当前位置:网站首页>[information security laws and regulations] review
[information security laws and regulations] review
2022-07-07 19:04:00 【Godams】
Examples are given to illustrate the static password and dynamic password mechanisms in common systems
- static password : Static password is actually a password word ; It is the most common authentication method in daily use , But security is also the most fragile authentication method , Such as password
- One-time password : Dynamic password is also called one-time password , It is more secure than static passwords . There are generally two kinds : Synchronous and asynchronous , Such as SMS verification code
Briefly describe the network boundary and communication security technology ?
(1) Physical isolation technology :“ Physical isolation ” It means that the intranet is not directly connected to the public network through wired or wireless means , So that the internal network and external public network are physically isolated . It is divided into network isolation and data isolation , Network isolation : Is to open the protected network 、 Borderless 、 Independent in a free environment , such , Hackers and computer viruses on the public Internet have no way to start , Not to mention invasion ; Data isolation : It refers to taking all possible means to prevent malware from invading protected data resources .
(2) Firewall technology : Concept : Firewall is a device or a set of system that controls the traffic between different security areas of the network , It can enhance the security of the organization's internal network .
(3) Network communication security technology : Network communication security technology is mainly based on TCP/IP Protocol security solutions at different levels , For enhancement TCP/IP Security of network communication
(4) Transport layer security technology : The purpose of transport layer security protocol is to protect the security of transport layer , And provide and realize confidentiality on the transport layer 、 Methods of authentication and integrity .
Virtual private network technology
Briefly describe the security technology of computing environment ?
(1) software security (software security): There is no unified explanation , Its main idea is to take a series of technical and management measures to ensure the safety of computer software .
(2) Software patches : It is aimed at some large software systems , A small program that fixes vulnerabilities due to problems exposed during use .
(3) Anti virus technology : Virus prevention technology 、 Virus detection technology 、 Virus removal technology
(4) Virtualization security : Traditional virtualization technology mainly refers to server virtualization , At present, network virtualization and other technologies are becoming more and more mature .
What are the characteristics of virtualization security threats ? Analyze whether the traditional protection technology is competent .
Virtualization technology has brought about changes in computing and service patterns , But it also brings some new security threats , For example, for virtual machine operation
Kernel level attacks can break through system boundaries , Cause greater harm than the traditional system environment .
The biggest difference between virtualized environment and physical environment is , In the physical environment, the operating system only enjoys the hardware resources of the physical machine . In virtualization
In the environment , Added the technology layer of virtual machine monitor , The guest operating system uses logical resources abstracted by the virtual machine monitor
Source , Multiple virtual machines can exist simultaneously on the same physical machine , These virtual machines share the underlying physical resources , in addition , In a virtualized environment
Be able to migrate virtual machines , Snapshots and backups .
Virtualization security threats :
The security threat of virtualization module itself
Security threats introduced by virtualization
Security threats introduced by multi business environment
Virtualization security enhancement challenges :
Traditional enterprise networks are divided into different security domains , And deploy network security devices such as firewalls between different security domains
Most virtualization security technologies use traditional host protection methods to enhance the security of virtual machines
Adopting virtualization layer security enhancement is a research hotspot
* Network intrusion detection technology :P2DR Model 、 intrusion detection system IDS、 Intrusion prevention system IPS
What is information security audit ? What are its functions ?
Information system security audit mainly refers to the identification of information related to security related activities 、 Record 、 Storage and Analysis ; The results of audit records are used to check what security related activities have taken place on the network , who ( Which user ) Be responsible for this activity ;
The main functions include : Automatic response of security audit 、 Security audit data generation 、 Safety audit analysis 、 Security audit browsing 、 Security audit event selection 、 Security audit event storage .
function ; obtain evidence 、 Deterrence 、 Discover system vulnerabilities 、 Abnormal operation of the system is found 、 Evaluation standard compliance
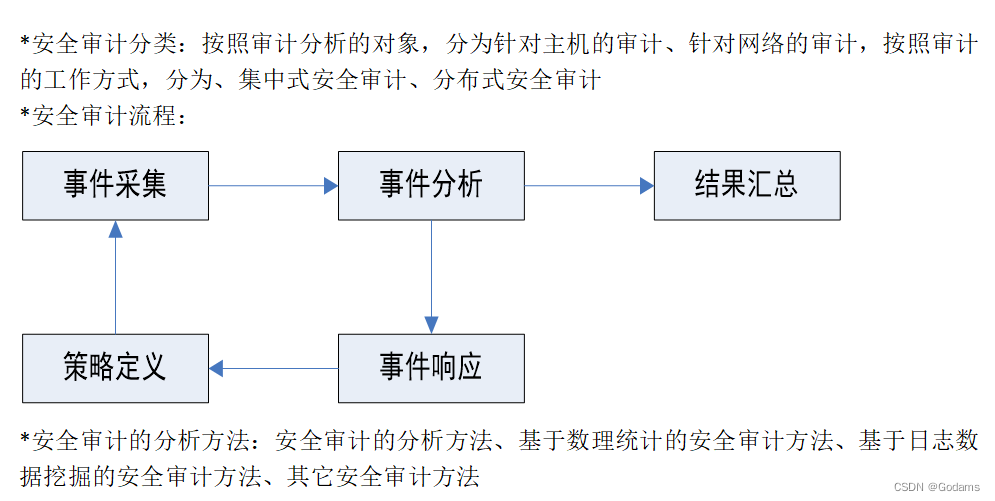
What data sources are available for security audit ?
