当前位置:网站首页>Talk about four cluster schemes of redis cache, and their advantages and disadvantages
Talk about four cluster schemes of redis cache, and their advantages and disadvantages
2022-07-07 12:45:00 【Java collection】
In service development , A single machine will have a single point of failure , And services are deployed on a server , Once the server goes down, the service is unavailable , So in order to make the service highly available , Distributed services appear , Deploy the same service to multiple machines , Even if several of the servers are down , As long as one server is available, the service is available .
redis Is the same , In order to solve the single machine fault, the master-slave mode is introduced , But there is a problem with the master-slave model :master Service after node failure , It is necessary to manually slave Node switching to maser The service is restored only after the node .redis In order to solve this problem, sentry mode is introduced , Sentinel mode can be in master After node failure, it can automatically salve The node is promoted to master node , Service availability can be restored without manual intervention .
But master-slave mode 、 Sentinel mode has not reached the real data sharding Storage , Every redis All the data stored in the instance is full data , therefore redis cluster It was born , It realizes the real data fragment storage . But because of redis cluster It was released late (2015 The official version was released only in ), The major factories can't wait , Continuously developed their own redis Data fragmentation cluster mode , such as :Twemproxy、Codis etc. .
1. A master-slave mode
redis Although a single node has passed RDB and AOF Persistence mechanism can persist data to hard disk , But the data is stored on a server , If the server has problems such as hard disk failure , Will result in data unavailability , And reading and writing cannot be separated , Read and write on the same server , When there is a large number of requests, there will be I/O bottleneck .
To avoid a single point of failure and Reading and writing are inseparable ,Redis Provides replication (replication) Function realization master After the data in the database is updated , The updated data will be automatically synchronized to other slave Database .
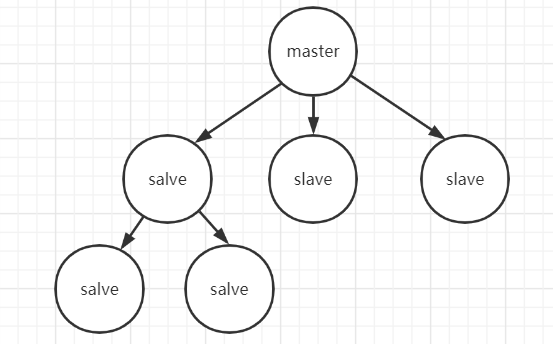
Above redis Characteristics of master-slave structure : One master There can be multiple salve node ;salve Nodes can have slave node , The slave node is a cascade structure .
Advantages and disadvantages of master-slave mode
advantage : The master-slave structure has read-write separation , Increase of efficiency 、 The data backup , Advantages such as providing multiple copies .
Insufficient : The biggest disadvantage is that the master-slave mode does not have the function of automatic fault tolerance and recovery , Primary node failure , Clusters don't work , The availability is relatively low , Manual intervention is required to upgrade the slave node to the master node .
Common master-slave mode , When the primary database crashes , You need to manually switch from database to master :
Using... From a database
SLAVE NO ONEThe command will be promoted from the database to the master data to continue the service .Crash the main database before starting , And then use SLAVEOF Command to set it to the slave database of the new master database , You can synchronize the data .
2. Sentinel mode
The first is master-slave synchronization / The pattern of replication , When the primary server goes down , You need to manually switch one from the server to the primary server , This requires human intervention , Laborious and arduous , It will also make the service unavailable for a period of time , Sentinel mode is needed at this time .
Sentinel mode is from Redis Of 2.6 The version begins to provide , But at that time, the mode of this version was unstable , until Redis Of 2.8 After the version , This sentinel mode just stabilized .
The core of sentinel mode is master-slave replication , However, in the case of master-slave mode, it can only lead to downtime , An additional election mechanism : Elect a new master node from all slave nodes . The realization of the election mechanism , It depends on starting a... In the system sentinel process .
