当前位置:网站首页>With 27K successful entry ByteDance, this "software testing interview notes" has benefited me for life
With 27K successful entry ByteDance, this "software testing interview notes" has benefited me for life
2022-07-06 14:43:00 【Programming simplicity】
My friend has been on the job for two weeks , The overall working environment was very satisfactory ! So I took the time to write this interview question for me , And I share it with my friends , interview & Entry experience !
Probably in 5 In the middle of the month, he told me that he submitted his resume ,7 The month passed 3 The round of interview yielded Offer, At that time, I also referred to the face experience of the big guys on many Niuke websites . Got it 27K
Today, I'd like to share with you all the questions I might ask .
Besides, the interview questions here , I can share it with you , In order not to affect everyone to watch , I put down the article at the end !
Personal information
Self introduction. project ( important )
The biggest challenge in the project , Projects that take the longest , Something with a sense of achievement
The most impressive of the project bug
What do you want to ask
Suitable for business testing or technical testing
Why choose bytes
Use them separately 3 Two words describe your strengths and weaknesses
test
Understanding of test development , Why do you want to do test development , Understanding of test opening
Classification of software
What is interface testing
Test case of wechat red envelope
Test case of wechat comment function
Test the Alipay payment code. , Design test cases
Black box test method
White box test method
Software testing process
How to design test cases for login function ?
How is online bank transfer measured , Design test cases .
Give you a website , How should you test ?
A paper cup with an advertisement , Please design test cases ?
Imagine a login box , Include ID、 password 、 Sign in 、 Cancel , Remember the password ( Check box ), Write out the test points you think of as much as possible ?
Test case of Taobao shopping cart
Design a test case for tiktok video.
Design tiktok app User login test
Interrupt test
Test in one scenario , Recommended filter
Friends circle praise comment test cases
Situation issues
If you tiktok, many users in a region can't download video.
If the user receives a short message from the bank, it indicates that the deduction has been successful , But the merchant did not receive the money , What do you think is the problem
Enter a url, What happened ?
How to implement a user login function
High parallel delivery reduces the performance consumption caused by transactions ?
If one API There is an unstable interface bug, How to determine ?
If you submit bug, Development tells you it doesn't exist , How to deal with it ?
Reasons for slow loading of access pages and how to solve them
How do you disagree with your leader , What would you do
If the picture upload fails , The analysis reason
For comment function , How do you design interfaces , The main answer is what parameters need to be passed ?
app Why is the page white
Full link voltage measurement , A server was found CPU Load rate 100%, Disk and memory usage is normal , How would you analyze the possible causes
Design a system for buying train tickets , Enter the departure and arrival stations , Returns all possible results
What happened after adding the cart request
Reasons for payment failure of Taobao users
If you have a lot of puzzles in the software testing industry , So welcome to communicate and discuss with me in the communication group in the industry . There are free tutorial materials and testing resources at all stages in the group , I hope it can help you break through the bottleneck
Python Basics
python Memory pool mechanism
python The difference between arrays and lists
python Which bags do you often use , Standard library
The difference between process oriented and object-oriented languages
Reflection
python Data structure of
dict and list The underlying implementation of
python Decorator , effect , usage
Compiled and interpreted languages The advantages of interpretive language
Garbage collection mechanism
GIL lock
is and ==
__new__ and __init__ difference
use python Write multithreading , Loop printing 123
operating system
Read-write lock , Difference , Application scenarios
What's the difference between threads and processes
What is a deadlock , Conditions for Deadlock
How to prevent deadlock ,! Avoid deadlock , Check for deadlock occurrence
What is the difference between heap and stack and storage mode
Memory leaks and overflows
Multithreading and multiprocessing , And application scenarios
Process communication mode
How to implement multithreading
Ways of computer memory management
Process scheduling method
What is? Linux User mode and kernel mode
State of process , What is the difference between a process state ready and a waiting state
What is virtual memory for
Thread pool
How to realize thread safety
Context switching between processes and threads
coroutines
computer network
TCP Three handshakes , The process of waving four times
Why should the client be in TIME_WAIT Status wait for a period of time
CLOSING state
If server The client did not receive the third time ack, But yes client Data sent by the end ,server What will the end do
Let me talk about it. get and post
http Status code
TCP and UDP
once HTTP Process of request ( Input URL The whole process from to return )
http and https
Stateless and connectionless
OSI Seven layer model , What are the protocols at each layer
HTTP agreement Request message structure
TCP How to ensure reliable transmission , What should I do if I lose my bag
Let's talk about sliding windows
TCP Three handshakes SYN and ACK What's the difference between bags , What does it contain
UDP How do you want to be reliable RUDP
Semi connected attack
TCP Sticking and unpacking
cookie and session What is it? , Why use cookie and session
DNS Agreement and role
DNS Query mode of
ARP The role of the agreement 、 Operation mode
What is the maximum Ethernet packet size
Is there a security problem during the three handshakes ? Describe what security problems exist ? How to defend against such security problems ?
web attack ,CSRF attack
TCP How to control congestion ? How does congestion control judge congestion ?
