当前位置:网站首页>【指针】数组逆序重新存放后并输出
【指针】数组逆序重新存放后并输出
2022-07-06 09:24:00 【|光|】
要求
编写程序,输入n个整数存入一维数组,再按逆序重新存放后再输出。(用指针实现)
代码
#include<stdio.h>
/* * 该函数用来输入一维整数数组,输入的数据存放在形参a数组中 * 输入的数据以0作为结束标志,0不存入数组也不计入输入数据的总数 * 返回值为输入数据的个数 */
int input(int a[])
{
int n=0;
int b = 0;
do
{
scanf("%d",&b);
if(b == 0)
break;
else
{
a[n] = b;
n++;
}
}
while(b != 0);
return n;
}
/* * 该函数用来实现计算形参数组a的逆序存放 * n为a数组中的整数个数 */
void fun(int a[],int n)
{
int b[n],c = 0;
for(int i = n-1;i>=0;i--)
{
b[c] = a[i];
c++;
}
for(int i = 0;i<n;i++)
{
a[i] = b[i];
}
}
main函数
int main()
{
int a[200],n;
n=input(a);
fun(a,n);
for(int i=0;i<n;i++)
printf("%d ",a[i]);
return 0;
}
测试
测试输入
1 3 5 7 0
输出
7 5 3 1
边栏推荐
- Ucos-iii learning records (11) - task management
- Applet Web Capture -fiddler
- Intranet information collection of Intranet penetration (3)
- How to understand the difference between technical thinking and business thinking in Bi?
- Markdown font color editing teaching
- flask实现强制登陆
- Hackmyvm Target Series (3) - vues
- Intranet information collection of Intranet penetration (5)
- JDBC看这篇就够了
- 《统计学》第八版贾俊平第八章假设检验知识点总结及课后习题答案
猜你喜欢
Tencent map circle
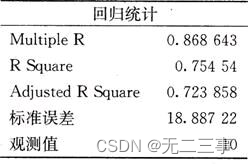
Statistics, 8th Edition, Jia Junping, Chapter 11 summary of knowledge points of univariate linear regression and answers to exercises after class