- Host based data sources : Audit records of the operating system 、 system log 、 Application log information
- Network based data source : Intrusion detection data , There are advantages :
Get network packets through passive network monitoring , It will not have any impact on the operation performance of the target monitoring system , And there is usually no need to change the original structure and working mode .
The sniffer module can work in a transparent mode to network users , It reduces the probability of being attacked . - Input information source based on network data , Many attack methods based on host data sources can be found , For example, the vulnerability discovery process based on Network Protocol , Or send abnormal network packets and a large number of misused packets DOS Attack, etc . The degree of standardization of network packets , Much higher than the host data source , For example, at present, almost most network protocols have adopted TCP/IP Protocol family . Due to the high degree of standardization , therefore , It is conducive to the transplantation of security audit system in different system platform environments .
- Other data sources : Data sources from other security products 、 Data sources from network devices 、 Out of band data source
Analyze the structure of centralized security audit and distributed security audit .
- The centralized architecture adopts a centralized approach , Collect and analyze data sources , All data should be submitted to the central processing unit for audit processing . The central processing unit undertakes the work of data management engine and security audit engine . The peripheral devices deployed on each monitored system are just simple data acquisition devices , Assume the role of event detection and data collection engine . With the wide application of distributed network technology, centralized audit architecture shows more and more defects , Mainly in : Centralized audit architecture increasingly shows its shortcomings , Mainly in : cause CPU、I/O And the burden of network communication , And the central computer is often prone to a single point of failure, which may cause the unavailability of the entire audit data due to the failure of a single point. The centralized architecture , Poor adaptability , Configuration cannot be changed automatically according to environmental changes
- The distributed security audit architecture consists of three parts : Host agent module 、 LAN Monitor agent module 、 Central manager module
advantage : Strong expansion ability 、 Strong fault tolerance 、 Strong compatibility 、 Strong adaptability
CC What are the requirements for safety audit ? Our national standard GB17859-1999 What are the requirements ?
CC The standard is based on the concept that safety functions are independent of safety assurance measures , In terms of organization, it is divided into basic concepts 、 Security function requirements and security assurance requirements .
CC in , Security requirements are based on classes 、 family 、 Define the hierarchical form of components . There are six families of security audit , The selection of audit records 、 Generate 、 Storage 、 Protect 、 Analysis and corresponding intrusion response and other functions have made different requirements .
China's national standard for information security GB 17859-1999《 Classification criteria for security protection level of computer information system 》 Five security levels are defined , Among them, the four higher levels have put forward clear requirements for audit
The concept of computer forensics and its existing technologies ?
Computer forensics is computer intrusion 、 damage 、 cheat 、 Attacks and other criminal acts , Using computer software and hardware technology , In a manner consistent with legal norms , For identification 、 preservation 、 The process of analyzing and submitting digital evidence .
According to the process of computer forensics , The related technologies involved are generally as follows :
Electronic evidence Monitoring Technology
Physical evidence acquisition technology
Electronic evidence collection technology
Electronic evidence preservation technology
Electronic evidence processing and identification technology
Electronic evidence submission Technology
Steps of computer forensics ?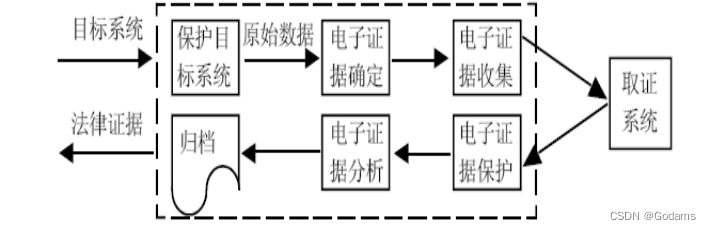
Business Continuity Management ? What is the goal ?
(⼀) Protect ⽬ Mark computer system
In the process of computer forensics , The first ⼀ The first thing to do is to freeze the computer system , Avoid sending ⽣ Any changes to system settings 、 Hardware damage 、 Data corruption or virus
Infection, etc .