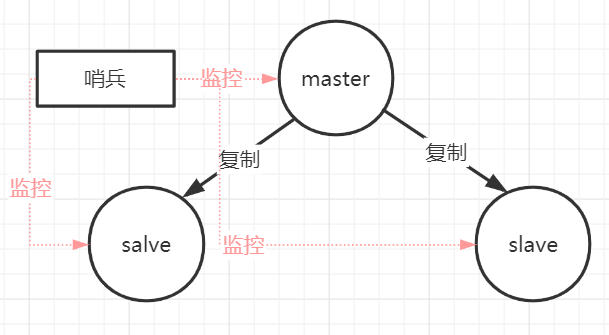
Pictured above , The sentry itself has a single point of failure , So in one master and many followers Redis In the system , Multiple sentinels can be used to monitor , Sentinels not only monitor the master and slave databases , Sentinels also monitor each other . Each sentinel is an independent process , As a process , It will run on its own .
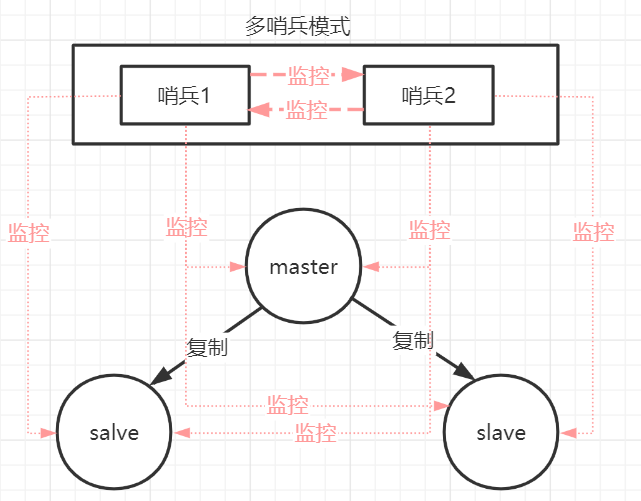
(1) The role of sentinel mode :
Monitor all servers for normal operation : Return the running status of the monitoring server by sending a command , Process and monitor the master server 、 From outside the server , Sentinels also monitor each other .
Fail over : When the Sentinels detect master Downtime , Will automatically slave Switch to master, Then the other slave servers are informed through publish subscribe mode , Modify the configuration file , Let them switch master. At the same time, the old master with problems will become the slave of the new master , That is, when the old lord recovers , It doesn't restore the original identity of master , But as a slave of the new Lord .
(2) Sentinel implementation principle
Sentinels start the process , Will read the contents of the configuration file , Find out the main database to be monitored through the following configuration :
sentinel monitor master-name ip port quorum
#master-name It's the name of the main database
#ip and port Is the current master database address and port number
#quorum Indicates before performing a failover operation , How many sentry nodes need to agree .The reason why we only need to connect the master node , It's because through the master node info command , Get information from the node , So that you can connect to the slave node as well , At the same time, it can also pass through the info Information knows the information of the new slave node .
A sentinel node can monitor multiple master nodes , But it's not advocated , Because when the sentinel node crashes , At the same time, multiple cluster handoffs will fail . After the Sentinels started , Two connections will be made to the main database .
Subscribe to the master database
_sentinel_:helloChannel to get sentinel node information that also monitors the databaseSend... To the main database on a regular basis info command , Get information about the master database itself .
After establishing a connection with the primary database, the following three operations will be performed regularly :
(1) every other 10s towards master and slave send out info command . The function is to obtain the current database information , For example, when a new slave node is found , Will establish a connection , And add it to the monitoring list , When the role of master-slave database changes, update the information .
(2) every other 2s To the master data and from the database _sentinel_:hello Channel sends its own message . The function is to share your monitoring data with the sentry . Every sentinel will subscribe to the database _sentinel:hello channel , When the other sentinels get the message , Will determine if the sentry is a new sentry , If so, add it to the sentinel list , And establish a connection .
(3) every other 1s Send to all master-slave nodes and all sentinel nodes ping command , The function is to monitor whether the node is alive .
(3) Subjective offline and objective offline
Sentinel node sends ping On command , When it's over a certain period of time (down-after-millisecond) after , If the node does not reply , Then the sentry thinks that . Subjective offline means that the current sentinel thinks that the node is already below , If the node is the primary database , The Sentry will further judge whether it is enough to fail over , At this time, you have to send commands (SENTINEL is-master-down-by-addr) Ask other sentinel nodes whether they think the master node is a subjective offline node , When the specified quantity is reached (quorum) when , The Sentry will think it's objective .
