边栏推荐
- Complete model verification (test, demo) routine
- FOFA-攻防挑战记录
- Cascade-LSTM: A Tree-Structured Neural Classifier for Detecting Misinformation Cascades(KDD20)
- 网络模型的保存与读取
- My best game based on wechat applet development
- Fundamentals - integrating third-party technology
- Password recovery vulnerability of foreign public testing
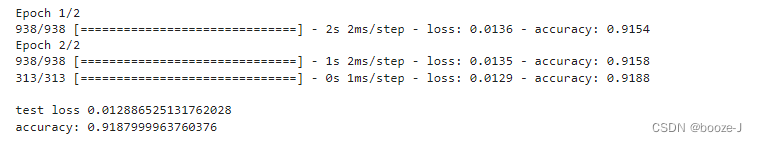
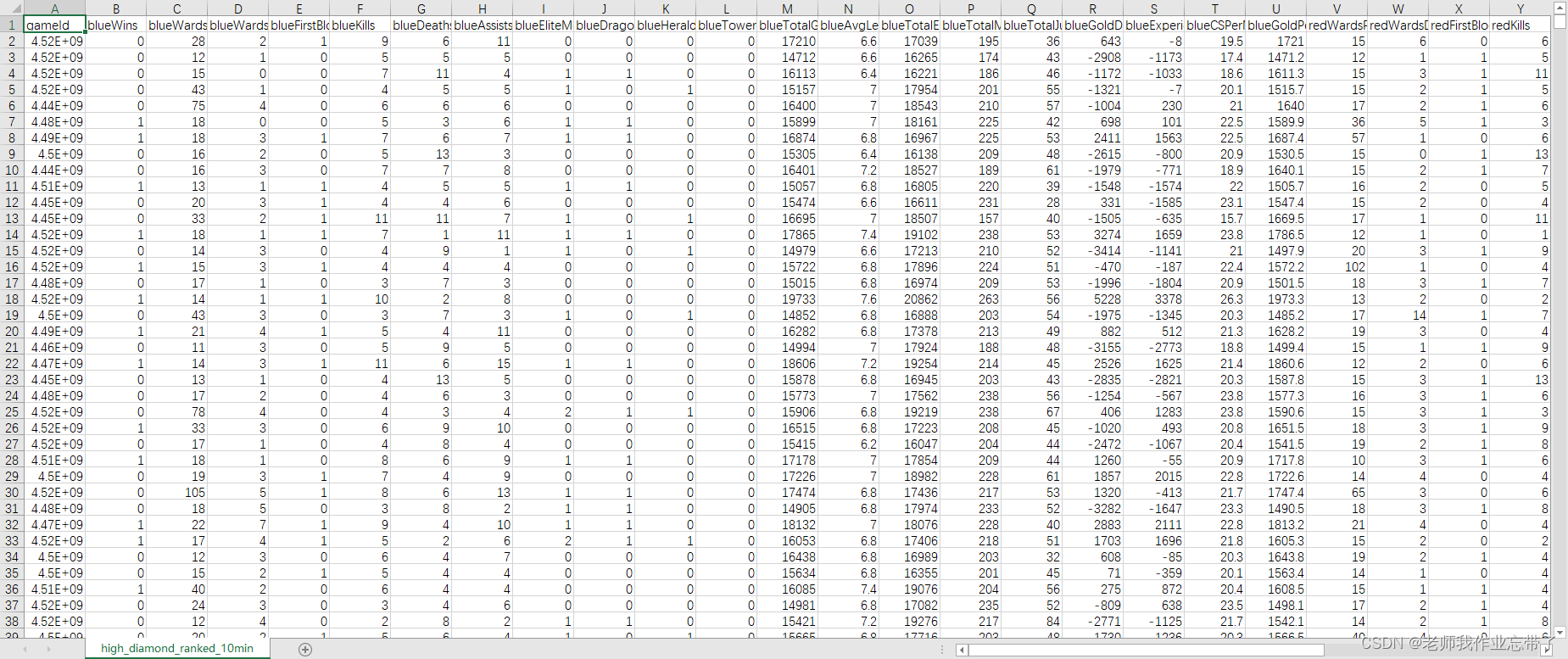
- Prediction of the victory or defeat of the League of heroes -- simple KFC Colonel
- C # generics and performance comparison
- Course of causality, taught by Jonas Peters, University of Copenhagen
猜你喜欢
随机推荐
【深度学习】AI一键换天
50MHz generation time
Codeforces Round #804 (Div. 2)
swift获取url参数
14. Draw network model structure
Codeforces Round #804 (Div. 2)(A~D)
Is it safe to open an account on the official website of Huatai Securities?
[deep learning] AI one click to change the sky
What is load balancing? How does DNS achieve load balancing?
ReentrantLock 公平锁源码 第0篇
The method of server defense against DDoS, Hangzhou advanced anti DDoS IP section 103.219.39 x
[Yugong series] go teaching course 006 in July 2022 - automatic derivation of types and input and output
国外众测之密码找回漏洞
Service mesh introduction, istio overview
Handwriting a simulated reentrantlock
51 communicates with the Bluetooth module, and 51 drives the Bluetooth app to light up
股票开户免费办理佣金最低的券商,手机上开户安全吗
Marubeni official website applet configuration tutorial is coming (with detailed steps)
Huawei switch s5735s-l24t4s-qa2 cannot be remotely accessed by telnet
Langchao Yunxi distributed database tracing (II) -- source code analysis