(⼆) electric ⼦ Confirmation of evidence
From storage in ⼤ In the massive data of capacity media , Distinguish which ones have ⽤ data , What is garbage data , In order to determine the activity records left by the criminals as the main electricity ⼦ evidence , And determine where these records exist ⾥、 How is it stored .
( 3、 ... and ) electric ⼦ Collection of evidence
Identification of ⼈ The policeman collects electricity at the computer crime scene ⼦ Of evidence ⼯ The operation includes collecting the hardware configuration information of the system and ⽹ Complex structure , Back up or print the original number of the system
According to the , And collect key evidence data to forensics equipment , And record relevant ⽇ period 、 Time and operation steps .
( Four ) electric ⼦ Protection of evidence
Mining ⽤ Effective measures to protect electricity ⼦ Integrity and authenticity of evidence , Include ⽤ proper ⼀ Secondary read-only storage media ( Such as CD-ROM) Into the ⾏ Original backup , Seal the backup media and put it in a safe place ⽅; For the electricity stored on the forensics server ⼦ The evidence is ⽤ encryption 、 Physical isolation 、 build ⽴ The security monitoring system monitors the operation of the forensics system in real time ⾏ State and other safety measures ⾏ Protect ,⾮ relevant ⼈ The operator is not allowed to operate and store electricity ⼦ Computer of evidence ; Not easy to delete or modify with evidence ⽆ Off ⽂ Pieces of , So as not to cause valuable evidence ⽂ Permanent loss of pieces .
( 5、 ... and ) electric ⼦ Analysis of evidence
On electricity ⼦ The analysis of evidence and the result report are electricity ⼦ Whether the evidence can be displayed in court ⽰, As a suspect in prosecuting computer crimes ⼈ The important process of criminal evidence . The analysis includes ⽤⼀ Series of keyword search to get the most important information ; Yes ⽂ Piece properties 、⽂ Digital summary and ⽇ Zhijin ⾏ analysis ; analysis Windows In exchange for ⽂ Pieces of 、⽂ Broken pieces ⽚ And data in unallocated space ; On electricity ⼦ The evidence is ⼀ Some intelligent correlation analysis , That is to discover the same ⼀ The connection between the different evidences of the event ; Finish the electricity ⼦ After the analysis of the evidence, an expert certificate is given , This is similar to that of forensic medicine when investigating ordinary crimes ⾓⾊ similar .
( 6、 ... and ) file
For those involved in computer crime ⽇ Date and time 、 Partition of hard disk 、 Operating system and version 、 shipment ⾏ obtain evidence ⼯ Integrity of temporal data and operating system 、 Computer virus evaluation 、⽂ Piece type 、 Software license and identification ⼈ Clerk to electricity ⼦ The analysis results of evidence and evaluation report etc ⾏ Filing , Form evidence that can be provided to the court .
The difference between a business continuity plan and a disaster recovery plan ?
Disaster recovery is the ability to recover data , Solve the problem of information system disaster recovery , Is part of the business continuity plan . Business continuity emphasizes the uninterrupted ability of the organization's business .
Emergency response plan , What are its purposes and principles ?
The preparation of emergency plans should follow ” people oriented 、 According to the law 、 In line with reality 、 Focus on effectiveness “ Principles .
Its purpose is to reduce sudden
Losses caused by the incident , Including the lives of the people 、 property loss , Economic losses of the state and enterprises , And the corresponding social evils
Influence, etc
What are the backup technologies ?
Data replication technology : The way of data replication 、 The form of data replication 、 Hierarchy of data replication
Redundancy technology
Disk mirroring technology
Providing business continuity for important applications and processes of an organization should include the following three aspects , Interrelated and cross : High availability 、 Continuous operation 、 disaster recovery
The strategies to deal with risks are to avoid risks 、 Reduce risk 、 There are four kinds of risks: transferring risks and accepting risks
According to the results of risk analysis and business impact analysis , Determine disaster recovery objectives , Include : Key business functions and priorities for recovery , Disaster recovery timeframe . The recovery time goal (RTO) And recovery point objectives (RPO) The scope of the .RPO For data loss , and RTO For service loss , There is no necessary correlation between the two .
Backup policy : Full backup 、 Incremental backup 、 Differential backup 、 Comprehensive full backup
Evaluation framework of information system security ?
The conceptual framework of information system security classification protection evaluation consists of three parts : Evaluation input 、 Evaluation process and evaluation output 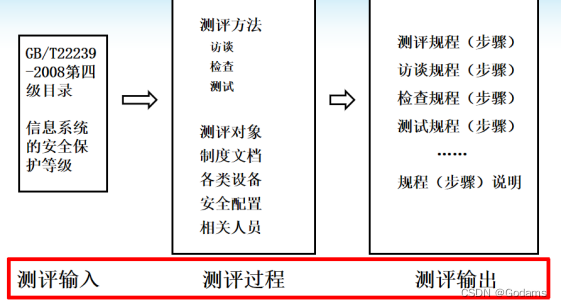
Evaluation input includes GB/T22239-2008 The security protection level of the fourth level directory and information system
The process component is a group of specific evaluation objects and evaluation methods related to the security control identified in the input component .
