当前位置:网站首页>[pointer] delete all spaces in the string s
[pointer] delete all spaces in the string s
2022-07-06 14:35:00 【|Light|】
requirement
Make up a function , Delete string s All spaces in .( Use a pointer to achieve )
Code
/* This function is used to delete all spaces in the string a Is a pointer to a string array */
char *delete_space(char *a)
{
int n = strlen(a);
int i=0,j=0,k=0;
char b[n];
for(i=0;i<n;i++)
{
if(a[i]==' ')
{
k++;
continue;
}
else
{
b[j]=a[i];
j++;
a[i]='\0';
}
}
for(j=0;j<n-k;j++)
{
a[j]=b[j];
}
return a;
}
main function
int main()
{
char a[200];
gets(a);
delete_space(a);
puts(a);
return 0;
}
test
Test input
I A m A Student
Output
IAmAStudent
边栏推荐
猜你喜欢
《统计学》第八版贾俊平第五章概率与概率分布
MySQL中什么是索引?常用的索引有哪些种类?索引在什么情况下会失效?

Résumé des points de connaissance et des réponses aux exercices après la classe du chapitre 7 de Jia junping dans la huitième édition des statistiques
《统计学》第八版贾俊平第六章统计量及抽样分布知识点总结及课后习题答案
On the idea of vulnerability discovery
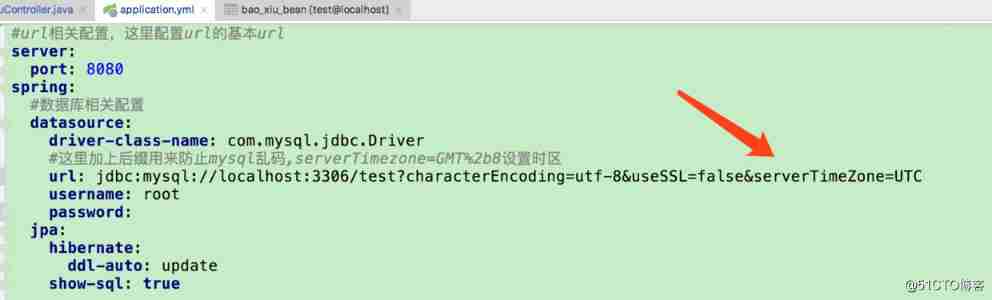
Solutions to common problems in database development such as MySQL
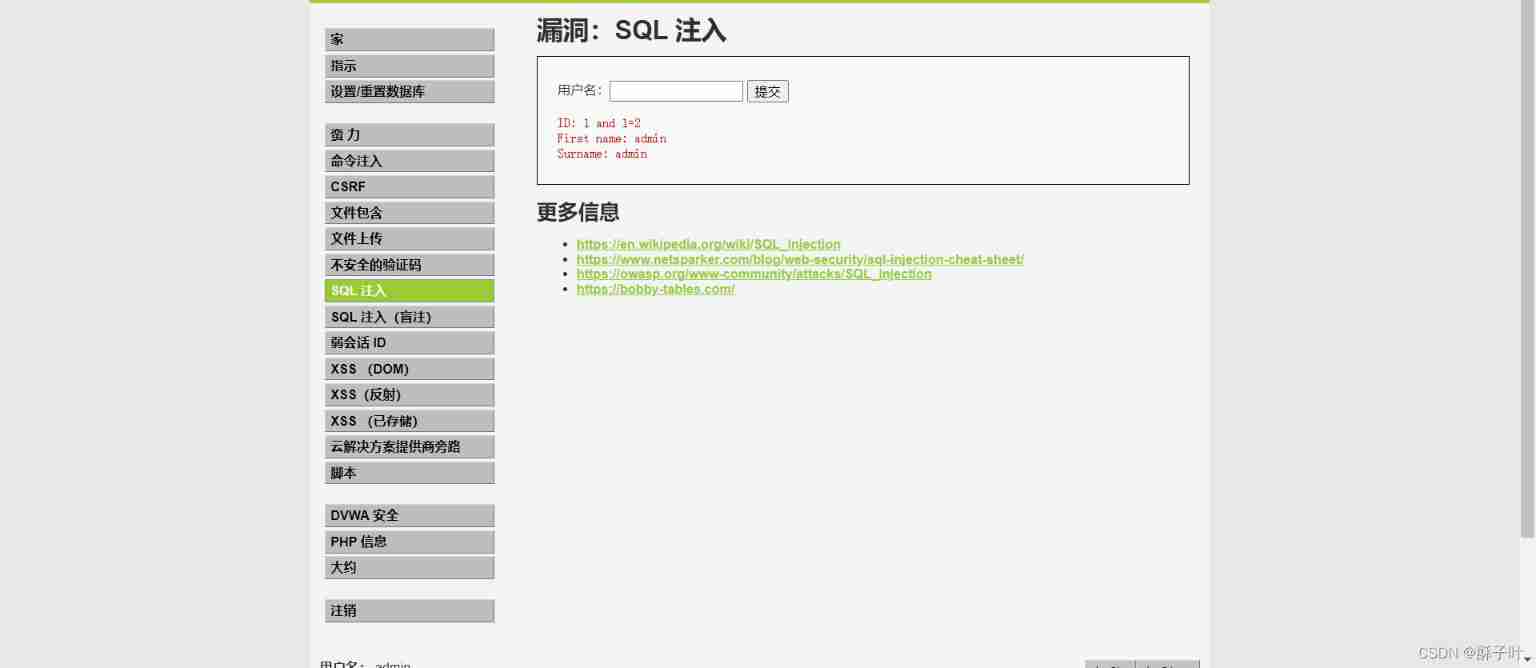
