当前位置:网站首页>JVM memory model concept
JVM memory model concept
2022-07-06 14:22:00 【xmh-sxh-1314】
 JVM The memory model is divided into virtual machine stack , Pile up , Method area , Program counter , Five parts of the local method stack .
JVM The memory model is divided into virtual machine stack , Pile up , Method area , Program counter , Five parts of the local method stack .
Java The virtual machine stack is the same as the program counter ,Java Virtual machine stack (Java Virtual Machine Stacks) It's also thread private , It has the same life cycle as a thread .
Java Heap for most applications ,Java Pile up (Java Heap) yes Java The largest chunk of memory managed by a virtual machine .Java The heap is an area of memory Shared by all threads , Created when the virtual machine starts .
Method area (Method Area) And Java Pile up , Is an area of memory Shared by each thread , It is used to store class information that has been loaded by the virtual machine 、 Constant 、 Static variables 、 Real time compiler compiled code and other data .
Program counter (Program Counter Register) It's a small amount of memory , Its function can be seen
It is the line number indicator of the bytecode executed by the current thread .
Native Method Stack (Native Method Stacks) It's very similar to what the virtual machine stack does , The difference is that the virtual machine stack executes for the virtual machine Java Method ( That's bytecode ) service , The local method stack is used by the virtual machine Native Method service .
JVM The advantages of memory model
Built in memory based concurrency model : Thread mechanism
Synchronization lock Synchronization
A large number of thread safe library packages support
Memory based concurrency mechanism , Flexible granularity control , Flexibility is higher than database lock .
Multi core parallel computing model
Thread based asynchronous model .
边栏推荐
- 搭建域环境(win)
- 【Numpy和Pytorch的数据处理】
- Hackmyvm target series (3) -visions
- Mathematical modeling idea of 2022 central China Cup
- Experiment 7 use of common classes (correction post)
- 图书管理系统
- HackMyvm靶机系列(4)-vulny
- Attack and defense world misc practice area (GIF lift table ext3)
- Yugu p1012 spelling +p1019 word Solitaire (string)
- Network technology related topics
猜你喜欢
List and data frame of R language experiment III
Hackmyvm target series (1) -webmaster
Library management system
Circular queue (C language)
![[VMware abnormal problems] problem analysis & Solutions](/img/64/f44864da600b61a1a646a5865a2083.jpg)
[VMware abnormal problems] problem analysis & Solutions
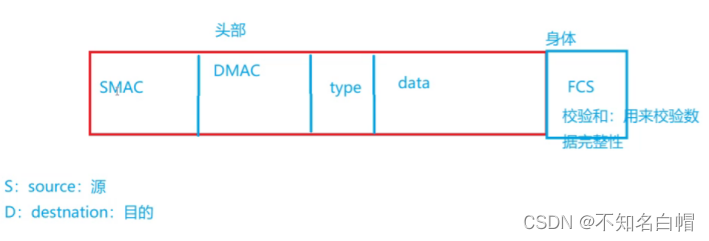
网络基础详解
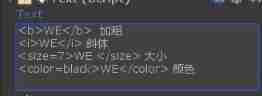
UGUI—Text
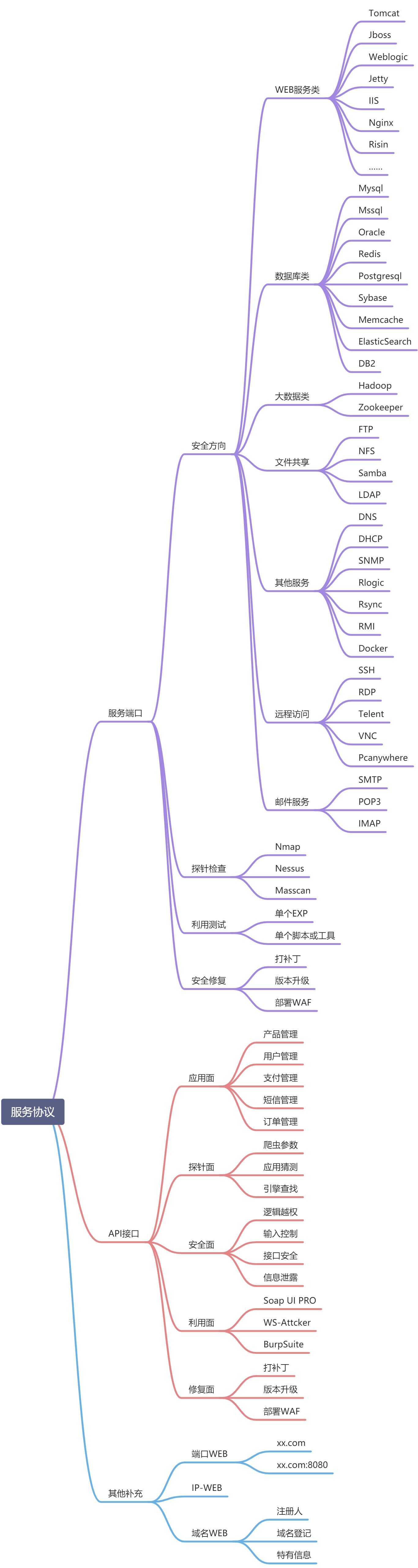
On the idea of vulnerability discovery
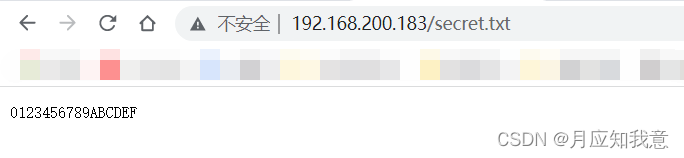
HackMyvm靶机系列(2)-warrior
Ucos-iii learning records (11) - task management
随机推荐
网络层—简单的arp断网
JS several ways to judge whether an object is an array
Strengthen basic learning records
How to turn wechat applet into uniapp
SRC mining ideas and methods
msf生成payload大全
Only 40% of the articles are original? Here comes the modification method
Intranet information collection of Intranet penetration (4)
Hcip -- MPLS experiment
强化学习基础记录
MySQL interview questions (4)
Package bedding of components
HackMyvm靶机系列(5)-warez
Wei Shen of Peking University revealed the current situation: his class is not very good, and there are only 5 or 6 middle-term students left after leaving class
captcha-killer验证码识别插件
攻防世界MISC练习区(gif 掀桌子 ext3 )
Apache APIs IX has the risk of rewriting the x-real-ip header (cve-2022-24112)
Tencent map circle
On the idea of vulnerability discovery
[insert, modify and delete data in the headsong educator data table]