The output component includes a set of procedural statements used by evaluators to determine the effectiveness of safety controls .
What are the basic principles of information system security management evaluation ?
The evaluation of information system security management should be scientific 、 effectiveness 、 Besides the basic principles of impartiality , The following principles should also be followed : The principle of systematization 、 Standardization principle 、 The principle of consistency 、 The principle of risk controllability 、 Safety management assurance principle 、 Principles of safety and impartiality
Flow chart of risk assessment .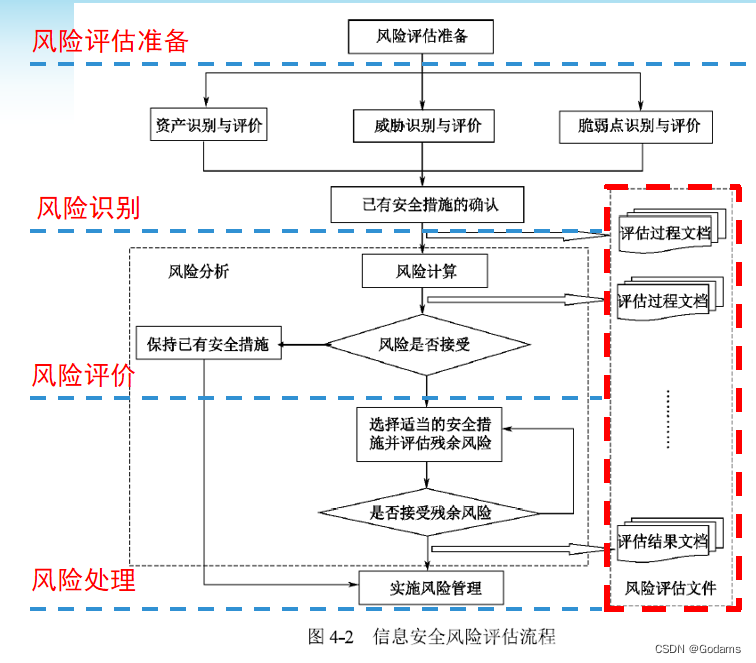
What are the documents in the risk assessment ?
The risk assessment documents include the assessment process documents and assessment result documents generated in the whole risk assessment process , Include : Risk assessment plan , Risk assessment process , Asset identification list , List of important assets , Threat list , List of vulnerabilities , There is a confirmation form of safety measures , Risk assessment report , Risk management plan , Risk assessment records .
What are the analysis steps of probabilistic risk assessment and dynamic probabilistic assessment ?
Identify the events that exist in the system , Find out the source of risk
Investigate the status of each risk source in system security , And their logical relationship , Give the risk source tree of the system
Identify the consequence size and risk probability of each risk source
The risk sources are combined through logical and mathematical methods , Finally, we get the measurement of system risk
What are the basic principles of social stability risk assessment ?
( One ) Adhere to the principle of people-oriented . Take whether the people support and support as the basic standard to measure whether various policies and initiatives have been introduced ; Take the satisfaction of the people as the basic yardstick ; Take safeguarding the fundamental interests of the broad masses of the people as the starting point and foothold . Reach the evaluation of being human , Evaluation depends on people , The evaluation result depends on people . conversely , Stability risk assessment will lose benchmark 、 footstone 、 Keynote , It will become no loss 、 No origin , The fundamental premise of losing your job .
㈡ Apply the principle of correct evaluation results . Whether the evaluation results can be introduced as a major policy 、 Decisions can be implemented 、 Whether the project can be run well 、 An important basis for success . Especially things that involve the vital interests of the masses , Make full use of the assessment results . The project application department shall take the result of stability risk assessment as the precondition for project application , The project approval department should take the evaluation results as one of the important basis for project implementation , For projects that have been evaluated and decided to implement , The unit responsible for the implementation of the project and the local government under its jurisdiction should track and do a good job in maintaining stability throughout the process .
( 3、 ... and ) Strictly evaluate the principle of responsibility . We should earnestly do a good job in the construction of social stability risk assessment mechanism , Bring the implementation of social stability risk assessment into the important assessment content of the annual work of departments at all levels , As a reward and punishment for the unit, collective and individual leaders 、 One of the bases for promotion , Supervise the implementation of responsibilities .
( Four ) Adhere to the principle of promoting development . The purpose of social stability risk assessment is to better promote development , therefore , The evaluation must stand at a high altitude 、 Wide vision , Strictly abide by the major policies of the Central Committee , Correctly handle the relationship between reform and development and social stability , Strive to evaluate the items in line with the reform efforts 、 The organic unity of development speed and social affordability .