DVWA (5th week)
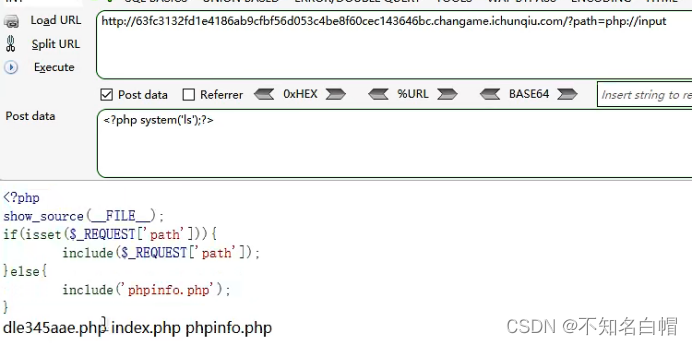
Web vulnerability - File Inclusion Vulnerability of file operation

Statistics 8th Edition Jia Junping Chapter 7 Summary of knowledge points and answers to exercises after class
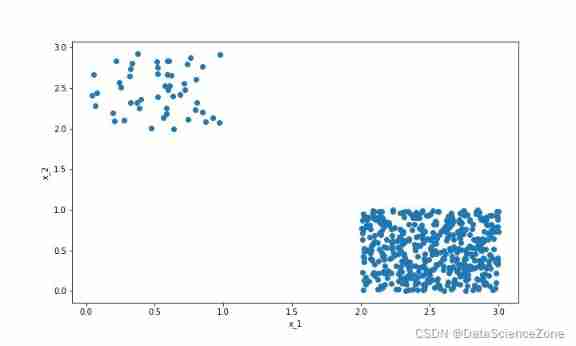
Data mining - a discussion on sample imbalance in classification problems
随机推荐
MySQL learning notes (stage 1)
Résumé des points de connaissance et des réponses aux exercices après la classe du chapitre 7 de Jia junping dans la huitième édition des statistiques
. Net6: develop modern 3D industrial software based on WPF (2)
Xray and Burp linked Mining
Mysql的事务是什么?什么是脏读,什么是幻读?不可重复读?
【指针】求字符串的长度
Intranet information collection of Intranet penetration (5)
我的第一篇博客
数字电路基础(四) 数据分配器、数据选择器和数值比较器
“人生若只如初见”——RISC-V
Uibutton status exploration and customization
Matplotlib绘图快速入门
Captcha killer verification code identification plug-in
内网渗透之内网信息收集(二)
关于超星脚本出现乱码问题
数字电路基础(三)编码器和译码器
What language should I learn from zero foundation. Suggestions
Load balancing ribbon of microservices
攻防世界MISC练习区(gif 掀桌子 ext3 )
浙大版《C语言程序设计实验与习题指导(第3版)》题目集