当前位置:网站首页>[pointer] solve the last person left
[pointer] solve the last person left
2022-07-06 14:36:00 【|Light|】
requirement
Yes n A circle of individuals , Sequence number . Count from the first person , Where to report 3 Of the people out of the circle , Make up a function , The last thing left is the original number .( Use a pointer to achieve )
Code
/* * This function is used to calculate the last remaining bit * n: The number of people in the enclosure * Return its number */
int last_one(int n)
{
int k=-1;
int i,j,l=0;
int a[n];
for(i=0;i<n;i++)
{
a[i] = 0;
}
for(i=0;i<n-1;i++)
{
for(j=0;j<3;j++)
{
if(a[l]==1)
{
j--;
l++;
if(l==n)
{
l=0;
}
continue;
}
if(j==2)
{
a[l]=1;
}
l++;
if(l==n)
l=0;
}
}
for(i=0;i<n;i++)
{
if(a[i]==0)
{
k = i+1;
break;
}
}
return k;
}
main function
int main()
{
int n;
scanf("%d",&n);
printf("%d\n",last_one(n));
return 0;
}
test
Test input
3
Output
2
边栏推荐
- 指针--剔除字符串中的所有数字
- 【指针】八进制转换为十进制
- 数字电路基础(一)数制与码制
- JDBC read this article is enough
- Library management system
- Xray and Burp linked Mining
- 【指针】查找最大的字符串
- Numpy Quick Start Guide
- MySQL中什么是索引?常用的索引有哪些种类?索引在什么情况下会失效?
- Bing Dwen Dwen official NFT blind box will be sold for about 626 yuan each; JD home programmer was sentenced for deleting the library and running away; Laravel 9 officially released | Sifu weekly
猜你喜欢
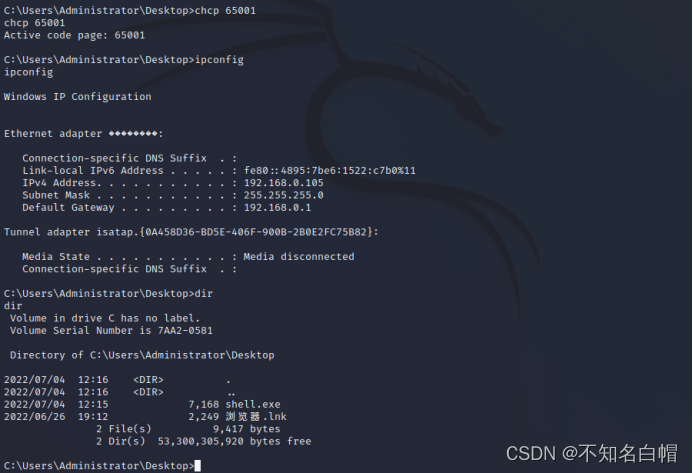
Intranet information collection of Intranet penetration (I)
“Hello IC World”
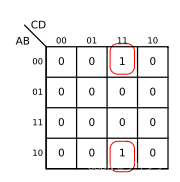