( 5、 ... and ) Adhere to the principles of democracy and the rule of law . Combine social stability risk assessment with democracy and legal system . Build a perfect decision-making system , Gradually form interest coordination 、 Appeal expression 、 Conflict resolution 、 A long-term mechanism for protecting rights and interests , Adhere to the unity of legal benefits and social effects .
* Risk assessment is the basis of risk management , It is one of the ways for organizations to determine information security requirements , It belongs to the planning process of the organization's information security management system
* Typical risk analysis methods : Fault tree analysis ( The process : Build fault tree 、 Find all the minimum cut sets of the fault tree 、 Calculate the probability of top event 、 Calculation of importance 、 Arrange the risk events ( Top event ) The order of )、 Failure mode impact and hazard analysis 、 Fuzzy comprehensive evaluation method 、 Delphi 、 Analytic hierarchy process 、 Event tree analysis 、 reason - Consequence analysis 、 Probabilistic risk assessment and dynamic risk probabilistic assessment
* In the process of risk assessment , Some auxiliary tools and methods can be used to collect data , Include :
questionnaire
Checklist
Personnel interview
Document checking
Vulnerability scanner
Penetration test
Draw ISMS Construction flow chart .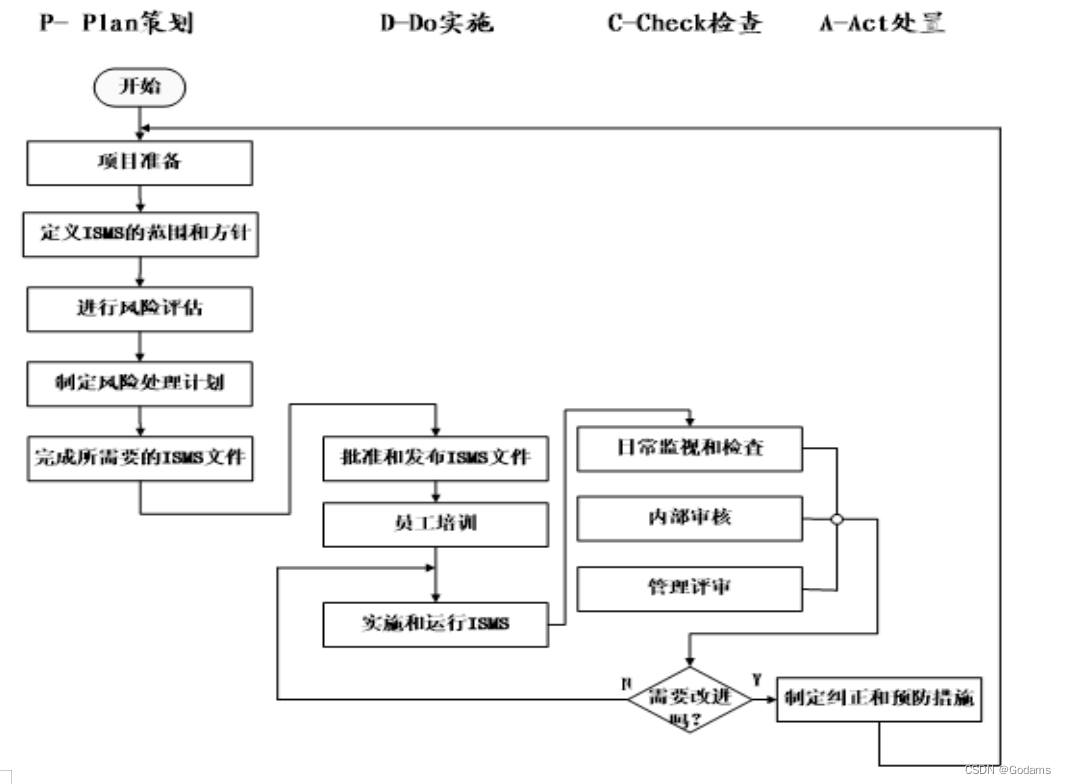
ISMS、 Class protection 、 What is the relationship between the three in risk assessment ?
ISMS The relationship between construction and risk assessment : The goal of risk assessment can be specific to specific application systems , It may also be an information system integrated by multiple application systems in an organization .
The most important purpose of risk assessment is to find security vulnerabilities for the assessed organization 、 Potential security threats , And formulate appropriate safety reinforcement measures on the basis of existing safety measures , Make the system more safe and reliable , Ensure the security of information and data .
(ISMS) It is a management system , It aims at an organization's information system , Based on risk assessment , Through risk assessment , Identify the safety risks of the organization , And then formulate a set of ISMS file , And in accordance with the PDCA Model , Experience builds ISMS、 Implementation and operation ISMS、 Monitoring and review ISMS、 Maintain and improve ISMS Wait for four cycles , To implement ISMS.
