当前位置:网站首页>Hashlimit rate control
Hashlimit rate control
2022-07-06 04:12:00 【redwingz】
iptables Extended match hashlimit stay hashlimit-mode When specified as null , Equate to limit matching . as follows hashlimit The limit is no more than 50 A message .
# iptables -A INPUT -p udp -j RATE-LIMIT
# iptables --new-chain RATE-LIMIT
# iptables --append RATE-LIMIT \
--match hashlimit \
--hashlimit-upto 50/sec \
--hashlimit-burst 20 \
--hashlimit-name conn_rate_limit \
--jump ACCEPT
# iptables --append RATE-LIMIT --jump DROP
#
# iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
RATE-LIMIT udp -- 0.0.0.0/0 0.0.0.0/0
Chain RATE-LIMIT (1 references)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 limit: up to 50/sec burst 20
DROP all -- 0.0.0.0/0 0.0.0.0/0
according to hashlimit-name Create the following PROC file , Because it's not specified hashlimit-mode, Source IP、 Purpose IP And source port 、 The destination port fields are all zero :
$ cat /proc/net/ipt_hashlimit/conn_rate_limit
0 0.0.0.0:0->0.0.0.0:0 54975581200000 54975581200000 2748779060000
Equivalent functions are provided by limit Match implementation , as follows , The limit is no more than 50 A message .
# iptables --flush
# iptables -A INPUT -p udp -j RATE-LIMIT
# iptables --new-chain RATE-LIMIT
# iptables -A RATE-LIMIT -m limit --limit 50/sec --limit-burst 20 -j ACCEPT
# iptables --append RATE-LIMIT --jump DROP
Message limit
Use hashlimit-mode Parameter assignment srcip, By source IP Address , Each one IP The rate of is limited to every minute 5 A message , The timeout length of hash table entries is 30 Second .
# iptables -I INPUT -p icmp -m hashlimit --hashlimit-name icmp-limit \
--hashlimit-mode srcip --hashlimit-srcmask 32 \
--hashlimit-above 5/minute --hashlimit-burst 2 \
--hashlimit-htable-expire 30000 -j DROP
adopt PROC file icmp-limit View hash table entries .
$ cat /proc/net/ipt_hashlimit/icmp-limit
29 192.168.1.114:0->0.0.0.0:0 804842551180032 3298534872000000 1649267436000000
29 192.168.1.117:0->0.0.0.0:0 748217702349568 3298534872000000 1649267436000000
Use dstip Pattern , Restrict access to each purpose IP The number of messages of the address is per minute 5 individual .
# iptables -I INPUT -p icmp -m hashlimit --hashlimit-name icmp-limit \
--hashlimit-mode dstip --hashlimit-srcmask 32 \
--hashlimit-above 5/minute --hashlimit-burst 2 \
--hashlimit-htable-expire 30000 -j DROP
adopt PROC file icmp-limit View hash table entries .
$ cat /proc/net/ipt_hashlimit/icmp-limit
27 0.0.0.0:0->192.168.9.133:0 675649895268352 3298534872000000 1649267436000000
Flow limit
Limit each source as follows IP The traffic of the address is per second 256kbit.
# iptables -I INPUT -p icmp -m hashlimit --hashlimit-name icmp-traffic-limit \
--hashlimit-mode srcip --hashlimit-srcmask 32 \
--hashlimit-above 256kb/s --hashlimit-burst 500kb \
--hashlimit-htable-expire 30000 -j DROP
adopt PROC file icmp-traffic-limit View hash table entries .
$ cat /proc/net/ipt_hashlimit/icmp-traffic-limit
29 192.168.9.1:0->0.0.0.0:0 4194304000 2 255984
Session traffic limit
Based on quintuples (icmp,srcip,dstip,srcport,dstport) Flow control .
# iptables -I INPUT -p icmp -m hashlimit --hashlimit-name icmp-session-limit \
--hashlimit-mode srcip,dstip,srcport,dstport \
--hashlimit-above 256kb/s --hashlimit-burst 512kb \
--hashlimit-htable-expire 30000 -j DROP
adopt PROC file icmp-session-limit View hash table entries ,ICMP No port number .
