当前位置:网站首页>[tpm2.0 principle and Application guide] Chapter 9, 10 and 11
[tpm2.0 principle and Application guide] Chapter 9, 10 and 11
2022-07-07 19:04:00 【Godams】
The first 9 Chapter hierarchy
NV The index belongs to a hierarchy, But not in the tree .
Every hierarchy The password root of is a seed , A large random number ,TPM produce , Never leak .
9.1 Three persistence hierarchy
TPM 1.2 in SRK( Store root key ) It's random , Once deleted, the same cannot be generated again SRK.
YPM 2.0 Three persistence are extended in hierarchy( platform 、 Storage 、 Recite ), These three hierarchy It has the following same characteristics
- Each has authorization values and policies
- Each has an enable flag
- Every one has a seed , From it, we can get the key and data object . Seeds are persistent .
- Each has a master key , A sub key can be generated from the master key
TPM 2.0 Added more flexibility :
- The master key is not limited to the storage key
- There can be more than one master key
- Do not store all master keys , They can be generated only when needed , Essentially , The seed is the real root , The master key can be swapped out to TPM external , Store as context .
Three hierarchy
- platform hierarchy:
Intended to be under the control of the platform manufacturer , platform hierarchy It is enabled when restarting , The platform authorization value is set to a zero length password , The strategy is set as an unsatisfiable strategy , This is in hierarchy Is unique . - Storage hierarchy
Intended for use by platform owners , Storage hierarchy Can be disabled by the owner , For non privacy sensitive operations , And endorsement under separate control hierarchy Then deal with privacy . - Recite hierarchy
Recite hierarchy It is used for privacy sensitive operations , Its enabling sign 、 Policy and authorization values , And others hierarchy They're all independent . Users who care about privacy can disable endorsement hierarchy,TPM Apps can still use storage hierarchy, Allow platform software to use TPM.
9.2 privacy
Privacy here means receiving TPM The remote party of the digital signature , Digital signatures cannot be associated , And it is proved from cryptography that it comes from the same TPM. Association is to determine that the signature key comes from a single 、 Certified TPM.
TPM Manufacturer generates endorsement master seed , Generate one or more master keys based on this seed , Then generate certificates for these keys . The certificate proves that the key comes from an authenticated TPM,TPM It is produced by the manufacturer .
If the master key is a signature key , Directly prove other signing keys , Correlation is very simple , Because all signatures converge to the same certificate .
When the master key is an encryption key , The process of creating a sub key certificate takes a more complex process , It is called activation certificate . The certificate authority is called privacy CA, Because for the key that has been proved , Think privacy CA Will not disclose any association between keys .
9.2.1 Activate Certificate
The master key is a decryption key , Unsigned key ,CA Generate Certificate , And encrypt it with the public key of the master key . Only those with the corresponding private key TPM, The certificate can be restored .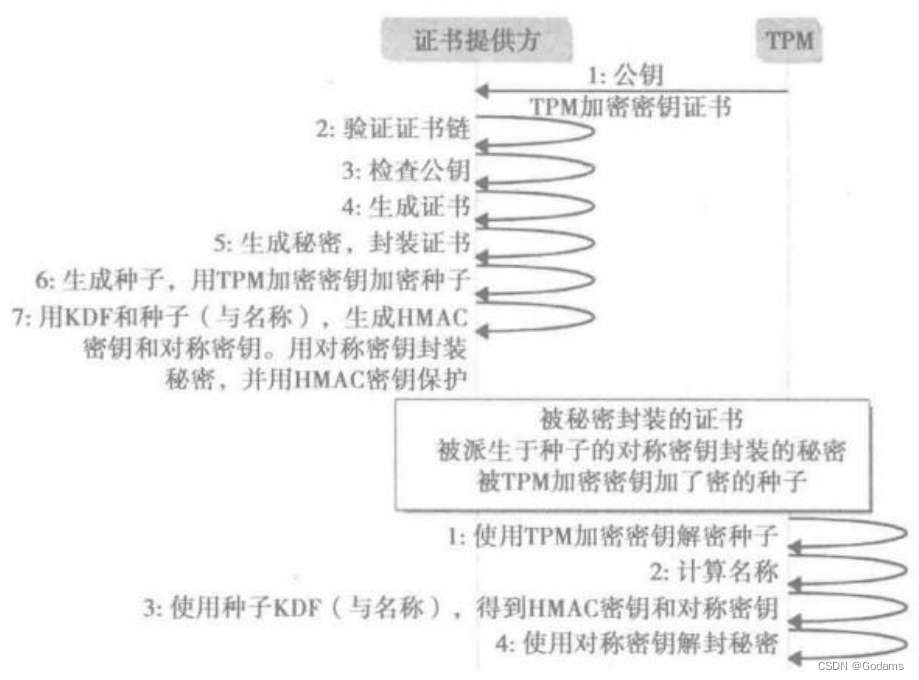
textbook P89 page , This part is too much , Typing may be a little slow .