Risk assessment yes ISMS The starting point of construction , It's also ISMS The important process of the implementation process .
For an organization ,ISMS It is a process of continuous improvement and improvement , Risk assessment is just ISMS An important step in the establishment process , But risk assessment can also be self-contained , As ISMS A part of the process exists independently .
ISMS Common with grade protection : The ultimate goal is the same , It is to effectively ensure the information security of the organization
Both fully embody the idea that information security should pay attention to management , Only do a good job in safety management , Safety technology can play a full role .
Since the connection between the two is mainly reflected in management , Then the integration of the two should be mainly reflected in the safety management part and ISMS Fusion .
(1) Both can strengthen the security of information : In the information security management system (ISMS) The establishment process of e-government should be combined with the hierarchical protection of e-government , Pass the grade evaluation , Implement level protection for information system .
One side , It can practically establish an information security management system suitable for e-government , On the other hand, it can promote the implementation of e-government level protection , Even a hierarchical information security management system can be established .
(2) The safety management requirements of the two are the same
The mutual promotion and complementary relationship between the two : adopt ISMS Construction practice and grade evaluation practice , establish ISMS And the grade evaluation of information system can promote and complement each other .
ISO 17799 The control measures of include the vast majority of requirements in the safety management of hierarchical protection , and ISMS The choice of risk control measures in the implementation process , Combined with the security level requirements determined by the information system , Supplement and select from the relevant standards of grade protection ISO 17799 Control measures beyond , Therefore, it fully meets the requirements of level protection safety management .
It fully embodies the idea that information security should pay attention to management , Only do a good job in safety management , Safety technology can play a full role .
ISMS And grade protection 、 The difference between grade evaluation : The implementation basis of the two is different
The implementation subjects of the two are different :ISMS The construction subject of the system , It is mainly for enterprises and organizations to maintain their own information security , The main body of the grade evaluation is the information security evaluation and certification organization recognized by the state
The implementation objects of the two are different :ISMS The implementation object of the system , Mainly for all enterprise units , The implementation object of grade evaluation , It is mainly the party and government organs at all levels and other government departments with information system level requirements
The implementation process of the two is different : The complete implementation process of the hierarchical protection system runs through the whole life cycle of the information system 、ISMS The complete implementation process of the management system runs through the whole life cycle of the organization or a specific scope of the organization
The results of the two are different :ISMS The result of the construction is to establish a complete set of ISMS System documents of , The result of level evaluation is to give whether the evaluated object meets the requirements of the declared security level
The relationship between risk assessment and level protection : The idea of system classification and classification in level protection is basically consistent with the importance classification of information assets in risk assessment .
In risk assessment , High value information assets do not necessarily have high risk levels .
After determining the system security level , The results of risk assessment can be used as the implementation of level protection 、 The starting point and reference of grade safety construction .
Risk assessment is classified protection ( Different levels and different safety requirements ) Starting point .
The final risk level in the risk assessment comprehensively considers the importance of information 、 The effectiveness of the existing safety control measures of the system and the comprehensive evaluation results after the operation status , High level information systems in level protection do not necessarily have high-level security risks .
What is included in establishing information security management policies ?
Basic principles of information security laws and regulations ?
The principle of who is in charge and who is responsible 、 The principle of highlighting the key points 、 The principle of prevention first 、 Principles of safety audit 、 Principles of risk management
《 Regulations of the people's Republic of China on the security protection of computer systems 》 What is the main content ?
link
The security management of information system involves two aspects of information system .
The security management of information system can be divided into technical management and legal management .
Technical management is based on OSI The management of security mechanism and security services, as well as the technical monitoring of the physical environment
SMIB, Safety management information base , Distributed storage related information .
Legal management focuses on the management of compliance with laws and regulations .
* The role of information security laws and regulations :(1) The safeguard role : The legal norms of information security provide law enforcement agencies with the right to drive 、 Provide legal basis and legal guarantee for performing duties ;
(2) Normative function : Information security legal norms are the code of conduct and evaluation standard for people to maintain information security and national security ;
(3) Disciplinary effect : There are many prohibitive laws and regulations in information security laws and regulations .
* Classification of information security laws and regulations :(1) Classified by architecture
By architecture , Information security legal norms can be divided into legal systems ( Department law system ) class 、 Regulatory system ( The policy system ) class .
(2) Classified by issuing agency
Press release institution , The legal norms of information security can be divided into : National 、 Local 、 International and so on .
* The concept of legislation : Certain state organs shall, in accordance with their statutory functions and powers and procedures , To develop 、 Activities to amend and repeal laws and other normative legal documents and recognize laws , It is an activity that raises the will of a certain class to the will of the state , It's about social resources 、 The first distribution of social interests
The legislative procedure of our country mainly includes the following four steps : Put forward legal proposals 、 Deliberate on legislative bills 、 Vote on legislative bills 、 Publish laws
* The concept of justice : It refers to the national judicial organ and its judicial personnel in accordance with legal functions and powers and legal procedures , The specific activities of using the law to deal with cases .
