当前位置:网站首页>Every API has its foundation when a building rises from the ground
Every API has its foundation when a building rises from the ground
2022-07-06 06:44:00 【Alibaba cloud developers】
brief introduction :6 month 30 On the afternoon of Sunday , Alibaba cloud WAF The product will be upgraded to 3.0 edition , Among them, it is aimed at the safety guarantee work during important festivals or large-scale activities , A special protective package for heavy maintenance scenarios will be released , Combine with basic product capabilities , Form a set of tens of millions IP The blacklist 、 One click regional ban 、 Scenario rules are automatically updated to effectively protect against new vulnerabilities , Open at the same time API The capability will help realize the integrated solution of automatic operation and maintenance .
Click to learn more about Alibaba cloud Web Application firewall 3.0 Release


Improper configuration , The internal interface is exposed
The code logic is flawed , Inadequate certification
The data reveal that ……
API Why is safety more and more important ?
API, Some applications call each other for convenience , Pre defined interfaces in the development process , For example, when you visit a shopping platform through wechat applet , The applet needs to pass API To connect the inventory of the mall 、 Order and other systems .
In the past, digital business was not rich , For an organization , Inside API The frequency of development and invocation is low , Less interaction with external systems and Applications , therefore API It's just complicated IT A trivial existence in the system , Its security is less concerned .
But now , More and more businesses have moved online , For organizations , Providing services on the Internet requires calling more external interfaces , Between different enterprise organizations API Mutual calls inevitably result in API Increased exposure ,API Safety is becoming more and more important .
The core risk caused by these risks is The data reveal that , With 《 Data security law 》、《 Personal information protection law 》 Have been introduced and formally implemented ,API As a core element in dealing with data, it needs to be focused .
Enterprises should do well API Where is the difficulty of safety ?
API One of the characteristics of is the business logic of the enterprise organization 、 Business scenario 、 Complexity is closely related . With the rapid development of digital services , It will also directly lead to API The number and safety demands are rising in a straight line .
existing API Unclear assets , newly added API Interface doesn't know
For traditional enterprises , Systems are often very complex , Which interfaces are called by whom , It's basically impossible to sort it out manually ; Even if it was born in API Emerging enterprises that have been widely concerned , It is not possible to check all interfaces before each version goes online . ideally , The business should be launched only when it is confirmed to be safe , But in fact, this is mission impossible, The risk is buried .
Besides ,API The R & D team is usually responsible for the development and maintenance of , Safety is the responsibility of the safety team , The information gap between the two sides , Make tradition API The gateway uploads interface information manually , It is bound to produce a large number of “ a fish escaped through the seine ”.
Richer digital services bring more complex API management
Enterprises API Safety construction opposite circuit 、 Aggregate analysis 、 Broadband 、 The consumption of computing resources is very high , Every change in digital business may bring API Number 、 Call logic 、 Changes in importance , There may be countless API Go online and fail , Not to protect API Safe and refuse business changes , Nor can it cause security risks due to business changes , How to balance the two is a necessary problem .
Alicloud native API Security solution : High performance 、 Super controllable 、 Extreme zoom 、 Minimalist and efficient
Alibaba cloud API Security is based on Alibaba cloud WAF A set of product construction revolves around API Comprehensive security solutions , It can completely cover OWASP API top 10 Risk response . stay WAF Press the previous key to open , Eliminate complex deployment costs , Support API Asset lifecycle management , And can directly play its original defense ability , Deal with malicious behavior to form a closed-loop scheme , Reduce cross product operation costs ,WAF The attack blocking ability of the product 、 Access frequency limit 、 Reptile protection 、 Special protection for account security 、 Security scanning protection 、 The ability to prevent leakage of sensitive data can be used API Safe disposal capability , Form feature schemes for specific scenes .