TCP How to judge the loss of fast retransmission ?
https Where are the certificates stored
Long and short connections and their respective scenarios
database
sql sentence Within one month id grouping Take the name of the youngest student in each class in a grade The score sheet outputs the top three scores , What about the last three Copy A Table data to B surface Query that each account is greater than 80 The student's name Filter out records per hour Investigate where Look at aggregate functions where and having The difference between A database sql Number of query duplicates Failed to check the average score in the student transcript ( lower than 60) Of the students id And average score Query the name of the person with the highest total score user Users logged in three times in a time period in the table id limit Usage of
Database engines and their differences InnoDB MyISAM MEMORY:
mysql How do I query my logs
( many times ) The reason for the slow query speed , How to solve
What are the transactions of the database ? How do you use it?
Primary key 、 Foreign keys 、 The respective meanings and differences of indexes
The nature of transactions (ACID), Tell me what each feature means
Type of index
What is a clustered index 、 What is a nonclustered index
What is the data structure of the index
Prefix index
MySQL/MongoDb Port number
There are several forms of connection between tables in a database ( Left connection , The right connection , Internal connection , Complete connection )
say something redis Data structure and application scenario in
Three paradigms
Database isolation level
Why use b+ Tree index instead of hash
Linux
Common command Check the process ps View all process long formats ps -ef Print current folder file ls -al a All the files l Details Soft link ln -s a target Hard links ln Create directory mkdir Modify the permissions chmod see file : Moving files mv You can also rename Copy file cp Delete file rm -r Recursive delete -f Delete read-only file wildcard ? Single character ,* Multiple characters ,[a-z] Character set grep Regular search According to the line Numbers -n Number of queries -c Reverse election -v View the specified process ps -ef | grep pid View command history history View disk space df -hl View file size du Find files find [ Catalog ] Find by name -name “h*” With h start terminate a process kill -9 pid
How to prevent new people from misoperation rm -rf
Found process number 199 The process of ls -ef|grep 199
Number of lines with keywords in a file grep -c "key" ./file
In this directory .log The ending file contains keywords a But does not contain keywords b The number of rows grep "a" ./file | grep -cv "b"
Intelligence questions
A gold bar , I need to be paid every day for a week , Cut twice , How do I cut it Cut the gold bar into 1/7, 2/7, 4/7, Change every day
100 Two football teams competed in pairs for a champion team , How many games will you play at least Eliminate one team per game , So we need to 99 game 25 horse 5 Track (s) , Top three