* The concept of law enforcement : Law enforcement , It refers to the state administrative organs in accordance with the statutory functions and powers and legal procedures , Exercise administrative authority 、 To perform one's duties 、 Activities to implement and enforce laws .
Characteristics of law enforcement :
(1) Law enforcement is the overall management of social life in the name of the state , It has national authority .
(2) The main body of law enforcement is public officials of state administrative organs .
(3) Law enforcement is mandatory by the state , The process of implementing laws by administrative organs is also the process of exercising law enforcement power , The administrative organ manages the society according to the authorization of the law , A certain administrative organ is the premise of effective management .
(4) Law enforcement is proactive and unilateral .
The principle of law enforcement : Administer according to law 、 fair and reasonable
What fields does the connotation of information security extend from traditional fields ?
Information security connotation expansion From the perspective of confidentiality 、 integrity 、 can ⽤ Sex extends to confidentiality 、 integrity 、 can ⽤ sex 、 Authenticity 、 Non repudiation 、
reliability 、 Controllability
Current situation of domestic information security management ?
present situation : China has initially established a national information security organization guarantee system , Put forward “ Active defense 、 Comprehensive prevention ” The policy of
(1) Set and introduced a number of important information security management standards
(2) We have formulated a series of necessary laws and regulations for information security management :《 Electronic signature law 》、《 Network security law 》、《 Cryptology 》
(3) Information security risk assessment has been paid attention to and carried out
problem :(1) The current situation of information security management is chaotic , Lack of an overall strategy at the national level , The actual management is insufficient , Policy implementation and supervision are not enough .
(2) With Chinese characteristics 、 Dynamic and inclusive organization 、 file 、 Control measures 、 The information security management system of operational processes and procedures and related resources has not been established .
(3) The information security risk assessment standard system with Chinese characteristics needs to be improved , The need for information security is difficult to determine , Lack of system 、 Comprehensive information security risk assessment and evaluation system and comprehensive 、 Perfect information security guarantee system .
(4) Lack of information security awareness , Heavy products are widespread 、 Light service , Heavy technology 、 Light management thought .
(5) Insufficient special funds , Management talents are extremely scarce , Basic theoretical research and key technologies are weak , Rely heavily on foreign countries .
(6) Insufficient technological innovation , The level and quality of information security management products are not high .
(7) stay 20 century 90 S before , Information security mainly depends on security technology and unsystematic management regulations . International information security management has entered the era of standardization and systematic management .
