b and k.( In the picture is b Of ,k Of is below )
Then is r0,r1,r2,r3 Generation
Then enter the key for loop 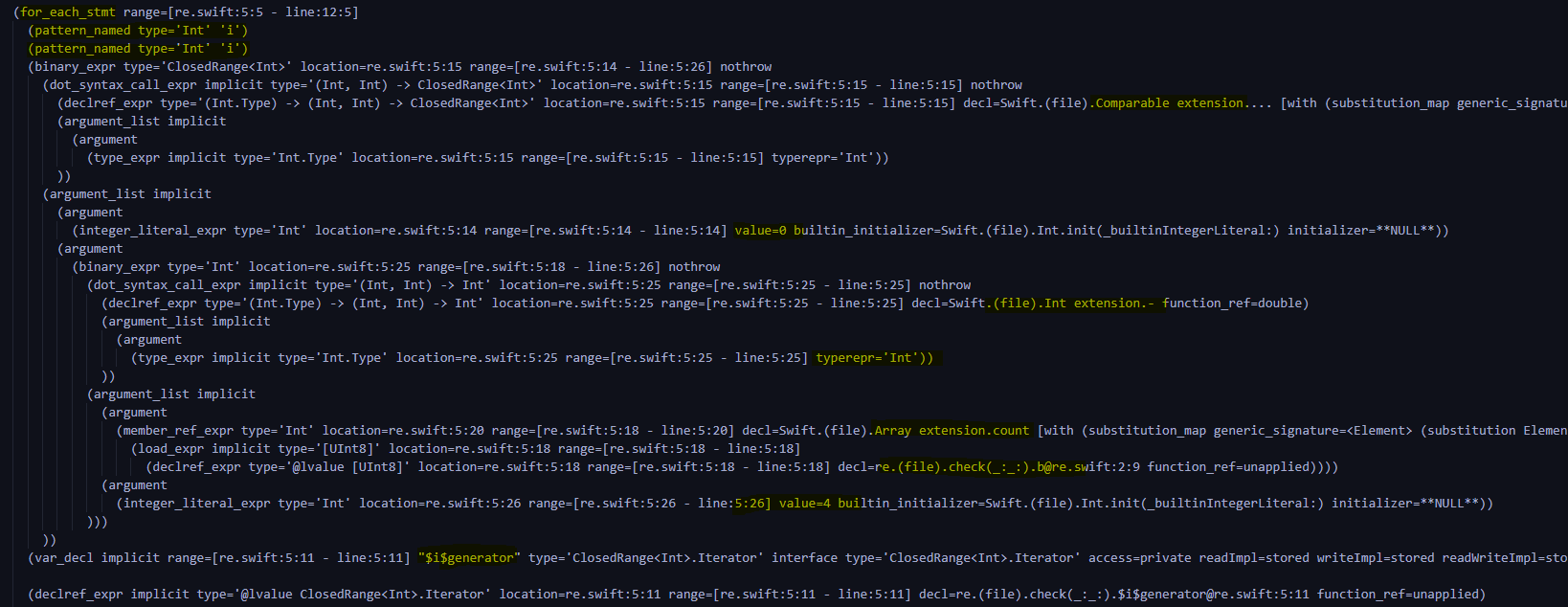
Refer to the logic of ciphertext comparison , It is not difficult to find that this is the declaration for i in range(0,len(b)-4+1)
And then into the circulatory body
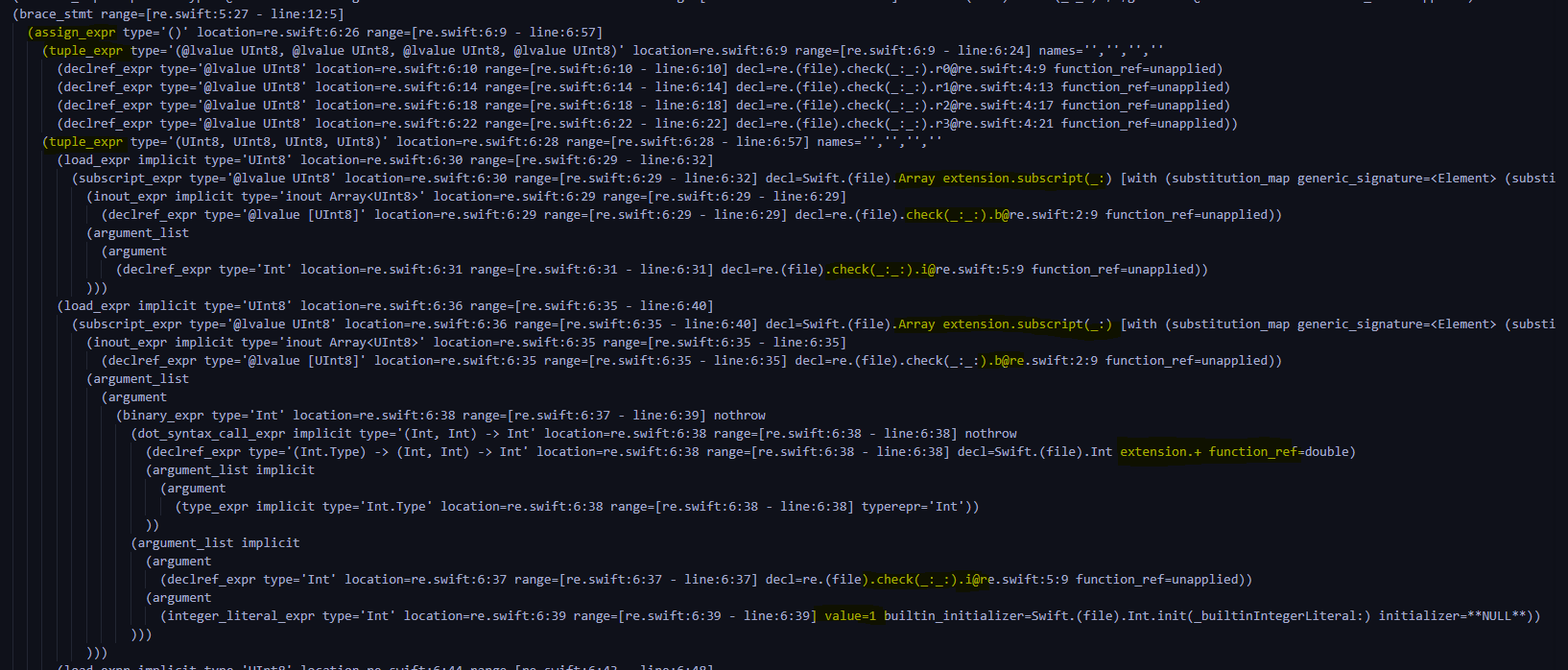
Sort out the logic , Namely r0 = b[i],r1 = b[i+1],r2=b[i+2],r3=b[i+3]( In the picture is r0 and r1 Assignment )