数字电路基础(二)逻辑代数
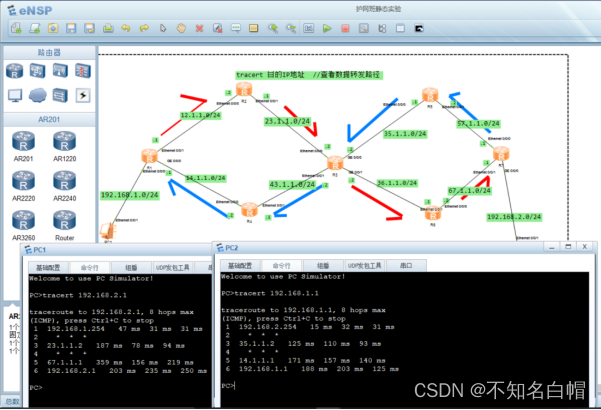
Detailed explanation of network foundation routing

数字电路基础(三)编码器和译码器
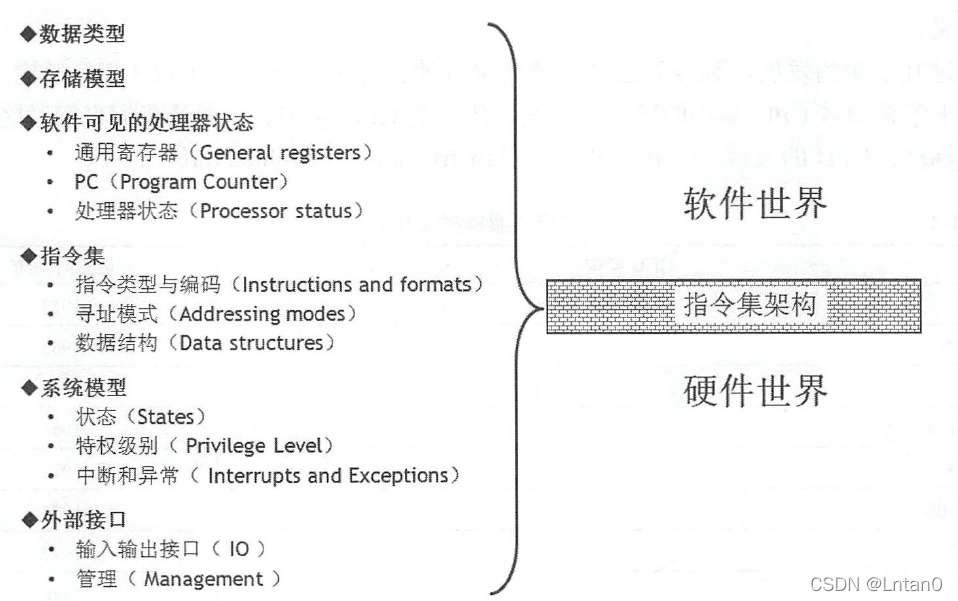
“人生若只如初见”——RISC-V
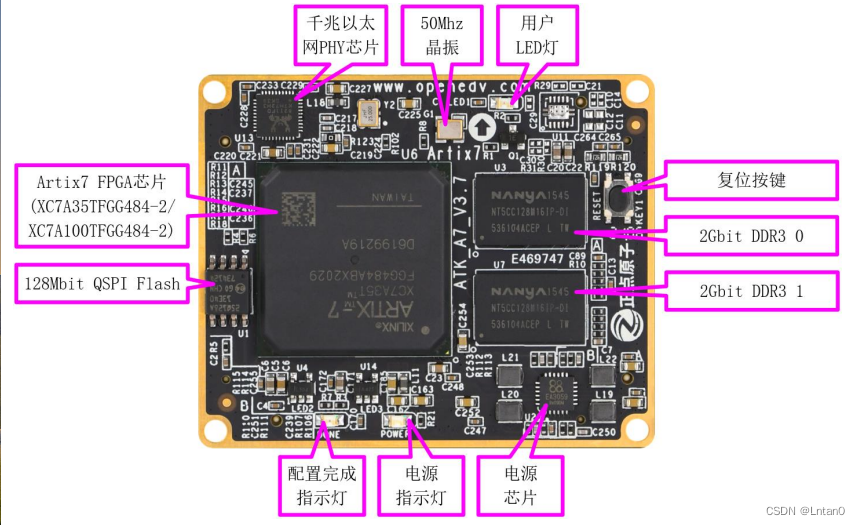
移植蜂鸟E203内核至达芬奇pro35T【集创芯来RISC-V杯】(一)
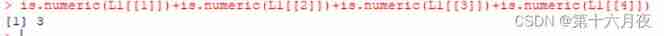
List and data frame of R language experiment III
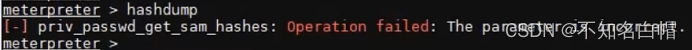
内网渗透之内网信息收集(三)
Fundamentals of digital circuit (IV) data distributor, data selector and numerical comparator
随机推荐
Library management system
Detailed explanation of network foundation
flask实现强制登陆
Only 40% of the articles are original? Here comes the modification method
Intranet information collection of Intranet penetration (3)
ES全文索引
Ucos-iii learning records (11) - task management
Mathematical modeling idea of 2022 central China Cup
Web vulnerability - File Inclusion Vulnerability of file operation
《统计学》第八版贾俊平第五章概率与概率分布
数字电路基础(二)逻辑代数
XSS unexpected event
c语言学习总结(上)(更新中)
Intranet information collection of Intranet penetration (2)
Bing Dwen Dwen official NFT blind box will be sold for about 626 yuan each; JD home programmer was sentenced for deleting the library and running away; Laravel 9 officially released | Sifu weekly
JDBC transactions, batch processing, and connection pooling (super detailed)
Windows platform mongodb database installation
The difference between layer 3 switch and router
Record once, modify password logic vulnerability actual combat
Numpy Quick Start Guide