When the master node is offline objectively, it needs to switch between master and slave , The steps of master-slave switching are :
Select the leading sentry .
All of the leading sentinels slave Select the highest priority from the database . Priority can be achieved by
slave-priorityOption is set .If the priority is the same , The larger the offset from the copied command ( That is, the more synchronous data is copied , The more new the data is ), Higher priority .
If all the above conditions are the same , select run ID Smaller from the database .
Select one from the database , The sentry sent slave no one Command upgrade to main database , And send the slaveof Command to set the master database of other slave nodes as the new master database .
(4) The advantages and disadvantages of sentry mode
1. advantage
Sentinel mode is based on the master-slave model , It can be solved in master-slave mode master The failure cannot be automatically switched .
2. Insufficient - problem
It is a centralized cluster implementation scheme : There is always one Redis The host receives and processes write requests , Write operations are affected by stand-alone bottlenecks .
All nodes in the cluster store full data , Wasted memory space , There is no real implementation of distributed storage . When the amount of data is too large , Master slave synchronization seriously affects master Performance of .
Redis After the host goes down , Sentinel mode is outside the voting situation , Because before the voting is over , No one knows who the master and slave are , here Redis It will also turn on the protection mechanism , Do not write , Until a new election Redis host .
in addition , public Number Java selected , reply java interview , obtain redis Interview information , Support online question brushing .
In master-slave mode or sentinel mode, the data stored in each node is the full amount of data , When the amount of data is too large , The stored data needs to be segmented and stored in multiple redis For instance . At this point, we need to use Redis Sharding technology .
3. Of the major factories Redis Cluster solution
Redis stay 3.0 Only single instance mode is supported before version , although Redis The developer of the Antirez As early as on my blog, I put forward in Redis 3.0 Add the function of cluster in version , but 3.0 Version wait until 2015 The official version was released only in . Major enterprises can't wait , stay 3.0 Before the release, in order to solve Redis Storage bottleneck of , Have launched their own Redis Cluster solution . The core idea of these schemes is to slice the data (sharding) Store in multiple Redis In the example , Every piece is one Redis example .
(1) Client fragmentation
Client sharding is to put the logic of sharding in Redis Client implementation ,( such as :jedis Already supported Redis Sharding function , namely ShardedJedis), adopt Redis Pre defined routing rules of the client ( Use consistent hashes ), Put right Key Forward your access to different Redis In the example , Collect the returned results when querying data . The pattern of this scheme is shown in the figure .
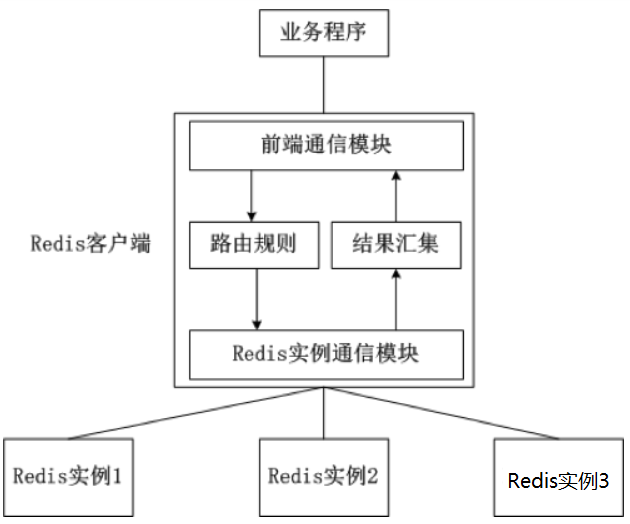
Advantages and disadvantages of client fragmentation :
advantage : client sharding engineering service hash The advantage of consistent algorithm fragmentation is that all logic is controllable , Independent of third-party distributed middleware . Server side Redis Examples are independent of each other , There's no connection , Every Redis The instance runs like a single server , It's very easy to expand linearly , The system is very flexible . Developers know how to implement sharding 、 Routing rules , Don't worry about stepping on the pit .