9.3 empty hierarchy
empty hierarchy With three kinds of persistence hierarchy similar , You can have a master key , Sub keys can be created based on the master key . The differences are as follows :
- The authorization value is a zero length password , Policy is empty ( Can't be satisfied ). These cannot be changed
- It cannot be disabled
- It has a seed , Both keys and data objects come from it . This seed is not persistent , At every reboot , It and proof Will be regenerated with different values
conversation 、 Saved context objects and sequence objects ( Summary and HMAC state ) It's all empty hierarchy. This makes them empty every time the system restarts , Because seeds and proof The value has changed . Users usually do not modify endorsements hierarchy seeds ( Because this will invalidate the certificate )、 Storage hierarchy seeds ( Because it will invalidate the key with a long life cycle ) And the platform hierarchy seeds ( Because users may not have this right ).
The temporary key will be erased after the system restarts ,TPM It can be used as a cryptographic coprocessor , Use the externally generated key , Execute cryptographic algorithm .
The first 10 Chapter secret key
When the application uses a key , At the same time, ensure that they exist safely in a hardware device , This is a TPM The strongest part of .
10.2 Key generator
Based on the weakness of software generated key if the strength of software random number generator or entropy source is not enough , It doesn't have .
10.3 Master key and seed
TPM The key can form a hierarchy, Encapsulate the child key with the parent key .
1、TPM The key can form a hierarchy, Encapsulate the child key with the parent key . The master key is hierarchy Root key of . They have no father .
2、 Three persistence hierarchy Each of them has a corresponding main seed : Endorsement main seed 、 Platform master seed and storage master seed . These seeds never leave TPM. They are secret inputs to key derivation functions . When TPM When creating a master key , It uses a master seed and a common template . When specifying a key , All the projects you usually expect are in the template , These items include algorithms and key sizes 、 Its policy and key type ( Signature 、 Encryption, etc ). The caller can also provide a unique data in the template . This unique data is the input of the public key area in the template .
3、 Key derivation functions are fixed and repeatable . The same seed 、 Same template , Always produce the same key . By changing the unique data in the template , The caller can create an unlimited number of master keys .
10.4 Key persistence
1、 The user calls TPM2_EvictControl command , Move a key from volatile space to non-volatile space , In this way, after each power on and restart , It can remain loaded ( Long term preservation ). No key needs to be persisted for use . Usually we want to have only a few master keys , Maybe everyone hierarchy There is one , Will be set to persist , To improve performance .
2、 In addition to the master key , In endorsement hierarchy、 Storage hierarchy And the platform hierarchy Other keys in can also be persisted .
3、 empty hierarchy There is no key that can be persisted . After restart , All keys will be lost .
