当前位置:网站首页>Leetcode skimming: binary tree 20 (search in binary search tree)
Leetcode skimming: binary tree 20 (search in binary search tree)
2022-07-07 12:47:00 【Taotao can't learn English】
700. Search in binary search tree
Given a binary search tree (BST) And a value . You need to BST Found a node whose value is equal to the given value . Return the subtree with this node as the root . If the node doesn't exist , Then return to NULL.
for example ,
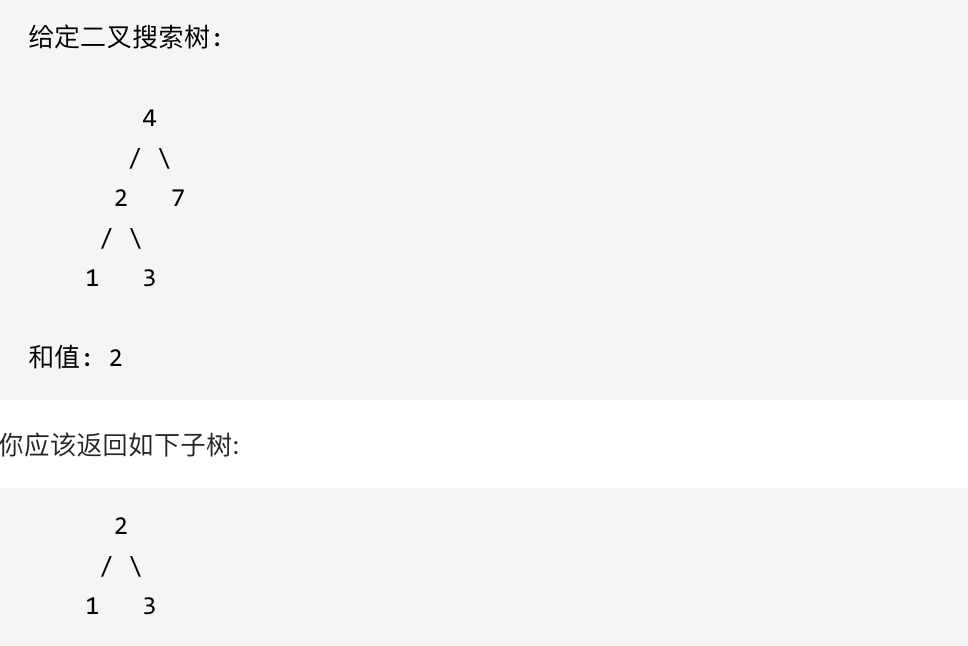
In the example above , If the value is 5, But because no node has a value of 5, We should go back to NULL.
A very simple question . recursive , When the current node is empty , Returns an empty , The current node is larger than the target number , Check the left subtree , Otherwise, check the right subtree , If equal , Then return to . Because binary search tree is non decreasing . Orderly , The idea of dichotomy .
package com.programmercarl.tree;
/** * @ClassName SearchBST * @Descriotion TODO * @Author nitaotao * @Date 2022/7/5 21:17 * @Version 1.0 * https://leetcode.cn/problems/search-in-a-binary-search-tree/ * 700. Search in binary search tree **/
public class SearchBST {
/** * BST, Also called balanced binary tree , It is a binary tree accessed by key , * And it is required to keep the order , That is, any node is not less than its left offspring , Not greater than its right offspring ( Note that offspring , It's not a child ). * BST The order of the ergodic sequence must be monotonic and non descending . * * @param root * @param val * @return */
public TreeNode searchBST(TreeNode root, int val) {
if (root == null) {
return null;
}
if (root.val == val) {
return root;
} else if (root.val < val) {
// The current value is smaller than the target value , Search on the right subtree
return searchBST(root.right, val);
} else {
// The current value is larger than the target value , Search on the left sub tree
return searchBST(root.left, val);
}
}
}
边栏推荐
- 通讯协议设计与实现
- IPv6 experiment
- [deep learning] image multi label classification task, Baidu paddleclas
- 对话PPIO联合创始人王闻宇:整合边缘算力资源,开拓更多音视频服务场景
- 编译 libssl 报错
- OSPF exercise Report
- ICLR 2022 | pre training language model based on anti self attention mechanism
- BGP actual network configuration
- visual stdio 2017关于opencv4.1的环境配置
- idm服务器响应显示您没有权限下载解决教程
猜你喜欢
visual stdio 2017关于opencv4.1的环境配置
opencv的四个函数

The left-hand side of an assignment expression may not be an optional property access.ts(2779)
ps链接图层的使用方法和快捷键,ps图层链接怎么做的
【深度学习】图像多标签分类任务,百度PaddleClas

爱可可AI前沿推介(7.7)

Master formula. (used to calculate the time complexity of recursion.)
【PyTorch实战】图像描述——让神经网络看图讲故事

普乐蛙小型5d电影设备|5d电影动感电影体验馆|VR景区影院设备
Static comprehensive experiment
随机推荐
Ctfhub -web SSRF summary (excluding fastcgi and redI) super detailed
【统计学习方法】学习笔记——逻辑斯谛回归和最大熵模型
How much does it cost to develop a small program mall?
用mysql查询某字段是否有索引
[crawler] avoid script detection when using selenium
layer弹出层的关闭问题
OSPF exercise Report
Vxlan 静态集中网关
About web content security policy directive some test cases specified through meta elements
The left-hand side of an assignment expression may not be an optional property access.ts(2779)
Guangzhou held work safety conference
@Resource和@Autowired的区别?
Cryptography series: detailed explanation of online certificate status protocol OCSP
对话PPIO联合创始人王闻宇:整合边缘算力资源,开拓更多音视频服务场景
Day-17 connection set
What if does not match your user account appears when submitting the code?
Attack and defense world - PWN learning notes
Cookie
HZOJ #240. 图形打印四
leetcode刷题:二叉树26(二叉搜索树中的插入操作)