Keep looking down 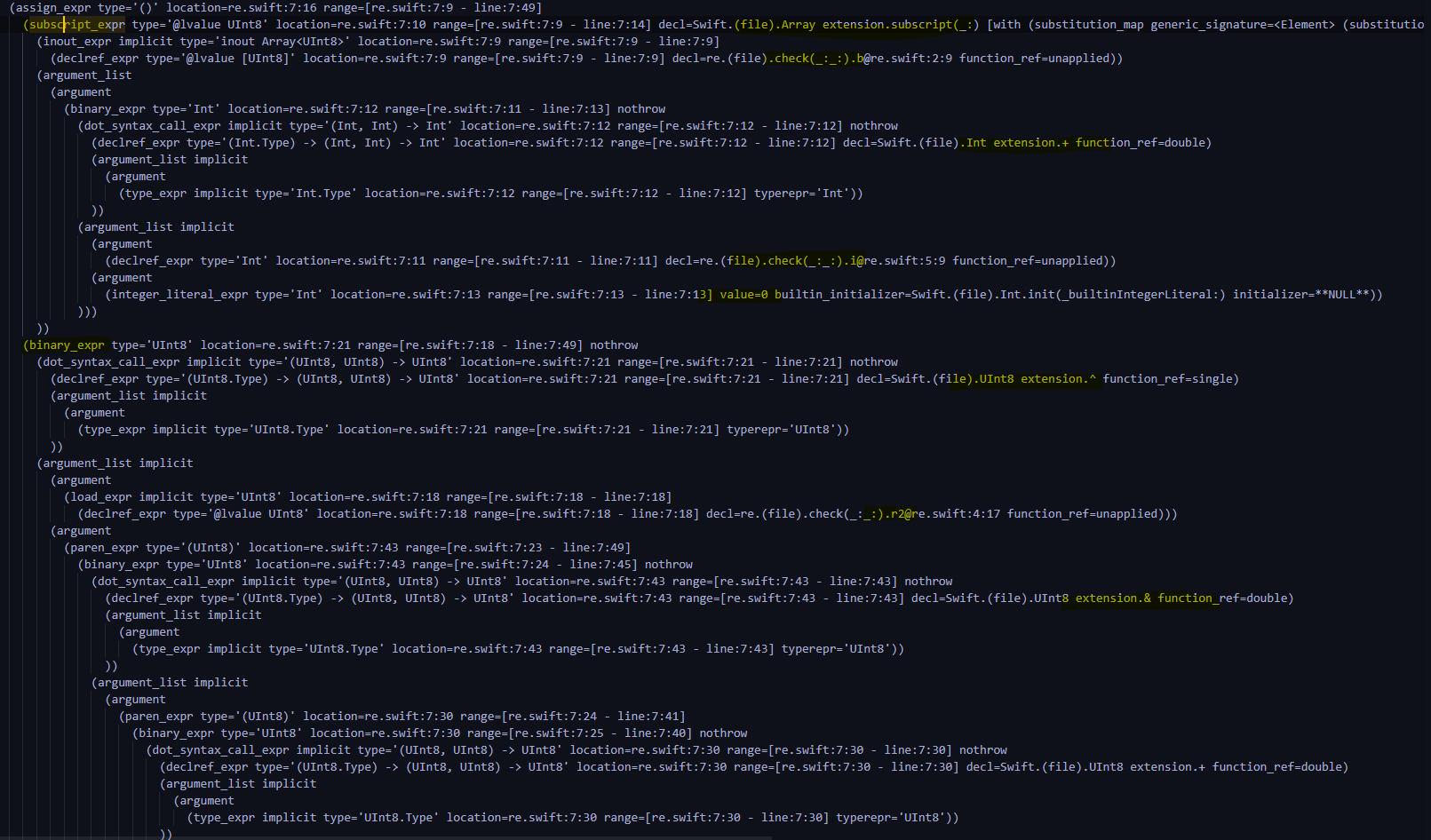
Found to be b[i]=r2^((k[0]+(r0>>4))&0xff) ( The picture is not complete , The whole process is very long , But logic is not difficult , It's from 207-288 That's ok )
And then you just keep looking down , Discovery is constant assignment , Get new value
Finally found for The cycle is return Stop before , The next step is to compare ciphertext , It means that check The function ends here .
