当前位置:网站首页>Terms related to hacker technology
Terms related to hacker technology
2022-07-04 10:48:00 【weixin_ thirty-four million three hundred and twenty-two thousa】
1. chicken : So-called 【 chicken 】 It is a metaphor for computers that can be controlled by us at will , The other side can be any system (Windows/Unix/Linux), It could be a normal personal computer , It can also be a large server , We can operate them like our own computers , Without being noticed by the other party
2. Trojan horse : It's what pretends to be normal programs , But when these programs run , You'll get the whole control of the system , Many hackers are keen on this method , Like a grey dove , Black holes ,PeShare etc.
3. Web Trojan : Pretending to be an ordinary web page file or inserting your own code directly into a normal web page file , When someone visits , The web Trojan will automatically download the configured Trojan to the visitor's computer by taking advantage of the vulnerability of the other party's system or browser
4. Hang a horse : It is to put a webpage Trojan horse in the website file of the person or embed the code into the real long webpage of the other party , In order to make the viewer in the horse
5. back door : It's a figurative metaphor , After the intruder successfully controlled the target host in some ways , Specific programs can be implanted in each other's systems , Or modify some settings , These changes are superficially difficult to detect , But the intruder can use the corresponding program or method to easily establish a connection with this computer , Take control of this computer again , It's like an intruder secretly equipped with a key to the master's room , You can go in and out at any time without being found
Usually, most Trojan horse programs can be used as backdoors
6.rootkit: It's used by attackers to hide their tracks and keep them root( Root permission , Can be interpreted as Windows Under the system Or administrator rights ) Access tools .
Usually , An attacker can gain from a remote attack root Access right , Or try password guessing first ( Crack ) To gain normal access to the system , After entering the system , Re pass , The security vulnerability in the other party's system obtains the system's root jurisdiction . then , The attacker will install rootkit, In order to achieve their own long-term control of each other's purpose ,rootkit It is very similar to the Trojan horse and back door I mentioned earlier , But more hidden than them , Hackers are typical rootkit, And domestic ntroorkit It's good to wait rootkit Tools
7.IPC$: It's sharing 【 name pipes 】 Resources for , It is an open named pipeline for inter process communication , You can get the corresponding permissions by verifying the user name and password , Use when remotely managing computers and viewing shared resources on computers
8. Weak password : Not strong enough , Easy to guess , similar 123,abc Such a password ( password )
9. Default share : The default share is Windows2000/XP/2003 When the system starts the sharing service, it will automatically open the sharing of all hard disks , Because of the addition of 【$】 Symbol , So you don't see a shared holding chart , Also known as hidden sharing
10.shell: It refers to a command execution environment , For example, we press the keyboard 【 Start button +R】 When 【 function 】 Dialog box , Type in 【cmd】 A black window will appear to execute the command , This is Windows Of shell execution environment . Usually, the environment used to execute system commands after we successfully use the remote overflow program to remote the computer is the other party's shell
11.webShell:webShell That is to say asp、PHP、jsp Or is it cgi A command execution environment in the form of web files , It can also be called a backdoor . Hackers after the invasion , It's usually done with these asp or PHP Valve file and server web After the normal web page files under the directory are mixed together , You can use a browser to access these asp perhaps PHP back door , Get a command execution environment , In order to control the website server , You can upload and download files , view the database , Execute any program command . Commonly used in China webShell There is Haiyang ASP Trojan horse ,PHPspy,c99shell etc.
12. overflow : Exactly , Should be 【 out of buffer 】. The simple explanation is that the program does not perform effective detection on the received input data, resulting in errors , The result could be a program crash or execution of an attacker's command . It can be roughly divided into two categories :1) Heap overflow ;2) Stack overflow
13. Inject : With B/S Development of pattern application development , More and more programmers write programs in this mode , However, due to the uneven level of programmers, a large number of applications have security risks . Users can submit a database query code , According to the result returned by the program , Get some data he wants to know , This is what we call SQLinjection. namely SQL Inject
14. Injection point : It is a place where injection can be implemented , It is usually a link to the database . According to the different permissions of the database running account injected , You get different permissions .