( Data reference OWASP API Security Top 10)
Extreme zoom
Combined with Alibaba cloud's global edge site network , Provide end users with the lowest possible API Request and response delays . Limit traffic and authorize API call , To ensure that back-end operations can withstand peak traffic , And will not unnecessarily call back-end systems .
If a customer one day 5000QPS, Millions of logs will be generated , Check millions of logs by manpower API risk , unimaginable , Automatic analysis with Alibaba cloud model , It can be finished in a few minutes ;
Easy monitoring
Monitor relevant information from Alibaba cloud control panel API call 、 The performance indicators and information of data latency and error rate help customers more intuitively monitor their calls to services . This console optimization , The visual aspect makes customers more clear about the asset life cycle 、 More convenient positioning of pre / Alarm and new / The old API Online and offline 、 More obvious dialysis data risks .
from API Asset discovery 、 Risk vulnerability detection and abnormal behavior detection are completed automatically , The user only needs to confirm and handle the alarm ;
Flexible control
There is no need to deploy detection nodes on the customer's business side , Adopt bypass static analysis , No business impact , It will not pollute business data . Alibaba cloud API Security solutions rely on the cloud WAF, Native access through cloud domain name , Static bypass analysis , Because all traffic flows through WAF,Web API The list of total assets is visible .
Minimalist and efficient
There is no need to configure one click on 、 Cloud management . Take full advantage of the native advantages of cloud , Combined with business logic , No mating or probe is required , Problems can be found 、 Detailed observation 、 Processing closed-loop one key start while assisting in optimizing business logic .
【 What is noteworthy is that this time it is aimed at API Console capability optimization , Make the asset life cycle clearer 、 Positioning problems is more convenient 、 The data problem is more obvious .】
Alibaba cloud automatically analyzes API Access log , Creatively for each API Automatically Put on the business label , from “ Interface type + Sensitivity level + Authentication capability ” Three dimensions , Comprehensive definition API Interface importance , Realize to API Classification and hierarchical management .
At present, Alibaba cloud provides nearly 20 Business labels , It basically covers the common business types of customers .
API Another advantage of classification and hierarchical management is that it can help optimize business logic . for example , In the anti climbing scene , If an interface is detected to be brushed , You can see the business scenario corresponding to the interface , So as to find out and optimize the homogeneous business scenarios in the alarm .
API Risk vulnerability identification
Alibaba cloud API Security can be identified, including brute force cracking 、 Safety risks such as anti climbing , Combined with the importance of the interface, the risk is divided into high, medium and low levels , Cover traffic 、 Online retailers 、 Financial insurance 、 Catering, retail and other different industries .
At the same time, we can actively and timely discover the natural problems existing in the development and design API Exposure risk , Prevent data leakage before it happens .
From the perspective of sensitive data API Call exception monitoring
Sensitive data identification is accurate judgment API Whether the call will lead to data disclosure , Based on the sensitive data identification capability of Alibaba cloud data security center , every time API call , Can clearly see whether sensitive data is involved , Prevent leakage .
meanwhile , The powerful computing power of the cloud can get rid of the traditional practice of judging exceptions by rules , With the help of intelligent model, from IP source 、 Access link 、 Parameters used by the access procedure 、 Comprehensive analysis of different dimensions such as the types of sensitive data obtained , Greatly reduce false positives and omissions .