1. Consistent hash algorithm :
It is a commonly used algorithm in distributed systems . such as , A distributed storage system , To store data on specific nodes , If we use ordinary hash Method , Map data to specific nodes , Such as mod(key,d),key It's data key,d Is the number of machine nodes , If a machine joins or exits the cluster , All data mappings are invalid .
The consistent hash algorithm solves the common remainder Hash The problem of poor scalability of the algorithm , It can be guaranteed to be online 、 In the case of offline servers, try to hit as many requests as possible to the original server .
2. Realization way : Uniformity hash Algorithm , such as MURMUR_HASH Hash algorithm 、ketamahash Algorithm
such as Jedis Of Redis Sharding Realization , Using a consistent hash algorithm (consistent hashing), take key And nodes name meanwhile hashing, And then map matching , The algorithm used is MURMUR_HASH.
The main reason for using consistent hashing instead of simple hash like modular mapping is that when nodes are added or reduced , It's not going to be caused by a rematch rehashing. The consistency hash only affects adjacent nodes key Distribute , The influence is small .
Insufficient :
This is a static fragmentation scheme , Need to increase or decrease Redis Number of instances , Need to manually adjust the slice program .
The operation and maintenance cost is relatively high , If there is any problem with the data of the cluster, the operation and maintenance personnel and developers need to work together , Slow down the speed of problem solving , Increases the cost of cross departmental communication .
In different client programs , Maintaining the same route fragmentation logic costs a lot . such as :java project 、PHP Share one set in the project Redis colony , Routing fragment logic needs to write two sets of the same logic , There will be two sets of maintenance in the future .
One of the biggest problems with client fragmentation is , Server side Redis When the topological structure of the instance group changes , Every client needs to update and adjust . If the client partition module can be carried out separately , Form a separate module ( middleware ), As a client and The bridge connecting the server can solve this problem , At this point, the agent partition appears .
(2) Agency segmentation
redis The most commonly used proxy segmentation is Twemproxy, from Twitter Open source Redis agent , The basic idea is this : In the form of middleware ,Redis The client sends the request to Twemproxy,Twemproxy Send to the correct destination according to the routing rules Redis example , Last Twemproxy Collect the results and return them to the client .
Twemproxy By introducing a proxy layer , Will be multiple Redis Unified management of instances , send Redis The client only needs to be in Twemproxy Operation on top , You don't need to care about how many there are behind Redis example , So that Redis colony .
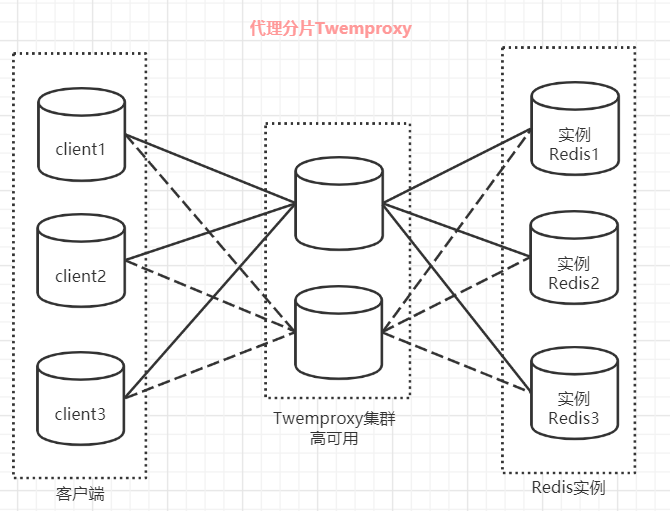
Twemproxy The advantages of :
The client is like a connection Redis Connect like an instance Twemproxy, No logic needs to be changed .
Invalid support Redis Automatic deletion of instances .
Twemproxy And Redis Instance remains connected , Reduces client and server costs Redis Number of connections to the instance .
Twemproxy Deficiency :
because Redis Every request from the client goes through Twemproxy The agent can arrive at Redis The server , There will be performance loss in this process .