15. Intranet : Generally speaking, it is LAN , For example, Internet bar , Campus network , The company content network belongs to this category . see IP If the address is in the following three ranges , It means that we are in the intranet :10.0.0.0——10.255.255.255 / 172.16.0.0——172.31.255.255 / 192.168.0.0——192.168.255.255
16. Extranet : Direct condensed milk Internet( Internet ), It can be accessed with any computer on the Internet ,IP The address is not reserved IP( Intranet )IP Address
17. port :(port) It is equivalent to a data transmission channel , Used to accept certain data , And then transmit it to the corresponding service , And the computer processes the data , Then the corresponding recovery is transmitted to the other party through the open port . Generally, each port corresponds to the corresponding service , To close these ports, you only need to turn off the service for drinking
18.3389/4899 chicken ;3389 yes Windows Terminal services (Terminal Services) The port number used by default , This service is Microsoft in order to facilitate network administrators remote management and maintenance server and launched , The network administrator can use the remote desktop to connect to any computer on the network with terminal services enabled , After successful login, you will operate the host as you operate your own computer .
This is very similar to the function of remote control software and even Trojan horse program , The link of terminal services is very stable , And any anti-virus software will not check and kill , Therefore, it is deeply loved by hackers . After the hacker invaded the host , Usually you will find a way to add your own back door account first , Then open the other party's terminal service , such , You can use terminal services to control each other at any time , Such a host , It's usually called 3389 chicken .
Radmin Is a very excellent remote control software ,4899 Namely Radmin The default value is , It is often used by hackers as a Trojan horse ( That's why , The current anti-virus software is also right for Radmin I killed ). Some people are using server port numbers . because Radmin It's very powerful , Transmission speed is also faster than most Trojans , And it won't be killed by antivirus software , So use Radmin When managing a remote computer, you use an empty or weak password , Hackers can use some software to scan the network Radmin A host with an empty or weak password , Then you can log in and remotely control each other , Such a controlled host is often referred to as 4899 chicken
19. Rabbit kill : It's by adding shells 、 encryption 、 Modify the signature code 、 Technology such as flower instruction to modify the program , Make it escape the killing of anti-virus software
20. shell : It's using special algorithms , take EXE Executable program or DLL Change the encoding of dynamic link library files ( For example, to achieve compression 、 encryption ), In order to reduce the size of the file or encryption program encoding , Even avoid the killing purpose of anti-virus software . At present, more commonly used shells are UPX、ASPack、PaPack、PECompact、UPack、 Immunity 007、 Wooden horse colored clothes etc.