Record an API interface SQL injection practice
Intranet information collection of Intranet penetration (I)
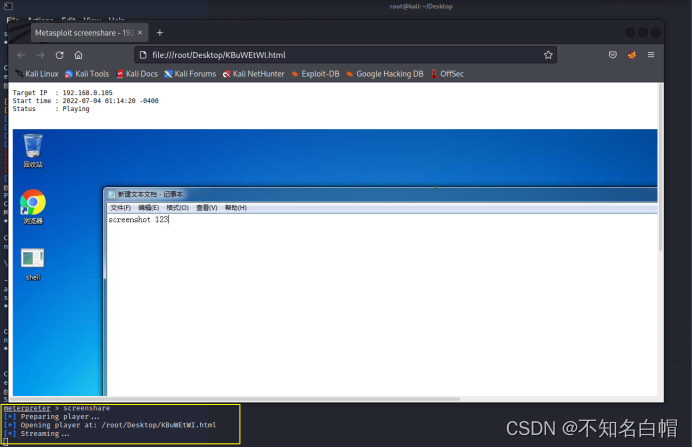
Intranet information collection of Intranet penetration (2)

线程的实现方式总结
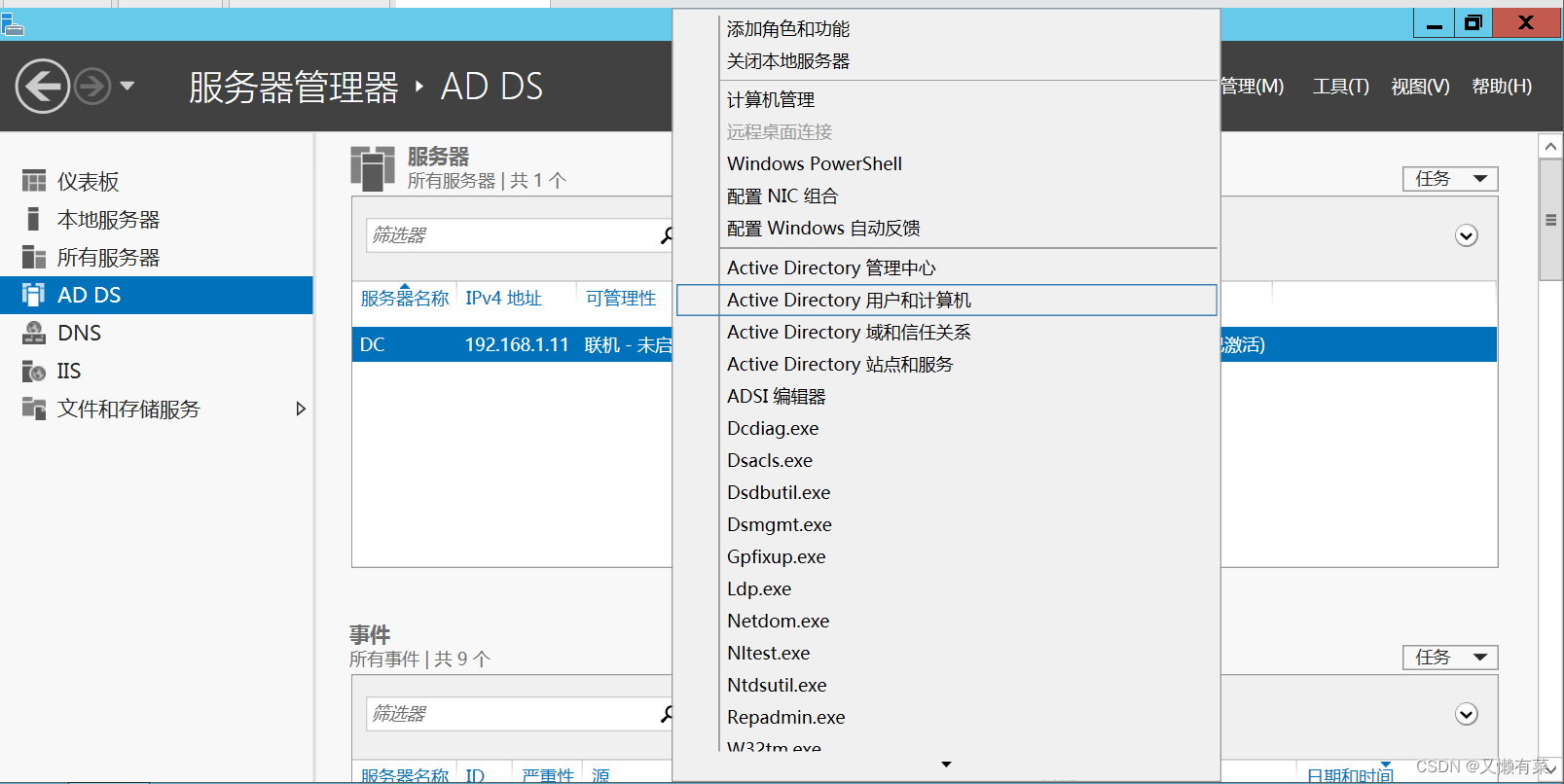
搭建域环境(win)
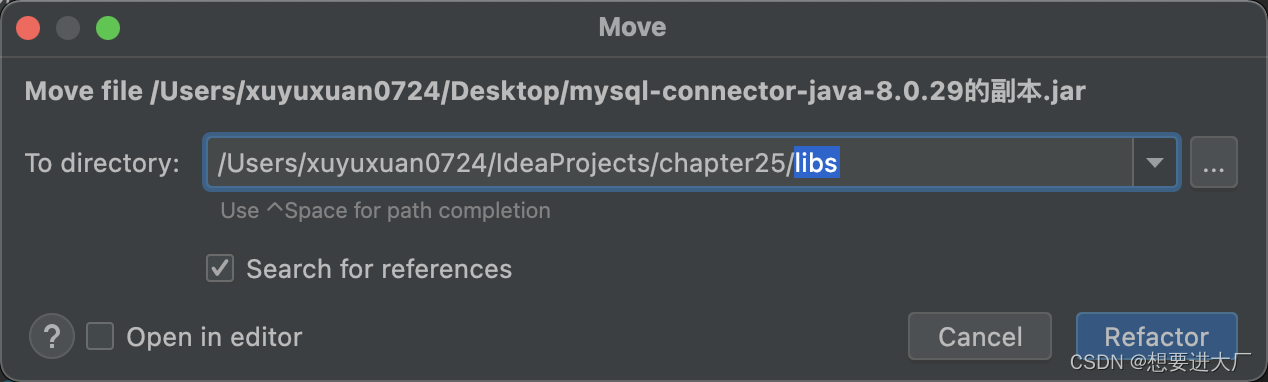
JDBC read this article is enough

Binary search tree concept
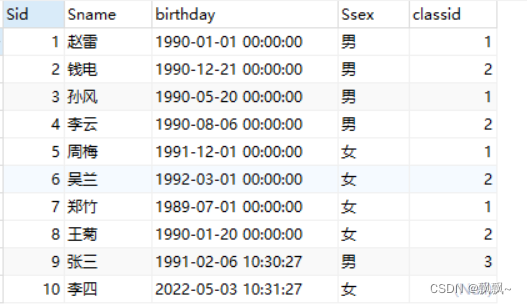
MySQL中什么是索引?常用的索引有哪些种类?索引在什么情况下会失效?
随机推荐
Hackmyvm Target Series (3) - vues
Markdown font color editing teaching
《统计学》第八版贾俊平第七章知识点总结及课后习题答案
浙大版《C语言程序设计实验与习题指导(第3版)》题目集
网络基础详解
Mathematical modeling idea of 2022 central China Cup
【指针】求二维数组中最大元素的值
XSS unexpected event
SystemVerilog discusses loop loop structure and built-in loop variable I
7-14 error ticket (PTA program design)
内网渗透之内网信息收集(三)
[paper reproduction] cyclegan (based on pytorch framework) {unfinished}
XSS之冷门事件
Hackmyvm target series (5) -warez
JVM memory model concept
Uibutton status exploration and customization
Record an API interface SQL injection practice
《统计学》第八版贾俊平第五章概率与概率分布
XSS (cross site scripting attack) for security interview
Only 40% of the articles are original? Here comes the modification method