There is no friendly monitoring and management background interface , It is not conducive to operation and maintenance monitoring .
Twemproxy The biggest pain point is , Can't expand smoothly / Shrinkage capacity . For operation and maintenance personnel , When business needs increase Redis The workload of the instance is very heavy .
Twemproxy As the most widely used 、 The most tested 、 The most stable Redis agent , It is widely used in the industry .
(3)Codis
Twemproxy Cannot increase smoothly Redis The problem of instance brings great inconvenience , So the pea pod was independently developed Codis, One supports smooth increase Redis Example of Redis Agent software , It is based on Go and C Language development , And in 2014 year 11 Month in GitHub The open source .
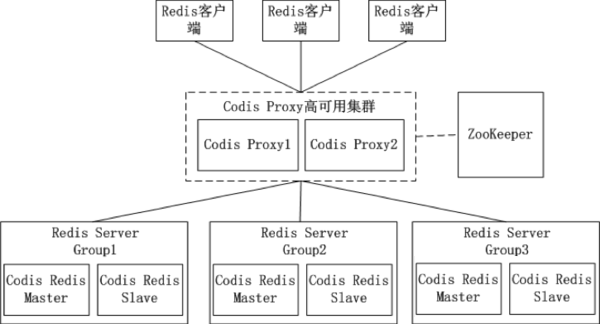
stay Codis In the architecture diagram of ,Codis Introduced Redis Server Group, This is done by specifying a master CodisRedis And one or more from CodisRedis, Realized Redis High availability of clusters . Be a master CodisRedis Hang up ,Codis It doesn't automatically take one from CodisRedis Promotion centered CodisRedis, This involves the consistency of data (Redis The data synchronization of itself adopts master-slave asynchronous replication , When the data is in the master CodisRedis When the write is successful , from CodisRedis There is no guarantee that this data has been read ), The administrator needs to manually switch from... On the management interface CodisRedis Promotion centered CodisRedis.
If manual processing is troublesome , Pea pods also provide a tool Codis-ha, This tool will detect the main CodisRedis When you hang up, take it offline and upgrade it by one from CodisRedis Mainly CodisRedis.
Codis In the form of pre segmentation , It's created at startup 1024 individual slot,1 individual slot amount to 1 A box , Each box has a fixed number , The scope is 1~1024.slot This box is used for storing Key, as for Key Which box to store , You can use the algorithm “crc32(key)%1024” Get a number , The range of this number must be 1~1024 Between ,Key Just put it in the... Corresponding to this number slot.
for example , If a Key By algorithm “crc32(key)%1024” The number is 5, Just put it in the code as 5 Of slot( The box ).1 individual slot You can only put 1 individual Redis Server Group, Can't take 1 individual slot Put it in multiple Redis Server Group in .1 individual Redis Server Group It can be stored at least 1 individual slot, Can store up to 1024 individual slot. therefore ,Codis You can specify at most 1024 individual Redis Server Group.
Codis The biggest advantage is that it supports smooth increase ( Reduce )Redis Server Group(Redis example ), Can be safe 、 Transparently migrate data , This is also Codis Different from Twemproxy Such as static distribution Redis Where the solution is .Codis Added Redis Server Group after , It involves slot The problem of migration .
for example , The system has two Redis Server Group,Redis Server Group and slot The corresponding relationship is as follows .
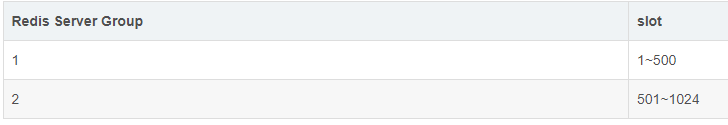
When you add a Redis Server Group,slot It's about to be redistributed .Codis Distribute slot There are two ways :
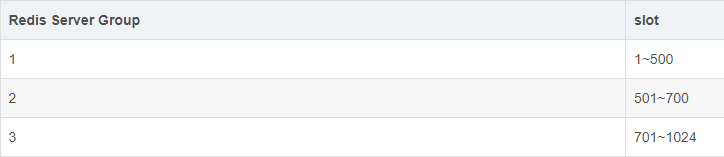
The first one is : adopt Codis Management tools Codisconfig Manual reassignment , Specify each Redis Server Group The corresponding slot The scope of the , for example : You can specify Redis Server Group and slot The new correspondence of is as follows .