Customer practice
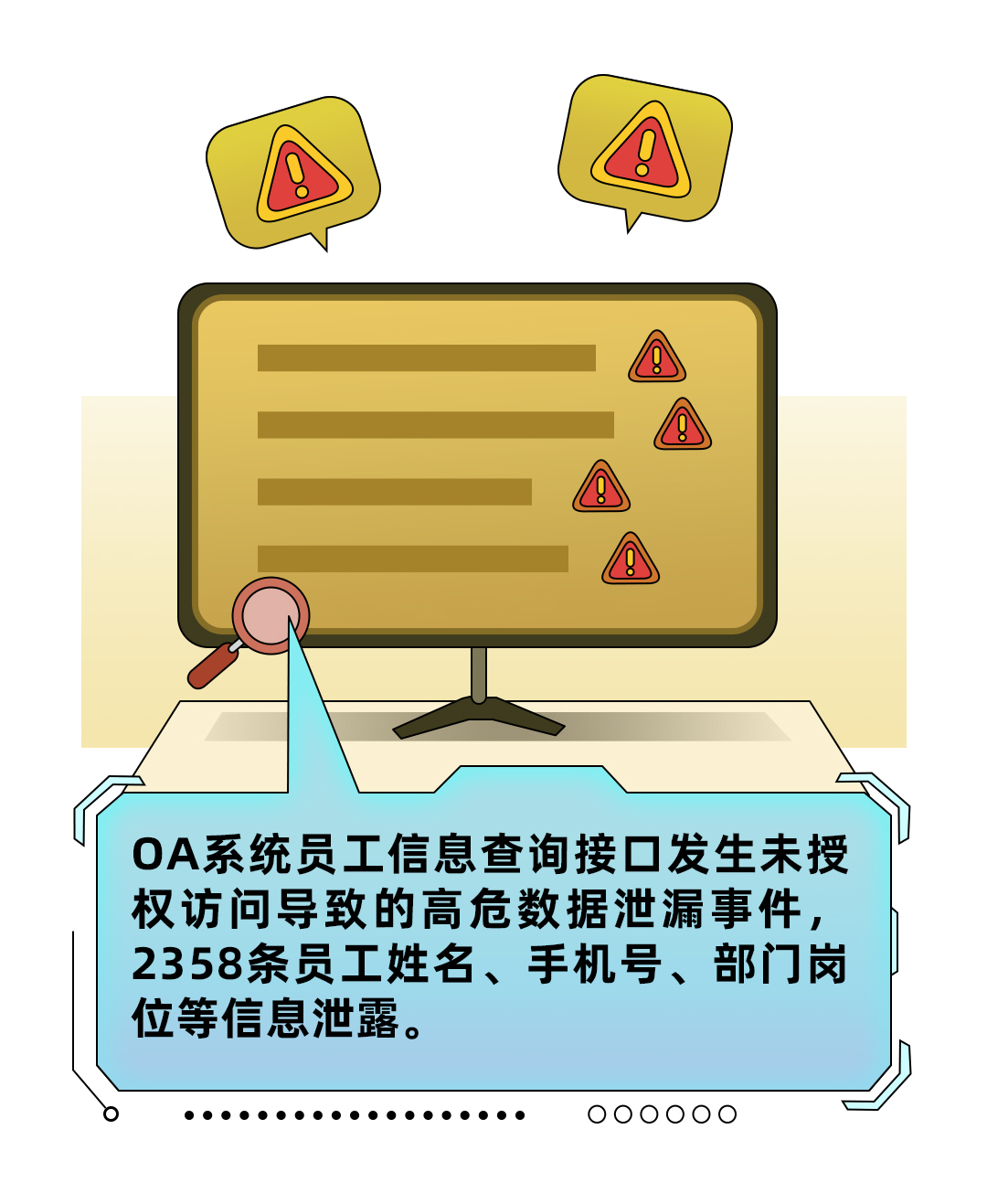
Case a : A third-party financial software provider ,OA System interface public network exposure risk
Hidden danger : The customer has not used effective API Control tools , Yes API I don't know about assets and their protection mechanism . And the safety awareness of the team is weak , The business side believes that as long as the interface authority control is well done , Even if the API There is no risk in opening to the public network .
Find the problem : Access Alibaba cloud API Safety products , The customer found that there were tens of thousands API Interface exists , And detected internally used OA The address book query interface of an employee in the office system is exposed on the public network , And unauthorized access . Through this interface , Get the names of all employees of the enterprise 、 Contact information 、 Organization structure and other core sensitive information .
Verified , Confirm that the customer exists API risk , Alibaba cloud immediately takes security measures :
- adopt WAF Console , Configure for this API Interface ACL Visit the white list ( Only its corporate office network is allowed IP Visit , Ban all others IP The interview of );
- Inform the business team in charge of the system of this information for rectification , The next day, the business team fixed the vulnerability of unauthorized access to the interface ;
- according to API Safety analysis results , adopt WAF For all its internal use API Interface configuration ACL Access control , Restrict access to sources
Case 2 : A catering enterprise Unauthorized access to customer consumption information
Consumer's name 、 Information such as mobile phone number is 《 Personal information protection law 》 Specify the personal privacy data to be protected , Its consumption data is the core business data of enterprises .
The customer accesses Alibaba cloud API The security product has detected that one of its interfaces for querying customer consumption records can be accessed without authorization , Through this interface , You can get the name of any customer according to your mobile phone number 、 Contact information 、 Records of consumption 、 Consumption habits and other core sensitive information of enterprises and customers .
Although the customer has been conscious of protecting this part of data , However, due to the code logic defects of the interface authentication part , On the surface, , The request of the interface needs to carry the identity field for authentication , However, this field is not verified in the actual code , This leads to unauthorized access to the interface 、 The risk of unauthorized access .
Customers are concerned about API After the risk vulnerability alarm and abnormal behavior event alarm , Quickly contacted Alibaba cloud security team to check and confirm the API The existence of risk loopholes , Confirm the attack attribute of the abnormal access behavior at the first time . The security team immediately passed WAF Console , All access to this interface is blocked to stop bleeding urgently , And inform the business team of the system of this information for rectification , A week later, the business team fixed the vulnerability , The interface is re enabled to provide services , Avoid a potential data leakage event .
Link to the original text :https://developer.aliyun.com/article/979780?
Copyright notice : The content of this article is contributed by alicloud real name registered users , The copyright belongs to the original author , Alicloud developer community does not own its copyright , It also does not bear the corresponding legal liability . Please check the specific rules 《 Alicloud developer community user service agreement 》 and 《 Alibaba cloud developer community intellectual property protection guidelines 》. If you find any suspected plagiarism in this community , Fill in the infringement complaint form to report , Once verified , The community will immediately delete the suspected infringement content .
边栏推荐
- 机器学习植物叶片识别
- Black cat takes you to learn UFS Protocol Part 8: UFS initialization (boot operation)
- Today's summer solstice
- On the first day of clock in, click to open a surprise, and the switch statement is explained in detail
- LeetCode 1200. Minimum absolute difference
- Automated test environment configuration
- Private cloud disk deployment
- CS-证书指纹修改
- Luogu p2141 abacus mental arithmetic test
- [English] Verb Classification of grammatical reconstruction -- English rabbit learning notes (2)
猜你喜欢
University of Manchester | dda3c: collaborative distributed deep reinforcement learning in swarm agent systems

