边栏推荐
- 直播预约通道开启!解锁音视频应用快速上线的秘诀
- 云安全日报220707:思科Expressway系列和网真视频通信服务器发现远程攻击漏洞,需要尽快升级
- Performance test process and plan
- “解密”华为机器视觉军团:华为向上,产业向前
- NAT地址转换
- [C language] string function
- 现在网上期货开户安全吗?国内有多少家正规的期货公司?
- Tips of this week 141: pay attention to implicit conversion to bool
- CVPR 2022 - learning non target knowledge for semantic segmentation of small samples
- RIP和OSPF的区别和配置命令
猜你喜欢
随机推荐
海量数据去重的hash,bitmap与布隆过滤器Bloom Filter
性能测试过程和计划
Comparison and selection of kubernetes Devops CD Tools
[principle and technology of network attack and Defense] Chapter 1: Introduction
[trusted computing] Lesson 13: TPM extended authorization and key management
DataSimba推出微信小程序,DataNuza接受全场景考验? | StartDT Hackathon
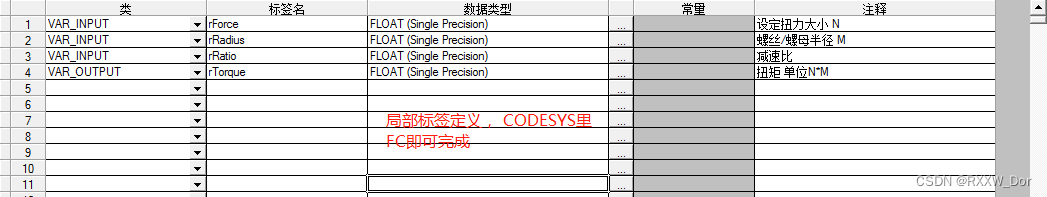
伺服力矩控制模式下的力矩目标值(fTorque)计算
Redis的发布与订阅
Usage of PHP interview questions foreach ($arr as $value) and foreach ($arr as $value)
Charles+Postern的APP抓包
直播软件搭建,canvas文字加粗
线程池的拒绝策略
sqlite sql 异常 near “with“: syntax error
通过 Play Integrity API 的 nonce 字段提高应用安全性
A few simple steps to teach you how to see the K-line diagram
Will domestic software testing be biased
Win11C盘满了怎么清理?Win11清理C盘的方法
企业展厅设计中常用的三种多媒体技术形式
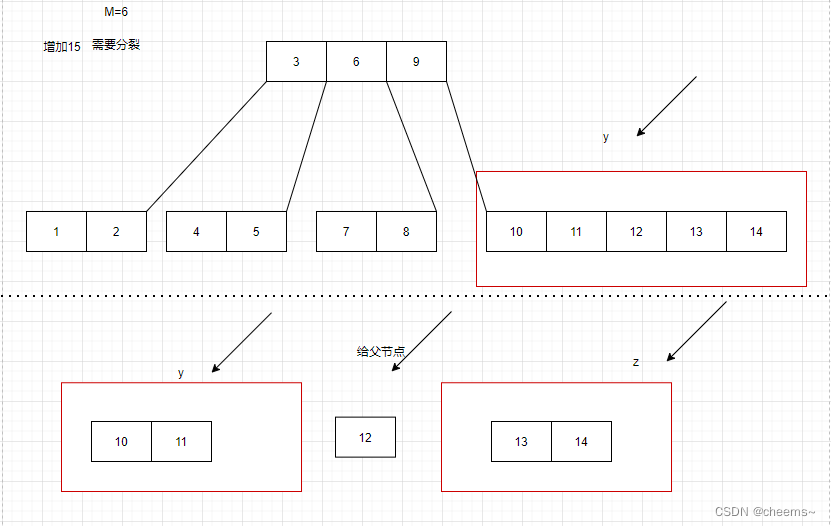
Disk storage chain B-tree and b+ tree
Kubernetes DevOps CD工具对比选型