$ cat /proc/net/ipt_hashlimit/icmp-session-limit
29 192.168.9.1:0->192.168.9.133:0 4194304000 2 255984
边栏推荐
- AcWing 243. A simple integer problem 2 (tree array interval modification interval query)
- Cross domain and jsonp details
- Python book learning notes - Chapter 09 section 01 create and use classes
- Network security - Security Service Engineer - detailed summary of skill manual (it is recommended to learn and collect)
- About some basic DP -- those things about coins (the basic introduction of DP)
- [disassembly] a visual air fryer. By the way, analyze the internal circuit
- pd. to_ numeric
- Facebook and other large companies have leaked more than one billion user data, and it is time to pay attention to did
- 图应用详解
- Determine which week of the month the day is
猜你喜欢
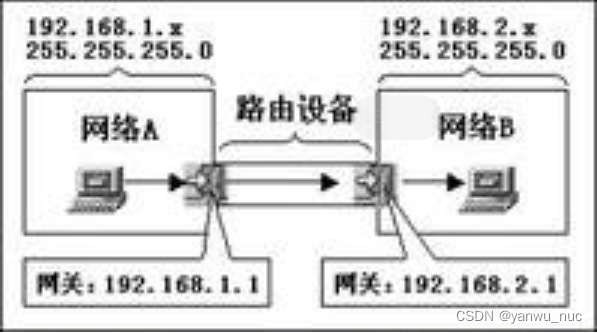
What is the difference between gateway address and IP address in tcp/ip protocol?
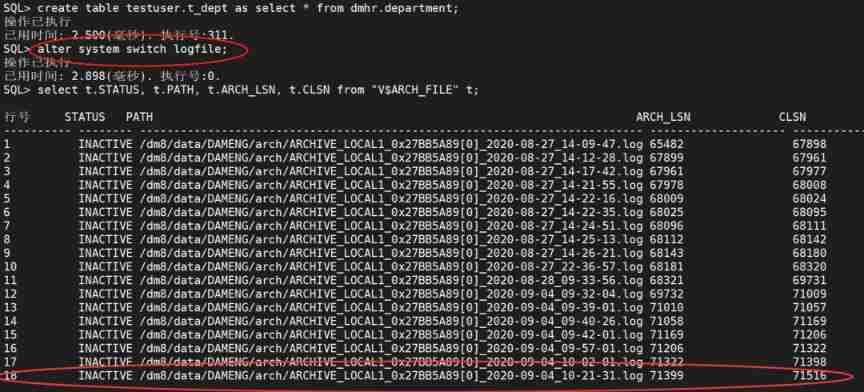
DM8 archive log file manual switching
About some basic DP -- those things about coins (the basic introduction of DP)
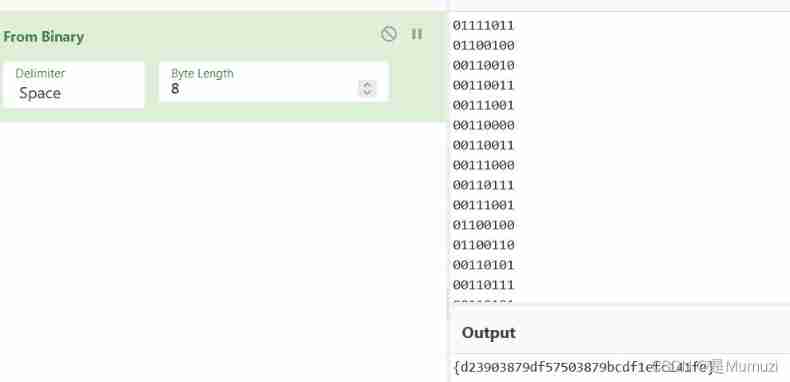
VNCTF2022 WriteUp
【按键消抖】基于FPGA的按键消抖模块开发

About some basic DP -- those things about coins (the basic introduction of DP)
10个 Istio 流量管理 最常用的例子,你知道几个?
Basic knowledge of binary tree, BFC, DFS
Figure application details
1291_Xshell日志中增加时间戳的功能
随机推荐
1291_Xshell日志中增加时间戳的功能
P2022 有趣的数(二分&数位dp)
The Research Report "2022 RPA supplier strength matrix analysis of China's banking industry" was officially launched
20、 EEPROM memory (AT24C02) (similar to AD)
[FPGA tutorial case 11] design and implementation of divider based on vivado core
Le compte racine de la base de données MySQL ne peut pas se connecter à distance à la solution
User datagram protocol UDP
Custom event of C (31)
【PSO】基于PSO粒子群优化的物料点货物运输成本最低值计算matlab仿真,包括运输费用、代理人转换费用、运输方式转化费用和时间惩罚费用
Solution to the problem that the root account of MySQL database cannot be logged in remotely
MySQL about self growth
Basic knowledge of binary tree, BFC, DFS
Stc8h development (XII): I2C drive AT24C08, at24c32 series EEPROM storage
关于进程、线程、协程、同步、异步、阻塞、非阻塞、并发、并行、串行的理解
Global and Chinese markets for fire resistant conveyor belts 2022-2028: Research Report on technology, participants, trends, market size and share
图应用详解
Web components series (VII) -- life cycle of custom components
判断当天是当月的第几周
Execution order of scripts bound to game objects
How to solve the problem of slow downloading from foreign NPM official servers—— Teach you two ways to switch to Taobao NPM image server