21. Flower instruction : Just a few assembly instructions , Let the assembly statement make some jumps , The anti-virus software can't normally judge the structure of the virus file . To put it more popular, it means 【 Antivirus software 】 It's looking for viruses from head to toe . If we put the head and foot of the virus upside down , Antivirus software can't find the virus
边栏推荐
- 2、 Operators and branches
- Linked list operation can never change without its roots
- Latex arranges single column table pictures in double column format articles
- Design and common methods of test case documents
- Write a thread pool by hand, and take you to learn the implementation principle of ThreadPoolExecutor thread pool
- On binary tree (C language)
- Architecture introduction
- [Galaxy Kirin V10] [desktop] printer
- Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
- Collection of practical string functions
猜你喜欢
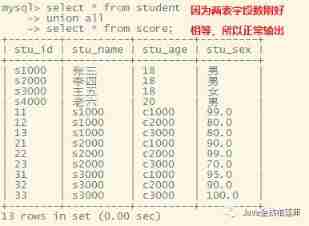
DML statement of MySQL Foundation
![[Galaxy Kirin V10] [server] FTP introduction and common scenario construction](/img/ef/f0f722aaabdc2d98723cad63d520e0.jpg)
[Galaxy Kirin V10] [server] FTP introduction and common scenario construction
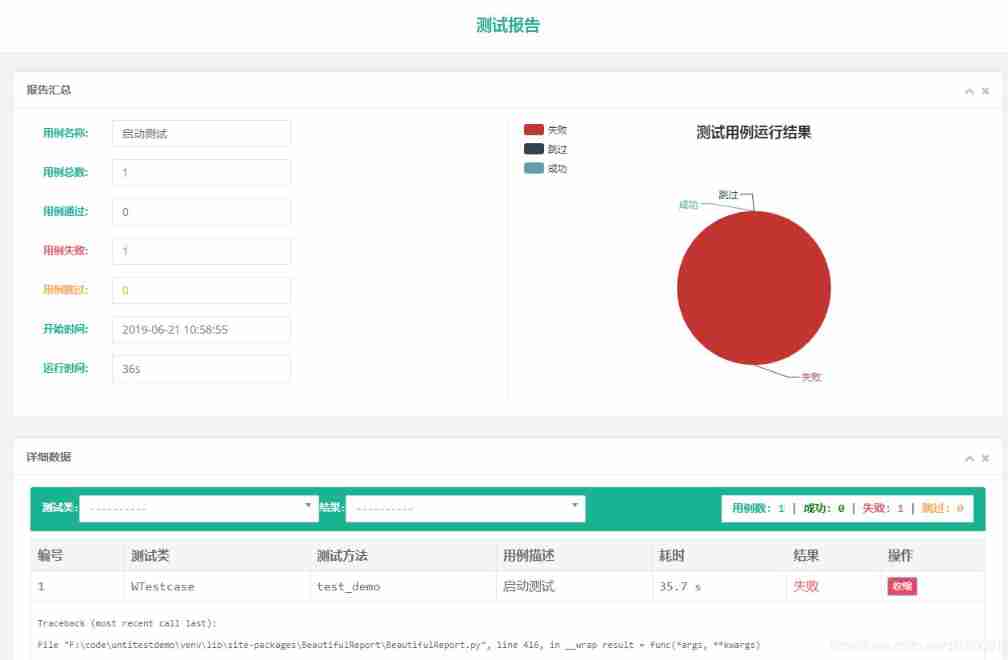
Unittest+airtest+beatiulreport combine the three to make a beautiful test report
The future education examination system cannot answer questions, and there is no response after clicking on the options, and the answers will not be recorded
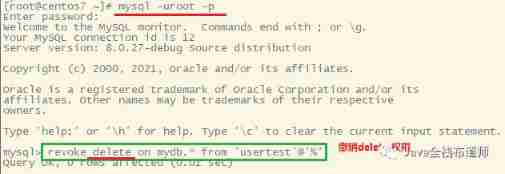
DCL statement of MySQL Foundation
![[Galaxy Kirin V10] [desktop] cannot add printer](/img/a6/28e4aa31e805a018e6db2b32ca1be0.jpg)
[Galaxy Kirin V10] [desktop] cannot add printer
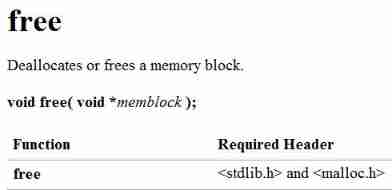
Dynamic memory management
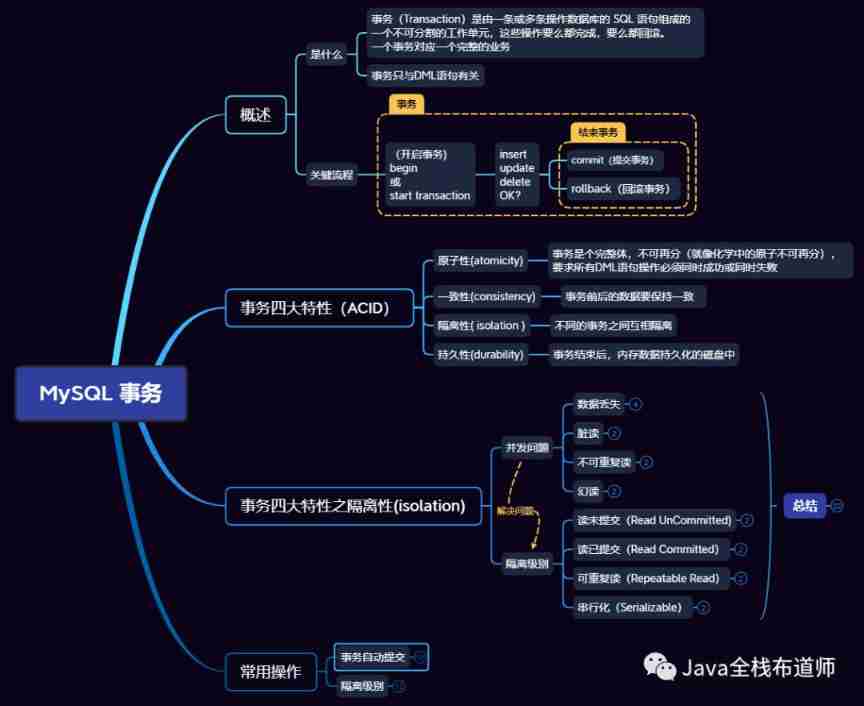
Four characteristics and isolation levels of database transactions
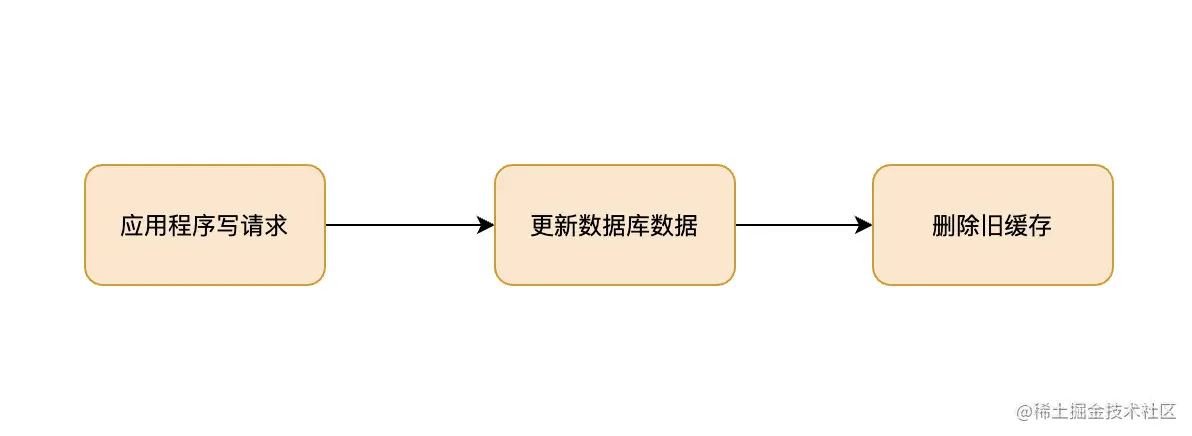
If you don't know these four caching modes, dare you say you understand caching?