Information security management The management subject is an organization , Country 、 Companies can ;
Management subject 5 Requirements : people 、 goods 、 matter 、 Information 、 space-time ;
Management means 5 In terms of : mandatory 、 In exchange for 、 punishment 、 incentive 、 Communication and persuasion ;
Management process 7 A link : Determination of management rules , Manage the allocation of resources , The establishment and decomposition of goals , Organization and implementation , process control , Effect evaluation , Summary and treatment .
Guiding principles of information security management Strategic principles : Is the basic principle of considering information security
Engineering principles : For the organization and implementation of information security engineering , Basic principles to follow
边栏推荐
- 来了!GaussDB(for Cassandra)新特性亮相
- 简单几步教你如何看k线图图解
- Multimodal point cloud fusion and visual location based on image and laser
- [Blue Bridge Cup training 100 questions] sort scratch from small to large. Blue Bridge Cup scratch competition special prediction programming question centralized training simulation exercise question
- IP netns command (memo)
- 伺服力矩控制模式下的力矩目标值(fTorque)计算
- SQLite SQL exception near "with": syntax error
- Basic concepts and properties of binary tree
- Redis
- Redis publishing and subscription
猜你喜欢
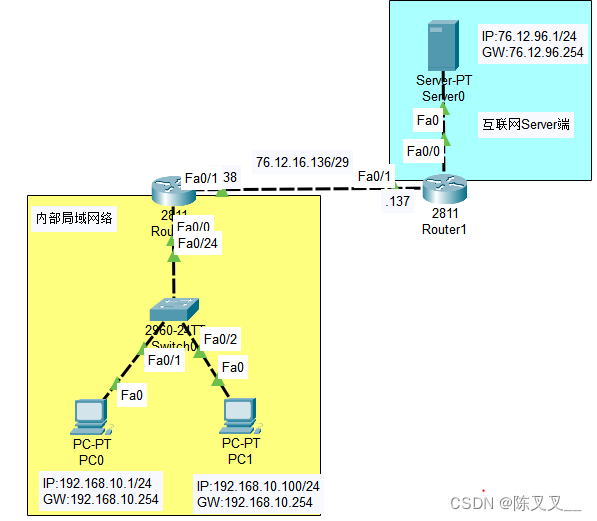
Simple configuration of single arm routing and layer 3 switching
10 schemes to ensure interface data security
![Interview vipshop internship testing post, Tiktok internship testing post [true submission]](/img/69/b27255c303150430df467ff3b5cd08.gif)
Interview vipshop internship testing post, Tiktok internship testing post [true submission]
Static routing configuration

Differences between rip and OSPF and configuration commands
Thread pool and singleton mode and file operation
NAT地址转换
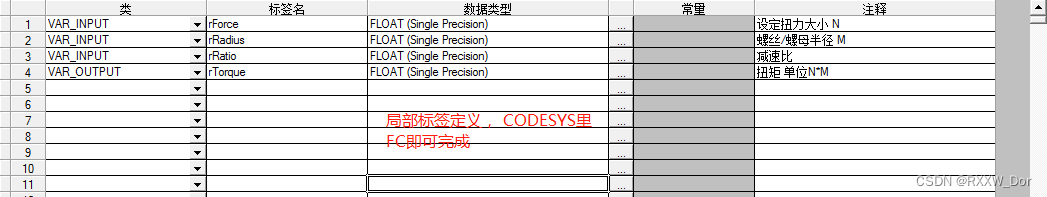
Calculation of torque target value (ftorque) in servo torque control mode
![Kirk borne's selection of learning resources this week [click the title to download directly]](/img/df/98aa3edf0a70b870684963d52e7c72.png)
Kirk borne's selection of learning resources this week [click the title to download directly]
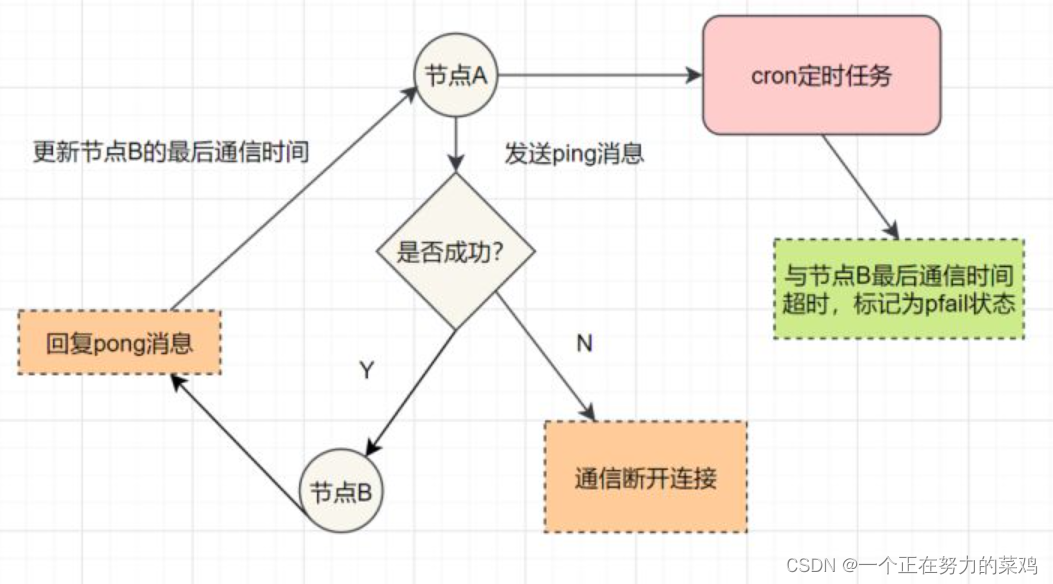
Redis集群与扩展
随机推荐
Redis cluster and expansion
Usage of PHP interview questions foreach ($arr as $value) and foreach ($arr as $value)
Flipping Game(枚举)
Nat address translation
高温火烧浑不怕,钟薛高想留清白在人间
DataSimba推出微信小程序,DataNuza接受全场景考验? | StartDT Hackathon
The moveposition function of rigidbody2d of unity2d solves the problem of people or screen jitter when moving
ip netns 命令(备忘)
[Tawang methodology] Tawang 3W consumption strategy - U & a research method
Learn open62541 -- [67] add custom enum and display name
Yunjing network technology interview question [Hangzhou multi tester] [Hangzhou multi tester _ Wang Sir]
PIP related commands
强化学习-学习笔记8 | Q-learning
Basic concepts and properties of binary tree
unity2d的Rigidbody2D的MovePosition函数移动时人物或屏幕抖动问题解决
10 schemes to ensure interface data security
What is the general yield of financial products in 2022?
Will domestic software testing be biased
The highest level of anonymity in C language
The live broadcast reservation channel is open! Unlock the secret of fast launching of audio and video applications