4、 Only a limited number of keys can be persisted , but TPM Can handle an unlimited number of keys , The application uses TPM Do this as a key cache
10.5 Key cache
Keys other than the master key ,TPM Can be used as key cache . in other words ,TPM2_Create Create a key , And use the parent key to encapsulate ( wrap)( encryption ) This key , Return the encapsulated key to the caller . The caller stores this key in TPM outside , It may be on disk . In order to use this key , Users must use TPM2_Load, Load it into TPM in . After completion , Callers can use TPM2_FlushContext Release space . This key is different from the master key , The master key has no father , After creation, it will remain TPM in .
10.6 Key authorization
TPM Can provide access control , Key access requires authorization . When the key leaves TPM when , It is encapsulated by a strong parent encryption key , And it has dictionary attack protection and logic protection , That is, when the password is wrong ,TPM Will record , And prevent further attempts within a configurable time .
10.7 Key destruction
Sometimes , The key needs to be destroyed , It may be because the authorization was leaked , It may also be that the machine is to be used for other purposes . Keys stored in software can never be destroyed , Because they can be copied anywhere . however TPM The key has a parent key or is itself the master key . Every hierarchy Each has its own unique main seed . Erase the main seed , You can prevent the re creation of this hierarchy Master key for —— Obviously, this is a very tough and rarely implemented behavior . Erasing the master key can prevent their child keys from being loaded into TPM in . There are attributes that can only exist in TPM All keys in will be destroyed .
Key types and properties

The master key cannot be copied , They and TPM One of the hierarchy Binding .
A major use case for key replication properties is key backup .TPM 2.0 Two properties control the replication of the key , One extreme is , A key is locked to a single TPM Single parent key on , Never allow to be copied . The other is , The key can be copied freely , All child keys encapsulated by the parent key , Until all descendants , Available on all target platforms . The middle case is , A key is locked to a parent key , But when the parent key is moved , He can also move .
A child key can have more than one parent key , The process of replication is the process of establishing a new parent-child relationship , But it did not abolish the original father son relationship .
Restricted signing key : A restricted signature key can only be signed by TPM Generated summary . However TPM How to know that it calculates the summary , The answer is to use tickets , When TPM When calculating the summary , It generates a ticket , The statement is TPM Summary of self calculation .TPM adopt 4 The magic number of bytes knows which data generates bills , It doesn't start with magic numbers , To create .
10.10 Context management and loading
Context management includes , Save a loaded key context to TPM outside , Then load the context into TPM in .
10.11 empty hierarchy
Every time you restart , Will be cleared
The first 11 Chapter Non volatile index
TPM It is required to use the following two general data structures , Need to use nonvolatile (NV) Memory :
- stay TPM Data structures defined in the architecture :hierarchy Authorization value 、 seeds 、 evidence 、 Counter 、 The clock 、 secret key
- Unstructured data defined by user or platform specific specifications : User defined index ,TPM Based on HMAC Shared private key for 、PCR value 、 physical position (locality), And physical presence to provide authorization , Then control index access .
NV Four index types : Common type , Counter type , Bit field type , Extension type
11.1 NV General index
General index – Be similar to TPM1.2 Indexes – Have unstructured data of any length . And counter 、 Bit fields are different from extended indexes , It has no restrictions on the types of data that can be written
- NV Counter index
The nonvolatile counter is an incrementable 64 A value . The first increment command starts with , It initializes to TPM The maximum value in any counter on . This value includes the currently defined counter index and the previously defined but no longer TPM The counter in . therefore , Even if the index is deleted or rebuilt , The counter cannot be reversed . - NV Bit field index
Bit field index protection 64 position , At the beginning of the first write, all bits are initialized to null , There can also be optional setting bits . a ( Or more ) You can set , But never empty . - NV Extended index
The extended index is defined by a specific hash algorithm , And has a fixed index life . The data size of the index is based on its hash algorithm . The data is initialized to 0. The write operation is an extension operation , Be similar to PCR Write operations in
Most force sets combine extended indexes and hybrid indexes to create flexible PCR, Another common use case is the security audit log , Because any extension operation will create an irreversible password protection history . - Mixed index
Another new TPM2.0 The feature is mixed index . As with non hybrid indexes ,NV Index metadata ( Index handle 、 size 、 attribute 、 Policy and password ) It's nonvolatile , Mixed index data is created in volatile memory . Process the mixing counter , Index data is written only when it is shut down normally NV Memory .4 Any of the index types ( Ordinary 、 Counter 、 Bit field or extension ) Can be mixed index .