It is necessary to understand these characteristics in translating subtitles of film and television dramas
![[English] Verb Classification of grammatical reconstruction -- English rabbit learning notes (2)](/img/3c/c25e7cbef9be1860842e8981f72352.png)
[English] Verb Classification of grammatical reconstruction -- English rabbit learning notes (2)
mysql的基础命令
Cobalt strike feature modification
CS通过(CDN+证书)powershell上线详细版

关于新冠疫情,常用的英文单词、语句有哪些?

Financial German translation, a professional translation company in Beijing
Luogu p2089 roast chicken

利用快捷方式-LNK-上线CS
随机推荐
[brush questions] how can we correctly meet the interview?
【刷题】怎么样才能正确的迎接面试?
Attributeerror successfully resolved: can only use cat accessor with a ‘category‘ dtype
云上有AI,让地球科学研究更省力
My seven years with NLP
LeetCode 732. My schedule III
端午节快乐Wish Dragon Boat Festival is happy
翻译公司证件盖章的价格是多少
Facebook AI & Oxford proposed a video transformer with "track attention" to perform SOTA in video action recognition tasks
How much is the price for the seal of the certificate
ML之shap:基于adult人口普查收入二分类预测数据集(预测年收入是否超过50k)利用Shap值对XGBoost模型实现可解释性案例之详细攻略
Summary of leetcode's dynamic programming 4
LeetCode 739. Daily temperature
Esp32 esp-idf watchdog twdt
In English translation of papers, how to do a good translation?
成功解决TypeError: data type ‘category‘ not understood
LeetCode每日一题(971. Flip Binary Tree To Match Preorder Traversal)
MySQL high frequency interview 20 questions, necessary (important)
How to do a good job in financial literature translation?
论文翻译英译中,怎样做翻译效果好?