The second kind : adopt Codis Management tools Codisconfig Of rebalance function , Automatically according to each Redis Server Group Memory pair slot Migration , To achieve data balance .
4.Redis Cluster
Redis Although the sentinel mode of has been able to achieve high availability , Read / write separation , However, there are several deficiencies :
In sentinel mode, each Redis Servers all store the same data , It's a waste of memory space ; Too much data , The master-slave synchronization seriously affects master performance .
Sentinel mode is a centralized cluster implementation scheme , Each slave is highly coupled with the host ,master Downtime to salve The election master Service unavailable during recovery .
Sentinel mode always has only one Redis The host receives and processes write requests , Write operations are still affected by stand-alone bottlenecks , There is no real distributed architecture .
redis stay 3.0 Added on Cluster Cluster pattern , Realized Redis Distributed storage , That is to say, each one Redis Different data is stored on the node .cluster Mode is to solve the problem of single machine Redis The problem of limited capacity , Allocate data to multiple machines according to certain rules , Memory /QPS Not limited to a single machine , It can benefit from the high scalability of distributed clusters .
Redis Cluster It's a kind of server Sharding technology ( Sharding and routing are implemented on the server ), Adopt multi master and multi subordinate , Each partition is made up of a Redis The master and multiple slaves consist of , Areas are parallel to each other .Redis Cluster Cluster adopted P2P The pattern of , Completely decentralized .
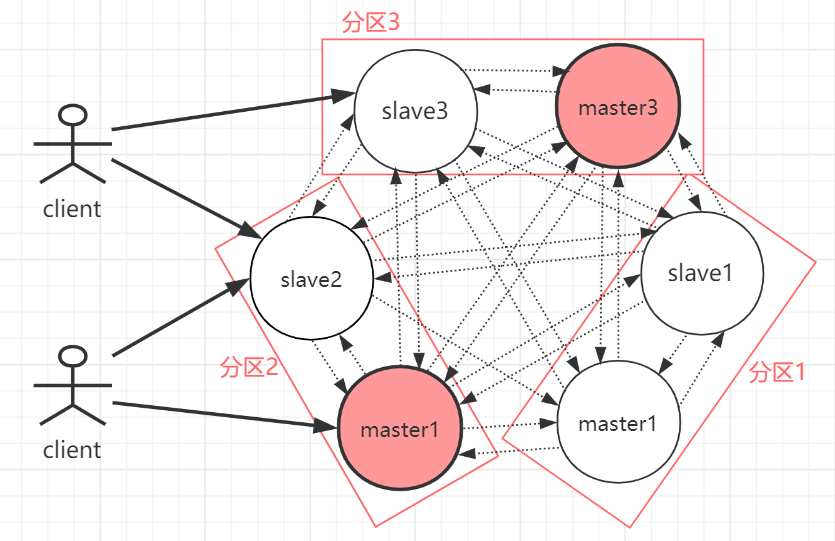
Pictured above , The official recommendation , Cluster deployment at a minimum 3 Table above master node , Best use 3 Lord 3 From the six node model .Redis Cluster Cluster has the following characteristics :
Clusters are completely decentralized , Adopt multi master and multi subordinate ; be-all redis Nodes interconnect with each other (PING-PONG Mechanism ), Internally, binary protocols are used to optimize transmission speed and bandwidth .
The client and Redis Node is directly connected , No intermediate agent layer is needed . The client does not need to connect to all the nodes of the cluster , Connect to any of the available nodes in the cluster .
Each partition is made up of a Redis The master and multiple slaves consist of , Pieces and pieces are parallel to each other .
every last master The node is responsible for maintaining part of the slot , And the key value data mapped by the slot ; Each node in the cluster has a full amount of slot information , Through each slot node We all know where the specific data is stored node On .
redis cluster Mainly for massive data + High concurrency + Highly available scenarios , Huge amounts of data , If you have a lot of data , Then the suggestion is to use redis cluster, When the amount of data is not very large , Use sentinel That's enough .redis cluster Its performance and high availability are better than sentinel mode .