When an application wants to write frequently , Hybrid index may be applicable . because NV Technology is often dielectric lossy ,TPM You can protect yourself by refusing frequent writes . There is no loss problem in volatile memory , So you can write mixed indexes as needed .
If the index is deleted before normal shutdown , Then mixed index data can only exist in volatile memory . Applications can define indexes 、 Write data 、 The authorization value of the applicable policy , Then delete the index .
Mix common 、 The extension and bit field indexes are written only during normal shutdown NV Memory , But the hybrid counter is more complex , Because it cannot rollback or lose incremental operations . Therefore, it must be ensured that even if normal shutdown cannot be achieved , Volatile values should also be written NV Memory . - NV Access control

- NV write in
Each index is created for the first time , There is an implied value : Not written . stay TPM1.2 in , Always use all 0 Data creation index , Therefore, the read operation cannot distinguish between all zeros and unwritten indexes . stay TPM2.0 in , Unwritten is a separate state . The policy can specify whether the index must be written or not . - NV Index handle value
When users create NV The index is , Users will assign index values . stay TPM1.2 in , Some bits have special properties , For example, for locking D position . stay TPM2.0 Library specification , There is no index assignment outside the scope of the global handle , And any bit of the index value , No special meaning .TPM No attribute is mandatory based on the index value . However , Specific platform specifications or global TCG The registry can specify index values . - NV name
TPM The name of the entity is unique ( encryption ) Defines the entity , And can be used to authorize .NV The index is the hash value of a public area , Include index ( Handle )、 attribute ( Including whether it has been written )、 Strategy and size .
- NV password