100 A bean , Five prisoners , The most or least beans taken will be executed , Whose survival probability is higher
The above information , It should be very helpful for friends who want to test advanced , You can click on the business card below to communicate for free .
边栏推荐
- Wang Shuang's detailed learning notes of assembly language II: registers
- 移植蜂鸟E203内核至达芬奇pro35T【集创芯来RISC-V杯】(一)
- Statistics, 8th Edition, Jia Junping, Chapter VIII, summary of knowledge points of hypothesis test and answers to exercises after class
- Function: find the maximum common divisor and the minimum common multiple of two positive numbers
- Fundamentals of digital circuit (IV) data distributor, data selector and numerical comparator
- Statistics 8th Edition Jia Junping Chapter 10 summary of knowledge points of analysis of variance and answers to exercises after class
- 《统计学》第八版贾俊平第十二章多元线性回归知识点总结及课后习题答案
- Statistics 8th Edition Jia Junping Chapter 5 probability and probability distribution
- Circular queue (C language)
- Statistics, 8th Edition, Jia Junping, Chapter 6 Summary of knowledge points of statistics and sampling distribution and answers to exercises after class
猜你喜欢
《统计学》第八版贾俊平第十三章时间序列分析和预测知识点总结及课后习题答案
图书管理系统
内网渗透之内网信息收集(三)

Intranet information collection of Intranet penetration (3)
Statistics, 8th Edition, Jia Junping, Chapter 11 summary of knowledge points of univariate linear regression and answers to exercises after class
Attack and defense world misc practice area (GIF lift table ext3)
Fundamentals of digital circuits (I) number system and code system
![Transplant hummingbird e203 core to Da Vinci pro35t [Jichuang xinlai risc-v Cup] (I)](/img/85/d6b196f22b60ad5003f73eb8d8a908.png)
Transplant hummingbird e203 core to Da Vinci pro35t [Jichuang xinlai risc-v Cup] (I)

Apache APIs IX has the risk of rewriting the x-real-ip header (cve-2022-24112)
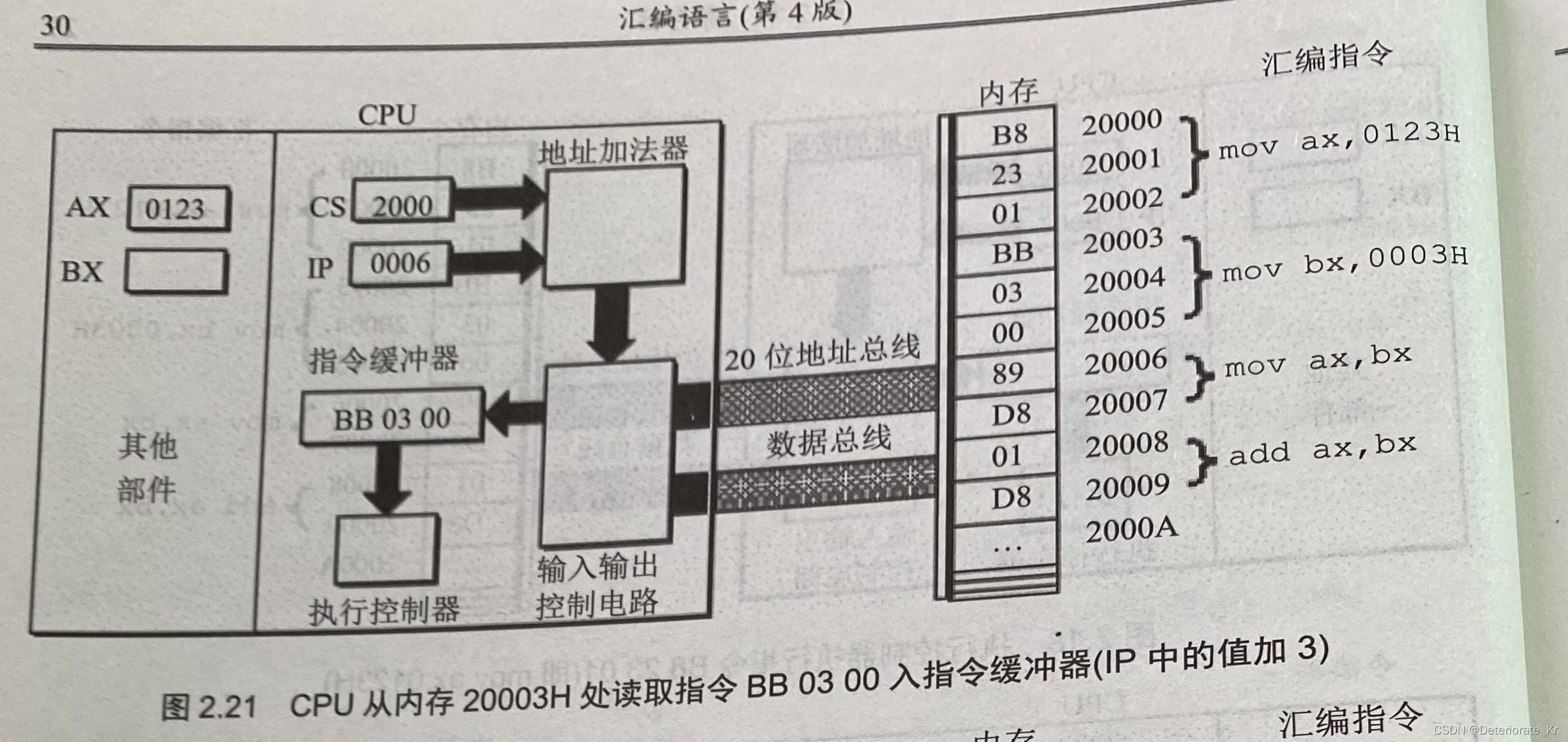
Wang Shuang's detailed learning notes of assembly language II: registers
随机推荐
《统计学》第八版贾俊平第三章课后习题及答案总结
Binary search tree concept
函数:求1-1/2+1/3-1/4+1/5-1/6+1/7-…+1/n
Pointeurs: maximum, minimum et moyenne
[issue 18] share a Netease go experience
XSS (cross site scripting attack) for security interview
[pointer] octal to decimal
Statistics 8th Edition Jia Junping Chapter 5 probability and probability distribution
Statistics, 8th Edition, Jia Junping, Chapter 6 Summary of knowledge points of statistics and sampling distribution and answers to exercises after class
servlet中 servlet context与 session与 request三个对象的常用方法和存放数据的作用域。
Feature extraction and detection 14 plane object recognition
Fundamentals of digital circuit (IV) data distributor, data selector and numerical comparator
【指针】查找最大的字符串
Intranet information collection of Intranet penetration (3)
Fundamentals of digital circuits (II) logic algebra
How does SQLite count the data that meets another condition under the data that has been classified once
数据库多表链接的查询方式
1.支付系统
循环队列(C语言)
【指针】删除字符串s中的所有空格