Redis Cluster Use virtual hash slot partitioning instead of consistency hash Algorithm , Pre allocate some card slots , All keys are mapped into these slots according to the hash function , Within each partition master The node is responsible for maintaining part of the slot and the key value data mapped by the slot .
Copyright notice : This paper is about CSDN Blogger 「 Yes, sir 」 The original article of , follow CC 4.0 BY-SA Copyright agreement , For reprint, please attach the original source link and this statement .
https://blog.csdn.net/Seky_fei/article/details/107239765
official account “Java selected ” The published content indicates the source of , All rights reserved ( Those whose copyright cannot be verified or whose source is not indicated all come from the Internet , Reprinted , The purpose of reprinting is to convey more information , The copyright belongs to the original author . If there is any infringement , Please contact the , The author will delete the first time !
Many people have asked recently , Is there any readers Communication group ! The way to join is simple , official account Java selected , reply “ Add group ”, You can join the group !
Java Interview questions ( Wechat applet ):3000+ The road test questions , contain Java Basics 、 Concurrent 、JVM、 Threads 、MQ series 、Redis、Spring series 、Elasticsearch、Docker、K8s、Flink、Spark、 Architecture design, etc , Brush questions online at any time !
------ Special recommendation ------
Special recommendation : Focus on the most cutting-edge information and technology sharing , Official account for preparing for overtaking on curves and various open source projects and efficient software ,「 Big coffee notes 」, Focus on finding good things , It's worth your attention . Click the official account card below to follow .
If the article helps , Click to see , Forward! !
边栏推荐
- Day-20 file operation, recursive copy, serialization
- Connect to blog method, overload, recursion
- SQL Lab (41~45) (continuous update later)
- 【PyTorch实战】用PyTorch实现基于神经网络的图像风格迁移
- 牛客网刷题网址
- leetcode刷题:二叉树23(二叉搜索树中的众数)
- About IPSec
- ACL 2022 | 序列标注的小样本NER:融合标签语义的双塔BERT模型
- How to use PS link layer and shortcut keys, and how to do PS layer link
- SQL Lab (32~35) contains the principle understanding and precautions of wide byte injection (continuously updated later)
猜你喜欢
MPLS experiment
File upload vulnerability - upload labs (1~2)

2022广东省安全员A证第三批(主要负责人)考试练习题及模拟考试

Customize the web service configuration file
SQL Lab (41~45) (continuous update later)
SQL Lab (46~53) (continuous update later) order by injection
In the small skin panel, use CMD to enter the MySQL command, including the MySQL error unknown variable 'secure_ file_ Priv 'solution (super detailed)
SQL Lab (36~40) includes stack injection, MySQL_ real_ escape_ The difference between string and addslashes (continuous update after)

爱可可AI前沿推介(7.7)
NPM instal reports agent or network problems
随机推荐
Zhimei creative website exercise
SQL Lab (41~45) (continuous update later)
【统计学习方法】学习笔记——第四章:朴素贝叶斯法
[Q&A]AttributeError: module ‘signal‘ has no attribute ‘SIGALRM‘
Day-15 common APIs and exception mechanisms
数据库安全的重要性
[Q&A]AttributeError: module ‘signal‘ has no attribute ‘SIGALRM‘
Financial data acquisition (III) when a crawler encounters a web page that needs to scroll with the mouse wheel to refresh the data (nanny level tutorial)
Epp+dis learning path (1) -- Hello world!
对话PPIO联合创始人王闻宇:整合边缘算力资源,开拓更多音视频服务场景
SQL Lab (46~53) (continuous update later) order by injection
Realize a simple version of array by yourself from
【从 0 开始学微服务】【01】什么是微服务
Typescript interface inheritance
SQL Lab (32~35) contains the principle understanding and precautions of wide byte injection (continuously updated later)
广州市召开安全生产工作会议
Experiment with a web server that configures its own content
Day-14 common APIs
H3C HCl MPLS layer 2 dedicated line experiment
GCC compilation error