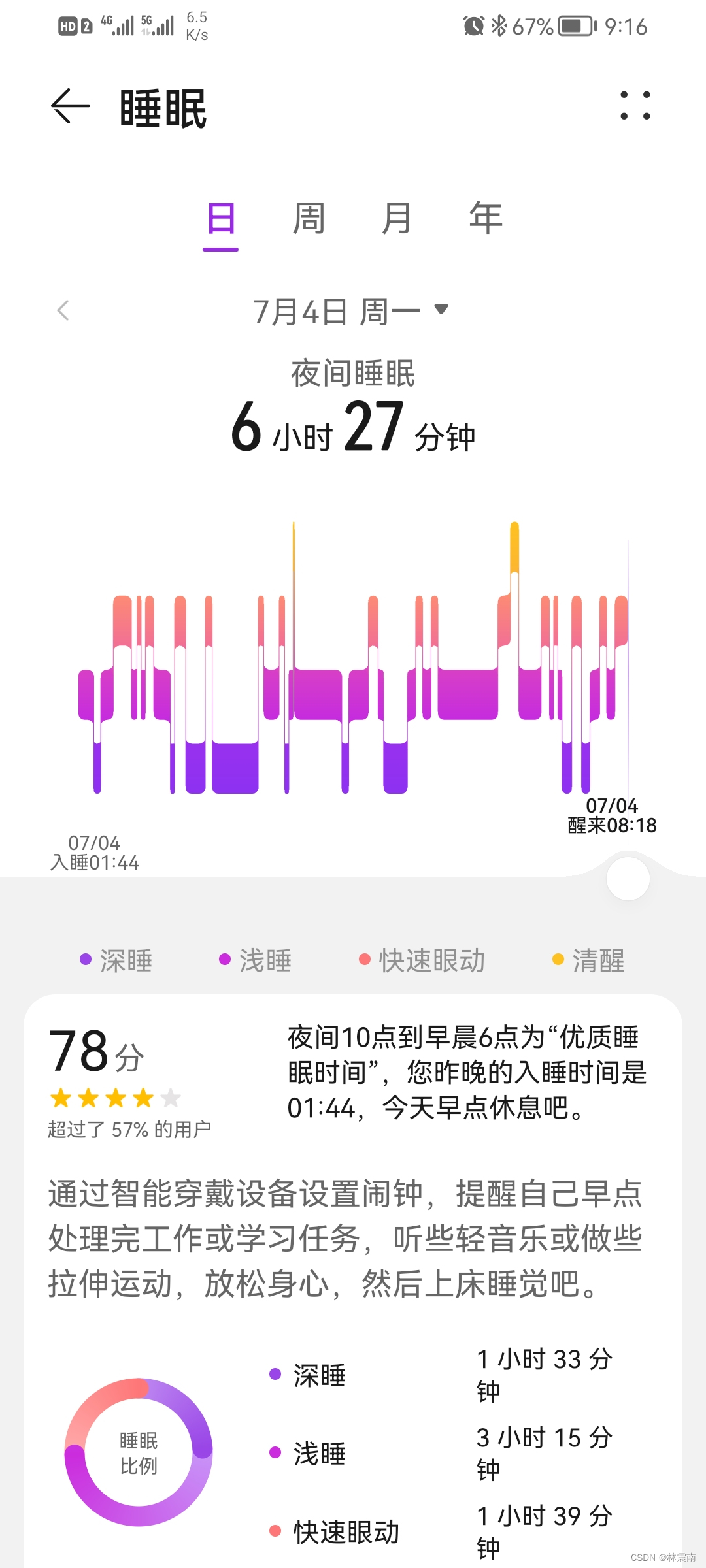
Today's sleep quality record 78 points
随机推荐
Network disk installation
DDL language of MySQL database: create, modify alter, delete drop of databases and tables
Communication layer of csframework
Introduction to extensible system architecture
Snake (C language)
Rhcsa learning practice
[Galaxy Kirin V10] [desktop] FTP common scene setup
/*The rewriter outputs the contents of the IA array. It is required that the type defined by typedef cannot be used in the outer loop*/
Student achievement management system (C language)
[Galaxy Kirin V10] [server] set time synchronization of intranet server
RHCE day 3
Basic data types of MySQL
Strings and characters
Collection of practical string functions
Container cloud notes
software test
When I forget how to write SQL, I
Rhcsa day 9
MPLS: multi protocol label switching
OSPF comprehensive experiment