当前位置:网站首页>Function: string storage in reverse order
Function: string storage in reverse order
2022-07-06 14:35:00 【|Light|】
requirement
Write a function , Make an input string stored in reverse order .
Code
#include<string.h>
#include<stdio.h>
/* * This function implements the reverse order of strings */
void reverse(char a[])
{
int i,j,l;
gets(a);
i = strlen(a);
int k=0;
l = i-1;
char b[i+1];
strcpy(b,a);
for(j=0;j<i;j++)
{
a[k] = b[l];
k=k+1;
l=l-1;
}
}
test
Test input
Be honest rather clever.
Output
.revelc rehtar tsenoh eB
边栏推荐
- Binary search tree concept
- Statistics 8th Edition Jia Junping Chapter 10 summary of knowledge points of analysis of variance and answers to exercises after class
- Lintcode logo queries the two nearest saplings
- Fire! One day transferred to go engineer, not fire handstand sing Conquest (in serial)
- 数字电路基础(一)数制与码制
- Attack and defense world misc practice area (simplerar, base64stego, no matter how high your Kung Fu is, you are afraid of kitchen knives)
- Numpy快速上手指南
- How to earn the first pot of gold in CSDN (we are all creators)
- 《英特尔 oneAPI—打开异构新纪元》
- 指针--剔除字符串中的所有数字
猜你喜欢
Detailed explanation of network foundation
![[paper reproduction] cyclegan (based on pytorch framework) {unfinished}](/img/16/43d8929d1a37c1c68e959d5854e18c.jpg)
[paper reproduction] cyclegan (based on pytorch framework) {unfinished}
网络基础之路由详解
How to earn the first pot of gold in CSDN (we are all creators)
Hackmyvm target series (1) -webmaster
![New version of postman flows [introductory teaching chapter 01 send request]](/img/0f/a41a39093a1170cc3f62075fd76182.jpg)
New version of postman flows [introductory teaching chapter 01 send request]
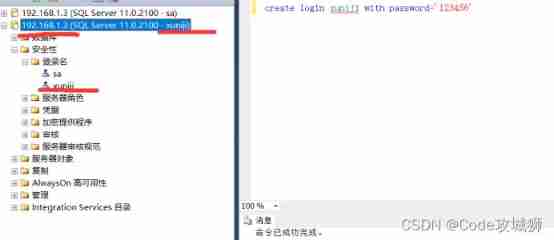
Based on authorized access, cross host, and permission allocation under sqlserver
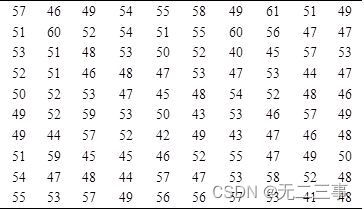
Statistics 8th Edition Jia Junping Chapter 3 after class exercises and answer summary
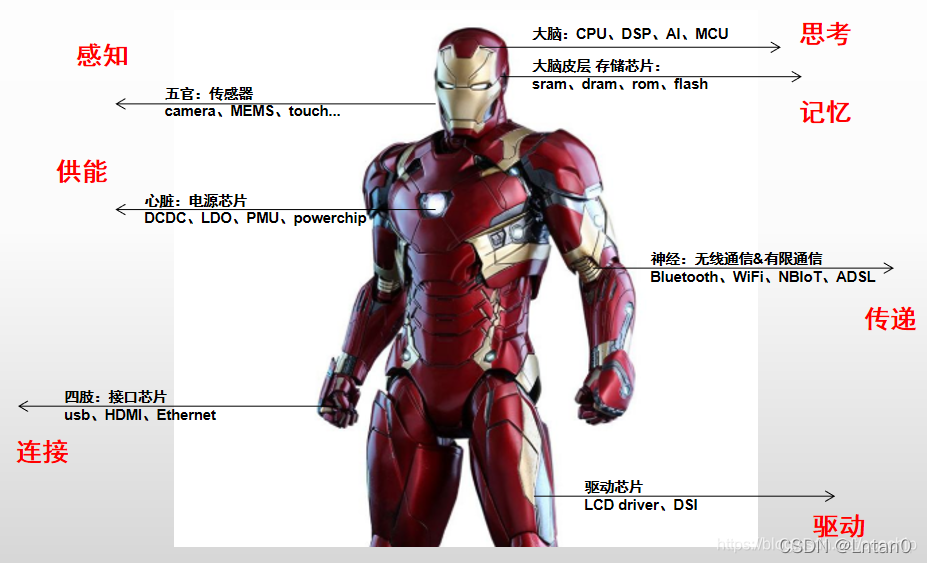
“Hello IC World”
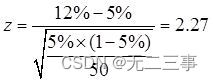
Statistics, 8th Edition, Jia Junping, Chapter VIII, summary of knowledge points of hypothesis test and answers to exercises after class
随机推荐
Sqqyw (indifferent dot icon system) vulnerability recurrence and 74cms vulnerability recurrence
Lintcode logo queries the two nearest saplings
数字电路基础(三)编码器和译码器
函数:求1-1/2+1/3-1/4+1/5-1/6+1/7-…+1/n
浅谈漏洞发现思路
5分钟掌握机器学习鸢尾花逻辑回归分类
C language file operation
DVWA (5th week)
2022华中杯数学建模思路
攻防世界MISC练习区(gif 掀桌子 ext3 )
[issue 18] share a Netease go experience
SystemVerilog discusses loop loop structure and built-in loop variable I
Hackmyvm target series (1) -webmaster
Ucos-iii learning records (11) - task management
Intranet information collection of Intranet penetration (4)
msf生成payload大全
1.支付系统
函数:字符串反序存放
Hackmyvm target series (2) -warrior
How to earn the first pot of gold in CSDN (we are all creators)