3. Write the encryption process
def check(data,key):
b=data
k=key
for i in range(len(b)-4+1):
r0,r1,r2,r3=b[i],b[i+1],b[i+2],b[i+3]
b[i]=r2^((k[0]+(r0>>4))&0xff)
b[i+1]=r3^((k[1]+(r1>>2))&0xff)
b[i+2]=r0^k[2]
b[i+3]=r1^k[3]
k[0] = k[1]
k[1] = k[2]
k[2] = k[3]
k[3] = k[0]
return b==res
4. Go back and decrypt
def decode(data,key):
b=data
k=key
k[0] = k[2]
k[1] = k[3]
k[2] = k[0]
k[3] = k[1]
r1 = b[38 + 3] ^ k[3]
r0 = b[38 + 2] ^ k[2]
r3 = b[38 + 1] ^ ((k[1] + (r1 >> 2)) & 0xff)
r2 = b[38] ^ ((k[0] + (r0 >> 4)) & 0xff)
b[38], b[38 + 1], b[38 + 2], b[38 + 3] = r0, r1, r2, r3
for i in range(37,-1,-1):
k[1] = k[0]
k[2] = k[1]
k[3] = k[2]
k[0] = k[3]
r1=b[i+3]^k[3]
r0=b[i+2]^k[2]
r3=b[i+1]^((k[1]+(r1>>2))&0xff)
r2=b[i]^((k[0]+(r0>>4))&0xff)
b[i], b[i + 1], b[i + 2], b[i + 3] = r0, r1, r2, r3
print("".join(chr(i) for i in b))
summary
Hard look
边栏推荐
- 3月15号 Go 1.18 正式版发布 了解最新特色以及使用方法
- Unity场景跳转及退出
- NovAtel 板卡OEM617D配置步骤记录
- 记录:初次cmd启动MySQL拒接访问之解决
- Rt-ppp test using rtknavi
- Comparative analysis of the execution efficiency of MySQL 5.7 statistical table records
- [算法] 剑指offer2 golang 面试题8:和大于或等于k的最短子数组
- Compile GDAL source code with nmake (win10, vs2022)
- Itext 7 生成PDF总结
- MySQL shutdown is slow
猜你喜欢

RTKLIB: demo5 b34f.1 vs b33
FGUI工程打包发布&导入Unity&将UI显示出来的方式
Programming homework: educational administration management system (C language)
![[algorithm] sword finger offer2 golang interview question 13: sum of numbers of two-dimensional submatrix](/img/17/e7c9bfa867030af97eb66a7932c7e3.png)
[algorithm] sword finger offer2 golang interview question 13: sum of numbers of two-dimensional submatrix
![[dry goods] cycle slip detection of suggestions to improve the fixed rate of RTK ambiguity](/img/9d/7284c1399964d3fb48886f12e4941c.jpg)
[dry goods] cycle slip detection of suggestions to improve the fixed rate of RTK ambiguity
Fairygui joystick
341. Flatten nested list iterator
Unity3d, Alibaba cloud server, platform configuration
The service robots that have been hyped by capital and the Winter Olympics are not just a flash in the pan
使用rtknavi进行RT-PPP测试
随机推荐
FairyGUI增益BUFF數值改變的顯示
Derivation of logistic regression theory
Naive Bayesian theory derivation
Solution to the problem of automatic login in Yanshan University Campus Network
Usage differences between isempty and isblank
Theoretical derivation of support vector machine
【无标题】
染色法判定二分图
记录:动态Web项目servlet访问数据库404错误之解决
PRIDE-PPPAR源码解析
[algorithm] sword finger offer2 golang interview question 5: maximum product of word length
Acwing-116 pilot brother
Special palindromes of daily practice of Blue Bridge Cup
Design and implementation of general interface open platform - (39) simple and crude implementation of API services
341. Flatten nested list iterator
编辑距离(多源BFS)
Sharing ideas of on-chip transplantation based on rtklib source code
In 2020, the average salary of IT industry exceeded 170000, ranking first
[algorithm] sword finger offer2 golang interview question 10: subarray with sum K
wsl常用命令