TPM A strange thing about is that the user can't really change the password of the object .TPM2_ObjectChangeAuth Command can create objects with new commands , But the original object still exists . Users can delete all existing copies of this object , but TPM This operation cannot be enforced .
NV The index only exists in TPM Inside . It will never be saved to the context or removed in any way TPM.
边栏推荐
- Charles+Postern的APP抓包
- DeSci:去中心化科学是Web3.0的新趋势?
- 【Unity Shader】插入Pass实现模型遮挡X光透视效果
- Charles+drony的APP抓包
- Reject policy of thread pool
- ip netns 命令(备忘)
- SQLite SQL exception near "with": syntax error
- 【Base64笔记】「建议收藏」
- The performance and efficiency of the model that can do three segmentation tasks at the same time is better than maskformer! Meta & UIUC proposes a general segmentation model with better performance t
- Will domestic software testing be biased
猜你喜欢

2022上半年朋友圈都在传的10本书,找到了
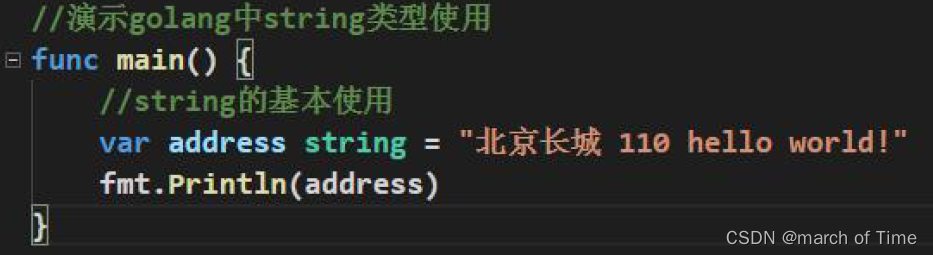
go语言的字符串类型、常量类型和容器类型
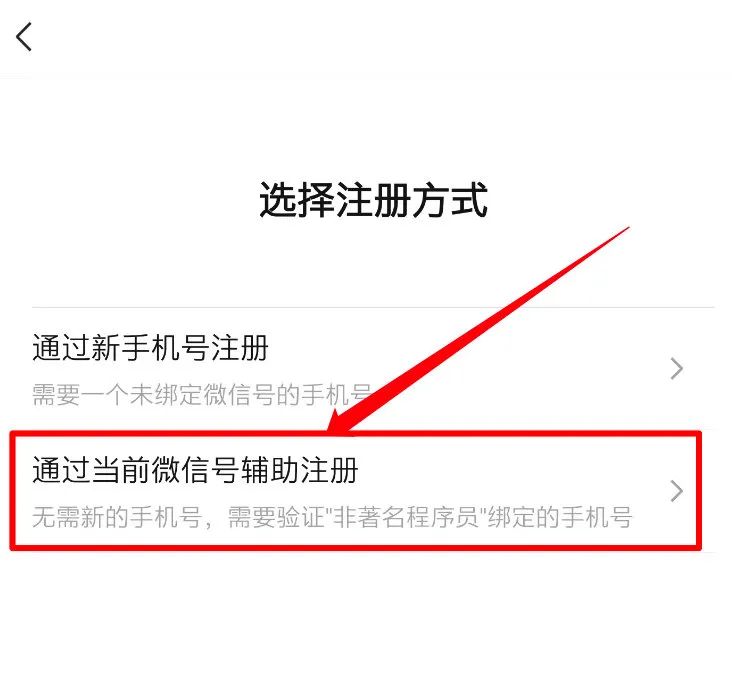
我感觉被骗了,微信内测 “大小号” 功能,同一手机号可注册两个微信
Reuse of data validation framework Apache bval
【塔望方法论】塔望3W消费战略 - U&A研究法

Antisamy: a solution against XSS attack tutorial
微信网页调试8.0.19换掉X5内核,改用xweb,所以x5调试方式已经不能用了,现在有了解决方案
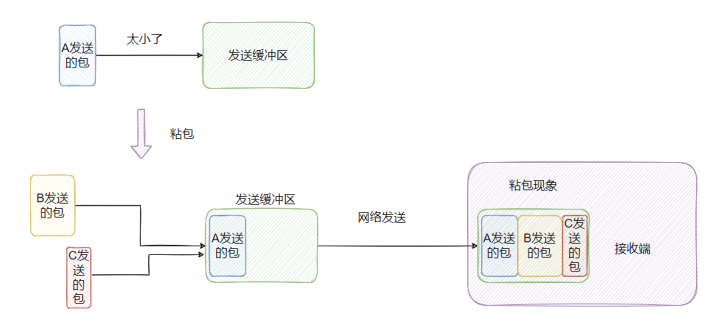
Do you really understand sticky bag and half bag? 3 minutes to understand it
Nat address translation
Save the memory of the model! Meta & UC Berkeley proposed memvit. The modeling time support is 30 times longer than the existing model, and the calculation amount is only increased by 4.5%
随机推荐
Mathematical analysis_ Notes_ Chapter 11: Fourier series
Do you really understand sticky bag and half bag? 3 minutes to understand it
RISCV64
CVPR 2022丨学习用于小样本语义分割的非目标知识
【C语言】字符串函数
Golang client server login
Charles+drony的APP抓包
Complete e-commerce system
高考填志愿规则
二叉树的基本概念和性质
Antisamy: a solution against XSS attack tutorial
CVPR 2022 - learning non target knowledge for semantic segmentation of small samples
nest. Database for getting started with JS
gsap动画库
如何给“不卖笔”的晨光估值?
Usage of PHP interview questions foreach ($arr as $value) and foreach ($arr as $value)
Redis
testing and SQA_动态白盒測试[通俗易懂]
Summary of evaluation indicators and important knowledge points of regression problems
idea彻底卸载安装及配置笔记